| Номер ошибки: | Ошибка 433 | |
| Название ошибки: | Cisco Vpn Client Error 433 | |
| Описание ошибки: | Ошибка 433: Возникла ошибка в приложении Cisco VPN Client. Приложение будет закрыто. Приносим извинения за неудобства. | |
| Разработчик: | Cisco Systems, Inc. | |
| Программное обеспечение: | Cisco VPN Client | |
| Относится к: | Windows XP, Vista, 7, 8, 10, 11 |
Объяснение «Cisco Vpn Client Error 433»
«Cisco Vpn Client Error 433» часто называется ошибкой во время выполнения (ошибка). Разработчики, такие как Cisco Systems, Inc., обычно проходят через несколько контрольных точек перед запуском программного обеспечения, такого как Cisco VPN Client. Как и во всем в жизни, иногда такие проблемы, как ошибка 433, упускаются из виду.
Ошибка 433 также отображается как «Cisco Vpn Client Error 433». Это распространенная ошибка, которая может возникнуть после установки программного обеспечения. Если возникает ошибка 433, разработчикам будет сообщено об этой проблеме через уведомления об ошибках, которые встроены в Cisco VPN Client. Затем программисты могут исправить эти ошибки в коде и включить исправление, которое можно загрузить с их веб-сайта. Если есть запрос на обновление Cisco VPN Client, это обычно обходной путь для устранения проблем, таких как ошибка 433 и другие ошибки.
Почему и когда срабатывает ошибка времени выполнения 433?
В первый раз, когда вы можете столкнуться с ошибкой среды выполнения Cisco VPN Client обычно с «Cisco Vpn Client Error 433» при запуске программы. Три распространенные причины, по которым ошибки во время выполнения, такие как всплывающее окно ошибки 433:
Ошибка 433 Crash — она называется «Ошибка 433», когда программа неожиданно завершает работу во время работы (во время выполнения). Если Cisco VPN Client не может обработать данный ввод, или он не может получить требуемый вывод, это обычно происходит.
Утечка памяти «Cisco Vpn Client Error 433» — ошибка 433 утечка памяти приводит к тому, что Cisco VPN Client использует все больше памяти, что делает ваш компьютер запуск медленнее и замедляет вывод системы. Повреждение памяти и другие потенциальные ошибки в коде могут произойти, когда память обрабатывается неправильно.
Ошибка 433 Logic Error — Компьютерная система создает неверную информацию или дает другой результат, даже если входные данные являются точными. Это связано с ошибками в исходном коде Cisco Systems, Inc., обрабатывающих ввод неправильно.
Cisco Systems, Inc. проблемы с Cisco Vpn Client Error 433 чаще всего связаны с повреждением или отсутствием файла Cisco VPN Client. Как правило, любую проблему, связанную с файлом Cisco Systems, Inc., можно решить посредством замены файла на новую копию. В некоторых случаях реестр Windows пытается загрузить файл Cisco Vpn Client Error 433, который больше не существует; в таких ситуациях рекомендуется запустить сканирование реестра, чтобы исправить любые недопустимые ссылки на пути к файлам.
Распространенные сообщения об ошибках в Cisco Vpn Client Error 433
Общие проблемы Cisco Vpn Client Error 433, возникающие с Cisco VPN Client:
- «Ошибка программы Cisco Vpn Client Error 433. «
- «Ошибка программного обеспечения Win32: Cisco Vpn Client Error 433»
- «Cisco Vpn Client Error 433 должен быть закрыт. «
- «Файл Cisco Vpn Client Error 433 не найден.»
- «Cisco Vpn Client Error 433 не найден.»
- «Ошибка запуска в приложении: Cisco Vpn Client Error 433. «
- «Файл Cisco Vpn Client Error 433 не запущен.»
- «Ошибка Cisco Vpn Client Error 433. «
- «Ошибка пути программного обеспечения: Cisco Vpn Client Error 433. «
Обычно ошибки Cisco Vpn Client Error 433 с Cisco VPN Client возникают во время запуска или завершения работы, в то время как программы, связанные с Cisco Vpn Client Error 433, выполняются, или редко во время последовательности обновления ОС. Отслеживание того, когда и где возникает ошибка Cisco Vpn Client Error 433, является важной информацией при устранении проблемы.
Источники проблем Cisco Vpn Client Error 433
Проблемы Cisco Vpn Client Error 433 вызваны поврежденным или отсутствующим Cisco Vpn Client Error 433, недопустимыми ключами реестра, связанными с Cisco VPN Client, или вредоносным ПО.
Точнее, ошибки Cisco Vpn Client Error 433, созданные из:
- Поврежденная или недопустимая запись реестра Cisco Vpn Client Error 433.
- Загрязненный вирусом и поврежденный Cisco Vpn Client Error 433.
- Другая программа злонамеренно или по ошибке удалила файлы, связанные с Cisco Vpn Client Error 433.
- Другая программа находится в конфликте с Cisco VPN Client и его общими файлами ссылок.
- Cisco VPN Client/Cisco Vpn Client Error 433 поврежден от неполной загрузки или установки.
Продукт Solvusoft
Загрузка
WinThruster 2023 — Проверьте свой компьютер на наличие ошибок.
Совместима с Windows 2000, XP, Vista, 7, 8, 10 и 11
Установить необязательные продукты — WinThruster (Solvusoft) | Лицензия | Политика защиты личных сведений | Условия | Удаление
Secure VPN Connection terminated by Peer.
Reason 433: Reason Not Specified by Peer
I ran into this error recently when trying to set up a Remote Access VPN. This error could be caused by multiple problems. However, in my particular case, it was the settings under AAA authentication servers. Upon connection, the VPN client would prompt for logon credentials and then immediately return this error.
In my environment, I was using a Windows Server 2003 Domain Controller for LDAP authentication. The VPN termination point was an older PIX 515 firewall running IOS 8.0. I was also using the latest Cisco VPN client on Windows 8.1.
After some quick troubleshooting, it appeared that the domain account used to query LDAP was either buried too deep in the OU structure or, some of the OU names were causing problems (they had spaces and special characters).
As a test, I moved the account back up to the root-level “Users” container. I then altered my DN settings on the firewall to reflect this change. The VPN client software connected immediately.
To be fair, I was configuring Remote Access VPN on a very old PIX 515. It could be that a newer ASA firewall running the latest IOS won’t have this particular issue. Either way, just something else to try if you get this error code.
Lastly, here is a quick screenshot of a working AAA server configuration as well as an explanation of all the fields.
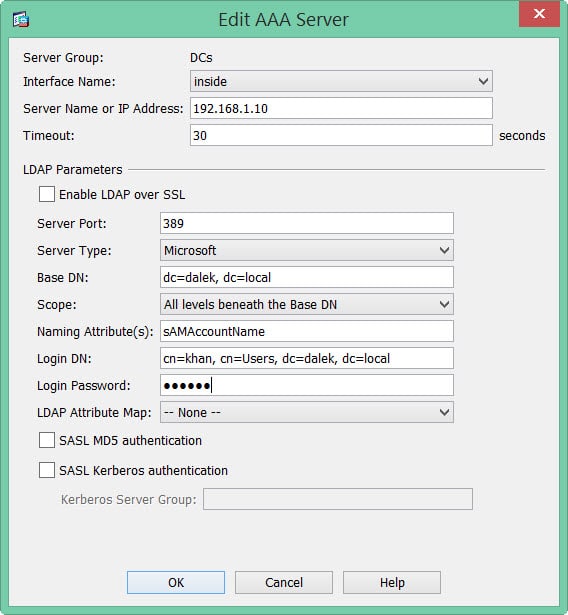
- Server Group: This is purely descriptive. Call it whatever you like.
- Interface Name: This is the name of the interface your AAA server can be located on. In my example, an interface called INSIDE.
- Server Name or IP Address: The name or IP address of your AAA server.
- Timeout: The default is 5 seconds. Set this to whatever makes you feel comfortable. I like 30 seconds.
- Enable LDAP over SSL: I typically leave this unchecked and do my LDAP queries over the standard 389 port. If you check this box it will default to port 636 and send queries over SSL.
- Server Port: The default LDAP port is 389. Most likely what you will have here.
- Server Type: For me, my LDAP server was Microsoft. You can pick other LDAP providers but the rest of these bullets will assume you are using Microsoft.
- Base DN: This sets wherein the hierarchy to start LDAP searches for users. We could drill this down to a specific OU. Or we could just use the root domain. For example dalek.local becomes dc=dalek, dc=local. (Being specific does have the potential to speed up LDAP queries!)
- Scope: I typically set this as All Levels Beneath the Base DN. This allows you to specify how deep from the Base DN you want LDAP queries to search.
- Naming Attributes: Specifies what to match against. In Windows, this is the account name, or, sAMAccountName.
- Login DN: The full path, including username, to the account used to perform the LDAP queries. In my case, the user was Khan and they were in the top level Users OU. Their domain is dalek.local. So, this becomes, cn=khan, cn=Users, dc=dalek, dc=local.
- All other options I leave as defaults.

Gareth is an Microsoft MVP specializing in Exchange and Office 365. Gareth also contributes to the Office 365 for IT Pros book, which is updated monthly with new content. Find Gareth on LinkedIn, Twitter, or, Facebook.
Reader Interactions
Introduction
This document describes the most common solutions to IPsec VPN problems.
Background Information
The solutions described here come directly from service requests that the Cisco Technical Support have solved.
Many of these solutions are implemented prior to the in-depth troubleshooting of an IPsec VPN connection.
This document provides a summary of common procedures to try before you begin to troubleshoot a connection.
Although the configuration examples in this document are for use on routers and security appliances, nearly all of these concepts are also applicable to the VPN 3000 .
Refer toIP Security Troubleshooting — Understanding and Using debug Commandsfor an explanation of common debug commands that are used to troubleshoot IPsec issues on both the Cisco IOS® software and .
Note: ASA does not pass multicast traffic over IPsec VPN tunnels.
Warning: Many of the solutions presented in this document can lead to a temporary loss of all IPsec VPN connectivity on a device.
It is recommended that these solutions be implemented with caution and in accordance with your change control policy.
Prerequisites
Requirements
Cisco recommends knowledge of IPsec VPN configuration on these Cisco devices:
-
Cisco ASA 5500 Series Security Appliance
-
Cisco IOS® Routers
Components Used
The information in this document is based on these software and hardware versions:
-
Cisco ASA 5500 Series Security Appliance
-
Cisco IOS®
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, ensure that you understand the potential impact of any command.
Conventions
Refer toCisco Technical Tips Conventionsfor more information on document conventions.
IPsec VPN Configuration Does Not Work
Problem
A recently configured or modified IPsec VPN solution does not work.
A current IPsec VPN configuration no longer works.
Solutions
This section contains solutions to the most common IPsec VPN problems.
Although they are not listed in any particular order, these solutions can be used as a checklist of items to verify or try before you engage in in-depth remediation.
All of these solutions come directly from TAC service requests and have resolved numerous issues.
-
Enable NAT-Traversal (#1 RA VPN Issue)
-
Test Connectivity Properly
-
Enable ISAKMP
-
Enable/Disable PFS
-
Clear Old or Existing Security Associations (Tunnels)
-
Verify ISAKMP Lifetime
-
Enable or Disable ISAKMP Keepalives
-
Re-Enter or Recover Pre-Shared-Keys
-
Mismatched Pre-shared Key
-
Remove and Re-apply Crypto Maps
-
Verify that sysopt Commands are Present (/ASA Only)
-
Verify the ISAKMP Identity
-
Verify Idle/Session Timeout
-
Verify that ACLs are Correct and are Binded to Crypto Map
-
Verify the ISAKMP Policies
-
Verify that Routing is Correct
-
Verify that Transform-Set is Correct
-
Verify Crypto Map Sequence Numbers and Name
-
Verify the Peer IP Address is Correct
-
Verify the Tunnel Group and Group Names
-
Disable XAUTH for L2L Peers
-
VPN Pool Getting Exhausted
-
Issues with latency for VPN client traffic
Note: Some of the commands in these sections have been brought down to a second line due to spatial considerations.
Enable NAT-Traversal (#1 RA VPN Issue)
NAT-Traversal (or NAT-T) allows VPN traffic to pass through NAT or PAT devices, such as a Linksys SOHO router.
If NAT-T is not enabled, VPN Client users often appear to connect to the ASA without a problem, but they are unable to access the internal network behind the security appliance.
If you do not enable the NAT-T in the NAT/PAT Device, you can receive theregular translation creation failed for protocol 50 src inside:10.0.1.26 dst outside:10.9.69.4error message in the ASA.
Similarly, if you are unable to do simultaneous login from the same IP address, theSecure VPN connection terminated locally by client. Reason 412: The remote peer is no longer responding.error message appears.
Enable NAT-T in the head end VPN device in order to resolve this error.
Note: With Cisco IOS® Software Release 12.2(13)T and later, NAT-T is enabled by default in Cisco IOS®.
Here is the command to enable NAT-T on a Cisco Security Appliance. The twenty (20) in this example is the keepalive time (default).
ASA
securityappliance(config)#crypto isakmp nat-traversal 20
The clients need to be modified as well in order for it to work.
In Cisco VPN Client, navigate toConnection Entriesand clickModify. It opens a new window where you have to choose theTransporttab.
Under this tab, clickEnable Transparent Tunnelingand theIPSec over UDP ( NAT / PAT )radio button. Then clickSaveand test the connection.
It is important to allow the UDP 4500 for NAT-T, UDP 500 and ESP ports by the configuration of an ACL because the ASA acts as a NAT device.
Refer toConfiguring an IPsec Tunnel through a Firewall with NATfor more information in order to learn more about the ACL configuration in ASA.
