vadjunik
#1
Оставлено
:
9 сентября 2017 г. 18:36:02(UTC)

Статус: Активный участник
Группы: Участники
Зарегистрирован: 09.12.2016(UTC)
Сообщений: 127

Откуда: Таганрог
Сказал «Спасибо»: 15 раз
Приветствую! Столкнулся с проблемой — некорректно (как я понимаю) формируется запрос на сертификат.
Прошерстил форум, именно такой связки проблем и технологий не нашел, встреченные рекомендации пробовал — не помогает( В документации тоже ответов не нашлось (может не там искал?)
Имеем на клиентах, браузеры
GH 61.0.3163.79 (версия плагина КриптоПро 2.0.13027) (обновил в надежде на решение проблемы, не помогло, как видно)
FF 55.0.3 (версия плагина КриптоПро 2.0.12888)
Соответственно,
используется асинхронный вариант
API.
Сразу уточню,
при запросе через API уровня ОС (работает старый NPAPI-шный плагин) — все четко
.
КриптоПро CSP: 4.0.9907
Версия ядра: 4.0.9015 КС1
При запросе указываю параметры провайдера:
Тип: 80
Имя: Crypto-Pro GOST R 34.10-2012 Cryptographic Service Provider
На сервере используется штатный майкрософтовский УЦ, котором в качестве криптопровайдера указан КриптоПро (GOST R 34.10-2012).
КриптоПро CSP: 4.0.9842
Версия ядра: 4.0.9014 КС1
Код запроса отрабатывает корретно.
Код:
<script type="text/javascript">
var ENROLL_X500NAME_FLAGS = {
XCN_CERT_NAME_STR_NONE : 0,
XCN_CERT_SIMPLE_NAME_STR : 0x00000001, // Это флаг плагину не нравится, ругается: The parameter is incorrect. (0x80070057)
XCN_CERT_OID_NAME_STR : 0x00000002,
XCN_CERT_X500_NAME_STR : 0x00000003,
XCN_CERT_XML_NAME_STR : 0x00000004,
XCN_CERT_NAME_STR_SEMICOLON_FLAG : 0x40000000,
XCN_CERT_NAME_STR_NO_PLUS_FLAG : 0x20000000,
XCN_CERT_NAME_STR_NO_QUOTING_FLAG : 0x10000000,
XCN_CERT_NAME_STR_CRLF_FLAG : 0x8000000,
XCN_CERT_NAME_STR_COMMA_FLAG : 0x4000000,
XCN_CERT_NAME_STR_REVERSE_FLAG : 0x2000000,
XCN_CERT_NAME_STR_FORWARD_FLAG : 0x1000000,
XCN_CERT_NAME_STR_DISABLE_IE4_UTF8_FLAG : 0x10000,
XCN_CERT_NAME_STR_ENABLE_T61_UNICODE_FLAG : 0x20000,
XCN_CERT_NAME_STR_ENABLE_UTF8_UNICODE_FLAG : 0x40000,
XCN_CERT_NAME_STR_FORCE_UTF8_DIR_STR_FLAG : 0x80000,
XCN_CERT_NAME_STR_DISABLE_UTF8_DIR_STR_FLAG : 0x100000
};
function(fullName, providerType, providerName)
{
// Ф-я ExecWithPlugin просто обертка над cadesplugin.async_spawn, перехватывающая и расшифровывающая ошибки.
