Hi everyone,
in last few days, I’m not able anymore to connect to my OpenVPN server, that runs on a PI. To install it I’ve followed this guide: https://pimylifeup.com/raspberry-pi-vpn-server/.
This is the error I’m getting from the openvpn.log:
Code: Select all
Mon Apr 30 11:08:06 2018 5.90.54.104:33909 VERIFY ERROR: depth=0, error=CRL has expired: CN=windowsClient
Mon Apr 30 11:08:06 2018 5.90.54.104:33909 OpenSSL: error:14089086:SSL routines:ssl3_get_client_certificate:certificate verify failed
Mon Apr 30 11:08:06 2018 5.90.54.104:33909 TLS_ERROR: BIO read tls_read_plaintext error
Mon Apr 30 11:08:06 2018 5.90.54.104:33909 TLS Error: TLS object -> incoming plaintext read error
Mon Apr 30 11:08:06 2018 5.90.54.104:33909 TLS Error: TLS handshake failed
Mon Apr 30 11:08:06 2018 5.90.54.104:33909 Fatal TLS error (check_tls_errors_co), restarting
And this from the client side:
Code: Select all
Validating certificate extended key usage
2018-04-30 11:28:17 ++ Certificate has EKU (str) TLS Web Server Authentication, expects TLS Web Server Authentication
2018-04-30 11:28:17 VERIFY EKU OK
2018-04-30 11:28:17 VERIFY X509NAME OK: CN=server_XXxQwp63Aywdvhzm
2018-04-30 11:28:17 VERIFY OK: depth=0, CN=server_XXxQwp63Aywdvhzm
2018-04-30 11:28:18 Connection reset, restarting [0]
2018-04-30 11:28:18 SIGUSR1[soft,connection-reset] received, process restarting
2018-04-30 11:28:18 MANAGEMENT: >STATE:1525080498,RECONNECTING,connection-reset,,,,,
It seems the CRL certificate has been expired; how Can I fix? I don’t want to change something on the client side. I’ve a .pem file in /etc/openvpn/ folder and I’ve a folder Easy-RSA. Thank you in advance for your help!
This topic has been deleted. Only users with topic management privileges can see it.
I’m testing upgrades between 2.4.5p1 to 2.6.0. The upgrade itself seems to go fine, I’m just testing services post-upgrade and found an issue with OpenVPN refusing TLS auth saying the certificate revocation list expired:
Jun 17 17:57:25 openvpn 90723 1.2.3.4:42081 TLS Error: TLS handshake failed
Jun 17 17:57:25 openvpn 90723 1.2.3.4:42081 TLS Error: TLS object -> incoming plaintext read error
Jun 17 17:57:25 openvpn 90723 1.2.3.4:42081 TLS_ERROR: BIO read tls_read_plaintext error
Jun 17 17:57:25 openvpn 90723 1.2.3.4:42081 OpenSSL: error:1417C086:SSL routines:tls_process_client_certificate:certificate verify failed
Jun 17 17:57:25 openvpn 90723 1.2.3.4:42081 VERIFY ERROR: depth=0, error=CRL has expired: C=GB, ST=London, L=London, O=MyOrg, emailAddress=technical@myorg.com, CN=myuser, serial=2
If I disable the use of the CRL in the OpenVPN server instance, clients can connect fine.
The CRL was created on this very pfSense box and would have used the default lifetime of 9999 days. That may have been on 2.2.6 and carried up through reinstalls to 2.4.5p1 or it may have been created on 2.4.5p1, I can’t remember now.
I think I can see the issue here:
me@myhost:~/$ openssl crl -in Revoked+Certs.crl -noout -text
Certificate Revocation List (CRL):
<snip>
Last Update: Jun 17 17:25:44 2022 GMT
Next Update: Apr 25 17:25:44 1955 GMT
Does that next update field mean the expiry date? If so, it looks like it’s off by about a century.
If I look at the one from the other firewall in the HA pair, which wasn’t upgraded yet, I see this:
Last Update: Jun 17 18:06:54 2022 GMT
Next Update: Nov 1 18:06:54 2049 GMT
So the one that got upgraded got messed up, right?