Test Connectivity Properly
Ideally, VPN connectivity is tested from devices behind the endpoint devices that do the encryption, yet many users test VPN connectivity with thepingcommand on the devices that do the encryption.
While thepinggenerally works for this purpose, it is important to source your ping from the correct interface.
If thepingis sourced incorrectly, it can appear that the VPN connection has failed when it really works. This is one example:
Router A crypto ACL
access-list 110 permit ip 192.168.100.0 0.0.0.255 192.168.200.0 0.0.0.255
Router B crypto ACL
access-list 110 permit ip 192.168.200.0 0.0.0.255 192.168.100.0 0.0.0.255
In this situation, apingmust be sourced from the inside network behind either router. This is because the crypto ACLs are only configured to encrypt traffic with those source addresses.
Apingsourced from the outside interfaces of either router are not encrypted. Use the extended options of thepingcommand in privileged EXEC mode to source a ping from the inside interface of a router:
routerA#ping Protocol [ip]: Target IP address: 192.168.200.10 Repeat count [5]: Datagram size [100]: Timeout in seconds [2]: Extended commands [n]: y Source address or interface: 192.168.100.1 Type of service [0]: Set DF bit in IP header? [no]: Validate reply data? [no]: Data pattern [0xABCD]: Loose, Strict, Record, Timestamp, Verbose[none]: Sweep range of sizes [n]: Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 192.168.200.1, timeout is 2 seconds: Packet sent with a source address of 192.168.100.1 !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = ½/4 ms
Imagine that the routers in this diagram have been replaced with ASA security appliances. Theping which is used to test connectivity can also be sourced from the inside interface with theinsidekeyword:
securityappliance#ping inside 192.168.200.10 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 192.168.200.10, timeout is 2 seconds: !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/1 ms
It is not recommended to target the inside interface of a security appliance with yourping.
If you must target the inside interface with yourping, you must enablemanagement-accesson that interface, or the appliance does not reply.
securityappliance(config)#management-access inside
When a problem exists with the connectivity, even phase one (1) of VPN does not function.
On the ASA, if connectivity fails, the SA output is similar to this example, which indicates a possible incorrect crypto peer configuration and/or incorrect ISAKMP proposal configuration:
Router#show crypto isakmp sa
1 IKE Peer: XX.XX.XX.XX
Type : L2L Role : initiator
Rekey : no State : MM_WAIT_MSG2
The state can be from MM_WAIT_MSG2 to MM_WAIT_MSG5, which denotes failure of concerned state exchange in Main Mode (MM).
Crypto SA output when the phase 1 is up is similar to this example:
Router#show crypto isakmp sa
1 IKE Peer: XX.XX.XX.XX
Type : L2L Role : initiator
Rekey : no State : MM_ACTIVE
Enable ISAKMP
If there is no indication that an IPsec VPN tunnel works, it possible that ISAKMP has not been enabled. Be sure that you have enabled ISAKMP on your devices.
Use one of these commands to enable ISAKMP on your devices:
Cisco IOS®
router(config)#crypto isakmp enable
Cisco ASA (replaceoutsidewith your desired interface)
securityappliance(config)#crypto isakmp enable outside
You can also get this error when you enable the ISAKMP on the outside interface:
UDP: ERROR - socket <unknown> 62465 in used ERROR: IkeReceiverInit, unable to bind to port
The cause of the error can be that the Client behind ASA gets PAT to udp port 500 before isakmp can be enabled on the interface. Once that PAT translation is removed (clear xlate), the isakmp is able to be enabled.
Verify that UDP 500 and 4500 port numbers are reserved for the negotiation of ISAKMP connections with the peer.
When the ISAKMP is not enabled on the interface, the VPN client shows an error message similar to this message:
Secure VPN connection terminated locally by client. Reason 412: The remote peer is no longer responding
In order to resolve this error, enable the ISAKMP on the crypto interface of the VPN gateway.
Enable/Disable PFS
In IPsec negotiations, Perfect Forward Secrecy (PFS) ensures that each new cryptographic key is unrelated to any previous key.
Either enable or disable PFS on both the tunnel peers; otherwise, the LAN-to-LAN (L2L) IPsec tunnel is not established in the ASA / Cisco IOS® router.
Perfect Forward Secrecy (PFS) is Cisco proprietary and is not supported on third party devices.
ASA:
PFS is disabled by default. In order to enable PFS, use thepfscommand with the enable keyword in group-policy configuration mode. In order to disable PFS, enter the disable keyword.
hostname(config-group-policy)#pfs {enable | disable}
In order to remove the PFS attribute from the configuration, enter the no form of this command.
A group policy can inherit a value for PFS from another group policy. Enter the no form of this command in order to prevent transfer of a value.
hostname(config-group-policy)#no pfs
Cisco IOS® Router:
In order to specify that IPsec must ask for PFS when new Security Associations are requested for this crypto map entry, use theset pfscommand in crypto map configuration mode.
In order to specify that IPsec requires PFS when it receives requests for new Security Associations, use theset pfscommand in crypto map configuration mode.
In order to specify that IPsec must not request PFS, use the no form of this command. By default, PFS is not requested. If no group is specified with this command, group1 is used as the default.
set pfs [group1 | group2] no set pfs
For the set pfs command:
-
group1 —Specifies that IPsec must use the 768-bit Diffie-Hellman prime modulus group when the new Diffie-Hellman exchange is performed.
-
group2 —Specifies that IPsec must use the 1024-bit Diffie-Hellman prime modulus group when the new Diffie-Hellman exchange is performed.
Example:
Router(config)#crypto map map 10 ipsec-isakmp Router(config-crypto-map)#set pfs group2
Clear Old or Current Security Associations (Tunnels)
If this error message occurs in the Cisco IOS®® router, the problem is that the SA has either expired or been cleared.
The remote tunnel end device does not know that it uses the expired SA to send a packet (not a SA establishment packet).
When a new SA has been established, the communication resumes, so initiate the interesting traffic across the tunnel to create a new SA and re-establish the tunnel.
%CRYPTO-4-IKMP_NO_SA: IKE message from x.x.x.x has no SA
If you clear ISAKMP (Phase I) and IPsec (Phase II) security associations (SAs), it is the simplest and often the best solution to resolve IPsec VPN problems.
If you clear SAs, you can frequently resolve a wide variety of error messages and strange behaviors without the need to troubleshoot.
While this technique can easily be used in any situation, it is almost always a requirement to clear SAs after you change or add to a current IPsec VPN configuration.
Moreover, while it is possible to clear only specific security associations, the most benefit can come from when you clear SAs globally on the device.
Once the Security Associations have been cleared, it can be necessary to send traffic across the tunnel to re-establish them.
Warning: Unless you specify which security associations to clear, the commands listed here can clear all security associations on the device. Proceed with caution if other IPsec VPN tunnels are in use.
-
View Security Associations before you clear them
-
Cisco Cisco IOS®
router#show crypto isakmp sa router#show crypto ipsec sa
-
Cisco ASA Security Appliances
securityappliance#show crypto isakmp sa securityappliance#show crypto ipsec sa
-
-
Clear Security Associations. Each command can be entered as shown in bold or entered with the options shown with them.
-
Cisco IOS®
-
ISAKMP (Phase I)
router#clear crypto isakmp ? <0 - 32766> connection id of SA <cr>
-
IPsec (Phase II)
router#clear crypto sa ? counters Reset the SA counters map Clear all SAs for a given crypto map peer Clear all SAs for a given crypto peer spi Clear SA by SPI <cr>
-
-
Cisco ASA Security Appliances
-
ISAKMP (Phase I)
securityappliance#clear crypto isakmp sa
-
IPsec (Phase II)
security appliance#clear crypto ipsec sa ? counters Clear IPsec SA counters entry Clear IPsec SAs by entry map Clear IPsec SAs by map peer Clear IPsec SA by peer <cr>
-
-
Verify ISAKMP Lifetime
If the users are frequently disconnected across the L2L tunnel, the problem can be the lesser lifetime configured in ISAKMP SA.
If any discrepancy occurs in the ISAKMP lifetime, you can receive the%ASA-5-713092: Group = x.x.x.x, IP = x.x.x.x, Failure during phase 1 rekey attempt due to collisionerror message in /ASA.
The default is 86,400 seconds or 24 hours. As a general rule, a shorter lifetime provides more secure ISAKMP negotiations (up to a point), but, with shorter lifetimes, the security appliance sets up future IPsec SAs more quickly.
A match is made when both policies from the two peers contain the same encryption, hash, authentication, and Diffie-Hellman parameter values, and when the policy of the remote peer specifies a lifetime less than or equal to the lifetime in the compared policy.
If the lifetimes are not identical, the shorter lifetime—from the policy of the remote peer—is used. If no acceptable match is found, the IKE refuses negotiation, and the IKE SA is not established.
Specify the SA lifetime. This examples sets a lifetime of 4 hours (14400 seconds). The default is 86400 seconds (24 hours).
ASA
hostname(config)#isakmp policy 2 lifetime 14400
Cisco IOS® Router
R2(config)#crypto isakmp policy 10 R2(config-isakmp)#lifetime 86400
If the maximum configured lifetime is exceeded, you receive this error message when the VPN connection is terminated:
Secure VPN Connection terminated locally by the Client. Reason 426: Maximum Configured Lifetime Exceeded.
In order to resolve this error message, set thelifetimevalue to zero (0) in order to set the lifetime of an IKE security association to infinity. The VPN is always be connected and does not terminate.
hostname(config)#isakmp policy 2 lifetime 0
You can also disable re-xauth in the group-policyin order to resolve the issue.
Enable or Disable ISAKMP Keepalives
If you configure ISAKMP keepalives, it helps prevent sporadically dropped LAN-to-LAN or Remote Access VPN, which includes VPN clients, tunnels and the tunnels that are dropped after a period of inactivity.
This feature lets the tunnel endpoint monitor the continued presence of a remote peer and report its own presence to that peer.
If the peer becomes unresponsive, the endpoint removes the connection.
In order for ISAKMP keepalives to work, both VPN endpoints must support them.
Configure ISAKMP keepalives in Cisco IOS® with this command:
router(config)#crypto isakmp keepalive 15
Use these commands to configure ISAKMP keepalives on the ASA Security Appliances:
Cisco ASA for the tunnel group named10.165.205.222
securityappliance(config)#tunnel-group 10.165.205.222 ipsec-attributes securityappliance(config-tunnel-ipsec)#isakmp keepalive threshold 15 retry 10
In some situations, it is necessary to disable this feature in order to solve the problem, for example, if the VPN Client is behind a Firewall that prevents DPD packets.
Cisco ASA, for the tunnel group named10.165.205.222
Disable IKE keepalive processing, which is enabled by default.
securityappliance(config)#tunnel-group 10.165.205.222 ipsec-attributes securityappliance(config-tunnel-ipsec)#isakmp keepalive disable
Disable Keepalive for Cisco VPN Client 4.x
Navigate to%System Root% > Program Files > Cisco Systems >VPN Client > Profileson the Client PC that experiences the issue in order to disable IKE keepalive, and edit thePCF file, where applicable, for the connection.
Change theForceKeepAlives=0(default) toForceKeepAlives=1.
Keepalives are Cisco proprietary and are not supported by third party devices.
Re-Enter or Recover Pre-Shared-Keys
In many cases, a simple typographical error can be to blame when an IPsec VPN tunnel does not work. For example, on the security appliance, pre-shared keys become hidden once they are entered.
This obfuscation makes it impossible to see if a key is incorrect. Be certain that you have entered any pre-shared-keys correctly on each VPN endpoint.
Re-enter a key to be certain that it is correct; this is a simple solution that can help avoid in-depth troubleshooting.
In Remote Access VPN, check that the valid group name and preshared key are entered in the CiscoVPN Client.
You can face this error if the group name or preshared key are not matched between the VPN Client and the head-end device.
1 12:41:51.900 02/18/06 Sev=Warning/3 IKE/0xE3000056 The received HASH payload cannot be verified 2 12:41:51.900 02/18/06 Sev=Warning/2 IKE/0xE300007D Hash verification failed 3 14:37:50.562 10/05/06 Sev=Warning/2 IKE/0xE3000099 Failed to authenticate peer (Navigator:904) 4 14:37:50.593 10/05/06 Sev=Warning/2 IKE/0xE30000A5 Unexpected SW error occurred while processing Aggressive Mode negotiator:(Navigator:2202) 5 14:44:15.937 10/05/06 Sev=Warning/2 IKE/0xA3000067 Received Unexpected InitialContact Notify (PLMgrNotify:888) 6 14:44:36.578 10/05/06 Sev=Warning/3 IKE/0xE3000056 The received HASH payload cannot be verified 7 14:44:36.593 10/05/06 Sev=Warning/2 IKE/0xE300007D Hash verification failed... possibly be configured with invalid group password. 8 14:44:36.609 10/05/06 Sev=Warning/2 IKE/0xE3000099 Failed to authenticate peer (Navigator:904) 9 14:44:36.640 10/05/06 Sev=Warning/2 IKE/0xE30000A5 Unexpected SW error occurred while processing Aggressive Mode negotiator:(Navigator:2202)
Warning: If you remove crypto-related commands, you are likely to bring down one or all of your VPN tunnels. Use these commands with caution and refer to the change control policy of your organization before you remove crypto-related commands..