ExecWithPlugin(function* () {
// Ф-я GetEnrollObject - обертка для создания асинхронного объекта из пространства имен X509Enrollment
var privateKey = yield* GetEnrollObject("CX509PrivateKey");
yield privateKey.propset_ProviderName(providerName);
yield privateKey.propset_ProviderType(providerType);
yield privateKey.propset_KeySpec(ENROLL_X509KEYSPEC.XCN_AT_SIGNATURE);
var certificateRequestPkcs10 = yield* GetEnrollObject("CX509CertificateRequestPkcs10");
yield certificateRequestPkcs10.InitializeFromPrivateKey(ENROLL_CONTEXT.ContextUser, privateKey, "");
var distinguishedName = yield* GetEnrollObject("CX500DistinguishedName");
// fullName - проиндексированный OID(ами) массив значений для RDN.
var certName = "";
var oids = Object.keys(fullName);
for(var i = 0; i < oids.length; i++){
if (certName != "")
certName += ", ";
certName += (oids[i] + "=" + fullName[oids[i]]);
}
yield distinguishedName.Encode(certName, ENROLL_X500NAME_FLAGS.XCN_CERT_NAME_STR_NONE);
yield certificateRequestPkcs10.propset_Subject(distinguishedName);
var keyUsageExtension = yield* GetEnrollObject("CX509ExtensionKeyUsage");
yield keyUsageExtension.InitializeEncode(
ENROLL_X509KEYUSAGE_FLAGS.XCN_CERT_KEY_ENCIPHERMENT_KEY_USAGE |
ENROLL_X509KEYUSAGE_FLAGS.XCN_CERT_DATA_ENCIPHERMENT_KEY_USAGE |
ENROLL_X509KEYUSAGE_FLAGS.XCN_CERT_DIGITAL_SIGNATURE_KEY_USAGE |
ENROLL_X509KEYUSAGE_FLAGS.XCN_CERT_NON_REPUDIATION_KEY_USAGE);
yield (yield certificateRequestPkcs10.X509Extensions).Add(keyUsageExtension);
var enroll = yield* GetEnrollObject("CX509Enrollment");
yield enroll.InitializeFromRequest(certificateRequestPkcs10);
// Пробовал менять тип кодировки при значении XCN_CRYPT_STRING_BINARY получаю:
// Данные ASN1 повреждены. 0x80093103 (ASN: 259)
// А при XCN_CRYPT_STRING_NOCR - Падает сам плагин (в Хроме).
// Сигнатура проблемы:
// Имя события проблемы: APPCRASH
// Имя приложения: nmcades.exe
// Версия приложения: 1.0.10478.0
// Отметка времени приложения: 597d48c9
// Имя модуля с ошибкой: nmcades.exe
// Версия модуля с ошибкой: 1.0.10478.0
// Отметка времени модуля с ошибкой: 597d48c9
// Код исключения: 40000015
// Смещение исключения: 000166f5
// Версия ОС: 6.1.7601.2.1.0.256.48
// Код языка: 1049
// Дополнительные сведения 1: 177b
// Дополнительные сведения 2: 177b64d1b0e35f4876ae099d0b42016e
// Дополнительные сведения 3: 7793
// Дополнительные сведения 4: 7793eef4e9c0c3a122a47f8bca2bf0a0
var certReq = yield enroll.CreateRequest(ENROLL_ENCODING_TYPE.XCN_CRYPT_STRING_BASE64);
var containerName = yield privateKey.ContainerName;
});
}
</script>
Значения флагов и констант взяты из MSDN, только флаги в ENROLL_X500NAME_FLAGS привел к единообразному 16-ричному виду, может как-то не так (добавил в исходник сюда)?
Но в итоге на сервере, при отправке запроса ЦС, получаю сообщение:
Встречено неверное значение тега ASN1. 0x8009310b (ASN: 267)
Кроме экспериментов с кодировкой самого запроса, пробовал по всякому формировать RDN (штано OID=значение) через «, «. Никаких изменений ( Руками делал строку, в которой забирал значения параметров с пробелами в кавычки, результат прежний.
Вот тут сам файл запроса, уже приехавший на сервер.
Может глаза замылились не вижу очевидной ошибки?