Can anyone advise on how to either extend the date of the existing CRL, or recreate it without losing which certs were revoked? I revoked some certs and deleted the actual certs so I can’t create a new CRL and then revoke the certs again. Googling I’ve seen suggestions to use easyrsa, but that doesn’t appear to be on my pfSense box.
The CRL is rewritten with a fresh date every time it rewrites the OpenVPN configuration.
What hardware is this on? If it’s a 32-bit ARM system it may be having a problem with the date going past 2038.
@jimp Thanks for your reply Jim.
This is AMD64. I’ll make a tweak to the OpenVPN config in that case and see if the issue goes away. It didn’t when I reconfigured the OpenVPN server instance to not use the CRL though, so we’ll see. I also tried adding another entry to the CRL, but that didn’t help. I’ll come back to update on whether it helped or not.
Issue resolved. After I found that the CRL expiry was getting updated but was still for some reason in 1955 after making tweaks to the OpenVPN config, I looked at what was in config.xml for the CRL and found that the lifetime was 99999 days, rather than 9999 is recommended. Changed it to 9999 and re-imported and it’s working properly now.
Thanks for pointing me in the right direction @jimp.
Looks like we have a similar issue too. I’ve got a pair of Netgate 7100’s which all of a sudden today are not letting users connect. When I look at the CRL it shows a date of Jan 1950 for the next issue.
I’ve tried recreating the CRL with 9900 days or setting the vpn server not to use a CRL but its still showing the error.
Is there a fix for the date roll over issue.
22.05-RELEASE (amd64)
built on Wed Jun 22 18:56:13 UTC 2022
FreeBSD 12.3-STABLE
@barryboden My issue may not be yours and I don’t know about 22.05 (we’re using CE), but I found if I exported the config (or just looked at it in /cf/conf/config.xml) in the <crl> section there was:
<lifetime>99999</lifetime>
I understand there was a change in OpenVPN between the versions used in 2.4.5p1 and 2.6.0 where the verification of the CRL was moved from being done by OpenVPN to being handled by OpenSSL which was stricter. It would be worth looking at what the CRL lifetime value is in your config.xml.
I found changing it in config.xml and rebooting didn’t work, pfSense must write its config out before rebooting. I had to export the config through the GUI, update the lifetime field (to 9999) then reimport it. In a crisis, you can just disable use of the CRL until you figure it out but obviously that would allow users with revoked certs to log in again.
That’s as far as I can help you. Hope it does.
@barryboden See my posts here https://forum.netgate.com/topic/174167/no-clients-can-connect-to-openvpn-due-to-crl-expiry
I’d suggest recreating the CRL with a much shorter lifetime (I did 730 days). Be sure to edit the OpenVPN server settings to point to the new CRL and then restart the OpenVPN service.
@ads76 thanks for your reply I did look in there any my config already says 9999, I’ve created new CRLs and if I set them to 9990 the dates look ok, but 9999 must roll over the year.
Adjusting this has got my clients connecting again, for 9 days.
I created a Redmine entry for this (https://redmine.pfsense.org/issues/13424) and I’ll be working on a fix shortly. When I have one, I’ll also create an entry in the System Patches package for it.
@jimp Applied diff manually and restarted Openvpn server service.
It works after restart of service.
I merged the fix in yesterday evening.
You can install the System Patches package and then create an entry for a3c1589086ea67d25a28ec14ab95d7fd9ab25fa2 to apply the fix.
It will be added as a «Recommended Patch» in the System Patches package soon, but in the meantime it is safe to add a manual entry to obtain the fix now.
@jimp I’ve just applied that patch and restarted OpenVPN. CRL expiry error no longer in OpenVPN logs and clients now connecting again — thanks !
PFSense: 22.05-RELEASE (amd64)
KVM Guest
Intel(R) Xeon(R) CPU E5-2650 v2 @ 2.60GHz
2 CPUs: 1 package(s) x 1 core(s) x 2 hardware threads
AES-NI CPU Crypto: Yes (active)
QAT Crypto: No
@jimp said in CRL has expired:
You can install the System Patches package and then create an entry for
a3c1589086ea67d25a28ec14ab95d7fd9ab25fa2to apply the fix.
We run into the same issue, lost all VPN connections.
