mstscax.dll error and 0x80071779 in Windows 10 usually occur in version 1803. The Windows 10 April 2018 Update contains several problems in network and RDP connections. It appears that there is no NIC adapter binding for the network that can be uninstalled through GUI. However, you can get rid of mstscax.dll error and 0x80071779 in Windows 10 pretty easily.
When users make an attempt to uninstall the client for Microsoft networks in the properties of a network adapter, they come across an Error Code 0x80071779. Whereas mstscax.dll message may show while using Remote Desktop Protocol for remote connections in Windows 10. However, Microsoft mentioned mstscax.dll error and 0x80071779 problems in KB articles along with their solutions.
Error 0x80071779 in Windows 10
When the administrator of Windows 10 version 1803 based device tries to uninstall the client for Microsoft networks through the network properties, they come across this specific issue. Probably a few numbers of users may need to perform this uninstallation in order to remove Microsoft networks.
Fix Through PowerShell
You can use the PowerShell cmdlet Disable-NetAdapterBinding to dispel the protocol. Here is the procedure –
Step-1: Make a joint press of Win+X in order to open Power user menu.
Step-2: Select “Windows PowerShell (Admin)” from the visible list and when a UAC appears, do a click on Yes to continue.
Explore more ways to Run PowerShell as administrator in Windows 10.
Step-3: Now type in the following command after the blinking cursor and then hit Enter.
Get-NetAdapterBinding
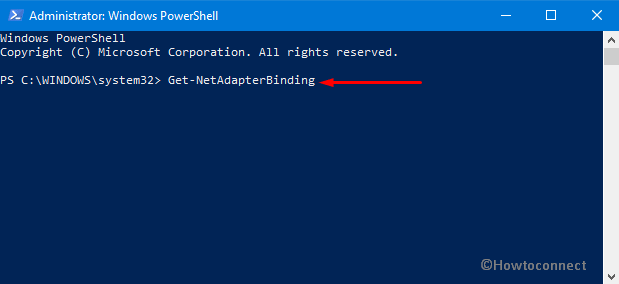
This command will list all adapter bindings where ms_msclient specifies Microsoft client and ms_pacer addresses the QoS packet planner.
Step-4: Moving ahead, type the below-given command in PowerShell and press Enter in order to delete a network protocol.
Disable-NetAdapterBinding -Name „Ethernet0“ -ComponentID ms_msclient
Note- To complete the process perfectly make sure you have put your Network name in the place of Ethernet0.
mstscax.dll Error in Windows 10
As mentioned above, this error shows up while using Remote Desktop Protocol (in short RDP) for remote connections in Windows 10. This error also seems to appear after the installation of an update such as KB4284835.
Furthermore, this problem comes up on PCs where mstsc.exe and mstxcax.dll files were replaced with a previous version of these files. Replacing them from earlier versions of the OS fails to support and thus lead to an unexpected behavior. And as a result, when users make an attempt to install future updates (KB4284835), file mismatch error occurs.
Hence, to resolve it, go through the below-given sequence of steps.
Step-1: At first, take ownership of your PC. And then provide full authorization to mstscax.dll and mstsc.exe files respectively.
Step-2: Uninstall the update that is causing this issue which is probably KB4284835.
Step-3: Processing forward, restore original Windows 10 files (mstsc.exe and mstscax.dll) to the following folder.
%windir%system32
Step-4: After successfully restoring the files, restart Windows 10 PC.
Step-5: Next, Reinstall the update again.
Step-6: Finally, again Reboot your computer once again in order to finish the process.
That’s all. Hopefully, you have resolved the issue already. If you have any question, don’t hesitate to ask.
Repair any Windows problems such as Blue/Black Screen, DLL, Exe, application, Regisrty error and quickly recover system from issues using Reimage.
Error 0x80071779 in Windows 10 is usually found in version 1803. Windows contains a problem with network connections. For users of the network adapter, they are faced with the error code 0x80071779. For Microsoft networks.
How To Fix Component Error 0x80071779 For Networks In Windows 10
You will receive an error 0x80071779. Let’s see it below.
Related :
HOW TO FIX ERROR 0X80070017 IN WINDOWS 10
You can use PowerShell to remove the protocol.
Step 1. Click the Win + X key combination and select “Windows PowerShell (Administrator)”.
Step 2. Now enter the command below and press Enter.
Get-NetAdapterBinding
Step 3. This command will show you your network adapters and client for Microsoft networks (ms_msclient). You have the same as I may have a lot of connections, remember your main connection or the one in which you want to uninstall the client for Microsoft networks. In my case, this is Ethernet0.