![]()
vadjunik
#1
Оставлено
:
9 сентября 2017 г. 18:36:02(UTC)

Статус: Активный участник
Группы: Участники
Зарегистрирован: 09.12.2016(UTC)
Сообщений: 127

Откуда: Таганрог
Сказал «Спасибо»: 15 раз
Приветствую! Столкнулся с проблемой — некорректно (как я понимаю) формируется запрос на сертификат.
Прошерстил форум, именно такой связки проблем и технологий не нашел, встреченные рекомендации пробовал — не помогает( В документации тоже ответов не нашлось (может не там искал?)
Имеем на клиентах, браузеры
GH 61.0.3163.79 (версия плагина КриптоПро 2.0.13027) (обновил в надежде на решение проблемы, не помогло, как видно)
FF 55.0.3 (версия плагина КриптоПро 2.0.12888)
Соответственно,
используется асинхронный вариант
API.
Сразу уточню,
при запросе через API уровня ОС (работает старый NPAPI-шный плагин) — все четко
.
КриптоПро CSP: 4.0.9907
Версия ядра: 4.0.9015 КС1
При запросе указываю параметры провайдера:
Тип: 80
Имя: Crypto-Pro GOST R 34.10-2012 Cryptographic Service Provider
На сервере используется штатный майкрософтовский УЦ, котором в качестве криптопровайдера указан КриптоПро (GOST R 34.10-2012).
КриптоПро CSP: 4.0.9842
Версия ядра: 4.0.9014 КС1
Код запроса отрабатывает корретно.
Код:
<script type="text/javascript">
var ENROLL_X500NAME_FLAGS = {
XCN_CERT_NAME_STR_NONE : 0,
XCN_CERT_SIMPLE_NAME_STR : 0x00000001, // Это флаг плагину не нравится, ругается: The parameter is incorrect. (0x80070057)
XCN_CERT_OID_NAME_STR : 0x00000002,
XCN_CERT_X500_NAME_STR : 0x00000003,
XCN_CERT_XML_NAME_STR : 0x00000004,
XCN_CERT_NAME_STR_SEMICOLON_FLAG : 0x40000000,
XCN_CERT_NAME_STR_NO_PLUS_FLAG : 0x20000000,
XCN_CERT_NAME_STR_NO_QUOTING_FLAG : 0x10000000,
XCN_CERT_NAME_STR_CRLF_FLAG : 0x8000000,
XCN_CERT_NAME_STR_COMMA_FLAG : 0x4000000,
XCN_CERT_NAME_STR_REVERSE_FLAG : 0x2000000,
XCN_CERT_NAME_STR_FORWARD_FLAG : 0x1000000,
XCN_CERT_NAME_STR_DISABLE_IE4_UTF8_FLAG : 0x10000,
XCN_CERT_NAME_STR_ENABLE_T61_UNICODE_FLAG : 0x20000,
XCN_CERT_NAME_STR_ENABLE_UTF8_UNICODE_FLAG : 0x40000,
XCN_CERT_NAME_STR_FORCE_UTF8_DIR_STR_FLAG : 0x80000,
XCN_CERT_NAME_STR_DISABLE_UTF8_DIR_STR_FLAG : 0x100000
};
function(fullName, providerType, providerName)
{
// Ф-я ExecWithPlugin просто обертка над cadesplugin.async_spawn, перехватывающая и расшифровывающая ошибки.
ExecWithPlugin(function* () {
// Ф-я GetEnrollObject - обертка для создания асинхронного объекта из пространства имен X509Enrollment
var privateKey = yield* GetEnrollObject("CX509PrivateKey");
yield privateKey.propset_ProviderName(providerName);
yield privateKey.propset_ProviderType(providerType);
yield privateKey.propset_KeySpec(ENROLL_X509KEYSPEC.XCN_AT_SIGNATURE);
var certificateRequestPkcs10 = yield* GetEnrollObject("CX509CertificateRequestPkcs10");
yield certificateRequestPkcs10.InitializeFromPrivateKey(ENROLL_CONTEXT.ContextUser, privateKey, "");
var distinguishedName = yield* GetEnrollObject("CX500DistinguishedName");
// fullName - проиндексированный OID(ами) массив значений для RDN.