Can we apply this patch also in 2.6.0 CE?
S sloopbun referenced this topic on
The patch applies cleanly to 2.6.0, you can use it there.
@jimp
thank you, the VPN working again.
O opana referenced this topic on
Thank you all for the comments and patch solution here. Many of my haproxy backends went down last week (ssl handshake errors) and diagnosing the issue was very difficult.
A lot of trial and error, I narrowed down the backend SSL verification and CRL, as the culprit. I stumbled upon this issue after searching errors related to a downed OpenVPN client. Applying the patch here (obviously) fixed both haproxy and OpenVPN issues I was having.
Just wanted to add my experience in case any others are having the same issues with haproxy, and are looking for a solution. Hopefully they will also find this thread.
@jimp
Thank you ! Worked like a charm on 22.05-RELEASE (amd64)
Same issue here. Patch solved it within a minute. Thanks.
This has some additional information: https://blog.nuvotex.de/pfsense-crl-has-expired/
Y2K all over again
had this same problem, applied the patch, fixed
Thanks Jim
P pigbrother referenced this topic on
P pigbrother referenced this topic on
P pigbrother referenced this topic on
P pigbrother referenced this topic on
I had the same issue with version 2.5 and 22.05, i wonder if netgate has permanent fix for that
Dear All,
Are we really really shure that the patch does fix this? I did apply it and it did work for the moment. After rebooting one of my four pfSense devices (2.6.0-RELEASE (amd64)), I was shut out of all of OpenVPN. The log did contain many entries like this:
Sep 1 18:09:39 openvpn 91912 xxx.xxx.xxx.185:31089 Certificate does not have key usage extension
Sep 1 18:09:39 openvpn 91912 xxx.xxx.xxx.185:31089 OpenSSL: error:1417C086:SSL routines:tls_process_client_certificate:certificate verify failed
Sep 1 18:09:39 openvpn 91912 xxx.xxx.xxx.185:31089 TLS_ERROR: BIO read tls_read_plaintext error
Sep 1 18:09:39 openvpn 91912 xxx.xxx.xxx.185:31089 TLS Error: TLS object -> incoming plaintext read error
Sep 1 18:09:39 openvpn 91912 xxx.xxx.xxx.185:31089 TLS Error: TLS handshake failed
The certificate did work before. After unchecking «Client Certificate Key Usage Validation», everything was OK again. Until the reboot today, it was no problem to leave «Client Certificate Key Usage Validation» checked.
Regards,
Michael
@ads76 Thank you very much. I did install the patches and I am «thrilled» to see what will happen next. I also hope that the system patches package will not become the replacement for regular system updates 
Those are the changes on the patch
https://github.com/pfsense/pfsense/commit/a3c1589086ea67d25a28ec14ab95d7fd9ab25fa2#diff-d2a6b2f1c6de8faca0eb12c53221e1874fa9943f07f6df127fb153cd1e03ba34
From a3c1589086ea67d25a28ec14ab95d7fd9ab25fa2 Mon Sep 17 00:00:00 2001
From: jim-p jimp@netgate.com
Date: Wed, 17 Aug 2022 12:09:36 -0400
Subject: [PATCH] CRL lifetime fixes to avoid rollover. Fixes #13424
src/etc/inc/certs.inc | 29 +++++++++++++++++++++++—
src/usr/local/www/system_crlmanager.php | 6 ++—
2 files changed, 30 insertions(+), 5 deletions(-)
diff —git a/src/etc/inc/certs.inc b/src/etc/inc/certs.inc
index c73a964f3ab..16a011d21eb 100644
— a/src/etc/inc/certs.inc
+++ b/src/etc/inc/certs.inc
@@ -54,6 +54,9 @@ $cert_altname_types = array(
global $cert_max_lifetime;
$cert_max_lifetime = 12000;
+global $crl_max_lifetime;
+$crl_max_lifetime = 9999;
+
function & lookup_ca($refid) {
global $config;