Step 4. To remove the network protocol, enter another command. Replace the Ethernet command with your own if you have a different adapter.
Disable-NetAdapterBinding -Name “Ethernet” -ComponentID ms_msclient
Back to top button

- Remove From My Forums
-
Question
-
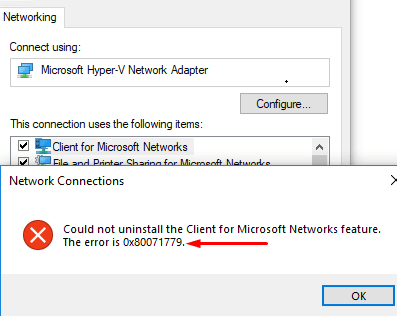
When trying to uninstall protocols from adapter, I get the error below.
Could not uninstall the Client for Microsoft Networks feature.
The error is 0x80071779
I have uninstalled all the adapters, reset winsock…
I am running Microsoft Windows [Version 10.0.17134.1]
-
Edited by
rbcarra
Thursday, April 19, 2018 3:38 AM
-
Edited by
All replies
-
Hi rbcarra,
Based on my test, yes and I can reproduce your problem.
It can be uninstalled on previous version, like Windows 10 1709, Windows 10 1607 etc. But when I uninstall it on Windows 10 1803, the result is same as yours:
And I capture the activity on Windows 10 1709 and Windows 10 1803, nothing can be found:
I will submit this feedback via our own channel. It’s also recommend you submit it via built-in Feedback app. If any update, I will post here.
Please remember to mark the replies as answers if they help.
If you have feedback for TechNet Subscriber Support, contact
tnmff@microsoft.com.-
Proposed as answer by
Karen_HuMicrosoft contingent staff
Monday, April 23, 2018 8:11 AM
-
Proposed as answer by
-
Same here. Upgrade or even fresh install of 1803 borks this feature.
-
Hello,
Why would we need to remove the Client for Microsoft Networks?
Thanks, Darrell Gorter [MSFT] This posting is provided «AS IS» with no warranties, and confers no rights.
-
It is unspecific to the protocol. You cannot remove any protocol at the moment.
-
Hi rbcarras,
Try to change the TCP/IP properties in the Registry with the following path:
[HKEY_LOCAL_MACHINESOFTWAREMicrosoftMicrosoft SQL ServerMSSQL11.SQL2012MSSQLServerSuperSocketNetLibTcp]
Momominta
What if i don’t even have this entry?
-
I agree that the message box could be a lot better here. We’ll look into that for the next release.
Blocking uninstallation of inbox drivers is by design, however. We do not support using this UI to remove built-in drivers. We don’t test in that configuration, and we know that uninstalling drivers breaks things.
As you’ve probably already noticed, uninstalling a driver from this UI was never permanent. E.g., if you uninstalled a driver from Windows 7, then upgraded to Windows 8, it would get reinstalled. Maybe more disconcertingly, a monthly security
update that affected that particular driver could reinstall it. The reason is that the OS’s servicing stack isn’t really aware of this UI, and doesn’t realize when this UI is removing drivers. The OS’s servicing stack will reinstall the driver
any time the driver is serviced.There’s some advice circulating the Internet to uninstall the «Multiplexor» driver. This is bad advice: it buys you nothing, since the multiplexor doesn’t even get loaded in memory unless you need it for a bridge or LBFO team.
And if you uninstall it, bridges and teams will be permanently broken. We’ve gotten support requests from quite a few customers who inadvertently damaged their systems by uninstalling drivers, and need help putting it back together. In Windows
10 1803, we block attempts to damage the system.Some of the built-in drivers can be uninstalled as part of a larger «optional feature». For example, you can get rid of the Virtual Switch driver by uninstalling the Hyper-V, WDAG, and Containers optional features. Optional features
are indeed supported and we do test the OS with the feature removed.If there are specific drivers that you would like to be removable, but which are not currently part of an Optional Feature, please file a feature request in the Feedback Hub.
Please note that you can always unbind the driver from any/all NICs, either using this GUI or using the PowerShell cmdlet «Disable-NetAdapterBinding». The only change is that you can’t deregister the OS driver entirely. But if you unbind
the driver from all your NICs, it’s effectively the same as uninstalling the driver.Also note that 3rd party drivers can still be installed & uninstalled (or bound/unbound) from this GUI. The change only affects the drivers that are part of the OS.
-
Hello,
Why would we need to remove the Client for Microsoft Networks?
Thanks, Darrell Gorter [MSFT] This posting is provided «AS IS» with no warranties, and confers no rights.