Use these commands to remove and re-enter the pre-shared-keysecretkeyfor the peer10.0.0.1or the groupvpngroupin Cisco IOS®:
Cisco LAN-to-LAN VPN
router(config)#no crypto isakmp key secretkey address 10.0.0.1 router(config)#crypto isakmp key secretkey address 10.0.0.1
Cisco Remote Access VPN
router(config)#crypto isakmp client configuration group vpngroup router(config-isakmp-group)#no key secretkey router(config-isakmp-group)#key secretkey
Use these commands to remove and re-enter the pre-shared-keysecretkeyfor the peer10.0.0.1on /ASA Security Appliances:
Cisco 6.x
(config)#no isakmp key secretkey address 10.0.0.1 (config)#isakmp key secretkey address 10.0.0.1
Cisco /ASA 7.x and later
securityappliance(config)#tunnel-group 10.0.0.1 ipsec-attributes securityappliance(config-tunnel-ipsec)#no ikev1 pre-shared-key securityappliance(config-tunnel-ipsec)# ikev1 pre-shared-key secretkey
Mismatched Pre-shared Key
The initiation of VPN Tunnel gets disconnected. This issue occurs because of a mismatched pre-shared-key during the phase I negotiations.
TheMM_WAIT_MSG_6message in theshow crypto isakmp sacommand indicates a mismatched pre-shared-key as shown in this example:
ASA#show crypto isakmp sa
Active SA: 1
Rekey SA: 0 (A tunnel reports 1 Active and 1 Rekey SA during rekey)
Total IKE SA: 1
1 IKE Peer: 10.7.13.20
Type : L2L Role : initiator
Rekey : no State : MM_WAIT_MSG_6
In order to resolve this issue, re-enter the pre-shared key in both appliances; the pre-shared-key must be unique and matched. SeeRe-Enter or Recover Pre-Shared-Keysfor more information.
Remove and Re-apply Crypto Maps
When youclear security associations, and it does not resolve an IPsec VPN issue, remove and reapply the relevant crypto map in order to resolve a wide variety of issues that includes intermittent drops of VPN tunnel and failure of some VPN sites to come up.
Warning: If you remove a crypto map from an interface, itdefinitelybrings down any IPsec tunnels associated with that crypto map. Cautiously proceed with these steps and consider the change control policy of your organization before you proceed.
Use these commands to remove and replace a crypto map in Cisco IOS®:
Begin with the removal of the crypto map from the interface. Use the no form of thecrypto mapcommand.
router(config-if)#no crypto map mymap
Continue to use thenoform to remove an entire crypto map.
router(config)#no crypto map mymap 10
Replace the crypto map on interface Ethernet0/0 for the peer10.0.0.1. This example shows the minimum required crypto map configuration:
router(config)#crypto map mymap 10 ipsec-isakmp router(config-crypto-map)#match address 101 router(config-crypto-map)#set transform-set mySET router(config-crypto-map)#set peer 10.0.0.1 router(config-crypto-map)#exit router(config)#interface ethernet0/0 router(config-if)#crypto map mymap
Use these commands to remove and replace a crypto map on the ASA:
Begin with the removal of the crypto map from the interface. Use the no form of thecrypto mapcommand.
securityappliance(config)#no crypto map mymap interface outside
Continue to use thenoform to remove the other crypto map commands.
securityappliance(config)#no crypto map mymap 10 match address 101 securityappliance(config)#no crypto map mymap set transform-set mySET securityappliance(config)#no crypto map mymap set peer 10.0.0.1
Replace the crypto map for the peer10.0.0.1. This example shows the minimum required crypto map configuration:
securityappliance(config)#crypto map mymap 10 ipsec-isakmp securityappliance(config)#crypto map mymap 10 match address 101 securityappliance(config)#crypto map mymap 10 set transform-set mySET securityappliance(config)#crypto map mymap 10 set peer 10.0.0.1 securityappliance(config)#crypto map mymap interface outside
If you remove and reapply the crypto map, this also resolves the connectivity issue if the IP address of head end has been changed.
Verify that sysopt Commands are Present (ASA Only)
The commandssysopt connection permit-ipsecandsysopt connection permit-vpnallow packets from an IPsec tunnel and their payloads to bypass interface ACLs on the security appliance.
IPsec tunnels that are terminated on the security appliance are likely to fail if one of these commands is not enabled.
In Security Appliance Software Version 7.0 and earlier, the relevant sysopt command for this situation issysopt connection permit-ipsec.
In Security Appliance Software Version 7.1(1) and later, the relevant sysopt command for this situation issysopt connection permit-vpn.
In 6.x, this functionality isdisabledby default. With /ASA 7.0(1) and later, this functionality isenabledby default. Use these show commands to determine if the relevantsysoptcommand is enabled on your device:
Cisco ASA
securityappliance# show running-config all sysopt no sysopt connection timewait sysopt connection tcpmss 1380 sysopt connection tcpmss minimum 0 no sysopt nodnsalias inbound no sysopt nodnsalias outbound no sysopt radius ignore-secret sysopt connection permit-vpn !--- sysopt connection permit-vpn is enabled !--- This device is running 7.2(2)
Use these commands in order to enable the correctsysoptcommand for your device:
Cisco ASA
securityappliance(config)#sysopt connection permit-vpn
If you do not wish to use thesysopt connectioncommand, explicitly permit the required interesting traffic from source to destination.
For example, from Remote to Local LAN of remote device and «UDP port 500» for outside interface of remote device to outside interface of local device, in outside ACL.
Verify the ISAKMP Identity
If the IPsec VPN tunnel has failed within the IKE negotiation, the failure can be due to either the or the inability of its peer to recognize the identity of its peer.
When two peers use IKE to establish IPsec security associations, each peer sends its ISAKMP identity to the remote peer.
It sends either its IP address or host name dependent upon how each has its ISAKMP identity set.
By default, the ISAKMP identity of the Firewall unit is set to the IP address.
As a general rule, set the security appliance and the identities of its peers in the same way to avoid an IKE negotiation failure.
In order to set the Phase 2 ID to be sent to the peer, use theisakmp identitycommand in global configuration mode.
crypto isakmp identity address !--- If the RA or L2L (site-to-site) VPN tunnels connect !--- with pre-shared key as authentication type
OR
crypto isakmp identity auto !--- If the RA or L2L (site-to-site) VPN tunnels connect !--- with ISAKMP negotiation by connection type; IP address for !--- preshared key or cert DN for certificate authentication.
OR
crypto isakmp identity hostname !--- Uses the fully-qualified domain name of !--- the host exchange ISAKMP identity information (default). !--- This name comprises the hostname and the domain name.
VPN tunnel fails to come up after a shift of configuration from to ASA with the ASA configuration migration tool; these messages appear in the log:
[IKEv1]: Group = x.x.x.x, IP = x.x.x.x, Stale PeerTblEntry found, removing!
[IKEv1]: Group = x.x.x.x, IP = x.x.x.x, Removing peer from correlator table failed, no match!
[IKEv1]: Group = x.x.x.x, IP = x.x.x.x, construct_ipsec_delete(): No SPI to identify Phase 2 SA!
[IKEv1]: Group = x.x.x.x, IP = x.x.x.x, Removing peer from correlator table failed, no match!
Verify Idle/Session Timeout
If the idle timeout is set to 30 minutes (default), it means that it drops the tunnel after 30 minutes of no traffic passes through it.
The VPN client gets disconnected after 30 minutes regardless of the idle timeout parameter and encounters thePEER_DELETE-IKE_DELETE_UNSPECIFIEDerror.
Configureidle timeoutandsession timeoutasnonein order to make the tunnel alwaysup, and so that the tunnel is never dropped even when third party devices are used.
ASA
Enter thevpn-idle-timeoutcommand in group-policy configuration mode or in username configuration mode in order to configure the user timeout period:
hostname(config)#group-policy DfltGrpPolicy attributes hostname(config-group-policy)#vpn-idle-timeout none
Configure a maximum amount of time for VPN connections with thevpn-session-timeoutcommand in group-policy configuration mode or in username configuration mode:
hostname(config)#group-policy DfltGrpPolicy attributes hostname(config-group-policy)#vpn-session-timeout none
When you havetunnel-allconfigured, you do not need to configureidle-timeoutbecause, even if you configure VPN-idle timeout, it does not work because all traffic goes through the tunnel (since tunnel-all is configured).
Therefore, the interesting traffic (or even the traffic generated by the PC) is interesting and does not let Idle-timeout come into action.
Cisco IOS® Router
Use thecrypto ipsec security-association idle-timecommand in global configuration mode or crypto map configuration mode in order to configure the IPsec SA idle timer.
By default IPsec SA idle timers are disabled.
crypto ipsec security-association idle-time seconds
Time is measured in seconds, which the idle timer allows an inactive peer to maintain an SA. Valid values for the seconds argument range from 60 to 86400.
Verify that ACLs are Correct and Binded to Crypto Map
There are two access lists used in a typical IPsec VPN configuration. One access list is used to exempt traffic that is destined for the VPN tunnel from the NAT process.
The other access list defines what traffic to encrypt; this includes a crypto ACL in a LAN-to-LAN setup or a split-tunnel ACL in a Remote Access configuration.
When these ACLs are incorrectly configured or missed, traffic perhaps flows in one direction across the VPN tunnel, or not sent across the tunnel at all.
Make sure to bind the crypto ACL with crypto map with the crypto map match address command in global configuration mode.
Be sure that you have configured all of the access lists necessary to complete your IPsec VPN configuration and that those access lists define the correct traffic.
This list contains simple things to check when you suspect that an ACL is the cause of problems with your IPsec VPN.
Make sure that your NAT Exemption and crypto ACLs specify the correct traffic.
If you have multiple VPN tunnels and multiple crypto ACLs, make sure that those ACLs do not overlap.
Make sure that your device is configured to use the NAT Exemption ACL. On a router, this means that you use theroute-mapcommand.
On the ASA, this means that you use thenat (0)command. A NAT exemption ACL is required for both LAN-to-LAN and Remote Access configurations.
Here, a Cisco IOS® router is configured to exempt traffic that is sent between192.168.100.0 /24and192.168.200.0 /24or192.168.1.0 /24from NAT. Traffic destined for anywhere else is subject to NAT overload:
access-list 110 deny ip 192.168.100.0 0.0.0.255 192.168.200.0 0.0.0.255 access-list 110 deny ip 192.168.100.0 0.0.0.255 192.168.1.0 0.0.0.255 access-list 110 permit ip 192.168.100.0 0.0.0.255 any route-map nonat permit 10 match ip address 110 ip nat inside source route-map nonat interface FastEthernet0/0 overload
NAT exemption ACLs work only with the IP address or IP networks, such as those examples mentioned (access-list noNAT), and must be identical to the crypto map ACLs.
The NAT exemption ACLs do not work with the port numbers (for instance, 23, 25,…).
In a VOIP environment, where the voice calls between networks are communicated through the VPN, the voice calls do not work if the NAT 0 ACLs are not properly configured.
Before troubleshooting, it is suggested to check the VPN connectivity status because the problem could be with misconfiguration of NAT exempt ACLs.
You can get the error message as shown if there is misconfiguration in NAT exemption (nat 0) ACLs.
%ASA-3-305005: No translation group found for udp src Outside:x.x.x.x/p dst Inside:y.y.y.y/p
Incorrect Example:
access-list noNAT extended permit ip 192.168.100.0 255.255.255.0 192.168.200.0 255.255.255.0 eq 25
If NAT exemption (nat 0) does not work, then try to remove it and issue theNAT 0command in order for it to work.
Make sure that your ACLs are not backwards and that they are the right type.
Crypto and NAT exemption ACLs for LAN-to-LAN configurations must be written from the perspective of the device on which the ACL is configured.
This means that the ACLs mustmirroreach other. In this example, a LAN-to-LAN tunnel is set up between192.168.100.0 /24and192.168.200.0 /24.
Router A crypto ACL
access-list 110 permit ip 192.168.100.0 0.0.0.255 192.168.200.0 0.0.0.255
Router B crypto ACL
access-list 110 permit ip 192.168.200.0 0.0.0.255 192.168.100.0 0.0.0.255
Although it is not illustrated here, this same concept applies to the ASA Security Appliances.
In ASA, split-tunnel ACLs for Remote Access configurations must bestandardaccess lists that permit traffic to the network to which the VPN clients need access.
Cisco IOS® routers can use extended ACL for split-tunnel. In the extended access list, to use‘any’at the source in the split tunnel ACL is similar to disable split tunnel.
Use only the source networks in the extended ACL for split tunnel.
Correct Example:
access-list 140 permit ip 10.1.0.0 0.0.255.255 10.18.0.0 0.0.255.255
Incorrect Example:
access-list 140 permit ip any 10.18.0.0 0.0.255.255
Cisco IOS®
router(config)#access-list 10 permit ip 192.168.100.0 router(config)#crypto isakmp client configuration group MYGROUP router(config-isakmp-group)#acl 10
Cisco ASA
securityappliance(config)#access-list 10 standard permit 192.168.100.0 255.255.255.0 securityappliance(config)#group-policy MYPOLICY internal securityappliance(config)#group-policy MYPOLICY attributes securityappliance(config-group-policy)#split-tunnel-policy tunnelspecified securityappliance(config-group-policy)#split-tunnel-network-list value 10
NAT exemption configuration in ASA version 8.3 for site-to-site VPN tunnel:
A site-to-site VPN has to be established between HOASA and BOASA with both ASAs with version 8.3. The NAT exemption configuration on HOASA looks similar to this:
object network obj-local subnet 192.168.100.0 255.255.255.0 object network obj-remote subnet 192.168.200.0 255.255.255.0 nat (inside,outside) 1 source static obj-local obj-local destination static obj-remote objremote
Verify the ISAKMP Policies
If the IPsec tunnel is not UP, check that the ISAKMP policies match with the remote peers. This ISAKMP policy is applicable to both the Site-to-Site (L2L) and Remote Access IPsec VPN.