var certName = "";
var oids = Object.keys(fullName);
for(var i = 0; i < oids.length; i++){
if (certName != "")
certName += ", ";
certName += (oids[i] + "=" + fullName[oids[i]]);
}
yield distinguishedName.Encode(certName, ENROLL_X500NAME_FLAGS.XCN_CERT_NAME_STR_NONE);
yield certificateRequestPkcs10.propset_Subject(distinguishedName);
var keyUsageExtension = yield* GetEnrollObject("CX509ExtensionKeyUsage");
yield keyUsageExtension.InitializeEncode(
ENROLL_X509KEYUSAGE_FLAGS.XCN_CERT_KEY_ENCIPHERMENT_KEY_USAGE |
ENROLL_X509KEYUSAGE_FLAGS.XCN_CERT_DATA_ENCIPHERMENT_KEY_USAGE |
ENROLL_X509KEYUSAGE_FLAGS.XCN_CERT_DIGITAL_SIGNATURE_KEY_USAGE |
ENROLL_X509KEYUSAGE_FLAGS.XCN_CERT_NON_REPUDIATION_KEY_USAGE);
yield (yield certificateRequestPkcs10.X509Extensions).Add(keyUsageExtension);
var enroll = yield* GetEnrollObject("CX509Enrollment");
yield enroll.InitializeFromRequest(certificateRequestPkcs10);
// Пробовал менять тип кодировки при значении XCN_CRYPT_STRING_BINARY получаю:
// Данные ASN1 повреждены. 0x80093103 (ASN: 259)
// А при XCN_CRYPT_STRING_NOCR - Падает сам плагин (в Хроме).
// Сигнатура проблемы:
// Имя события проблемы: APPCRASH
// Имя приложения: nmcades.exe
// Версия приложения: 1.0.10478.0
// Отметка времени приложения: 597d48c9
// Имя модуля с ошибкой: nmcades.exe
// Версия модуля с ошибкой: 1.0.10478.0
// Отметка времени модуля с ошибкой: 597d48c9
// Код исключения: 40000015
// Смещение исключения: 000166f5
// Версия ОС: 6.1.7601.2.1.0.256.48
// Код языка: 1049
// Дополнительные сведения 1: 177b
// Дополнительные сведения 2: 177b64d1b0e35f4876ae099d0b42016e
// Дополнительные сведения 3: 7793
// Дополнительные сведения 4: 7793eef4e9c0c3a122a47f8bca2bf0a0
var certReq = yield enroll.CreateRequest(ENROLL_ENCODING_TYPE.XCN_CRYPT_STRING_BASE64);
var containerName = yield privateKey.ContainerName;
});
}
</script>
Значения флагов и констант взяты из MSDN, только флаги в ENROLL_X500NAME_FLAGS привел к единообразному 16-ричному виду, может как-то не так (добавил в исходник сюда)?
Но в итоге на сервере, при отправке запроса ЦС, получаю сообщение:
Встречено неверное значение тега ASN1. 0x8009310b (ASN: 267)
Кроме экспериментов с кодировкой самого запроса, пробовал по всякому формировать RDN (штано OID=значение) через «, «. Никаких изменений ( Руками делал строку, в которой забирал значения параметров с пробелами в кавычки, результат прежний.
Вот тут сам файл запроса, уже приехавший на сервер.
Может глаза замылились не вижу очевидной ошибки?
We’ve seen a few instances of the following error message on 64 bit servers when IIS 7.0 is attempting to process a pending certificate request:
Complete Certificate Request
There was an error while performing this operation.
Details:
CertEnroll::CX509Enrollment::p_InstallResponse: ASN1 bad tag value met. 0x8009310b (ASN: 267)
This error seems to mean that the private key (created when the certificate request was made) does not match the public key (the .crt file). The keypair is not successfully joined into a working SSL certificate.