We want remove «Client for Microsoft Networks», LLDP and many others ’cause they are unnecessary to system operation specially on
public networks and machines that access many unknown networks… -
Uninstalling all items for my connection but TCP/IPv4 never broke anything for me on a stand alone system.
You guys force way to much to be installed on Windows pr. default and preventing uninstallation on top is just a silly move.
Regards Joerg Baermann
-
Proposed as answer by
krakdcorn
Sunday, November 18, 2018 6:23 PM
-
Proposed as answer by
-
You can always unbind these drivers — just uncheck the box next to its name. Unbinding the driver will 100% prevent it from communicating on that network.
-
We do not support using this UI to remove built-in Drivers.
Since when ? — You have this UI with the Option to install/remove Protocols, inside Windows for almost 30 Years !!! — Not sure, if it was there in Windows 3.11 but Windows 95 got it… — Even some external Network/Wlan protocols, work with exactly this Panel!
— Are you sure, you speak for the whole MS-Company, when you say, you just drop the support, for Network Protocol, de-install, re-install, install, cause one update broke it ?-
Edited by
Beschwerde
Sunday, May 13, 2018 7:29 PM
-
Edited by
-
There’s some advice circulating the Internet to uninstall the «Multiplexor» driver. This is bad advice: it buys you nothing, since the multiplexor doesn’t even get loaded in memory unless you need it for a bridge or
LBFO team. …Why is this even on the client SKU as NIC teams are not supported on client SKUs ?
-
I recall an advanced Windows NT course where we taught unbinding protocols to a NIC in order to lock down a machine. Part of the Microsoft curriculum taught how to take it a step further and actually uninstall the protocols. This was back in the late 1990’s!
Given the advancements in technology since then and even greater cyber threats of today, why in the world would Microsoft ever prevent us from uninstalling a protocol if we didn’t want it there? This is a huge problem. -
A little workaround I did to fix this «little bug». I have services like Server and
Workstation disabled (plus a few other things), that should take care of the «Client for Microsoft Network» and «File and Printer Sharing». As for the rest, disabling the driver should prevent them from working.rem Link-Layer Topology Discovery Responder / Default - 2 reg add "HKLMSystemCurrentControlSetServicesrspndr" /v "Start" /t REG_DWORD /d "4" /f rem Link-Layer Topology Discovery Mapper I/O Driver / Default - 2 reg add "HKLMSystemCurrentControlSetServiceslltdio" /v "Start" /t REG_DWORD /d "4" /f rem Microsoft LLDP Protocol Driver / Default - 2 reg add "HKLMSystemCurrentControlSetServicesMsLldp" /v "Start" /t REG_DWORD /d "4" /f rem Microsoft Virtual Network Adapter Enumerator / Default - 3 reg add "HKLMSystemCurrentControlSetServicesNdisVirtualBus" /v "Start" /t REG_DWORD /d "4" /f rem QoS for storage I/O traffic / Default - 2 reg add "HKLMSystemCurrentControlSetServicesstorqosflt" /v "Start" /t REG_DWORD /d "4" /f rem QoS Multimeda Class Scheduler / Default - 2 reg add "HKLMSystemCurrentControlSetServicesMMCSS" /v "Start" /t REG_DWORD /d "4" /f rem QoS Packet Scheduler / Default - 1 reg add "HKLMSystemCurrentControlSetServicesPsched" /v "Start" /t REG_DWORD /d "4" /f rem Named pipe service trigger provider / Default - 1 rem https://msdn.microsoft.com/en-us/library/windows/desktop/aa365590(v=vs.85).aspx reg add "HKLMSystemCurrentControlSetServicesnpsvctrig" /v "Start" /t REG_DWORD /d "4" /f rem NetBIOS Interface / Default - 1 reg add "HKLMSystemCurrentControlSetServicesNetBIOS" /v "Start" /t REG_DWORD /d "4" /f rem NetBIOS over TCP/IP / Default - 1 reg add "HKLMSystemCurrentControlSetServicesNetBT" /v "Start" /t REG_DWORD /d "4" /f rem Remote Desktop Device Redirector Bus Driver / Default - 3 reg add "HKLMSystemCurrentControlSetServicesrdpbus" /v "Start" /t REG_DWORD /d "4" /f rem The framework for network mini-redirectors / Default - 1 rem https://docs.microsoft.com/en-us/windows-hardware/drivers/ifs/the-redirected-drive-buffering-subsystem reg add "HKLMSystemCurrentControlSetServicesrdbss" /v "Start" /t REG_DWORD /d "4" /f rem A little bonus - Disable IPv6/LMHOSTS lookup/NetBIOS and Set DNS Servers netsh int ipv6 isatap set state disabled netsh int teredo set state disabled netsh interface ipv6 6to4 set state state=disabled undoonstop=disabled reg add "HKLMSystemCurrentControlSetServicesTcpip6Parameters" /v "DisabledComponents" /t REG_DWORD /d "255" /f wmic nicconfig where DHCPEnabled=TRUE call SetDNSServerSearchOrder ("1.1.1.1") reg add "HKLMSystemCurrentControlSetServicesNetBTParameters" /v "EnableLMHOSTS" /t REG_DWORD /d "0" /f wmic nicconfig where TcpipNetbiosOptions=0 call SetTcpipNetbios 2 wmic nicconfig where TcpipNetbiosOptions=1 call SetTcpipNetbios 2-
Edited by
TairikuOkami
Saturday, June 9, 2018 12:08 PM
-
Edited by
-
‘ We don’t test in that configuration’ — very sad. Maybe misleading. Inconsistent. Slightly arrogant.