If the Cisco VPN Clients or the Site-to-Site VPN are not able to establish the tunnel with the remote-end device, check thatthe two peers contain the same encryption, hash, authentication, and Diffie-Hellman parameter values.
Verify when the remote peer policy specifies a lifetime less than or equal to the lifetime in the policy that the initiator sent.
If the lifetimes are not identical, the security appliance uses the shorter lifetime. If no acceptable match exists, ISAKMP refuses negotiation, and the SA is not established.
"Error: Unable to remove Peer TblEntry, Removing peer from peer table failed, no match!"
Here is the detailed log message:
4|Mar 24 2010 10:21:50|713903: IP = X.X.X.X, Error: Unable to remove PeerTblEntry 3|Mar 24 2010 10:21:50|713902: IP = X.X.X.X, Removing peer from peer table failed, no match! 3|Mar 24 2010 10:21:50|713048: IP = X.X.X.X, Error processing payload: Payload ID: 1 4|Mar 24 2010 10:21:49|713903: IP = X.X.X.X, Information Exchange processing failed 5|Mar 24 2010 10:21:49|713904: IP = X.X.X.X, Received an un-encrypted NO_PROPOSAL_CHOSEN notify message, drop
This message usually appears due to mismatched ISAKMP policies or a missed NAT 0 statement.
In addition, this message appears:
Error Message %ASA-6-713219: Queueing KEY-ACQUIRE messages to be processed when P1 SA is complete.
This message indicates that Phase 2 messages are in the queue after Phase 1 completes. This error message is due to one of these reasons:
-
Mismatch in phase on any of the peers
-
ACL blocks the peers from completion of phase 1
This message usually comes after theRemoving peer from peer table failed, no match!error message.
If the Cisco VPN Client is unable to connect the head-end device, the problem can be the mismatch of ISAKMP Policy. The head-end device must match with one of theIKE Proposals of the Cisco VPN Client.
For the ISAKMP policy and IPsec Transform-set that is used on the ASA, the Cisco VPN client cannot use a policy with a combination of DES and SHA.
If you use DES, you need to use MD5 for the hash algorithm, or you can use the other combinations, 3DES with SHA and 3DES with MD5.
Verify that Routing is Correct
Be certain that your encryption devices such as Routers and ASA Security Appliances have the proper routing information to send traffic over your VPN tunnel.
If other routers exist behind your gateway device, be sure that those routers know how to reach the tunnel and what networks are on the other side.
One key component of routing in a VPN deployment is Reverse Route Injection (RRI).
RRI places dynamic entries for remote networks or VPN clients in the routing table of a VPN gateway.
These routes are useful to the device on which they are installed, as well as to other devices in the network because routes installed by RRI can be redistributed through a routing protocol such as EIGRP or OSPF.
In a LAN-to-LAN configuration, it is important for each endpoint to have a route or routes to the networks for which it is supposed to encrypt traffic.
In this example, Router A must have routes to the networks behind Router B through10.89.129.2. Router B must have a similar route to192.168.100.0 /24:
The first way to ensure that each router knows the appropriate route(s) is to configure static routes for each destination network. For example, Router A can have these route statements configured:
ip route 0.0.0.0 0.0.0.0 172.22.1.1 ip route 192.168.200.0 255.255.255.0 10.89.129.2 ip route 192.168.210.0 255.255.255.0 10.89.129.2 ip route 192.168.220.0 255.255.255.0 10.89.129.2 ip route 192.168.230.0 255.255.255.0 10.89.129.2
If Router A was replaced with a ASA, the configuration can look like this:
route outside 0.0.0.0 0.0.0.0 172.22.1.1 route outside 192.168.200.0 255.255.255.0 10.89.129.2 route outside 192.168.200.0 255.255.255.0 10.89.129.2 route outside 192.168.200.0 255.255.255.0 10.89.129.2 route outside 192.168.200.0 255.255.255.0 10.89.129.2
If a large number of networks exists behind each endpoint, the configuration of static routes becomes difficult to maintain.
Instead, it is recommended that you use Reverse Route Injection, as described. RRI places into the routing table routes for all of the remote networks listed in the crypto ACL.
For example, the crypto ACL and crypto map of Router A can look like this:
access-list 110 permit ip 192.168.100.0 0.0.0.255 192.168.200.0 0.0.0.255 access-list 110 permit ip 192.168.100.0 0.0.0.255 192.168.210.0 0.0.0.255 access-list 110 permit ip 192.168.100.0 0.0.0.255 192.168.220.0 0.0.0.255 access-list 110 permit ip 192.168.100.0 0.0.0.255 192.168.230.0 0.0.0.255 crypto map myMAP 10 ipsec-isakmp set peer 10.89.129.2 reverse-route set transform-set mySET match address 110
If Router A was replaced by ah ASA, the configuration can look like this:
access-list cryptoACL extended permit ip 192.168.100.0 255.255.255.0 192.168.200.0 255.255.255.0 access-list cryptoACL extended permit ip 192.168.100.0 255.255.255.0 192.168.210.0 255.255.255.0 access-list cryptoACL extended permit ip 192.168.100.0 255.255.255.0 192.168.220.0 255.255.255.0 access-list cryptoACL extended permit ip 192.168.100.0 255.255.255.0 192.168.230.0 255.255.255.0 crypto map myMAP 10 match address cryptoACL crypto map myMAP 10 set peer 10.89.129.2 crypto map myMAP 10 set transform-set mySET crypto map mymap 10 set reverse-route
In a Remote Access configuration, routing changes are not always necessary.
Yet, if other routers exist behind the VPN gateway router or Security Appliance, those routers need to learn the path to the VPN clients somehow.
In this example, suppose that the VPN clients are given addresses in the range of10.0.0.0 /24when they connect.
If no routing protocol is in use between the gateway and the other router(s), static routes can be used on routers such as Router 2:
ip route 10.0.0.0 255.255.255.0 192.168.100.1
If a routing protocol such as EIGRP or OSPF is in use between the gateway and other routers, it is recommended that Reverse Route Injection be used as described.
RRI automatically adds routes for the VPN client to the routing table of the gateway. These routes can then be distributed to the other routers in the network.
Cisco IOS® Router:
crypto dynamic-map dynMAP 10 set transform-set mySET reverse-route crypto map myMAP 60000 ipsec-isakmp dynamic dynMAP
Cisco ASA Security Appliance:
crypto dynamic-map dynMAP 10 set transform-set mySET crypto dynamic-map dynMAP 10 set reverse-route crypto map myMAP 60000 ipsec-isakmp dynamic dynMAP
The routing issue occurs if the pool of IP addresses assigned for the VPN clients are overlaps with internal networks of the head-end device. For further information, refer to theOverlapping Private Networkssection .
Verify that Transform-Set is Correct
Make sure that the IPsec encryption and hash algorithms to be used by the transform set on the both ends are the same.
Refer to theCommand referencesection of the Cisco Security Appliance configuration guide for more information.
For the ISAKMP policy and IPsec Transform-set that is used on the ASA, the Cisco VPN client cannot use a policy with a combination of DES and SHA.
If you use DES, you need to use MD5 for the hash algorithm, or you can use the other combinations, 3DES with SHA and 3DES with MD5.
Verify Crypto Map Sequence Numbers and Name and also that the Crypto map is applied in the right interface in which the IPsec tunnel start/end
If static and dynamic peers are configured on the same crypto map, the order of the crypto map entries is very important.
The sequence number of the dynamic crypto map entrymust behigher than all of the other static crypto map entries.
If the static entries are numbered higher than the dynamic entry, connections with those peers fail and the debugs as shown appears.
IKEv1]: Group = x.x.x.x, IP = x.x.x.x, QM FSM error (P2 struct &0x49ba5a0, mess id 0xcd600011)! [IKEv1]: Group = x.x.x.x, IP = x.x.x.x, Removing peer from correlator table failed, no match!
Only one Dynamic Crypto-map is allowed for each interface in the Security Appliance.
Here is an example of a properly numbered crypto map that contains a static entry and a dynamic entry. Note that the dynamic entry has the highest sequence number and room has been left to add additional static entries:
crypto dynamic-map cisco 20 set transform-set myset crypto map mymap 10 match address 100 crypto map mymap 10 set peer 172.16.77.10 crypto map mymap 10 set transform-set myset crypto map mymap interface outside crypto map mymap 60000 ipsec-isakmp dynamic ciscothe
Crypto map names are case-sensitive.
This error message can also be seen when the dynamic crypto man sequence is not correct which causes the peer to hit the wrong crypto map.
This is also caused by a mismatched crypto access list that defines the interesting traffic:%ASA-3-713042: IKE Initiator unable to find policy:
In a scenario where multiple VPN tunnels to be terminated in the same interface, create crypto map with same name (only one crypto map is allowed per interface) but with a different sequence number.
This holds true for the router, and ASA.
Similarly, refer toASA: Add a New Tunnel or Remote Access to an Existing L2L VPN — Ciscofor more information about the crypto map configuration for both the L2L and Remote Access VPN scenario.
Verify the Peer IP Address is Correct
Create and manage the database of connection-specific records for IPsec.
For a ASA Security Appliance LAN-to-LAN (L2L) IPsec VPN configuration, specify the<name>of the tunnel group as the Remote peer IP Address (remote tunnel end) in thetunnel-group <name> type ipsec-l2lcommand.
The peer IP address must match intunnel group nameand theCrypto map set addresscommands.
While you configure the VPN with ASDM, it generated the tunnel group name automatically with right peer IP address.
If the peer IP Address is not configured properly, the logs can contain this message, which can be resolved by proper configuration of thePeer IP Address.
[IKEv1]: Group = DefaultL2LGroup, IP = x.x.x.x, ERROR, had problems decrypting packet, probably due to mismatched pre-shared key. Aborting
When the peer IP address has not been configured properly on the ASA crypto configuration, the ASA is not able to establish the VPN tunnel and hangs in theMM_WAIT_MSG4stage only.
In order to resolve this issue, correct the peer IP address in the configuration.
Here is the output of theshow crypto isakmp sacommand when the VPN tunnel hangs at in the MM_WAIT_MSG4 state.
hostname#show crypto isakmp sa
1 IKE Peer: XX.XX.XX.XX
Type : L2L Role : initiator
Rekey : no State : MM_WAIT_MSG4
Verify the Tunnel Group and Group Names
%ASA-3-713206: Tunnel Rejected: Conflicting protocols specified by tunnel-group and group-policy
The message appears when a tunnel is dropped because the allowed tunnel specified in the group policy is different than the allowed tunnel in the tunnel-group configuration.
group-policy hf_group_policy attributes vpn-tunnel-protocol l2tp-ipsec username hfremote attributes vpn-tunnel-protocol l2tp-ipsec Both lines read: vpn-tunnel-protocol ipsec l2tp-ipsec
Enable IPSec In Default Group policy to the already Existing Protocols In Default Group Policy .
group-policy DfltGrpPolicy attributes vpn-tunnel-protocol L2TP-IPSec IPSec webvpn
Disable XAUTH for L2L Peers
If a LAN-to-LAN tunnel and a Remote Access VPN tunnel are configured on the same crypto map, the LAN-to-LAN peer is prompted for XAUTH information, and the LAN-to-LAN tunnel fails with «CONF_XAUTH» in the output of theshow crypto isakmp sacommand.
Here is an example of the SA output:
Router#show crypto isakmp sa IPv4 Crypto ISAKMP SA dst src state conn-id slot status X.X.X.X Y.Y.Y.Y CONF_XAUTH 10223 0 ACTIVE X.X.X.X Z.Z.Z.Z CONF_XAUTH 10197 0 ACTIVE
This issue only applies to Cisco IOS® whereas ASA is not affected by this issue since it uses tunnel-groups.
Use theno-xauthkeyword when you enter the isakmp key, so the device does not prompt the peer for XAUTH information (username and password).
This keyword disables XAUTH for static IPsec peers. Enter a command similar to this on the device that has both L2L and RA VPN configured on the same crypto map:
router(config)#crypto isakmp key cisco123 address 172.22.1.164 no-xauth
In the scenario where the ASA acts as the Easy VPN Server, the easy VPN client is unable to connect to head end because of the Xauth issue.
Disable the user authentication in the ASA in order to resolve the issue as shown:
ASA(config)#tunnel-group example-group type ipsec-ra ASA(config)#tunnel-group example-group ipsec-attributes ASA(config-tunnel-ipsec)#isakmp ikev1-user-authentication none
See theMiscellaneoussection of this document in order to know more about theisakmp ikev1-user-authenticationcommand.
VPN Pool Getting Exhausted
When the range of IP addresses assigned to the VPN pool are not sufficient, you can extend the availability of IP addresses in two ways:
-
Remove the existing range, and define the new range. Here is an example:
CiscoASA(config)#no ip local pool testvpnpool 10.76.41.1-10.76.41.254 CiscoASA(config)#ip local pool testvpnpool 10.76.41.1-10.76.42.254
-
When discontiguous subnets are to be added to the VPN pool, you can define two separate VPN pools and then specify them in order under the «tunnel-group attributes «. Here is an example:
CiscoASA(config)#ip local pool testvpnpoolAB 10.76.41.1-10.76.42.254 CiscoASA(config)#ip local pool testvpnpoolCD 10.76.45.1-10.76.45.254 CiscoASA(config)#tunnel-group test type remote-access CiscoASA(config)#tunnel-group test general-attributes CiscoASA(config-tunnel-general)#address-pool (inside) testvpnpoolAB testvpnpoolCD CiscoASA(config-tunnel-general)#exit
The order in which you specify the pools is very important because the ASA allocates addresses from these pools in the order in which the pools appear in this command.
The address-pools settings in the group-policy address-pools command always override the local pool settings in the tunnel-group address-pool command.