So far this behavior seems most common with .crt files (instead of the .cer files many of us are more used to) issued by one specific Certification Authority—which will remain nameless here.
The error shows up after reaching the point in the process where you ‘specify certificate authority response’ and guide the wizard to the ‘File name containing the certification authority’s response…’ (the .crt file).
So far there seem to be two solutions.
Solution 1:
Verisign has a support article that matches this error message: https://knowledge.verisign.com/support/ssl-certificates-support/index?page=content&id=S:SO8467&actp=…. Their recommendation seems to be to replace the certificate with a new one. This method has worked for at least one of my customers in this place with a GoDaddy certificate. All they had to do was make a new certificate request (CSR text file), log into the the Godaddy web interface and re-key (we chose re-key rather than re-issue) their certificate. The new file processed fine.
Solution 2:
Begin by importing the .crt file into the Personal certificate store for the local computer. (Start button > Run: MMC > File Menu > Add/Remove Snap-in > highlight Certificates snap-in and click the ADD button > select Computer Account and click Finish > Click OK > drill into Personal > Certificates > right-click and select All Tasks > select Import > guide to the .crt file.) At this point your certificate is basically a half-certificate. It is still missing its private key.
Second, double-click the crt certificate file you just imported, select the Details tab, scroll all the way down to Thumbprint and highlight Thumbprint. In the lower pane, block and copy all the letters of the thumbprint. Paste the thumbprint characters into notepad. Open the command prompt and run this command: Certutil /?
The command you’ll want to run is:
certutil -repairstore my «{insert all of the thumbprint characters here}»
When you see the response: “CertUtil: -repairstore command completed successfully” you should have a private key associated with the .crt file in the personal store. There should no longer be any need to run through the “Complete Certificate Request…” wizard. The certificate should show up in the IIS Manager’s list of server certificates at this point. It should also be available in the SSL Certificates drop-down list when attempting to edit the https binding for a website.
Incidentally, a common way of attempting to deal with this error is to take the .p7b file from the Certification Authority and import the CA’s certificates into the Trusted and Intermediate stores. As far as I can tell, this approach has no useful effect upon this problem.
Other relevant links:
https://knowledge.verisign.com/support/ssl-certificates-support/index?page=content&id=S:SO8467&actp=…
http://blogs.msdn.com/vijaysk/archive/2008/11/25/certenroll-cx509enrollment-p-installresponse-asn1-b…
Author: Christopher T. Haun
- Remove From My Forums
-
Question
-
Hi All,
I have recieved CSR request from App team but i am getting below error While creating Certificate in root CA.
Certificate Request Denied

Your certificate request was denied.
Your Request Id is 0. The disposition message is
«Error Parsing Request ASN1 bad tag value met. 0x8009310b (ASN: 267)».
Contact your administrator for further information.
Answers
-
Thanks Elke . Issue fixed . Application team send one more updated CSR and now i am able to create certificate .
- Marked as answer by
Tuesday, July 29, 2014 3:01 AM
- Marked as answer by
Solution
To verify that the SSL certificate is successfully installed, try to bind the certificate to the website.
To bind the certifcate to the appropriate website, perform the following steps:
- Click Start > Administrative Tools > Internet Information Services (IIS) Manager
- Browse to your Server Name > Sites > Your SSL-based site
- From the Actions pane, click Bindings
- In the Site Bindings window, click Add
- From the Add Site Bindings window, provide the binding type as HTTPS
- Select the SSL certificate that will be used for this site
- Click OK
- Test the if the site is secure by using HTTPS
If in step 6 above, the new certificate cannot be found in the list, try restoring the private key:
Import certificate in to the Computer certificate store
- Create a certificate snap-in in a Microsoft Management Console (MMC)
- In the left-hand pane, expand the Certificates folder, expand and select the Personal folder
- Right-click the Certificates folder inside the Personal folder, click All Tasks then Import
- The Certificate Import Wizard opens. Click Next
- Click Browse and then navigate to the file that contains the SSL certificate. Click Open > Next
- Ensure «Place all certificates in the following store» is selected, ensure that «Personal» is listed for the certificate store, click Next > Finish
Restore Private Key
- With the MMC still open, click the Certificates folder inside the Personal folder in the left-hand pane.