It is not just ‘protocols’. It includes ‘service’ and ‘client’ network features.
In the past some of these were not uninstallable. And when you tried to uninstall the button to do so was greyed out. Now items that in the past were uninstallable are not, the uninstall button does not grey out, and you get a silly
error message.Someone dropped the ball at Microsoft. Seems to happen a lot.
Stan
-
Well said, like DNS Cache service for example, which can be disabled only via registry,, ofr now. Disabling it increases security by decreasing the attack surface on the client’s side, like DNS poisoning. DNS malware/attacks are on the rise. I disable it
plus I use dnscrypt with DNSSEC servers.-
Edited by
TairikuOkami
Saturday, June 9, 2018 3:43 PM
-
Edited by
-
Hi rbcarra,
Based on my test, yes and I can reproduce your problem.
It can be uninstalled on previous version, like Windows 10 1709, Windows 10 1607 etc. But when I uninstall it on Windows 10 1803, the result is same as yours:
And I capture the activity on Windows 10 1709 and Windows 10 1803, nothing can be found:
I will submit this feedback via our own channel. It’s also recommend you submit it via built-in Feedback app. If any update, I will post here.
Please remember to mark the replies as answers if they help.
If you have feedback for TechNet Subscriber Support, contact
tnmff@microsoft.com.Have a look at this kb article — maybe the PowerShell workaround helps.
1. Press Windows + X and invoke PowerShell console
2. Enter Get-NetAdapterBinding and press Enter
This lists all bindings of your network
3. Enter the following command to remove a binding
Disable-NetAdapterBinding -Name „Ethernet0“ -ComponentID ms_msclient
Ethernet0 is the placeholder for your network adapter. Instead of ms_msclient you need to identify the component ID returned by Get-NetAdapterBinding and press Enter. QoS is ms_pacer imho.HTP
Gruß/greetings G. Born — Blogs: http://www.borncity.com/blog (Ger) — http://www.borncity.com/win (EN)
-
Edited by
Günter BornMVP
Tuesday, June 26, 2018 1:38 PM
added the PS commands
-
Edited by
-
This is part of some workaround here: https://blog.olandese.nl/2017/05/03/solve-docker-for-windows-error-a-firewall-is-blocking-file-sharing-between-windows-and-the-containers/
So by breaking existing functionality, you also broke workaround. Not cool.
-
Public KB
Error 0x80071779 when removing network components in Windows 10, version 1803
https://support.microsoft.com/en-us/help/4340181/ -
Some of the built-in drivers can be uninstalled as part of a larger «optional feature». For example, you can get rid of the Virtual Switch driver by uninstalling the Hyper-V
Wrong. I’ve uninstalled Hyper-V feature but it didn’t remove neither Hyper-V adapters nor v-switch driver from the OS. I’ve managed to remove NICs manually but can’t uninstall v-switch driver because of this error. There should be some solution to purge
this garbage from the system. -
I been a whole week that I’m trying to fix this, I got screwed using this garbage hyper-v that can not be cleaned from my computer, effectively wrecking any chance of using virtual-box. MS should get a damn checklist and work by it instead of half-fixing
old issues. -
Also trying to use the Docker workaround. Tried Gunter Born’s approach to disable and then re-enable the binding. Sadly did not work.
-
I have tried many of the above suggestions on Windows 10 Pro and no luck.
I have tried using the disable-netadapterbinding on the file and print sharing service for the particular network but after that when i tried to install it again it doesn’t show up in the list as a service to pick.
Also just tried the disable then enable netadapterbinding command and that didn’t work either.
Any other ideas?

