Содержание
- LDAP: error code 49 — Invalid Credentials During FileNet Enterprise Manager (FEM) Logon
- Troubleshooting
- Problem
- Symptom
- Cause
- Diagnosing The Problem
- Resolving The Problem
- Ldap error invalid credentials error code 49
- Asked by:
- Question
- LDAP Integration — Bind failed: 49: Invalid credentials #4177
- Comments
- Steps to reproduce
- Expected behaviour
- Actual behaviour
- Server configuration
- LDAP configuration (delete this part if not used)
- Client configuration
- Web server error log
- Nextcloud log (data/nextcloud.log)
- Browser log
- Ldap error invalid credentials error code 49
- Asked by:
- Question
- LDAP Integration — Bind failed: 49: Invalid credentials #4177
- Comments
- Steps to reproduce
- Expected behaviour
- Actual behaviour
- Server configuration
- LDAP configuration (delete this part if not used)
- Client configuration
- Web server error log
- Nextcloud log (data/nextcloud.log)
- Browser log
LDAP: error code 49 — Invalid Credentials During FileNet Enterprise Manager (FEM) Logon
Troubleshooting
Problem
Users cannot login to FEM
Symptom
FEM returns a «LDAP: error code 49 — Invalid Credentials»
Cause
1. The credential of the bind user in one of the Directory Configurations is incorrect.
2. The credential of bootstrap user is incorrect
Diagnosing The Problem
Check for Directory Configuration bind user credential is incorrect
1. Check the ping page and confirm that CE has started successfully with no errors.
2. Attempt to login through FEM with a valid user. If the login fails with a LDAP error 49, at least one of the directory configuration bind user credential is incorrect.
Check for bootstrap user credential is incorrect
1. Check the ping page and confirm that CE has started, but the ping page should give a LDAP error 49.
2. Attempt to login through FEM with a valid user. If the login fails with a LDAP error 49, the bootstrap user crenential is incorrect.
Resolving The Problem
Using a third-party tool, login to the LDAP server with directory configuration bind user credential. If login is unsuccessful, contact an LDAP administrator to get the correct password. If login is successful, the bootstrap or bind user credential is incorrect.
Directory Configuration bind user credential is incorrect
Use the GCDUtil tool to modify the Directory Configuration bind user password
Bootstrap user credential is incorrect
Start CMUI tool, run the bootstrap task to update the bootstrap user credentials, and then redeploy CE.
Источник
Ldap error invalid credentials error code 49
This forum has migrated to Microsoft Q&A. Visit Microsoft Q&A to post new questions.
Asked by:

Question


We are developing a LDAP authentication against Active Directory, we met the follow errors, although the username and password are correct.
LDAP: error code 49 — 80090308: LdapErr: DSID-0C090334, comment: AcceptSecurityContext error, data 52e, vece
The user detail is: CN=Peter, Lia ,OU=DEV,OU=HK_U,OU=cita,OU=US,DC=achtest,DC=local
As you may saw, the last name of this user has a backslash, plus a space in CN, we guess it may be the problem, since other users don’t have this problem if the last name of users don’t have a backslash and a space.
However we don’t know how we can add a new user to duplicate this issue, since it’s not way to add a new user with space in the end of name, the Active Directory will auto trim the space when system save the new user to database.
My questions are:
1. Do you have this kind of experience? Any idea to resolve?
2. How we can add a new user with a space in the end of last name? and then we can replicate this issue again?
Источник
LDAP Integration — Bind failed: 49: Invalid credentials #4177
Steps to reproduce
- Connect to LDAP Server, Configuration OK. 301 Users found, they show up in User category.
2.Try to log in with a user, using the ‘username’ displayed in NC
3.Wrong Password shows up and user is rejected, log says Bind failed: 49: Invalid credentials
Expected behaviour
User should be authenticated and logged in
Actual behaviour
User is rejected
Server configuration
Operating system:
Ubuntu 12.04.5 LTS
Web server:
Apache2
Database:
MySql
PHP version:
PHP 7.0.15-0ubuntu0.16.04.4
Nextcloud version: (see Nextcloud admin page)
11,0,2,7
Updated from an older Nextcloud/ownCloud or fresh install:
Fresh install
Where did you install Nextcloud from:
Tar from official website: Nextcloud-11.0.2.tar.bz2
Signing status:
List of activated apps:
- activity: 2.4.1
- admin_audit: 1.1.0
- comments: 1.1.0
- dav: 1.1.1
- federatedfilesharing: 1.1.1
- federation: 1.1.1
- files: 1.6.1
- files_pdfviewer: 1.0.1
- files_sharing: 1.1.1
- files_texteditor: 2.2
- files_trashbin: 1.1.0
- files_versions: 1.4.0
- files_videoplayer: 1.0.0
- firstrunwizard: 2.0
- gallery: 16.0.0
- logreader: 2.0.0
- lookup_server_connector: 1.0.0
- nextcloud_announcements: 1.0
- notifications: 1.0.1
- provisioning_api: 1.1.0
- serverinfo: 1.1.1
- sharebymail: 1.0.1
- survey_client: 0.1.5
- systemtags: 1.1.3
- theming: 1.1.1
- twofactor_backupcodes: 1.0.0
- updatenotification: 1.1.1
- user_external: 0.4
- user_ldap: 1.1.2
- workflowengine: 1.1.1
Disabled: - encryption
- external
- files_accesscontrol
- files_automatedtagging
- files_external
- files_retention
- password_policy
- templateeditor
- user_saml
The content of config/config.php:
Are you using external storage, if yes which one: local/smb/sftp/.
no
Are you using encryption: yes/no
no
Are you using an external user-backend, if yes which one: LDAP/ActiveDirectory/Webdav/.
LDAP:
Kerberos with LDAP as login agent
LDAP configuration (delete this part if not used)
Client configuration
Browser:
Operating system:
Web server error log
Nextcloud log (data/nextcloud.log)
+——————————-+————————————————————————————-+
| Configuration | s01 |
+——————————-+————————————————————————————-+
| hasMemberOfFilterSupport | |
| hasPagedResultSupport | |
| homeFolderNamingRule | |
| lastJpegPhotoLookup | 0 |
| ldapAgentName | cn=ADMIN,dc=ds,dc=local |
| ldapAgentPassword | *** |
| ldapAttributesForGroupSearch | |
| ldapAttributesForUserSearch | |
| ldapBackupHost | |
| ldapBackupPort | |
| ldapBase | dc=ds,dc=local |
| ldapBaseGroups | dc=ds,dc=local |
| ldapBaseUsers | ou=people,dc=ds,dc=local |
| ldapCacheTTL | 600 |
| ldapConfigurationActive | 1 |
| ldapDynamicGroupMemberURL | |
| ldapEmailAttribute | mail |
| ldapExperiencedAdmin | 0 |
| ldapExpertUUIDGroupAttr | |
| ldapExpertUUIDUserAttr | |
| ldapExpertUsernameAttr | uid |
| ldapGroupDisplayName | cn |
| ldapGroupFilter | (&(|(objectclass=posixGroup))) |
| ldapGroupFilterGroups | |
| ldapGroupFilterMode | 1 |
| ldapGroupFilterObjectclass | posixGroup |
| ldapGroupMemberAssocAttr | memberUid |
| ldapHost | teller.ds.local |
| ldapIgnoreNamingRules | |
| ldapLoginFilter | (&(|(objectclass=inetOrgPerson))(uid=%uid)) |
| ldapLoginFilterAttributes | |
| ldapLoginFilterEmail | 0 |
| ldapLoginFilterMode | 1 |
| ldapLoginFilterUsername | 1 |
| ldapNestedGroups | 1 |
| ldapOverrideMainServer | |
| ldapPagingSize | 1000 |
| ldapPort | 389 |
| ldapQuotaAttribute | |
| ldapQuotaDefault | |
| ldapTLS | 0 |
| ldapUserDisplayName | cn |
| ldapUserDisplayName2 | |
| ldapUserFilter | (|(objectclass=inetOrgPerson)(objectclass=krb5Principal)(objectclass=posixAccount)) |
| ldapUserFilterGroups | |
| ldapUserFilterMode | 0 |
| ldapUserFilterObjectclass | inetOrgPerson;krb5Principal;posixAccount |
| ldapUuidGroupAttribute | auto |
| ldapUuidUserAttribute | auto |
| turnOffCertCheck | 1 |
| turnOnPasswordChange | 0 |
| useMemberOfToDetectMembership | 1 |
+——————————-+————————————————————————————-+
+——————————-+—————+
| Configuration | s02 |
+——————————-+—————+
| hasMemberOfFilterSupport | 0 |
| hasPagedResultSupport | |
| homeFolderNamingRule | |
| lastJpegPhotoLookup | 0 |
| ldapAgentName | |
| ldapAgentPassword | *** |
| ldapAttributesForGroupSearch | |
| ldapAttributesForUserSearch | |
| ldapBackupHost | |
| ldapBackupPort | |
| ldapBase | |
| ldapBaseGroups | |
| ldapBaseUsers | |
| ldapCacheTTL | 600 |
| ldapConfigurationActive | 0 |
| ldapDynamicGroupMemberURL | |
| ldapEmailAttribute | |
| ldapExperiencedAdmin | 0 |
| ldapExpertUUIDGroupAttr | |
| ldapExpertUUIDUserAttr | |
| ldapExpertUsernameAttr | |
| ldapGroupDisplayName | cn |
| ldapGroupFilter | |
| ldapGroupFilterGroups | |
| ldapGroupFilterMode | 0 |
| ldapGroupFilterObjectclass | |
| ldapGroupMemberAssocAttr | uniqueMember |
| ldapHost | |
| ldapIgnoreNamingRules | |
| ldapLoginFilter | |
| ldapLoginFilterAttributes | |
| ldapLoginFilterEmail | 0 |
| ldapLoginFilterMode | 0 |
| ldapLoginFilterUsername | 1 |
| ldapNestedGroups | 0 |
| ldapOverrideMainServer | |
| ldapPagingSize | 500 |
| ldapPort | |
| ldapQuotaAttribute | |
| ldapQuotaDefault | |
| ldapTLS | 0 |
| ldapUserDisplayName | displayName |
| ldapUserDisplayName2 | |
| ldapUserFilter | |
| ldapUserFilterGroups | |
| ldapUserFilterMode | 0 |
| ldapUserFilterObjectclass | |
| ldapUuidGroupAttribute | auto |
| ldapUuidUserAttribute | auto |
| turnOffCertCheck | 0 |
| turnOnPasswordChange | 0 |
| useMemberOfToDetectMembership | 1 |
+——————————-+—————+
Browser log
Due to personal info and IP’s I can’t admitt the log. Putting warnings and errors here.
Warning user_ldap Bind failed: 49: Invalid credentials
Warning core Login failed: ‘Username’
Error index OCServerNotAvailableException: Connection to LDAP server could not be established (This one might have showed up when I was tinkering and is probably not a permanent one)
Error PHP ldap_search(): Partial search results returned: Sizelimit exceeded at /var/www/nextcloud/apps/user_ldap/lib/LDAP.php#293
The text was updated successfully, but these errors were encountered:
Источник
Ldap error invalid credentials error code 49
This forum has migrated to Microsoft Q&A. Visit Microsoft Q&A to post new questions.
Asked by:

Question


We are developing a LDAP authentication against Active Directory, we met the follow errors, although the username and password are correct.
LDAP: error code 49 — 80090308: LdapErr: DSID-0C090334, comment: AcceptSecurityContext error, data 52e, vece
The user detail is: CN=Peter, Lia ,OU=DEV,OU=HK_U,OU=cita,OU=US,DC=achtest,DC=local
As you may saw, the last name of this user has a backslash, plus a space in CN, we guess it may be the problem, since other users don’t have this problem if the last name of users don’t have a backslash and a space.
However we don’t know how we can add a new user to duplicate this issue, since it’s not way to add a new user with space in the end of name, the Active Directory will auto trim the space when system save the new user to database.
My questions are:
1. Do you have this kind of experience? Any idea to resolve?
2. How we can add a new user with a space in the end of last name? and then we can replicate this issue again?
Источник
LDAP Integration — Bind failed: 49: Invalid credentials #4177
Steps to reproduce
- Connect to LDAP Server, Configuration OK. 301 Users found, they show up in User category.
2.Try to log in with a user, using the ‘username’ displayed in NC
3.Wrong Password shows up and user is rejected, log says Bind failed: 49: Invalid credentials
Expected behaviour
User should be authenticated and logged in
Actual behaviour
User is rejected
Server configuration
Operating system:
Ubuntu 12.04.5 LTS
Web server:
Apache2
Database:
MySql
PHP version:
PHP 7.0.15-0ubuntu0.16.04.4
Nextcloud version: (see Nextcloud admin page)
11,0,2,7
Updated from an older Nextcloud/ownCloud or fresh install:
Fresh install
Where did you install Nextcloud from:
Tar from official website: Nextcloud-11.0.2.tar.bz2
Signing status:
List of activated apps:
- activity: 2.4.1
- admin_audit: 1.1.0
- comments: 1.1.0
- dav: 1.1.1
- federatedfilesharing: 1.1.1
- federation: 1.1.1
- files: 1.6.1
- files_pdfviewer: 1.0.1
- files_sharing: 1.1.1
- files_texteditor: 2.2
- files_trashbin: 1.1.0
- files_versions: 1.4.0
- files_videoplayer: 1.0.0
- firstrunwizard: 2.0
- gallery: 16.0.0
- logreader: 2.0.0
- lookup_server_connector: 1.0.0
- nextcloud_announcements: 1.0
- notifications: 1.0.1
- provisioning_api: 1.1.0
- serverinfo: 1.1.1
- sharebymail: 1.0.1
- survey_client: 0.1.5
- systemtags: 1.1.3
- theming: 1.1.1
- twofactor_backupcodes: 1.0.0
- updatenotification: 1.1.1
- user_external: 0.4
- user_ldap: 1.1.2
- workflowengine: 1.1.1
Disabled: - encryption
- external
- files_accesscontrol
- files_automatedtagging
- files_external
- files_retention
- password_policy
- templateeditor
- user_saml
The content of config/config.php:
Are you using external storage, if yes which one: local/smb/sftp/.
no
Are you using encryption: yes/no
no
Are you using an external user-backend, if yes which one: LDAP/ActiveDirectory/Webdav/.
LDAP:
Kerberos with LDAP as login agent
LDAP configuration (delete this part if not used)
Client configuration
Browser:
Operating system:
Web server error log
Nextcloud log (data/nextcloud.log)
+——————————-+————————————————————————————-+
| Configuration | s01 |
+——————————-+————————————————————————————-+
| hasMemberOfFilterSupport | |
| hasPagedResultSupport | |
| homeFolderNamingRule | |
| lastJpegPhotoLookup | 0 |
| ldapAgentName | cn=ADMIN,dc=ds,dc=local |
| ldapAgentPassword | *** |
| ldapAttributesForGroupSearch | |
| ldapAttributesForUserSearch | |
| ldapBackupHost | |
| ldapBackupPort | |
| ldapBase | dc=ds,dc=local |
| ldapBaseGroups | dc=ds,dc=local |
| ldapBaseUsers | ou=people,dc=ds,dc=local |
| ldapCacheTTL | 600 |
| ldapConfigurationActive | 1 |
| ldapDynamicGroupMemberURL | |
| ldapEmailAttribute | mail |
| ldapExperiencedAdmin | 0 |
| ldapExpertUUIDGroupAttr | |
| ldapExpertUUIDUserAttr | |
| ldapExpertUsernameAttr | uid |
| ldapGroupDisplayName | cn |
| ldapGroupFilter | (&(|(objectclass=posixGroup))) |
| ldapGroupFilterGroups | |
| ldapGroupFilterMode | 1 |