@@ -978,9 +981,31 @@ function cert_get_max_lifetime() {
return min($max, $cert_max_lifetime);
}
+/* Detect a rollover at 2050 with UTCTime
-
- See: https://redmine.pfsense.org/issues/9098 */
+function crl_get_max_lifetime() {
- See: https://redmine.pfsense.org/issues/9098 */
- global $crl_max_lifetime;
- $max = $crl_max_lifetime;
- $now = new DateTime(«now»);
- $utctime_before_roll = DateTime::createFromFormat(‘Ymd’, ‘20491231’);
- if ($date !== false) {
-
$interval = $now->diff($utctime_before_roll); -
$max_days = abs($interval->days); -
/* Reduce the max well below the rollover time */ -
if ($max_days > 1000) { -
$max_days -= 1000; -
} -
return min($max_days, cert_get_max_lifetime()); - }
- /* Cannot use date functions, so use a lower default max. */
- return min(7000, cert_get_max_lifetime());
+}
function crl_create(& $crl, $caref, $name, $serial = 0, $lifetime = 3650) {
global $config;
- $max_lifetime = cert_get_max_lifetime();
-
$max_lifetime = crl_get_max_lifetime();
$ca =& lookup_ca($caref);
if (!$ca) {
return false;
@@ -1017,7 +1042,7 @@ function crl_update(& $crl) {
require_once(‘X509_CRL.php’);global $config;
- $max_lifetime = cert_get_max_lifetime();
- $max_lifetime = crl_get_max_lifetime();
$ca =& lookup_ca($crl[‘caref’]);
if (!$ca) {
return false;
diff —git a/src/usr/local/www/system_crlmanager.php b/src/usr/local/www/system_crlmanager.php
index d471209d3e3..4b3ed0a6f33 100644
— a/src/usr/local/www/system_crlmanager.php
+++ b/src/usr/local/www/system_crlmanager.php
@@ -34,8 +34,8 @@
require_once(«pfsense-utils.inc»);
require_once(«vpn.inc»);
-$max_lifetime = cert_get_max_lifetime();
-$default_lifetime = min(9999, $max_lifetime);
+$max_lifetime = crl_get_max_lifetime();
+$default_lifetime = min(730, $max_lifetime);
global $openssl_crl_status;
@@ -255,7 +255,7 @@
}
if ($pconfig['method'] == "internal") {
-
$crl['serial'] = empty($pconfig['serial']) ? 9999 : $pconfig['serial'];
-
$crl['serial'] = empty($pconfig['serial']) ? '0' : $pconfig['serial']; $crl['lifetime'] = empty($pconfig['lifetime']) ? $default_lifetime : $pconfig['lifetime']; $crl['cert'] = array(); }
K khodorb referenced this topic on
🔍 Простой поиск по базе знаний

Достаточно часто при использовании списка отозванных сертификатов через месяц становится невозможно установить связь с сервером OpenVPN. В логах OpenVPN появляется ошибка установления соединения с сервером:
TLS: Initial packet from [AF_INET]ХХ.ХХ.ХХ.ХХ:62889, sid=ba13f8a4 4c4aec28 VERIFY ERROR: depth=0, error=CRL has expired: CN=client1 OpenSSL: error:140890B2:SSL routines:SSL3_GET_CLIENT_CERTIFICATE:no certificate returned TLS_ERROR: BIO read tls_read_plaintext error TLS Error: TLS object -> incoming plaintext read error TLS Error: TLS handshake failed SIGUSR1[soft,tls-error] received, client-instance restarting
Причина — в превышении времени жизни списка отозванных сертификатов, который хранится в файле crl.pem (CRL — certificate revoke list). Проверить это можно выдав следующую команду:
$ sudo openssl crl -inform PEM -in /etc/openvpn/easy-rsa/keys/crl.pem -text -noout [sudo] пароль для user1: Certificate Revocation List (CRL): Version 1 (0x0) Signature Algorithm: sha256WithRSAEncryption Issuer: /C=RU/ST=RU/L=Moscow/O=ХХХХ/OU=ХХХХ/CN=ХХХХ/name=EasyRSA/emailAddress=хххх@yourmail.ru Last Update: Sep 10 09:26:36 2020 GMT Next Update: Sep 11 09:26:36 2021 GMT
Из вывода видно что не позднее 11 сентября необходимо перевыпустить список отозванных сертификатов. Иначе будет появляться эта ошибка.