- Remove From My Forums
-
Question
-
When trying to uninstall protocols from adapter, I get the error below.
Could not uninstall the Client for Microsoft Networks feature.
The error is 0x80071779
I have uninstalled all the adapters, reset winsock…
I am running Microsoft Windows [Version 10.0.17134.1]
-
Edited by
rbcarra
Thursday, April 19, 2018 3:38 AM
-
Edited by
All replies
-
Hi rbcarra,
Based on my test, yes and I can reproduce your problem.
It can be uninstalled on previous version, like Windows 10 1709, Windows 10 1607 etc. But when I uninstall it on Windows 10 1803, the result is same as yours:
And I capture the activity on Windows 10 1709 and Windows 10 1803, nothing can be found:
I will submit this feedback via our own channel. It’s also recommend you submit it via built-in Feedback app. If any update, I will post here.
Please remember to mark the replies as answers if they help.
If you have feedback for TechNet Subscriber Support, contact
tnmff@microsoft.com.-
Proposed as answer by
Karen_HuMicrosoft contingent staff
Monday, April 23, 2018 8:11 AM
-
Proposed as answer by
-
Same here. Upgrade or even fresh install of 1803 borks this feature.
-
Hello,
Why would we need to remove the Client for Microsoft Networks?
Thanks, Darrell Gorter [MSFT] This posting is provided «AS IS» with no warranties, and confers no rights.
-
It is unspecific to the protocol. You cannot remove any protocol at the moment.
-
Hi rbcarras,
Try to change the TCP/IP properties in the Registry with the following path:
[HKEY_LOCAL_MACHINESOFTWAREMicrosoftMicrosoft SQL ServerMSSQL11.SQL2012MSSQLServerSuperSocketNetLibTcp]
Momominta
What if i don’t even have this entry?
-
I agree that the message box could be a lot better here. We’ll look into that for the next release.
Blocking uninstallation of inbox drivers is by design, however. We do not support using this UI to remove built-in drivers. We don’t test in that configuration, and we know that uninstalling drivers breaks things.
As you’ve probably already noticed, uninstalling a driver from this UI was never permanent. E.g., if you uninstalled a driver from Windows 7, then upgraded to Windows 8, it would get reinstalled. Maybe more disconcertingly, a monthly security
update that affected that particular driver could reinstall it. The reason is that the OS’s servicing stack isn’t really aware of this UI, and doesn’t realize when this UI is removing drivers. The OS’s servicing stack will reinstall the driver
any time the driver is serviced.There’s some advice circulating the Internet to uninstall the «Multiplexor» driver. This is bad advice: it buys you nothing, since the multiplexor doesn’t even get loaded in memory unless you need it for a bridge or LBFO team.
And if you uninstall it, bridges and teams will be permanently broken. We’ve gotten support requests from quite a few customers who inadvertently damaged their systems by uninstalling drivers, and need help putting it back together. In Windows
10 1803, we block attempts to damage the system.Some of the built-in drivers can be uninstalled as part of a larger «optional feature». For example, you can get rid of the Virtual Switch driver by uninstalling the Hyper-V, WDAG, and Containers optional features. Optional features
are indeed supported and we do test the OS with the feature removed.If there are specific drivers that you would like to be removable, but which are not currently part of an Optional Feature, please file a feature request in the Feedback Hub.
Please note that you can always unbind the driver from any/all NICs, either using this GUI or using the PowerShell cmdlet «Disable-NetAdapterBinding». The only change is that you can’t deregister the OS driver entirely. But if you unbind
the driver from all your NICs, it’s effectively the same as uninstalling the driver.Also note that 3rd party drivers can still be installed & uninstalled (or bound/unbound) from this GUI. The change only affects the drivers that are part of the OS.
-
Hello,
Why would we need to remove the Client for Microsoft Networks?
Thanks, Darrell Gorter [MSFT] This posting is provided «AS IS» with no warranties, and confers no rights.
We want remove «Client for Microsoft Networks», LLDP and many others ’cause they are unnecessary to system operation specially on
public networks and machines that access many unknown networks… -
Uninstalling all items for my connection but TCP/IPv4 never broke anything for me on a stand alone system.
You guys force way to much to be installed on Windows pr. default and preventing uninstallation on top is just a silly move.
Regards Joerg Baermann
-
Proposed as answer by
krakdcorn
Sunday, November 18, 2018 6:23 PM
-
Proposed as answer by
-
You can always unbind these drivers — just uncheck the box next to its name. Unbinding the driver will 100% prevent it from communicating on that network.
-
We do not support using this UI to remove built-in Drivers.