| ldapGroupFilterObjectclass | posixGroup |
| ldapGroupMemberAssocAttr | memberUid |
| ldapHost | teller.ds.local |
| ldapIgnoreNamingRules | |
| ldapLoginFilter | (&(|(objectclass=inetOrgPerson))(uid=%uid)) |
| ldapLoginFilterAttributes | |
| ldapLoginFilterEmail | 0 |
| ldapLoginFilterMode | 1 |
| ldapLoginFilterUsername | 1 |
| ldapNestedGroups | 1 |
| ldapOverrideMainServer | |
| ldapPagingSize | 1000 |
| ldapPort | 389 |
| ldapQuotaAttribute | |
| ldapQuotaDefault | |
| ldapTLS | 0 |
| ldapUserDisplayName | cn |
| ldapUserDisplayName2 | |
| ldapUserFilter | (|(objectclass=inetOrgPerson)(objectclass=krb5Principal)(objectclass=posixAccount)) |
| ldapUserFilterGroups | |
| ldapUserFilterMode | 0 |
| ldapUserFilterObjectclass | inetOrgPerson;krb5Principal;posixAccount |
| ldapUuidGroupAttribute | auto |
| ldapUuidUserAttribute | auto |
| turnOffCertCheck | 1 |
| turnOnPasswordChange | 0 |
| useMemberOfToDetectMembership | 1 |
+——————————-+————————————————————————————-+
+——————————-+—————+
| Configuration | s02 |
+——————————-+—————+
| hasMemberOfFilterSupport | 0 |
| hasPagedResultSupport | |
| homeFolderNamingRule | |
| lastJpegPhotoLookup | 0 |
| ldapAgentName | |
| ldapAgentPassword | *** |
| ldapAttributesForGroupSearch | |
| ldapAttributesForUserSearch | |
| ldapBackupHost | |
| ldapBackupPort | |
| ldapBase | |
| ldapBaseGroups | |
| ldapBaseUsers | |
| ldapCacheTTL | 600 |
| ldapConfigurationActive | 0 |
| ldapDynamicGroupMemberURL | |
| ldapEmailAttribute | |
| ldapExperiencedAdmin | 0 |
| ldapExpertUUIDGroupAttr | |
| ldapExpertUUIDUserAttr | |
| ldapExpertUsernameAttr | |
| ldapGroupDisplayName | cn |
| ldapGroupFilter | |
| ldapGroupFilterGroups | |
| ldapGroupFilterMode | 0 |
| ldapGroupFilterObjectclass | |
| ldapGroupMemberAssocAttr | uniqueMember |
| ldapHost | |
| ldapIgnoreNamingRules | |
| ldapLoginFilter | |
| ldapLoginFilterAttributes | |
| ldapLoginFilterEmail | 0 |
| ldapLoginFilterMode | 0 |
| ldapLoginFilterUsername | 1 |
| ldapNestedGroups | 0 |
| ldapOverrideMainServer | |
| ldapPagingSize | 500 |
| ldapPort | |
| ldapQuotaAttribute | |
| ldapQuotaDefault | |
| ldapTLS | 0 |
| ldapUserDisplayName | displayName |
| ldapUserDisplayName2 | |
| ldapUserFilter | |
| ldapUserFilterGroups | |
| ldapUserFilterMode | 0 |
| ldapUserFilterObjectclass | |
| ldapUuidGroupAttribute | auto |
| ldapUuidUserAttribute | auto |
| turnOffCertCheck | 0 |
| turnOnPasswordChange | 0 |
| useMemberOfToDetectMembership | 1 |
+——————————-+—————+
Browser log
Due to personal info and IP’s I can’t admitt the log. Putting warnings and errors here.
Warning user_ldap Bind failed: 49: Invalid credentials
Warning core Login failed: ‘Username’
Error index OCServerNotAvailableException: Connection to LDAP server could not be established (This one might have showed up when I was tinkering and is probably not a permanent one)
Error PHP ldap_search(): Partial search results returned: Sizelimit exceeded at /var/www/nextcloud/apps/user_ldap/lib/LDAP.php#293
The text was updated successfully, but these errors were encountered:
Источник
In my previous post, you learned how to troubleshoot HTTP Error 503. Today, we will look into how to troubleshoot 401 – Unauthorized: Access is denied due to invalid credentials in Internet Information Services (IIS).
Contents
- 401 – Unauthorized
- How IIS authentication works
- Cause of error
- Debugging the error
- Resolving the error
- Common 401 substatus codes
- Conclusion
- Author
- Recent Posts
![]()
Surender Kumar has more than twelve years of experience in server and network administration. His fields of interest are Windows Servers, Active Directory, PowerShell, web servers, networking, Linux, virtualization, and penetration testing. He loves writing for his blog.
![]()
Latest posts by Surender Kumar (see all)
- Backup in Proxmox VE — Thu, Jan 26 2023
- Snapshots in Proxmox VE — Wed, Jan 25 2023
- Create a Windows VM in Proxmox VE — Fri, Jan 13 2023
401 – Unauthorized