Можно конечно перевыпустить список ещё на год, но лучше всё таки увеличить его срок жизни.
Время жизни списка отозванных сертификатов задается в файле /etc/openvpn/easy-rsa/openssl-1.0.0.cnf в следующей секции:
# Extensions to add to a CRL. Note: Netscape communicator chokes on V2 CRLs # so this is commented out by default to leave a V1 CRL. # crl_extensions = crl_ext default_days = 3650 # how long to certify for default_crl_days= 365 # how long before next CRL default_md = sha256 # use public key default MD preserve = no # keep passed DN ordering
default_crl_days= 365 это и есть количество дней до перевыпуска списка отозванных сертификатов или время жизни этого списка. Открываем файл конфигурации любимым редактором, например nano:
$ sudo nano /etc/openvpn/easy-rsa/openssl-1.0.0.cnf
и изменяем default_crl_days= 365 на, например, default_crl_days= 3650. То-есть на 10 лет. Затем перевыпускаем сам список:
$ sudo su # cd /etc/openvpn/easy-rsa # openssl ca -gencrl -keyfile keys/ca.key -cert keys/ca.crt -out keys/crl.pem -config ./openssl-1.0.0.cnf # exit
Проверяем:
$ sudo openssl crl -inform PEM -in /etc/openvpn/easy-rsa/keys/crl.pem -text -noout [sudo] пароль для user1: Certificate Revocation List (CRL): Version 1 (0x0) Signature Algorithm: sha256WithRSAEncryption Issuer: /C=RU/ST=RU/L=Moscow/O=ХХХХ/OU=ХХХХ/CN=ХХХХ/name=EasyRSA/emailAddress=хххх@yourmail.ru Last Update: Sep 10 09:26:36 2020 GMT Next Update: Sep 11 09:26:36 2030 GMT
Все нормально и все должно работать.
TLS: Initial packet from [AF_INET]XXX.XXX.XXX.XXX:60382, sid=c9c9a1f3 02ce9312 VERIFY ERROR: depth=0, error=CRL hasexpired: CN=client_name OpenSSL: error:14089086:SSL routines: ssl3_get_client_certificate:certificate verify failed TLS_ERROR: BIO read tls_read_plaintext error TLS Error: TLS object -> incoming plaintext read error TLS Error: TLS handshake failed SIGUSR1[soft,tls-error] received, client-instance restarting
Сегодня речь пойдет об одном нюансе, связанном со списком отозванных сертификатов (Сertificate Revocation List, CRL) в OpenVPN. Данный механизм применяется, когда требуется блокировать доступ отдельных узлов к сети (в случае увольнения сотрудника или подозрения что выданный сертификат скомпрометирован).
В какой-то момент времени, может возникнуть ошибка OpenVPN CRL has expired (просрочен список CRL) и клиенты перестают подключаться. Убедиться, что проблема именно в этом довольно просто, достаточно закомментировать в конфиге сервера строку проверки отозванных сертификатов и перезапустить сервер.
crl-verify crl.pem
После чего клиенты спокойно начнут подключаться.
Обновление списка отозванных сертификатов OpenVPN
Для решения проблемы со списком CRL надо этот список обновить. Делается это элементарно, о чём я уже рассказывал в статье про отзыв пользовательских сертификатов OpenVPN на FreeBSD 10/11:
# cd /usr/local/etc/openvpn/easy-rsa # ./easyrsa.real gen-crl
Почему возникла данная проблема? Дело в том, что периодичность обновление списка отозванных сертификатов задаётся в переменной default_crl_days в конфиге /usr/local/openvpn/easy-rsa/openssl-1.0.cnf:
default_crl_days= $ENV::EASYRSA_CRL_DAYS # how long before next CRL
Сами значения переменных задаются в файле /usr/local/openvpn/easy-rsa/vars. По умолчанию обновление списка CRL происходит каждые 180 дней (можно задать своё значение, например 365 дней) :
#set_var EASYRSA_CRL_DAYS 180
Подписывайтесь на канал
Яндекс.Дзен
и узнавайте первыми о новых материалах, опубликованных на сайте.