Since when ? — You have this UI with the Option to install/remove Protocols, inside Windows for almost 30 Years !!! — Not sure, if it was there in Windows 3.11 but Windows 95 got it… — Even some external Network/Wlan protocols, work with exactly this Panel!
— Are you sure, you speak for the whole MS-Company, when you say, you just drop the support, for Network Protocol, de-install, re-install, install, cause one update broke it ?-
Edited by
Beschwerde
Sunday, May 13, 2018 7:29 PM
-
Edited by
-
There’s some advice circulating the Internet to uninstall the «Multiplexor» driver. This is bad advice: it buys you nothing, since the multiplexor doesn’t even get loaded in memory unless you need it for a bridge or
LBFO team. …Why is this even on the client SKU as NIC teams are not supported on client SKUs ?
-
I recall an advanced Windows NT course where we taught unbinding protocols to a NIC in order to lock down a machine. Part of the Microsoft curriculum taught how to take it a step further and actually uninstall the protocols. This was back in the late 1990’s!
Given the advancements in technology since then and even greater cyber threats of today, why in the world would Microsoft ever prevent us from uninstalling a protocol if we didn’t want it there? This is a huge problem. -
A little workaround I did to fix this «little bug». I have services like Server and
Workstation disabled (plus a few other things), that should take care of the «Client for Microsoft Network» and «File and Printer Sharing». As for the rest, disabling the driver should prevent them from working.rem Link-Layer Topology Discovery Responder / Default - 2 reg add "HKLMSystemCurrentControlSetServicesrspndr" /v "Start" /t REG_DWORD /d "4" /f rem Link-Layer Topology Discovery Mapper I/O Driver / Default - 2 reg add "HKLMSystemCurrentControlSetServiceslltdio" /v "Start" /t REG_DWORD /d "4" /f rem Microsoft LLDP Protocol Driver / Default - 2 reg add "HKLMSystemCurrentControlSetServicesMsLldp" /v "Start" /t REG_DWORD /d "4" /f rem Microsoft Virtual Network Adapter Enumerator / Default - 3 reg add "HKLMSystemCurrentControlSetServicesNdisVirtualBus" /v "Start" /t REG_DWORD /d "4" /f rem QoS for storage I/O traffic / Default - 2 reg add "HKLMSystemCurrentControlSetServicesstorqosflt" /v "Start" /t REG_DWORD /d "4" /f rem QoS Multimeda Class Scheduler / Default - 2 reg add "HKLMSystemCurrentControlSetServicesMMCSS" /v "Start" /t REG_DWORD /d "4" /f rem QoS Packet Scheduler / Default - 1 reg add "HKLMSystemCurrentControlSetServicesPsched" /v "Start" /t REG_DWORD /d "4" /f rem Named pipe service trigger provider / Default - 1 rem https://msdn.microsoft.com/en-us/library/windows/desktop/aa365590(v=vs.85).aspx reg add "HKLMSystemCurrentControlSetServicesnpsvctrig" /v "Start" /t REG_DWORD /d "4" /f rem NetBIOS Interface / Default - 1 reg add "HKLMSystemCurrentControlSetServicesNetBIOS" /v "Start" /t REG_DWORD /d "4" /f rem NetBIOS over TCP/IP / Default - 1 reg add "HKLMSystemCurrentControlSetServicesNetBT" /v "Start" /t REG_DWORD /d "4" /f rem Remote Desktop Device Redirector Bus Driver / Default - 3 reg add "HKLMSystemCurrentControlSetServicesrdpbus" /v "Start" /t REG_DWORD /d "4" /f rem The framework for network mini-redirectors / Default - 1 rem https://docs.microsoft.com/en-us/windows-hardware/drivers/ifs/the-redirected-drive-buffering-subsystem reg add "HKLMSystemCurrentControlSetServicesrdbss" /v "Start" /t REG_DWORD /d "4" /f rem A little bonus - Disable IPv6/LMHOSTS lookup/NetBIOS and Set DNS Servers netsh int ipv6 isatap set state disabled netsh int teredo set state disabled netsh interface ipv6 6to4 set state state=disabled undoonstop=disabled reg add "HKLMSystemCurrentControlSetServicesTcpip6Parameters" /v "DisabledComponents" /t REG_DWORD /d "255" /f wmic nicconfig where DHCPEnabled=TRUE call SetDNSServerSearchOrder ("1.1.1.1") reg add "HKLMSystemCurrentControlSetServicesNetBTParameters" /v "EnableLMHOSTS" /t REG_DWORD /d "0" /f wmic nicconfig where TcpipNetbiosOptions=0 call SetTcpipNetbios 2 wmic nicconfig where TcpipNetbiosOptions=1 call SetTcpipNetbios 2-
Edited by
TairikuOkami
Saturday, June 9, 2018 12:08 PM
-
Edited by
-
‘ We don’t test in that configuration’ — very sad. Maybe misleading. Inconsistent. Slightly arrogant.