401 Unauthorized Access is denied due to invalid credentials
The 401 – Unauthorized: Access is denied due to invalid credentials error is a common access-related error that you may experience with a website hosted on IIS.
How IIS authentication works
The error itself indicates that it is caused by a failure to authorize access. Someone who is a beginner in IIS could find the error description «you do not have permission to view this directory or page using the credentials that you supplied» slightly confusing. If you think from an end user’s perspective, you might be wondering when you supplied any credentials while accessing the website. Well, this happened automatically on the server side. By default, every website hosted on IIS has anonymous authentication enabled.
If you open the IIS Manager, select your website, and then double-click Authentication under the IIS section in the Features view, you will see the various authentication modes (such as basic authentication, forms authentication, anonymous authentication, etc.) that are supported by IIS.
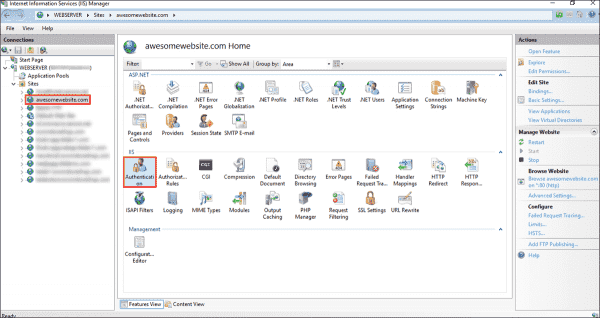
Viewing various authentication modes supported by a website in IIS
Each website has to have at least one authentication mode enabled and, by default, Anonymous Authentication mode enabled. Authentication is a mechanism that is used to verify the visitor’s identity to your website. See the following screenshot for reference:
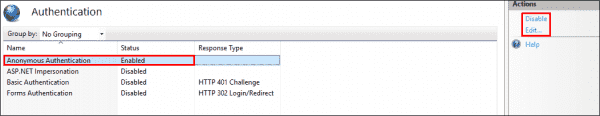
Default authentication modes supported by a website in IIS
Anonymous authentication allows visitors to access the public content of your website anonymously without having to supply any credentials. If you don’t want to use it, select the authentication mode, and then click Disable in the Actions pane on the right. To view or modify which credentials are used by anonymous authentication, click the Edit link on the right. You will see two options, as shown in the following screenshot:

View or modify the credentials used by anonymous authentication in IIS
By default, each website is set to use the IUSR user for anonymous user identity, which is a built-in account starting with IIS version 7. If you are using a custom username as the application pool identity, make sure you select the application pool identity option here. This way, you don’t have to worry about updating the user’s password in the website configuration over and over when the user’s password is changed.
Cause of error
The primary cause of the 401 – Unauthorized: Access is denied due to invalid credentials error is that you are using a custom username as the application pool identity. In simple terms, when you set the application pool to use a custom application pool identity (a custom username and password) rather than the default identity (which is ApplicationPoolIdentity), the Anonymous Authentication mode of the website continues using the IUSR user for authentication, which results in this error.
Debugging the error
As discussed in previous posts, the error page we saw above is a custom error page and does not reveal much helpful information for administrators. If you enable the detailed errors, you will see an error page with much detailed information, as shown in the following screenshot:
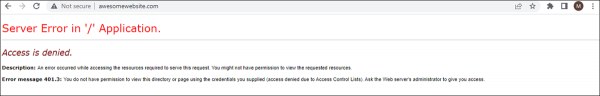
Error message 401.3 – You do not have permission to view this directory or page using the credentials you supplied (access denied due to Access Control Lists)
The detailed error gave you the HTTP 401.3 status code, which will guide you in checking the access control permissions on the file system. Make sure that the user who is set as the application pool identity has the read and execute permissions on the website’s root directory. If the error persists, the most likely cause is incorrect anonymous user identity. The following screenshot shows the problematic scenario:

Mismatched application pool identity and anonymous authentication identity user in IIS
The screenshot shows a mismatched application pool identity and anonymous authentication identity on the website, which is causing the error. For a website to work properly, both should be the same.
Resolving the error
Now that you know the cause of the HTTP 401.3 status code, do the following to fix the error:
If you are using a custom username as the application pool identity, make sure that the user has read and execute permissions on the website’s root directory.