Перейти к содержимому

По неведомой причине, без каких-либо вмешательств, перестали подключаться клиенты к OpenVPN-серверу PFSENSE 2.6.0-RELEASE (amd64). Анализ логов показал ошибку CRL has expired, хотя по факту до просрочки этого списка еще очень далеко
Sep 1 10:02:17 openvpn 94243 11.22.33.44:1194 VERIFY ERROR: depth=0, error=CRL has expired: CN=user@domain.ru, C=RU, ST=KRR, L=KRD, O=DOMAIN.RU, OU=IT, serial=24
Sep 1 10:02:17 openvpn 94243 11.22.33.44:1194 OpenSSL: error:1417C086:SSL routines:tls_process_client_certificate:certificate verify failed
Sep 1 10:02:17 openvpn 94243 11.22.33.44:1194 TLS_ERROR: BIO read tls_read_plaintext error
Sep 1 10:02:17 openvpn 94243 11.22.33.44:1194 TLS Error: TLS object -> incoming plaintext read error
Sep 1 10:02:17 openvpn 94243 11.22.33.44:1194 TLS Error: TLS handshake failed
Пересоздание CRL проблему не решило, отключение проверки Peer Certificate Revocation list проблему конечно решает, но тогда нет возможности “блокировки неугодных”. Ответ был найден на форуме forum.netgate.com
Первым делом нужно добавить пакет System_Patches в PFSENSE. Делается просто через GUI: System / Package Manager / Available Packages
Далее, так же System / Patches добавить патч по хэшу a3c1589086ea67d25a28ec14ab95d7fd9ab25fa2
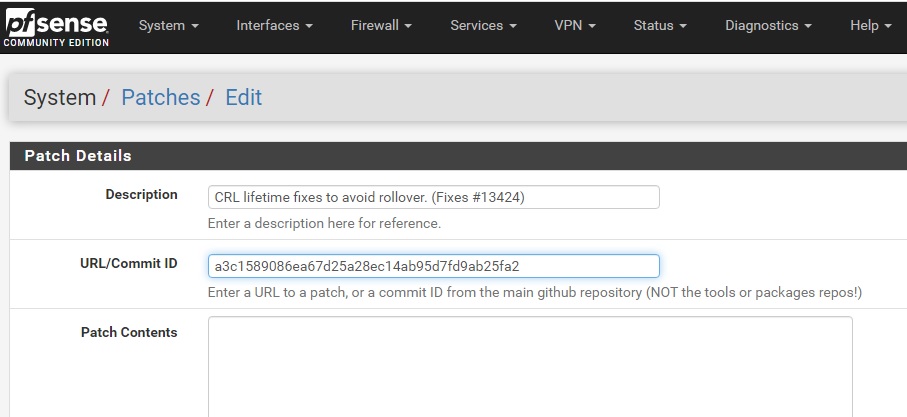
После добавления сделать Fetch и Apply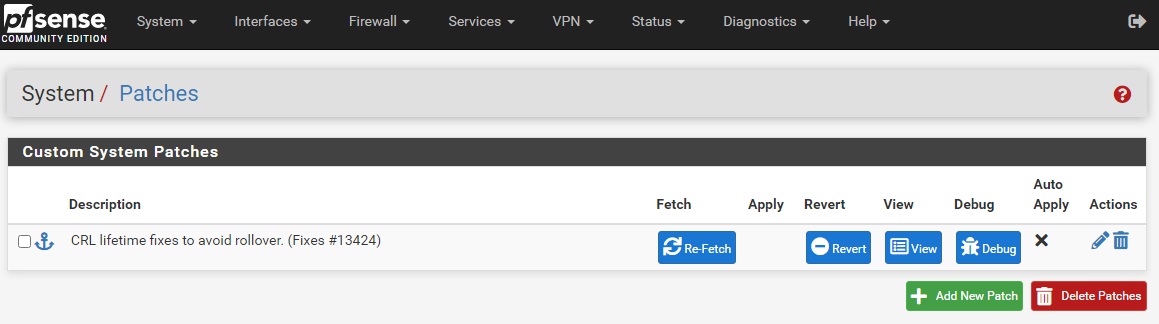
Патч исправляет ошибку проверки срока годности CRL-списка отзывов сертификатов и клиенты нормально подключаются к OpenVPN серверу.
1 016