Issues with Latency for VPN Client Traffic
When there are latency issues over a VPN connection, verify these conditions in order to resolve this:
-
Verify if the MSS of the packet can be reduced further.
-
If IPsec/tcp is used instead of IPsec/udp, then configurepreserve-vpn-flow .
-
Re-load the Cisco ASA.
VPN Clients are Unable to Connect with ASA
Problem
Cisco VPN clients are unable to authenticate when the X-auth is used with the Radius server.
Solution
The problem can be that the xauth times out. Increase the timeout value for AAA server in order to resolve this issue.
For example:
Hostname(config)#aaa-server test protocol radius hostname(config-aaa-server-group)#aaa-server test host 10.2.3.4 hostname(config-aaa-server-host)#timeout 10
Problem
Cisco VPN clients are unable to authenticate when the X-auth is used with the Radius server.
Solution
Initially, make sure that the authentication works properly. To narrow down the problem, first verify the authentication with local database on ASA.
tunnel-group tggroup general-attributes
authentication-server-group none
authentication-server-group LOCAL
exit
If this works fine, then the problem is related to Radius server configuration.
Verify the connectivity of the Radius server from the ASA. If the ping works without any problem, then check the Radius-related configuration on ASA and database configuration on the Radius server.
You could use thedebug radiuscommand to troubleshoot radius related issues. For sampledebug radiusoutput, refer to thisSample Output.
Before you use thedebugcommand on the ASA, refer to this documentation:Warning message.
VPN Client Drops Connection Frequently on First Attempt or «Security VPN Connection terminated by peer. Reason 433.» or «Secure VPN Connection terminated by Peer Reason 433:(Reason Not Specified by Peer)»
Problem
Cisco VPN client users receive this error when they attempt the connection with the head end VPN device.
VPN client drops connection frequently on first attempt
Security VPN Connection terminated by peer. Reason 433.
Secure VPN Connection terminated by Peer Reason 433:(Reason Not Specified by Peer)
Attempted to assign network or broadcast IP address, removing (x.x.x.x) from pool
Solution 1
The problem can be with the IP pool assignment either through ASA, Radius server, DHCP server or through Radius server which acts as DHCP server.
Use thedebug cryptocommand in order to verify that the netmask and IP addresses are correct. Also, verify that the pool does not include the network address and the broadcast address.
Radius servers must be able to assign the proper IP addresses to the clients.
Solution 2
This issue also occurs due to the failure of extended authentication. You must check the AAA server to troubleshoot this error.
Check the server authentication password on Server and client. Reload the AAA server can resolve this issue.
Solution 3
Another workaround for this issue is to disable the threat detection feature.
At times when there are multiple re-transmissions for different incomplete Security Associations (SAs), the ASA with the threat-detection feature enabled thinks that a scanning attack occurred and the VPN ports are marked as the main offender.
Try to disable the threat-detection feature as this can cause a lot of overhead on the processing of ASA. Use these commands in order to disable the threat detection:
no threat-detection basic-threat no threat-detection scanning-threat shun no threat-detection statistics no threat-detection rate
This can be used as a workaround to verify if this fixes the actual problem.
Make sure that to disable the threat detection on the Cisco ASA actually compromises several security features such as mitigation of the Scanning Attempts, DoS with Invalid SPI, packets that fail Application Inspection , and Incomplete Sessions.
Solution 4
This issue also occurs when a transform set is not properly configured. A proper configuration of the transform set resolves the issue.
Remote Access and EZVPN Users Connect to VPN but Cannot Access External Resources
Problem
Remote access users have no Internet connectivity once they connect to the VPN.
Remote access users cannot access resources located behind other VPNs on the same device.
Remote access users can access only the local network.
Solutions
Try these solutions in order to resolve this issue:
-
Unable to Access the Servers in DMZ
-
VPN Clients Unable to Resolve DNS
-
Split-Tunnel—Unable to access Internet or excluded networks
-
Local LAN Access
-
Overlapping Private Networks
Unable to Access the Servers in DMZ
Once the VPN client is established the IPsec tunnel with the VPN head-end device (ASA / Cisco IOS® Router), the VPN client users are able to access the INSIDE network (10.10.10.0/24) resources, but they are unable to access the DMZ network (10.1.1.0/24).
Diagram
Check that the Split Tunnel, NO NAT configuration is added in the head-end device to access the resources in the DMZ network.
Example:
ASA configuration:
This configuration shows how to configure the NAT exemption for the DMZ network in order to enable the VPN users to access the DMZ network:
object network obj-dmz subnet 10.1.1.0 255.255.255.0 object network obj-vpnpool subnet 192.168.1.0 255.255.255.0 nat (inside,dmz) 1 source static obj-dmz obj-dmz destination static obj-vpnpool obj-vpnpool
After you add a new entry for the NAT configuration, clear the NAT translation.
Clear xlate Clear local
Verify:
If the tunnel has been established, go to theCisco VPN Clientand chooseStatus > Route Detailsto check that the secured routes are shown for both the DMZ and INSIDE networks.
Refer toASA: Add a New Tunnel or Remote Access to an Existing L2L VPN — Ciscofor steps required to add a new VPN tunnel or a remote access VPN to a L2L VPN configuration that already exists.
Refer toASA: Allow Split Tunneling for VPN Clients on the ASA Configuration Examplefor step-by-step instructions on how to allow VPN Clients access to the Internet while tunneled into a Cisco 5500 Series Adaptive Security Appliance (ASA).
VPN Clients Unable to Resolve DNS
After the tunnel has been established, if the VPN Clients are unable to resolve the DNS, the problem can be the DNS Server configuration in the head-end device (ASA).
Also check the connectivity between the VPN Clients and the DNS Server. The DNS Server configuration must be configured under the group policy and applied under the the group policy in the tunnel-group general attributes; for example:
!--- Create the group policy named vpn3000 and !--- specify the DNS server IP address(172.16.1.1) !--- and the domain name(cisco.com) in the group policy. group-policy vpn3000 internal group-policy vpn3000 attributes dns-server value 172.16.1.1 default-domain value cisco.com !--- Associate the group policy(vpn3000) to the tunnel group !--- with the default-group-policy. tunnel-group vpn3000 general-attributes default-group-policy vpn3000
VPN clients unable to connect internal servers by name
The VPN client is unable to ping the hosts or servers of the remote or head end internal network by name. You need to enable the split-dns configure on ASA in order to resolve this issue.
Split-Tunnel—Unable to access Internet or excluded networks
Split tunnel lets remote-access IPsec clients conditionally direct packets over the IPsec tunnel in encrypted form or to a network interface in cleartext form, decrypted, where they are routed to a final destination.
Split-tunnel is disabled by default, which istunnelalltraffic.
split-tunnel-policy {tunnelall | tunnelspecified | excludespecified}
The option excludespecified is supported only for Cisco VPN clients, not EZVPN clients.
ciscoasa(config-group-policy)#split-tunnel-policy excludespecified
Refer to these documents for detailed configuration examples of split-tunnel:
-
ASA: Allow Split Tunneling for VPN Clients on the ASA Configuration Example
-
Router Allows VPN Clients to Connect IPsec and Internet Using Split Tunneling Configuration Example
Hairpin solution
This feature is useful for VPN traffic that enters an interface but is then routed out of that same interface.
For example, in a hub and spoke VPN network, where the security appliance is the hub and remote VPN networks are spokes, spoke-to-spoke communication traffic must go into the security appliance and then out again to the other spoke.
Use thesame-security-trafficconfiguration to allow traffic to enter and exit the same interface.
securityappliance(config)#same-security-traffic permit intra-interface
Local LAN Access
Remote access users connect to the VPN and are able to connect to local network only.
For a more detailed configuration example, refer toASA: Allow local LAN access for VPN clients.
Overlapping Private Networks
Problem
If you are unable to access the internal network after the tunnel establishment, check the IP address assigned to the VPN client that overlaps with the internal network behind the head-end device.
Solution
Verify that the IP addresses in the pool to be assigned for the VPN clients, the internal network of the head-end device, and the VPN Client internal network, are in different networks.
You can assign the same major network with different subnets, but sometimes the routing issues occur.
For further examples, see theDiagramandExampleof theUnable to Access the Servers in DMZsection.
Unable to Connect More Than Three VPN Client Users
Problem
Only three VPN clients can connect to ASA/; connection for the fourth client fails. Upon failure, this error message is displayed:
Secure VPN Connection terminated locally by the client. Reason 413: User Authentication failed.
tunnel rejected; the maximum tunnel count has been reached
Solutions
In most cases, this issue is related to a simultaneous login setting within group policy and the maximum session-limit.
Try these solutions in order to resolve this issue:
-
Configure Simultaneous Logins
-
Configure the ASA with CLI
-
Configure Configure
Configure Simultaneous Logins
If theInheritcheck box in ASDM is checked, only the default number of simultaneous logins is allowed for the user. The default value for simultaneous logins is three (3).
In order to resolve this issue, increase the value for simultaneous logins.
-
Launch ASDM and then navigate toConfiguration > VPN > Group Policy.
-
Choose the appropriateGroupand click theEditbutton.
-
Once in theGeneraltab, undo theInheritcheck box forSimultaneous LoginsunderConnection Settings. Choose an appropriate value in the field.
The minimum value for this field is zero (0), which disables login and prevents user access.
When you log in with the same user account from a different PC, the current session (the connection established from another PC with the same user account) is terminated, and the new session is established.
This is the default behaviour and is independent to VPN simultaneous logins.
Configure the ASA with CLI
Complete these steps to configure the desired number of simultaneous logins. In this example, twenty (20) was chosen as the desired value.
ciscoasa(config)#group-policy Bryan attributes ciscoasa(config-group-policy)#vpn-simultaneous-logins 20
In order to learn more about this command, refer toCisco Security Appliance Command Reference.
Use thevpn-sessiondb max-session-limitcommand in global configuration mode in order to limit VPN sessions to a lower value than the security appliance allows.
Use thenoversion of this command in order to remove the session limit. Use the command again in order to overwrite the current setting.
vpn-sessiondb max-session-limit {session-limit}
This example shows how to set a maximum VPN session limit of 450:
hostname#vpn-sessiondb max-session-limit 450
Configure
Error Message
20932 10/26/2007 14:37:45.430 SEV=3 AUTH/5 RPT=1863 10.19.187.229 Authentication rejected: Reason = Simultaneous logins exceeded for user handle = 623, server = (none), user = 10.19.187.229, domain = <not specified>
Solution
Complete these steps in order to configure the desired number of simultaneous logins. You can also try to set the Simultaneous Logins to 5 for this SA:
ChooseConfiguration > User Management > Groups > Modify 10.19.187.229 > General > Simultaneous Logins, and change the number of logins to5.
Unable to Initiate the Session or an Application and Slow Transfer after the Tunnel Establishment
Problem
After the IPsec tunnel establishment, the application or the session does not initiate across the tunnel.
Solutions
Use thepingcommand to check the network or find whether the application server is reachable from your network.
It can be a problem with the maximum segment size (MSS) for transient packets that traverse a router or /ASA device, specifically TCP segments with the SYN bit set.
Cisco IOS® Router—Change the MSS Value in the Outside Interface (Tunnel End Interface) of the Router
Run these commands in order to change the MSS value in the outside interface (tunnel end interface) of the router:
Router>enable Router#configure terminal Router(config)#interface ethernet0/1 Router(config-if)#ip tcp adjust-mss 1300 Router(config-if)#end
These messages show the debug output for TCP MSS:
Router#debug ip tcp transactions Sep 5 18:42:46.247: TCP0: state was LISTEN -> SYNRCVD [23 -> 10.0.1.1(38437)] Sep 5 18:42:46.247: TCP: tcb 32290C0 connection to 10.0.1.1:38437, peer MSS 1300, MSS is 1300 Sep 5 18:42:46.247: TCP: sending SYN, seq 580539401, ack 6015751 Sep 5 18:42:46.247: TCP0: Connection to 10.0.1.1:38437, advertising MSS 1300 Sep 5 18:42:46.251: TCP0: state was SYNRCVD -> ESTAB [23 -> 10.0.1.1(38437)]
The MSS gets adjusted to 1300 on the router as configured.
For more information, refer toASA and Cisco IOS®: VPN Fragmentation.
ASA —Refer to /ASA Documentation
There is an inability to access the Internet properly or slow transfer through the tunnel because it gives the MTU size error message and MSS issues.
Refer to this document in order to resolve the issue:
Unable to Initiate VPN Tunnel from ASA
Problem
You are unable to initiate the VPN tunnel from ASA interface, and after the tunnel establishment, the remote end/VPN Client is unable to ping the inside interface of ASA on the VPN tunnel.
For example, the pn client can be unable to initiate a SSH or HTTP connection to ASAs inside interface over VPN tunnel.
Solution
The inside interface of the cannot be pinged from the other end of the tunnel unless themanagement-accesscommand is configured in the global configuration mode.
ASA-02(config)#management-access inside ASA-02(config)#show management-access management-access inside
This command also helps with ssh initiation or http connection to inside interface of ASA through a VPN tunnel.
This information holds true for DMZ interface as well. For example, if you want to ping the DMZ interface of /ASA or want to initiate a tunnel from DMZ interface, then themanagement-access DMZcommand is required.
ASA-02(config)#management-access DMZ
If the VPN client is unable to connect, then make sure ESP and UDP ports are open.
However, if those ports are not open, try to connect on TCP 10000 with the selection of this port under the VPN client connection entry.
Right clickmodify > transport tab > IPsec over TCP.
Unable to Pass Traffic Across VPN Tunnel
Problem
You are unable to pass traffic across a VPN tunnel.