Ensuring that the custom application pool user has read and execute permissions on the root directory
If you’re using the default ApplicationPoolIdentity for your application pool, make sure that the built-in IUSR user or IIS_IUSRS group has exactly the same permissions as shown in the screenshot below.
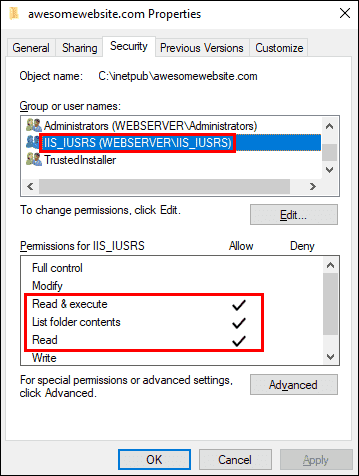
Ensuring that the default application pool identity has read and execute permissions on the root directory
If the error persists, edit the Anonymous Authentication setting of your website, as explained in the How IIS authentication works section. Be sure it is set to use the Application pool identity. See the following screenshot for reference:
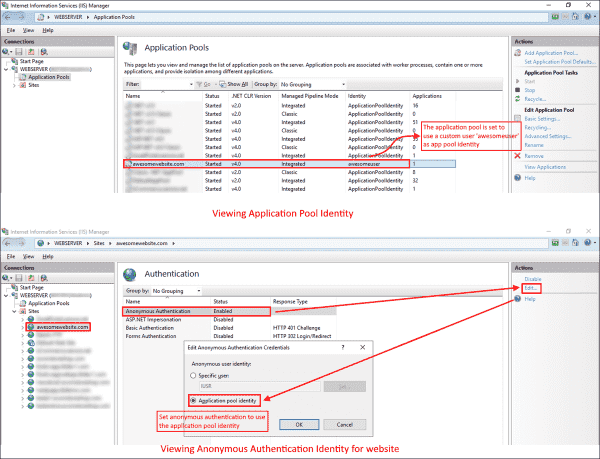
Modifying the anonymous authentication identity to match the application pool identity in IIS
Common 401 substatus codes
The following table covers the most common HTTP 401 substatus codes, along with their possible causes and troubleshooting advice:
Subscribe to 4sysops newsletter!
| Status Code | Possible Cause | Troubleshooting Advice |
| 401.1 | Logon failed | The logon attempt failed, probably due to an invalid user name or password. |
| 401.2 | Logon failed due to server configuration | The 401.2 status code indicates that there is a problem in the authentication configuration on the server. |
| 401.3 | Unauthorized due to ACL on resource | We covered how to fix this error above. |
Conclusion
I hope you’re enjoying this series of resolving common HTTP errors. In the next post, we will discuss how to fix the HTTP Error 403.14 – Forbidden error.
- Remove From My Forums
-
Вопрос
-
Здравствуйте!
Имеем сервер, RAID контроллер Intel, ОС — Windows Server 2016
C сайта Intel для данного контроллера скачал утилиту управления — RAID Web Console 3.
При запуске утилиты требуется ввести логин и пароль администратора (пользователь с правами администратора Windows). При вводе как локального так и доменного администратора выдается ошибка
«Error Code:49 : Invalid Credentials».Данная утилита использует LSI Storage Authority, в интернете нашел статью с данной проблемой
https://www.broadcom.com/support/knowledgebase/1211236746276/error-code-49-invalid-credentials-when-trying-to-login-to-lsa
в которой говорится что данная проблема возникает из за того LSA поддерживает только английский и поэтому не может правильно трактовать группы отличающиеся
от «Administrators». Предлагается изменить один параметр в конфигурационном файле на «Администраторы».В моем случае изменение параметра не помогло.
Проверял также на Windows 7, Windows 10 и Server 2019 — везде ошибка при входе.
Как решить данную проблему?
Ответы
-
Получил ответ из официальной поддержки Intel.
Подтверждена поддержка консолью только английского языка (были внесены соответствующие изменения в руководство по установке консоли).
Предложено два решения. Для обоих необходимо создать локального пользователя из латинских символов, входящего в группу «Администраторы».
1. Уже приводил ссылку на такое решение. Необходимо изменить
в файлеC:Program Files(x86)LSILSIStorageAuthorityconfLSA.conf
параметр full_access_groups = Administrators на full_access_groups =
АдминистраторыПерезапустить службы или перезагрузить компьютер.
Пробовал данное решение как писал выше но не сработало, наверно из за того что параметр я копировал из статьи, возможно вставлялся пробел или какой либо другой символ. Когда набрал вручную, все заработало.
2. Переименовать через консоль «Управление компьютером» группу «Администраторы» в группу «Administrators» и перезагрузить компьютер.
Данный вариант не пробовал.
-
Помечено в качестве ответа
5 марта 2020 г. 8:17
-
Помечено в качестве ответа
Импорт из AD, ошибка #165, invalid credentials
Добрый день.
При импорте пользователей из AD возникает ошибка.
Как ее решить?
Вложения
Screenshot.png (12.41 КБ) Просмотров: 2120
Здравствуйте. У вас есть кнопка «Помощь» в окне с ошибкой. Нажмите её, откроется справка, там написано, из-за чего может происходить такая ошибка.
Цитата из справки:
#49
LDAP_INVALID_CREDENTIALS
•логин или пароль для подключения указаны неверно;
•срок действия пароля истёк;
•учётная запись заблокирована;
•система обнаружения вторжений заблокировала учётную запись.
Team lead
Чат со мной
Учетные данные указанны верно.
На стороне сервера ошибка по памяти при закрытии которой сервер чата вываливается.
Журнал сервера и скрин ошибки направил на вашу почту.
0
1
Всем привет. Использую NSS_LDAP для атворизации SSH по доменному имени пользователя AD.
Настроил Nslcd.conf на свой домен
dc=office
binddn cn=testuser,dc=office
bindpw testpass
Перезагружаю nslcd.
Пытаюсь получить пароли
getent passwd и в логах syslog вижу, что
<passwd(all)> no available LDAP server found: Invalid credentials
Пользователь есть, пароль верный. Время настроено верно на обоих серверах. Мб я что-то упустил? Подскажите, пожалуйста
Тестирую так же через ldapsearch — та же ошибка (Invalid Credentials)
In my previous post, you learned how to troubleshoot HTTP Error 503. Today, we will look into how to troubleshoot 401 – Unauthorized: Access is denied due to invalid credentials in Internet Information Services (IIS).
Contents
- 401 – Unauthorized
- How IIS authentication works
- Cause of error
- Debugging the error
- Resolving the error
- Common 401 substatus codes
- Conclusion
- Author
- Recent Posts
![]()
Surender Kumar has more than twelve years of experience in server and network administration. His fields of interest are Windows Servers, Active Directory, PowerShell, web servers, networking, Linux, virtualization, and penetration testing. He loves writing for his blog.
![]()
401 – Unauthorized