It is not just ‘protocols’. It includes ‘service’ and ‘client’ network features.
In the past some of these were not uninstallable. And when you tried to uninstall the button to do so was greyed out. Now items that in the past were uninstallable are not, the uninstall button does not grey out, and you get a silly
error message.Someone dropped the ball at Microsoft. Seems to happen a lot.
Stan
-
Well said, like DNS Cache service for example, which can be disabled only via registry,, ofr now. Disabling it increases security by decreasing the attack surface on the client’s side, like DNS poisoning. DNS malware/attacks are on the rise. I disable it
plus I use dnscrypt with DNSSEC servers.-
Edited by
TairikuOkami
Saturday, June 9, 2018 3:43 PM
-
Edited by
-
Hi rbcarra,
Based on my test, yes and I can reproduce your problem.
It can be uninstalled on previous version, like Windows 10 1709, Windows 10 1607 etc. But when I uninstall it on Windows 10 1803, the result is same as yours:
And I capture the activity on Windows 10 1709 and Windows 10 1803, nothing can be found:
I will submit this feedback via our own channel. It’s also recommend you submit it via built-in Feedback app. If any update, I will post here.
Please remember to mark the replies as answers if they help.
If you have feedback for TechNet Subscriber Support, contact
tnmff@microsoft.com.Have a look at this kb article — maybe the PowerShell workaround helps.
1. Press Windows + X and invoke PowerShell console
2. Enter Get-NetAdapterBinding and press Enter
This lists all bindings of your network
3. Enter the following command to remove a binding
Disable-NetAdapterBinding -Name „Ethernet0“ -ComponentID ms_msclient
Ethernet0 is the placeholder for your network adapter. Instead of ms_msclient you need to identify the component ID returned by Get-NetAdapterBinding and press Enter. QoS is ms_pacer imho.HTP
Gruß/greetings G. Born — Blogs: http://www.borncity.com/blog (Ger) — http://www.borncity.com/win (EN)
-
Edited by
Günter BornMVP
Tuesday, June 26, 2018 1:38 PM
added the PS commands
-
Edited by
-
This is part of some workaround here: https://blog.olandese.nl/2017/05/03/solve-docker-for-windows-error-a-firewall-is-blocking-file-sharing-between-windows-and-the-containers/
So by breaking existing functionality, you also broke workaround. Not cool.
-
Public KB
Error 0x80071779 when removing network components in Windows 10, version 1803
https://support.microsoft.com/en-us/help/4340181/ -
Some of the built-in drivers can be uninstalled as part of a larger «optional feature». For example, you can get rid of the Virtual Switch driver by uninstalling the Hyper-V
Wrong. I’ve uninstalled Hyper-V feature but it didn’t remove neither Hyper-V adapters nor v-switch driver from the OS. I’ve managed to remove NICs manually but can’t uninstall v-switch driver because of this error. There should be some solution to purge
this garbage from the system. -
I been a whole week that I’m trying to fix this, I got screwed using this garbage hyper-v that can not be cleaned from my computer, effectively wrecking any chance of using virtual-box. MS should get a damn checklist and work by it instead of half-fixing
old issues. -
Also trying to use the Docker workaround. Tried Gunter Born’s approach to disable and then re-enable the binding. Sadly did not work.
-
I have tried many of the above suggestions on Windows 10 Pro and no luck.
I have tried using the disable-netadapterbinding on the file and print sharing service for the particular network but after that when i tried to install it again it doesn’t show up in the list as a service to pick.
Also just tried the disable then enable netadapterbinding command and that didn’t work either.
Any other ideas?
Всем доброго дня!
Имеется система Windows 10 Pro 20H2, комп не доменный, ни в каких сетях не состоит, никакие ГП на него никогда не применялись, работаю под локальным админом
Проблема такова: Нет доступа к админским шарам компа по пути UNC, т.е. если вбить в проводнике \имякомпаADMIN$ (C$, D$ и т.д.) то проводник долго думает потом выдает:
Windows не может получить доступ к \имякомпаимяшары (ADMIN$, C$, D$ и т.д. т.е. все шары пробовал)
Код ошибки 0x80070035 Ненайден сетевой путь(Админские шары нужны мне т.к. они нужны для работы некоторых утилит (пакет Sysinternals и др.) без них они не будут работать ни в какую но сейчас речь не о них)
В оснастке «Управление компьютером» (compmgmt.msc) все эти шары есть, и если кликнуть прав.кнопкой мыши и выбрать «Открыть» то шара открывается в проводнике но не с UNC путём в заголовке а с непосредственным путем на диске т.е. ADMIN$ — C:Windows и т.д.