Solution
This issue can also occur when the ESP packets are blocked. In order to resolve this issue, reconfigure the VPN tunnel.
This issue can occur when data is not encrypted, but only decrypted over the VPN tunnel as shown in this output:
ASA# sh crypto ipsec sa peer x.x.x.x
peer address: y.y.y.y
Crypto map tag: IPSec_map, seq num: 37, local addr: x.x.x.x
access-list test permit ip host xx.xx.xx.xx host yy.yy.yy.yy
local ident (addr/mask/prot/port): (xx.xx.xx.xx/255.255.255.255/0/0)
remote ident (addr/mask/prot/port): (yy.yy.yy.yy/255.255.255.255/0/0)
current_peer: y.y.y.y
#pkts encaps: 0, #pkts encrypt: 0, #pkts digest: 0
#pkts decaps: 393, #pkts decrypt: 393, #pkts verify: 393
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts comp failed: 0, #pkts decomp failed: 0
#pre-frag successes: 0, #pre-frag failures: 0, #fragments created: 0
#PMTUs sent: 0, #PMTUs rcvd: 0, #decapsulated frgs needing reassembly: 0
#send errors: 0, #recv errors: 0
In order to resolve this issue, check for these conditions:
-
If the crypto access-lists match with the remote site, and that NAT 0 access-lists are correct.
-
If routing is correct and traffic does hit outside interface which passes through inside. The sample output shows that decryption is done, but encryption does not occur.
-
If thesysopt permit connection-vpn command has been configured on the ASA. If not configured, configure this command because it allows the ASA to exempt the encrypted/VPN traffic from interface ACL Check.
Configure Backup peer for vpn tunnel on same crypto map
Problem
You want to use multiple backup peers for a single vpn tunnel.
Solution
The configuration of multiple peers is equivalent to the provision of a fallback list. For each tunnel, the security appliance attempts to negotiate with the first peer in the list.
If that peer does not respond, the security appliance works its way down the list until either a peer responds or there are no more peers in the list.
The ASA has a crypto map already configured as the primary peer. The secondary peer could be added after the primary one.
This example configuration shows the primary peer as X.X.X.X and backup peer as Y.Y.Y.Y:
ASA(config)#crypto map mymap 10 set peer X.X.X.X Y.Y.Y.Y
Disable/Restart VPN Tunnel
Problem
In order to temporarily disable the VPN tunnel and restart the service, complete the procedure described in this section.
Solution
Use thecrypto map interfacecommand in global configuration mode to remove a previously defined crypto map set to an interface.
Use thenoform of this command in order to remove the crypto map set from the interface.
hostname(config)#no crypto map map-name interface interface-name
This command removes a crypto map set to any active security appliance interface and make the IPsec VPN tunnel inactive in that interface.
To restart the IPsec tunnel on an interface, you must assign a crypto map set to an interface before that interface can provide IPsec services.
hostname(config)#crypto map map-name interface interface-name
Some Tunnels not Encrypted
Problem
When a huge number of tunnels are configured on the VPN gateway, some tunnels do not pass traffic. The ASA does not receive encrypted packets for those tunnels.
Solution
This issue occurs because the ASA fails to pass the encrypted packets through the tunnels. Duplicate encryption rules are created in the ASP table.
Error:- %ASA-5-713904: Group = DefaultRAGroup, IP = x.x.x.x, … unsupported Transaction Mode v2 version.Tunnel terminated.
Problem
The%ASA-5-713904: Group = DefaultRAGroup, IP = 192.0.2.0,… unsupported Transaction Mode v2 version.Tunnel terminatederror message appears.
Solution
The reason for theTransaction Mode v2error message is that ASA supports only IKE Mode Config V6 and not the old V2 mode version.
Use the IKE Mode Config V6 version in order to resolve this error.
Error:- %ASA-6-722036: Group client-group User xxxx IP x.x.x.x Transmitting large packet 1220 (threshold 1206)
Problem
The%ASA-6-722036: Group < client-group > User < xxxx > IP < x.x.x.x> Transmitting large packet 1220 (threshold 1206)error message appears in the logs of ASA.
What does this log means and how this can be resolved?
Solution
This log message states that a large packet was sent to the client. The source of the packet is not aware of the MTU of the client.
This can also be due to compression of non-compressible data. The workaround is to turn off the SVC compression with thesvc compression nonecommand, which resolves the issue.
Error Message when QoS is Enabled in one End of the VPN Tunnel
Problem
If you enabled QoS in one end of the VPN Tunnel, you can receive this error message:
IPSEC: Received an ESP packet (SPI= 0xDB6E5A60, sequence number= 0x7F9F) from 10.18.7.11 (user= ghufhi) to 172.16.29.23 that failed anti-replay check
Solution
This message is normally caused when one end of the tunnel performs QoS. This happens when a packet is detected as out of order.
You can disable QoS to stop this but it can be ignored as long as traffic is able to traverse the tunnel.
WARNING: crypto map entry incomplete
Problem
When you run thecrypto map mymap 20 ipsec-isakmpcommand, you can receive this error:
WARNING: crypto map entry incomplete
For example:
ciscoasa(config)#crypto map mymap 20 ipsec-isakmp WARNING: crypto map entry incomplete
Solution
This is a usual alert when you define a new crypto map; a reminder that parameters such as access-list (match address), transform set and peer address must be configured before it can work.
It is also normal that the first line you type in order to define the crypto map does not show in the configuration.
Error:- %ASA-4-400024: IDS:2151 Large ICMP packet from to on interface outside
Problem
Unable to pass large ping packet across the vpn tunnel. When we try to pass large ping packets we get the error%ASA-4-400024: IDS:2151 Large ICMP packet from to on interface outside.
Solution
Disable the signatures 2150 and 2151 in order to resolve this issue.Once the signatures are disabled ping works fine.
Use these commands in order to disable the signatures:
ASA(config)#ip audit signature 2151 disable
ASA(config)#ip audit signature 2150 disable
Error:- %ASA-4-402119: IPSEC: Received a protocol packet (SPI=spi, sequence number= seq_num) from remote_IP (username) to local_IP that failed anti-replay check.
Problem
I received this error in the log messages of the ASA:
Error:- %|ASA-4-402119: IPSEC: Received a protocol packet (SPI=spi, sequence number= seq_num) from remote_IP (username) to local_IP that failed anti-replay check.
Solution
In order to resolve this error, use thecrypto ipsec security-association replay window-sizecommand in order to vary the window size.
hostname(config)#crypto ipsec security-association replay window-size 1024
Cisco recommends that you use the full 1024 window size to eliminate any anti-replay problems.
Error Message — %ASA-4-407001: Deny traffic for local-host interface_name:inside_address, license limit of number exceeded
Problem
Few hosts are unable to connect to the Internet, and this error message appears in the syslog:
Error Message — %ASA-4-407001: Deny traffic for local-host interface_name:inside_address, license limit of number exceeded
Solution
This error message is received when the number of users exceeds the user limit of the license used. This error can be resolved by upgrade of the license to a higher number of users.
The user license can include 50, 100, or unlimited users as required.
Error Message — %VPN_HW-4-PACKET_ERROR:
Problem
TheError Message — %VPN_HW-4-PACKET_ERROR:error message indicates that ESP packet with HMAC received by the router are mismatched. This error can be caused by these issues:
-
Defective VPN H/W module
-
Corrupt ESP packet
Solution
In order to resolve this error message:
-
Ignore the error messages unless there is traffic disruption.
-
If there is traffic disruption, replace the module.
Error message: Command rejected: delete crypto connection between VLAN XXXX and XXXX, first.
Problem
This error message appears when you attempt to add an allowed VLAN on the trunk port on a switch:Command rejected: delete crypto connection between VLAN XXXX and VLAN XXXX, first..
The WAN edge trunk cannot be modified to allow additional VLANs. That is, you are unable to add VLANs in theIPSEC VPN SPAtrunk.
This command is rejected because it results in a crypto connected interface VLAN that belongs to the allowed VLAN list, which poses a potential IPSec security breach.
Note that this behavior applies to all trunk ports.
Solution
Instead of theno switchport trunk allowed vlan (vlanlist)command, use theswitchport trunk allowed vlan nonecommand or the»switchport trunk allowed vlan remove (vlanlist)»command.
Error Message — % FW-3-RESPONDER_WND_SCALE_INI_NO_SCALE: Dropped packet — Invalid Window Scale option for session x.x.x.x:27331 to x.x.x.x:23 [Initiator(flag 0,factor 0) Responder (flag 1, factor 2)]
Problem
This error occurs when you try to telnet from a device on the far end of a VPN tunnel or when you try to telnet from the router itself:
Error Message — % FW-3-RESPONDER_WND_SCALE_INI_NO_SCALE: Dropped packet — Invalid Window Scale option for session x.x.x.x:27331 to x.x.x.x:23 [Initiator(flag 0,factor 0) Responder (flag 1, factor 2)]
Solution
The user license can include 50, 100, or unlimited users as required. Window scale function was added to allow for rapid transmission of data on long fat networks (LFN).
These are typically connections with very high bandwidth, but also high latency.
Networks with satellite connections are one example of an LFN, since satellite links always have high propagation delays but typically have high bandwidth.
To enable window scale function to support LFNs, the TCP window size must be more than 65,535. This error message can be resolved if you increase the TCP window size to be more than 65,535.
%ASA-5-305013: Asymmetric NAT rules matched for forward and reverse . Please update this issue flows
Problem
This error message appears once the VPN tunnel comes up:
%ASA-5-305013: Asymmetric NAT rules matched for forward and reverse . Please update this issue flows
Solution
In order to resolve this issue when not on the same interface as the host with NAT, use the mapped address instead of the actual address to connect to the host.
In addition, enable theinspectcommand if the application embeds the IP address.
%ASA-5-713068: Received non-routine Notify message: notify_type
Problem
This error message appears if the VPN tunnel fails to come up:
%ASA-5-713068: Received non-routine Notify message: notify_type
Solution
This message occurs due to misconfiguration (that is, when the policies or ACLs are not configured to be the same on peers).
Once the policies and ACLs are matched the tunnel comes up without any problem.
%ASA-5-720012: (VPN-Secondary) Failed to update IPSec failover runtime data on the standby unit (or) %ASA-6-720012: (VPN-unit) Failed to update IPsec failover runtime data on the standby unit
Problem
One of these error messages appear when you try to upgrade the Cisco Adaptive Security Appliance (ASA):
%ASA-5-720012: (VPN-Secondary) Failed to update IPSec failover runtime data on the standby unit.
%ASA-6-720012: (VPN-unit) Failed to update IPsec failover runtime data on the standby unit.
Solution
These error messages are informative errors. The messages do not impact functionality of the ASA or the VPN.
These messages appear when the VPN failover subsystem cannot update IPsec-related runtime data because the related IPsec tunnel has been deleted on the standby unit.
In order to resolve these, issue thewr standbycommand on the active unit.
Error:- %ASA-3-713063: IKE Peer address not configured for destination 0.0.0.0
Problem
The %ASA-3-713063: IKE Peer address not configured for destination 0.0.0.0error message appears and the tunnel fails to come up.
Solution
This message appears when the IKE peer address is not configured for a L2L tunnel.
This error can be resolved if you change the sequence number of crypto map, then remove and reapply the crypto map.
Error: %ASA-3-752006: Tunnel Manager failed to dispatch a KEY_ACQUIRE message.
Problem
The%ASA-3-752006: Tunnel Manager failed to dispatch a KEY_ACQUIRE message.Probable mis-configuration of the crypto map or tunnel-group.»error message is logged on the Cisco ASA.
Solution
This error message can be caused by a misconfiguration of the crypto map or tunnel group. Ensure that both are configured properly. For more information about this error message, refer toError 752006 .
Here are some of the corrective actions:
-
Remove the crypto ACL (for example, associated to dynamic map).
-
Remove unused IKEv2 related configuration, if any.
-
Verify that the crypto ACL matched properly.
-
Remove duplicate access-list entries, if any.
Error: %ASA-4-402116: IPSEC: Received an ESP packet (SPI= 0x99554D4E, sequence number= 0x9E) from XX.XX.XX.XX (user= XX.XX.XX.XX) to YY.YY.YY.YY
In a LAN-to-LAN VPN tunnel setup, this error is received on one end ASA:
The decapsulated inner packet does not match the negotiated policy in the SA.
The packet specifies its destination as 10.32.77.67, its source as 10.105.30.1, and its protocol as icmp.
The SA specifies its local proxy as 10.32.77.67/255.255.255.255/ip/0 and its remote_proxy as 10.105.42.192/255.255.255.224/ip/0.
Solution
You need to verify the interesting traffic access-lists defined on both ends of the VPN tunnel. Both must match as exact mirror images.
Failed to launch 64-bit VA installer to enable the virtual adapter due to error 0xffffffff
Problem
TheFailed to launch 64-bit VA installer to enable the virtual adapter due to error 0xfffffffflog message is received when AnyConnect fails to connect.
Solution
Complete these steps in order to resolve this issue:
-
Go toSystem > Internet Communication Management > Internet Communication settingsand make sure thatTurn Off Automatic Root Certificates Updateis disabled.
-
If it is disabled, then disable the entireAdministrative Templatepart of the GPO assigned to the affected machine and test again.
Refer toTurn off Automatic Root Certificates Updatefor more information.
Cisco VPN Client Does Not Work with Data Card on Windows 7
Problem
Cisco VPN Client does not work with data card on Windows 7.
Solution
Cisco VPN Client installed on Windows 7 does not work with 3G connections since data cards are not supported on VPN clients installed on a Windows 7 machine.