- Double-click the newly imported SSL certificate in the right-hand pane, then click the Details tab.
- Scroll down and click the Thumbprint field, then copy the entire thumbprint (in the bottom box) to the clipboard.
- Open a command prompt, then enter the following command:
certutil -repairstore my «<thumbprint>»
Example:
certutil -repairstore my «00 01 02 03 04 05 06 07 08 09 0a 0b 0c 0d 0e 0f»
If successful, the response will be «CertUtil: -repairstore command completed successfully«
Assign SSL certificate in IIS
- Open the IIS Manager application.
- From the Connections pane on the left, expand the local server, expand the Sites folder and select the website to be secured with SSL.
- From the Actions pane on the right, select the Bindings option (under Edit Site).
- In the Site Bindings window, select an existing https binding and click Edit. If there are no existing https bindings, click Add.
- Ensure the type is set to ‘https’, then select the new SSL certificate from the drop down menu. Click the View button to confirm details of the certificate, if necessary. Click OK > Close
If the above steps do not resolve the issue, an alternative method of installation using the X.509 version of the certificate can be attempted.
- Acquire the SSL certificate in X.509 (PKCS#10) format and install
- Obtain the Intermediate CA and install this via Microsoft Management Console
DigiCert SSL certificates for Microsoft servers are delivered in PKCS#7 format. This means the certificate file includes the corresponding Intermediate CA(s). To acquire the certificate in X.509 (PKCS#10) format, perform the following steps:
- Download the certificate via DigiCert Trust Center. Selecting «Other» as the server platform will provide the certificate in the X.509 (PKCS#10) format.
- Install the the X.509 (PKCS#10) certificate file.
- Download and install the Intermediate CA.
- Remove From My Forums
-
Question
-
Hi All,
I have recieved CSR request from App team but i am getting below error While creating Certificate in root CA.
Certificate Request Denied

Your certificate request was denied.
Your Request Id is 0. The disposition message is
«Error Parsing Request ASN1 bad tag value met. 0x8009310b (ASN: 267)».
Contact your administrator for further information.
Answers
-
Thanks Elke . Issue fixed . Application team send one more updated CSR and now i am able to create certificate .
- Marked as answer by
Tuesday, July 29, 2014 3:01 AM
- Marked as answer by
- Remove From My Forums
-
Question
-
Hi All,
I have recieved CSR request from App team but i am getting below error While creating Certificate in root CA.
Certificate Request Denied

Your certificate request was denied.
Your Request Id is 0. The disposition message is
«Error Parsing Request ASN1 bad tag value met. 0x8009310b (ASN: 267)».
Contact your administrator for further information.
Answers
-
Thanks Elke . Issue fixed . Application team send one more updated CSR and now i am able to create certificate .
- Marked as answer by
Tuesday, July 29, 2014 3:01 AM
- Marked as answer by
Обновлено 2023 января: перестаньте получать сообщения об ошибках и замедлите работу вашей системы с помощью нашего инструмента оптимизации. Получить сейчас в эту ссылку
- Скачайте и установите инструмент для ремонта здесь.
- Пусть он просканирует ваш компьютер.
- Затем инструмент почини свой компьютер.
Ошибка Windows 0x8009310B вызвана неподходящим закрытым ключом. Если закрытый ключ все еще находится на сервере, возможно установить сертификат и восстановить закрытый ключ. Следующее решение может исправить ошибку; если это не работает, сертификат должен быть заменен.