если выполнить:
NET VIEW \имякомпа /ALL
то получаю:
Общие ресурсы на \имякомпа
Имя общего ресурса Тип Используется как Комментарий
-------------------------------------------------------------------------------
ADMIN$ Диск Удаленный Admin
C$ Диск Стандартный общий ресурс
D$ Диск Стандартный общий ресурс
IPC$ IPC Удаленный IPC
Команда выполнена успешно.НО! при попытке выполнить: net use y: \имякомпаадминшара /user:Я
Получаю:
Сервер не настроен для удаленного администрирования.
Для вызова дополнительной справки наберите NET HELPMSG 3743.
Предыстория такова: Изначально (как в винде всегда и бывает) все работало (хотя уже точно не помню как именно работало т.к. в некоторых вин10 админские шары сразу не работают но легко расшариваются и потом работают, ключами из реестра ниже), потом как то я увлекся и решил отключить протокол Samba2 (чето по глупости подумалось раз Samba1 нашли уязвимости то и Samba2 отключу т.к. у меня не сервер и сети нет) потом вдруг через время обнаружил что админские шары исчезли и доступа к ним по UNC пути нет (как выше описал)
Покопавшись обнаружил что неработает служба LanmanWorkstation и не запускается, оказалось она зависит от службы mrxsmb20 который обеспечивает работу протокола Samba2 который я отключил (админские шары расшариваются по протоколу Samba) вобщем включил Samba2, запустил mrxsmb20 а потом и LanmanWorkstation — доступ в проводнике по UNC пути \имякомпаимяшары появился сразу же даже без перезагрузки, прошло некоторое приличное время админские шары опять понадобились — опа а они опять не работают! Доступа по UNC пути опять нет!
Хотя уже и LanmanWorkstation (ессно и LanmanServer тоже) работают и Samba2 включен и mrxsmb20 работает и вообще за время прошедшее с последней работы с админскими шарами мною в системе вообще больше ничего не менялось и ничего не отключалось! Служба обновлений wuauserv у меня отключена а потому никакие обновления не устанавливались!
Фаерволл тоже как бы не причем, виндовый фаер у меня отключен а вместо него Agnitum Outpost, сначала при нем все работало, в самом фаерволле я ничего не менял
Что делал:
По многочисленным статьям в инете где решается подобная проблема выставил в реестре:
HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindowsCurrentVersionPoliciesSystemLocalAccountTokenFilterPolicy - 1
HKEY_LOCAL_MACHINESYSTEMCurrentControlSetServicesLanmanServerParametersAutoShareServer - 1
HKEY_LOCAL_MACHINESYSTEMCurrentControlSetServicesLanmanServerParametersAutoShareWks - 1
HKEY_LOCAL_MACHINESYSTEMCurrentControlSetServicesLanmanWorkstationParametersAllowInsecureGuestAuth - 1
HKEY_LOCAL_MACHINESYSTEMCurrentControlSetServicesLanmanWorkstationParametersEnablePlainTextPassword - 1Полностью отключил UAC, полностью разрешил в фаерволле Agnitum ВСЕ!, т.е. любой траффик всем процессам в любом направлении
В Локальных групповых политиках в: Конфигурация компьютера — Конфигурация Windows — Параметры безопасности — Локальные политики — Назначение прав пользователя :
Доступ к компьютеру из сети — Все, Администраторы
Отказать в доступе к этому компьютеру из сети — был Гость — удалил
(Кстати когда админские шары заработали после первого отключения и включения Samba2 — практически все эти параметры имели значение — 0! А шары работали!)
Проверял службы fdPHost и FDResPub (Хост поставщика функции обнаружения и Публикация ресурсов обнаружения функции) — работают
В Панель управленияСеть и ИнтернетЦентр управления сетями и общим доступомДополнительные параметры общего доступа — для всех сетей включен общий доступ (все три параметра)
Samba1 -отключен, Samba2 — включен и работает, пробовал и Samba1 включать — непомогает
Вообщем после всех вышеописанных процедур (выполнял их последовательно перезагружая комп)
Шары по UNC пути доступны так и не стали,
Есс-но после применения всех вышеприведенных параметров комп перезагружал и не раз — ничего не меняется