Alert: «VPN functionality may not work at all»
Problem
During attempts to enable the isakmp on the outside interface of ASA, this alert message is received:
ASA(config)# crypto isakmp enable outside WARNING, system is running low on memory. Performance may start to degrade. VPN functionality may not work at all.
At this point, access to ASA through ssh. HTTPS is stopped and other SSL clients are also affected.
Solution
This problem is due to memory requirements by different modules such as logger and crypto.
Make sure you do not have thelogging queue 0command. It makes the queue size set to 8192 and the memory allocation increases.
In platforms such as ASA5505 and ASA5510, this memory allocation tends to memory-starve other modules.
IPSec Padding error
Problem
This error message is received:
%ASA-3-402130: CRYPTO: Received an ESP packet (SPI = 0xXXXXXXX, sequence number= 0xXXXX) from x.x.x.x (user= user) to y.y.y.y with incorrect IPsec padding
Solution
The issue occurs because the IPSec VPN negotiates without a hash algorithm. Packet hash ensures integrity check for the ESP channel.
Therefore, without hash, malformed packets are accepted undetected by the Cisco ASA and it attempts to decrypt these packets.
However, because these packets are malformed, the ASA finds flaws during packet decryption. This causes the padding error messages that are seen.
The recommendation is to include a hash algorithm in the transform set for the VPN and to ensure that the link between the peers has minimum packet malformation.
VPN tunnel gets disconnected after every 18 hours
Problem
The VPN tunnel gets disconnected after every 18 hours even though the lifetime is set for 24 hours.
Solution
The lifetime is the maximum time the SA can be used for rekey. The value you enter in the configuration as the lifetime is different from the rekey time of the SA.
Therefore, it is necessary to negotiate a new SA (or SA pair in the case of IPsec) before the current one expires.
The rekey time must always be smaller than the lifetime in order to allow for multiple attempts in case the first rekey attempt fails.
The RFCs do not specify how to calculate the rekey time. This is left to the discretion of the implementers.
Therefore, the time varies with platform. Some implementations can use a random factor to calculate the rekey timer.
For example, if the ASA initiates the tunnel, then it is normal that it rekeys at 64800 seconds = 75% of 86400.
If the router initiates, then the ASA can wait longer to give the peer more time to initiate the rekey.
Thus, it is normal that the VPN session gets disconnected every 18 hours to use another key for the VPN negotiation. This must not cause any VPN drop or problem.
Traffic flow is not maintained after the LAN to LAN tunnel is re-negotiated
Problem
Traffic flow is not maintained after the LAN to LAN tunnel is re-negotiated.
Solution
The ASA monitors every connection that passes through it and maintains an entry in its state table in accordance with the application inspection feature.
The encrypted traffic details that pass through the VPN are maintained in the form of a security association (SA) database. For LAN to LAN VPN connections, it maintains two different traffic flows.
One is the encrypted traffic between the VPN gateways. The other is the traffic flow between the network resource behind the VPN gateway and the end-user behind the other end.
When the VPN is terminated, the flow details for this particular SA are deleted.
However, the state table entry maintained by the ASA for this TCP connection becomes stale because of no activity, which hampers the download.
This means the ASA still retains the TCP connection for that particular flow while the user application terminates.
However, the TCP connections become stray and eventually timeout after the TCP idle-timer expires.
This problem has been resolved with the introduction of a feature called Persistent IPSec Tunneled Flows.
A new command,sysopt connection preserve-vpn-flows , has been integrated into the Cisco ASA in order to retain the state table information at the re-negotiation of the VPN tunnel.
By default, this command is disabled. To enable this, the Cisco ASA maintains the TCP state table information when the L2L VPN recovers from the disruption and re-establishes the tunnel.
Error message states that Bandwidth reached for the Crypto functionality
Problem
This error message is received on the 2900 Series Router:
Error: Mar 20 10:51:29: %CERM-4-TX_BW_LIMIT: Maximum Tx Bandwidth limit of 85000 Kbps reached for Crypto functionality with securityk9 technology package license.
Solution
This is a known issue that occurs because of the strict guidelines issued by the United States government.
In accordance, the securityk9 license can only allow a payload encryption up to rates close to 90Mbps and limit the number of encrypted tunnels/TLS sessions to the device.
For more information about the crypto export restrictions, refer toCisco ISR G2 SEC and HSEC Licensing.
In case of Cisco devices, it is derived to be less than 85Mbps unidirectional traffic in or out of the ISR G2 router, with a bidirectional total of 170 Mbps.
This requirement applies for the Cisco 1900, 2900, and 3900 ISR G2 platforms. This command helps to view these limitations:
Router#show platform cerm-information Crypto Export Restrictions Manager(CERM) Information: CERM functionality: ENABLED ---------------------------------------------------------------- Resource Maximum Limit Available ---------------------------------------------------------------- Tx Bandwidth(in kbps) 85000 85000 Rx Bandwidth(in kbps) 85000 85000 Number of tunnels 225 225 Number of TLS sessions 1000 1000 ---Output truncated----
To avoid this problem, purchase a HSECK9 license. An «hseck9» feature license provides enhanced payload encryption functionality with increased VPN tunnel counts and secure voice sessions.
For more information about Cisco ISR Router licensing, refer toSoftware Activation.
Problem: Outbound encryption traffic in an IPsec tunnel fails, even if inbound decryption traffic works.
Solution
This issue has been observed on an IPsec connection after multiple rekeys, but the trigger condition is not clear.
The presence of this issue can be established if you check the output of theshow asp dropcommand and verifying that the Expired VPN context counter increases for each outbound packet sent.
Miscellaneous
AG_INIT_EXCH Message Appears in the «show crypto isakmp sa» and «debug» Commands Output
If the tunnel does not get initiated, theAG_INIT_EXCHmessage appears in output of theshow crypto isakmp sacommand and indebugoutput as well.
The reason can be due to a mismatch of isakmp policies or if port udp 500 gets blocked on the way.
Debug Message «Received an IPC message during invalid state» Appears
This message is an informational message and has nothing to do with the disconnection of the VPN tunnel.
Related Information
- ASA and Cisco IOS®: VPN Fragmentation
- Cisco ASA 5500 Series Security Appliances
- IPsec Negotiation/IKE Protocols
- Technical Support & Documentation — Cisco Systems

When we talk about software and applications, we avoid using the phrase “ideal” for them. Even the best programs are susceptible to technical problems.
Furthermore, because these services would be provided over a network, it is impossible to predict when an error will occur.
VPN services and clients are a good way to create a second encrypted network to carry out online work and access blocked content anonymously, but they do not guarantee that you have a completely secure and impenetrable connection.
Cisco VPN client is one of the most personalized and widely used VPN clients. You may be familiar with the service if your job requires you to use a VPN to access multiple resources.
Cisco has a great interface and strong security protocols that aim to conceal your identity so you can work without being tracked. However, even though much of this client is protected and secured, you cannot guarantee error-free operation.
Cisco VPN, like other applications and services, has its fair share of issues that can get on your nerves at times. The “cisco VPN client error 433” is one of them.
This typically identifies as a runtime error and is common when you have a corrupted client, a virus attack, or due to active conflicting applications.
Runtime errors typically occur without warning, but you may be prompted by unexpected dialogue boxes appearing on your screen. To avoid further errors, try to resolve them as soon as possible.
Now we assume you’ve come here for the same reason: to read this article and find a solution that works. So, without further ado, let us look into this problem’s troubleshooting.
- Conflicting Application And Programs:
Your computer is a machine that is built to multitask. However, when two active programs with equal influence run concurrently, a runtime error occurs.
It is not always corrupted software that causes such error codes, but sometimes you have to start from the beginning because this is where the problem begins.
As a result, you will need to close any active programs that are interfering with the smooth operation of the VPN client. To do so, open the task manager by pressing Ctrl+Alt+Del at the same time.

When the task manager appears, it will display a list of programs that are currently running on your device. There will be multiple processes, so go to each one and end it by clicking the End button.
Check to see if the error dialogue box appears when you exit any process. If it doesn’t, you’ve successfully stopped a conflicting process.
- Reset Browser:
It is not always the application, but rather the browser you are using while connected to the VPN. In addition, if you are using a browser that is not working properly or has crashed, you will receive the runtime error.
As a result, a simple browser reset will suffice. You can access your computer’s control panel and navigate to the internet options. Click the Reset button in the advanced section to finish.
The exact procedure for resetting your browser may differ depending on the version of OS, so consult a manual to obtain the necessary settings.
- Free Memory On Your Computer:
A runtime error can occur when your device memory accumulates, resulting in a battle of resources for programs, so it is possible that your system has already accumulated excess storage and you need to free up some space for it to run smoothly.

Simply back up your files and delete them from your hard drive to free up space. Small bits of files can also accumulate over time, so it is best to clear the cache on your device and browser to free up storage.
Simply restart your computer after that. This will refresh the computer, resulting in improved performance and no runtime errors for your VPN service.
- Reinstall The Client:
Although the Cisco VPN client has a good performance-to-feature ratio, you can never guarantee the performance of a network-based application because it is prone to technical errors.
It’s possible that the VPN client encountered an error or a temporary glitch, resulting in the runtime error. A software failure can also cause your application to behave erratically, resulting in the 433 error code.
Reinstalling the client on your device is a good way to get rid of it. This way, any software crashes experienced by the Cisco VPN client will be addressed without complications.
If the service is corrupted, make sure to delete the cache and residual files as soon as you uninstall it. As a result, the next reinstallation is unaffected by the garbage resources on your computer.
- Reinstall Runtime Libraries:

Some packages are installed by your computer that is required for your programs to run. The runtime error will appear if you have an incomplete installation of these packages, such as MS Visual C++, on your computer.
As a result, it is critical to complete the installation of these packages so that the programs run smoothly. You can uninstall the package by going to the features of the program on your computer.
After removing the package, you can reinstall it. To ensure performance, make sure you download it from a reputable source such as Microsoft.
- Issues with the AAA server:
Another reason for the error is a problem with the AAA server. If authentication fails for this server, you will see the error 433 on your Cisco VPN client.
As a result, you must verify that the server has the correct password and is not experiencing any problems. A simple reloads to the server will resolve your issue by refreshing your connection.
- Update The Virus Program:

When the Cisco VPN client is compromised, you will typically receive the 433 error. A virus or a threat may cause your program to behave erratically.
As a result, you should check and update your virus protection software so that the threat is addressed and resolved as soon as possible before it causes harm to your system.
What is Error 433?
Error 433 is a kind of Runtime error that is found in the Microsoft Windows operating systems. The file can be found for Cisco VPN Client. Cisco Vpn Client Error 433 has a popularity rating of 1 / 10.
Errors
This tutorial contains information on Error 433 or otherwise known as Cisco Vpn Client Error 433. Errors such as Cisco Vpn Client Error 433 indicate your machine has faulty hardware or software that should be fixed when possible. Below is information on how to repair Error 433 and get your computer back to normal.
 Signs of Error 433:
Signs of Error 433:
- When your computer freezes or locks up at random.
- When your computer crashes when you are running Cisco VPN Client.
- If Cisco Vpn Client Error 433 pops up and causes a program to shutdown or your computer to crash.
- Your computer is running slow, taking a long time to boot up, and you suspect Error 433 by Cisco VPN Client is the cause.
What Causes Runtime Errors Like Error 433?
There are several causes of runtime errors like Cisco Vpn Client Error 433, such as viruses, out of date drivers, missing files or folders, incomplete or poor installation, and registry errors. They can also occur due to an issue with the computer’s memory, which may often be due to a hardware problem. In some cases there was an issue installing Cisco VPN Client and an error occurred.
 How to Fix Cisco Vpn Client Error 433
How to Fix Cisco Vpn Client Error 433
Follow the step by step instructions below to fix the Error 433 problem. We recommend you do each in order. If you wish to skip these steps because they are too time consuming or you are not a computer expert, see our easier solution below.
Step 1 — Uninstall and Reinstall Cisco VPN Client
If the Cisco Vpn Client Error 433 is a result of using Cisco VPN Client, you may want to try reinstalling it and see if the problem is fixed. Please follow these steps:
Windows XP
- Click “Start Menu”.
- Click “Control Panel”.
- Select the “Add or Remove” program icon.
- Find the Error 433 associated program.
- Click the Change/Remove button on the right side.
- The uninstaller pop up will give you instructions. Click “okay” or “next” or “yes” until it is complete.
- Reinstall the software.
Windows 7 and Windows Vista
- Click “Start Menu”.
- Click “Control Panel”.
- Click “Uninstall a Program” which is under the “Programs” header.
- Find the Error 433 associated program.
- Right click on it and select “Uninstall”.
- The uninstaller pop up will give you instructions. Click “okay” or “next” or “yes” until it is complete.
- Reinstall the software and run the program.
Windows 8, 8.1, and 10
- Click “Start Menu”.
- Click “Programs and Features”.
- Find the software that is linked to **insert file name**.
- Click Uninstall/Change.
- The uninstaller will pop up and give you instructions. Click “okay” and “next” until it is complete.
- Restart your computer.
- Reinstall the software and run the program.
Step 2 — Remove Registry Entry related to Error 433
 WARNING: Do NOT edit the Windows Registry unless you absolutely know what you are doing. You may end up causing more trouble than you start with. Proceed at your OWN RISK.
WARNING: Do NOT edit the Windows Registry unless you absolutely know what you are doing. You may end up causing more trouble than you start with. Proceed at your OWN RISK.
- Create a backup of registry files.
- Click “Start”.
- Type regedit, select it, and grant permission in order to proceed.
- Click HKEY LOCAL MACHINE>>SOFTWARE>>Microsoft>>Windows>>Current Version>>Uninstall.