401 Unauthorized Access is denied due to invalid credentials
The 401 – Unauthorized: Access is denied due to invalid credentials error is a common access-related error that you may experience with a website hosted on IIS.
How IIS authentication works
The error itself indicates that it is caused by a failure to authorize access. Someone who is a beginner in IIS could find the error description «you do not have permission to view this directory or page using the credentials that you supplied» slightly confusing. If you think from an end user’s perspective, you might be wondering when you supplied any credentials while accessing the website. Well, this happened automatically on the server side. By default, every website hosted on IIS has anonymous authentication enabled.
If you open the IIS Manager, select your website, and then double-click Authentication under the IIS section in the Features view, you will see the various authentication modes (such as basic authentication, forms authentication, anonymous authentication, etc.) that are supported by IIS.

Viewing various authentication modes supported by a website in IIS
Each website has to have at least one authentication mode enabled and, by default, Anonymous Authentication mode enabled. Authentication is a mechanism that is used to verify the visitor’s identity to your website. See the following screenshot for reference:

Default authentication modes supported by a website in IIS
Anonymous authentication allows visitors to access the public content of your website anonymously without having to supply any credentials. If you don’t want to use it, select the authentication mode, and then click Disable in the Actions pane on the right. To view or modify which credentials are used by anonymous authentication, click the Edit link on the right. You will see two options, as shown in the following screenshot:

View or modify the credentials used by anonymous authentication in IIS
By default, each website is set to use the IUSR user for anonymous user identity, which is a built-in account starting with IIS version 7. If you are using a custom username as the application pool identity, make sure you select the application pool identity option here. This way, you don’t have to worry about updating the user’s password in the website configuration over and over when the user’s password is changed.
Cause of error
The primary cause of the 401 – Unauthorized: Access is denied due to invalid credentials error is that you are using a custom username as the application pool identity. In simple terms, when you set the application pool to use a custom application pool identity (a custom username and password) rather than the default identity (which is ApplicationPoolIdentity), the Anonymous Authentication mode of the website continues using the IUSR user for authentication, which results in this error.
Debugging the error
As discussed in previous posts, the error page we saw above is a custom error page and does not reveal much helpful information for administrators. If you enable the detailed errors, you will see an error page with much detailed information, as shown in the following screenshot:

Error message 401.3 – You do not have permission to view this directory or page using the credentials you supplied (access denied due to Access Control Lists)
The detailed error gave you the HTTP 401.3 status code, which will guide you in checking the access control permissions on the file system. Make sure that the user who is set as the application pool identity has the read and execute permissions on the website’s root directory. If the error persists, the most likely cause is incorrect anonymous user identity. The following screenshot shows the problematic scenario:

Mismatched application pool identity and anonymous authentication identity user in IIS
The screenshot shows a mismatched application pool identity and anonymous authentication identity on the website, which is causing the error. For a website to work properly, both should be the same.
Resolving the error
Now that you know the cause of the HTTP 401.3 status code, do the following to fix the error:
If you are using a custom username as the application pool identity, make sure that the user has read and execute permissions on the website’s root directory.

Ensuring that the custom application pool user has read and execute permissions on the root directory
If you’re using the default ApplicationPoolIdentity for your application pool, make sure that the built-in IUSR user or IIS_IUSRS group has exactly the same permissions as shown in the screenshot below.

Ensuring that the default application pool identity has read and execute permissions on the root directory
If the error persists, edit the Anonymous Authentication setting of your website, as explained in the How IIS authentication works section. Be sure it is set to use the Application pool identity. See the following screenshot for reference:

Modifying the anonymous authentication identity to match the application pool identity in IIS
Common 401 substatus codes
The following table covers the most common HTTP 401 substatus codes, along with their possible causes and troubleshooting advice:
Subscribe to 4sysops newsletter!
| Status Code | Possible Cause | Troubleshooting Advice |
| 401.1 | Logon failed | The logon attempt failed, probably due to an invalid user name or password. |
| 401.2 | Logon failed due to server configuration | The 401.2 status code indicates that there is a problem in the authentication configuration on the server. |
| 401.3 | Unauthorized due to ACL on resource | We covered how to fix this error above. |
Conclusion
I hope you’re enjoying this series of resolving common HTTP errors. In the next post, we will discuss how to fix the HTTP Error 403.14 – Forbidden error.