- Find the Cisco Vpn Client Error 433 software from the list you wish to uninstall.
- Select the software and double click the UninstallString icon on the right side.
- Copy the highlighted text.
- Exit and go to the search field.
- Paste the data.
- Select Okay in order to uninstall the program.
- Reinstall the software.
Step 3 – Ensure Junk Isn’t Causing Cisco Vpn Client Error 433
Any space that isn’t regularly cleaned out tends to accumulate junk. Your personal computer is no exception. Constant web browsing, installation of applications, and even browser thumbnail caches slow down your device and in the absence of adequate memory, can also trigger a Cisco Vpn Client Error 433 error.
So how do you get around this problem?
- You can either use the Disk Cleanup Tool that comes baked into your Windows operating system.
- Or you can use a more specialized hard drive clean up solution that does a thorough job and flushes the most stubborn temporary files from your system.
Both solutions may take several minutes to complete the processing of your system data if you haven’t conducted a clean up in a while.
The browser caches are almost a lost cause because they tend to fill up quite rapidly, thanks to our constantly connected and on the go lifestyle.
Here’s how you can run the Window’s Disk Cleanup Tool, without performance issues or surprises.
- For Windows XP and Windows 7, the program can be ran from “Start” and from the “Command Prompt”.
- Click “Start”, go to All Programs > Accessories > System Tools, click Disk Cleanup. Next choose the type of files you wish to remove, click OK, followed by “Delete Files”.
- Open up the Command Prompt, type “c:windowscleanmgr.exe /d” for XP and “cleanmgr” for Windows 7. Finish by pressing “Enter”.
- For Windows 8 and Windows 8.1, the Disk Cleanup Tool can be accessed directly from “Settings”. Click “Control Panel” and then “Administrative Tools”. You can select the drive that you want to run the clean up on. Select the files you want to get rid of and then click “OK” and “Delete Files”.
- For Windows 10, the process is simplified further. Type Disk Cleanup directly in the search bar and press “Enter”. Choose the drive and then the files that you wish to wipe. Click “OK”, followed by “Delete Files”.
The progressive ease with which the Cleanup Tool can be used points to the growing importance of regularly deleting temporary files and its place in preventing Cisco Vpn Client Error 433.
 PRO TIP:
PRO TIP:
Remember to run the Disk Cleanup as an administrator.
Step 4 – Fix Infections and Eliminate Malware in Your PC
 How do you gauge if your system is infected with a malware and virus?
How do you gauge if your system is infected with a malware and virus?
Well, for one, you may find certain applications misbehaving.
And you may also see the occurrence of Error 433.
Infections and malware are the result of:
- Browsing the Internet using open or unencrypted public Wi-Fi connections
- Downloading applications from unknown and untrustworthy sources
- Intentional planting of viruses in your home and office networks
But thankfully, their impact can be contained.
- Enter “safe mode” by pressing the F8 key repeatedly when your device is restarting. Choose “Safe Mode with Networking” from the Advanced Boot Options menu.
- Back up all the data in your device to a secure location. This is preferably a storage unit that is not connected to your existing network.
- Leave program files as is. They are where the infection generally spreads from and may have been compromised.
- Run a thorough full-system scan or check of an on-demand scanner. If you already have an antivirus or anti-malware program installed, let it do the heavy lifting.
- Restart your computer once the process has run its course.
- Lastly, change all your passwords and update your drivers and operating system.
 PRO TIP: Are you annoyed by the frequent updates to your antivirus program? Don’t be! These regular updates add new virus signatures to your software database for exponentially better protection.
PRO TIP: Are you annoyed by the frequent updates to your antivirus program? Don’t be! These regular updates add new virus signatures to your software database for exponentially better protection.
Step 5 – Return to the Past to Eliminate Error 433
The steps outlined up until this point in the tutorial should have fixed Cisco Vpn Client Error 433 error. But the process of tracking what has caused an error is a series of educated guesses. So in case the situation persists, move to Step 5.
Windows devices give users the ability to travel back in time and restore system settings to an uncorrupted, error free state.
This can be done through the convenient “System Restore” program. The best part of the process is the fact that using System Restore doesn’t affect your personal data. There is no need to take backups of new songs and pictures in your hard drive.
- Open “Control Panel” and click on “System & Security”.
- Choose the option “System”.
- To the left of the modal, click on “System Protection”.
- The System Properties window should pop-up. You’ll be able to see the option “System Restore”. Click on it.
- Go with “Recommended restore” for the path of least hassles and surprises.
- Choose a system restore point (by date) that will guarantee taking your device back to the time when Error 433 hasn’t been triggered yet.
- Tap “Next” and wrap up by clicking “Finish”.
If you’re using Windows 7 OS, you can reach “System Restore” by following the path Start > All Programs > Accessories > System Tools.
Step 6 — Error 433 Caused by Outdated Drivers
Updating a driver is not as common as updating your operating system or an application used to run front-end interface tasks.
Drivers are software snippets in charge of the different hardware units that keep your device functional.
So when you detect an Cisco Vpn Client Error 433 error, updating your drivers may be a good bet. But it is time consuming and shouldn’t be viewed as a quick fix.
Here’s the step-by-step process you can go through to update drivers for Windows 8, Windows 8.1 and Windows 10.
- Check the site of your hardware maker for the latest versions of all the drivers you need. Download and extract them. We strongly advice going with original drivers. In most cases, they are available for free on the vendor website. Installing an incompatible driver causes more problems than it can ever fix.
- Open “Device Manager” from the Control Panel.
- Go through the various hardware component groupings and choose the ones you would like to update.
- On Windows 10 and Windows 8, right-click on the icon of the hardware you would like to update and click “Update Driver”.
- On Windows 7 and Vista, you right-click the hardware icon, choose “Properties”, navigate to the Driver panel, and then click “Update Driver”.
- Next you can let your device automatically search for the most compatible drivers, or you can choose to update the drivers from the versions you have on your hard drive. If you have an installer disk, then the latter should be your preferred course of action. The former may often get the driver selection incorrect.
- You may need to navigate a host of warnings from the Windows OS as you finalize the driver update. These include “Windows can’t verify that the driver is compatible” and “Windows can’t verify the publisher of this driver”. If you know that you have the right one in line, click “Yes”.
- Restart the system and hopefully the Cisco Vpn Client Error 433 error should have been fixed.
Step 7 – Call the Windows System File Checker into Action
 By now the Cisco Vpn Client Error 433 plaguing your device should have been fixed. But if you haven’t resolved the issue yet, you can explore the Windows File Checker option.
By now the Cisco Vpn Client Error 433 plaguing your device should have been fixed. But if you haven’t resolved the issue yet, you can explore the Windows File Checker option.
With the Windows File Checker, you can audit all the system files your device needs to operate, locate missing ones, and restore them.
Sound familiar? It is almost like “System Restore”, but not quite. The System Restore essentially takes you back in time to a supposedly perfect set up of system files. The File Checker is more exhaustive.
It identifies what is amiss and fills the gaps.
- First and foremost, open up an elevated command prompt.
- Next, if you are using Windows 8, 8.1 or 10, enter “DISM.exe /Online /Cleanup-image /Restorehealth” into the window and press Enter.
- The process of running the Deployment Image Servicing and Management (DISM) tool may take several minutes.
- Once it completes, type the following command into the prompt “sfc /scannow”.
- Your device will now go through all protected files and if it detects an anomaly, it will replace the compromised version with a cached version that resides at %WinDir%System32dllcache.
Step 8 – Is your RAM Corrupted? Find Out.
Is it possible? Can the memory sticks of your device trigger Error 433?
It is unlikely – because the RAM chips have no moving parts and consume little power. But at this stage, if all else has failed, diagnosing your RAM may be a good move.
You can use the Windows Memory Diagnostics Tool to get the job done. Users who are on a Linux or Mac and are experiencing crashes can use memtest86.
- Open up your device and go straight to the “Control Panel”.
- Click on “Administrative Tools”.
- Choose “Windows Memory Diagnostic”.
- What this built-in option does is it burns an ISO image of your RAM and boots the computer from this image.
- The process takes a while to complete. Once it is done, the “Status” field at the bottom of the screen populates with the result of the diagnosis. If there are no issues with your RAM/memory, you’ll see “No problems have been detected”.
One drawback of the Windows Memory Diagnostic tool pertains to the number of passes it runs and the RAM segments it checks.
Memtest86 methodically goes over all the segments of your memory – irrespective of whether it is occupied or not.
But the Windows alternative only checks the occupied memory segments and may be ineffective in gauging the cause of the Cisco Vpn Client Error 433 error.
Step 9 – Is your Hard Drive Corrupted? Find Out.
Your RAM or working memory isn’t the only culprit that may precipitate an Cisco Vpn Client Error 433 error. The hard drive of your device also warrants close inspection.
The symptoms of hard drive error and corruption span:
- Frequent crashes and the Blue Screen of Death (BSoD).
- Performance issues like excessively slow responses.
- Errors like Error 433.
Hard drives are definitely robust, but they don’t last forever.
There are three things that you can do to diagnose the health of your permanent memory.
- It is possible that your device may have a hard time reading your drive. This can be the cause of an Cisco Vpn Client Error 433 error. You should eliminate this possibility by connecting your drive to another device and checking for the recurrence of the issue. If nothing happens, your drive health is okay.
- Collect S.M.A.R.T data by using the WMIC (Windows Management Instrumentation Command-line) in the command prompt. To do this, simply type “wmic” into the command prompt and press Enter. Next follow it up with “diskdrive get status”. The S.M.A.R.T status reading is a reliable indicator of the longevity of your drive.
- Fix what’s corrupt. Let’s assume you do find that all isn’t well with your hard drive. Before you invest in an expensive replacement, using Check Disk or chkdsk is worth a shot.
- Open the command prompt. Make sure you are in Admin mode.
- Type “chkdsk C: /F /X /R” and press “Enter”. “C” here is the drive letter and “R” recovers data, if possible, from the bad sectors.
- Allow the system to restart if the prompt shows up.
- And you should be done.
These steps can lead to the resolution you’re seeking. Otherwise the Cisco Vpn Client Error 433 may appear again. If it does, move to Step 10.
Step 10 – Update Windows OS
 Like the software applications you use to render specific tasks on your device, the Operating System also requires periodic updates.
Like the software applications you use to render specific tasks on your device, the Operating System also requires periodic updates.
Yes, we’ve all heard the troubling stories.
Devices often develop problems post unfinished updates that do not go through. But these OS updates include important security patches. Not having them applied to your system leaves it vulnerable to viruses and malware.
And may also trigger Error 433.
So here’s how Windows 7, Windows 8, Windows 8.1 and Windows 10 users can check for the latest updates and push them through:
- Click the “Start” button on the lower left-hand corner of your device.
- Type “Updates” in the search bar. There should be a “Windows Update” or “Check for Updates” option, based on the OS version you’re using.
- Click it. The system will let you know if any updates are available.
- You have the convenience of choosing the components of the update you’d like to push through. Always prioritize the security updates.
- Click “OK” followed by “Install Updates”.
Step 11 – Refresh the OS to Eliminate Persistent Cisco Vpn Client Error 433 Error
“Windows Refresh” is a lifesaver.
For those of you who are still with us and nothing has worked to eliminate the Error 433, until recently, a fresh install of Windows would have been the only option.
Not anymore.
The Windows Refresh is similar to reinstalling your Windows OS, but without touching your personal data. That’s hours of backup time saved in a jiffy.
Through the Refresh, all your system files become good as new. The only minor annoyance is the fact that any custom apps you’ve installed are gone and the system applications you had uninstalled are back.
Still, it is the best bet as the final step of this process.
- Enter the “Settings” of your PC and click on “Change Settings”.
- Click “Update and recovery” and then choose “Recovery”.
- Select “Keep my files”. This removes apps and settings, but lets your personal files live on.
- You’ll get some warning messages about the apps that will be uninstalled. If you’ve gone through a recent OS upgrade, the Refresh process makes it so that you can’t go back to your previous OS version – if you should ever feel the need to do it.
- Click the “Refresh” button.
Are you using an older version of Windows that doesn’t come with the power to “Refresh”?
Maybe it is time to start from scratch.
- Enter your BIOS set-up.
- This is where you need to change your computer’s boot order. Make it so that the boot happens not from the existing system files, but from the CD/DVD Drive.
- Place the original Windows disk in the CD/DVD drive.
- Turn on or restart the device.
- Choose where you’d like the system files to be installed.
- Your PC will restart several times as the process runs its course.
FAQ’s
What are Runtime Errors?
A runtime error, also often known as a program error, occurs while the program is active and running. The result of the error may lead to a program crash. However, there are other types of similar program errors such as logic errors and memory leaks. More commonly known as bugs, such errors are usually identified during the debugging process.
Should I Bring My Computer to the Repair Shop if There are Runtime Errors Like Error 433?
You can bring it to the repair shop but they will charge you a lot more than trying to fix it on your own or by using a specialized repair software. We would recommend trying some of the DIY ideas first such as diagnosing the problem and then working backwards from there. For example, if a specific program is causing it, try reinstalling the program. If that doesn’t work, try using a software to diagnose the errors on your system. As a last recourse, you can bring it to the repair shop.
Should I Update My Drivers if There are Runtime Errors Like Error 433?
Drivers are a piece of software that the computer uses to communicate properly with the hardware and to Windows. When they can no longer communicate, such as when faulty or old, this can cause many different errors — Runtime Errors included. If you are experiencing problems like Error 433, we do recommend keeping your drivers updated.
![]()
Start Download Now
Author:

Curtis Hansen has been using, fiddling with, and repairing computers ever since he was a little kid. He contributes to this website to help others solve their computer issues without having to buy a new one.