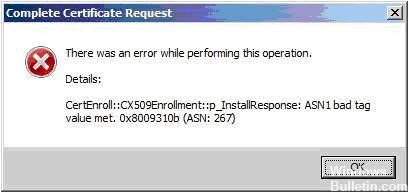
Восстановление поврежденного сертификата
Откройте командную строку DOS (cmd.exe).
Введите: certutil -repairstore мое «ЗНАЧЕНИЕ ПЕЧАТИ ИЛИ СЕРИЙНЫЙ НОМЕР».
Примечание. Если вы не уверены, что можете найти THUMBPRINT или СЕРИЮ, следуйте этим инструкциям. Кроме того, сертификат иногда недоступен и должен быть импортирован, чтобы эта команда работала. Если вы получили сообщение об ошибке, убедитесь, что используемая вами СЕРИЯ и / или ТЕМАТИЧЕСКАЯ ПЕЧАТЬ являются ТОЧНЫМИ, указанными в вашем сертификате, поскольку Windows иногда вставляет один или несколько вопросительных знаков, что приводит к ошибке.
Вернитесь в диспетчер IIS и снова измените ярлыки для этого сайта. (Где вы можете выбрать сертификат)
Примечание. Иногда вы получаете сообщение об ошибке, поэтому просто проигнорируйте ошибку и попробуйте снова. При повторной попытке может оказаться, что сертификат уже выбран, и больше ничего не нужно делать. Если вы не видите сертификат в списке, вам может потребоваться дать ему понятное имя в MMC, изменив его свойства.
Обновление за январь 2023 года:
Теперь вы можете предотвратить проблемы с ПК с помощью этого инструмента, например, защитить вас от потери файлов и вредоносных программ. Кроме того, это отличный способ оптимизировать ваш компьютер для достижения максимальной производительности. Программа с легкостью исправляет типичные ошибки, которые могут возникнуть в системах Windows — нет необходимости часами искать и устранять неполадки, если у вас под рукой есть идеальное решение:
- Шаг 1: Скачать PC Repair & Optimizer Tool (Windows 10, 8, 7, XP, Vista — Microsoft Gold Certified).
- Шаг 2: Нажмите «Начать сканирование”, Чтобы найти проблемы реестра Windows, которые могут вызывать проблемы с ПК.
- Шаг 3: Нажмите «Починить все», Чтобы исправить все проблемы.

Сканирование папки
1. нажмите на Пуск. выберите Run.
2. введите SIGVERIF в открытое поле.
3. нажмите на ОК
4. Нажмите кнопку «Дополнительно» и выберите «Искать другие файлы без цифровой подписи».
5. Нажмите кнопку «Обзор» в поле «Искать в этой папке» и укажите папку C: WINDOWS SYSTEM32 CATROOT.
6. Установите флажок «Включить подпапки».
7. нажмите ОК, затем на Пуск.
8. После завершения сканирования появится окно со списком неподписанных файлов.
Импорт сертификата в хранилище сертификатов компьютера
- Создание оснастки сертификата в консоли MMC от KB Solution SO1849
- На левой панели разверните папку «Сертификаты», разверните ее и выберите личную папку.
- Щелкните правой кнопкой мыши папку «Сертификаты» в личной папке, выберите «Все задачи», выберите «Импорт».
- Откроется Мастер импорта сертификатов. Нажмите на Далее
- Щелкните Обзор, затем перейдите к файлу, содержащему сертификат SSL. Нажмите «Открыть»> «Далее».
- Убедитесь, что выбрано «Поместить все сертификаты в следующий список», убедитесь, что в списке сертификатов указано «Личные», нажмите «Далее»> «Готово».
https://stackoverflow.com/questions/26011760/cryptdecodeobjectex-bad-tag-error-0x8009310b
Совет экспертов: Этот инструмент восстановления сканирует репозитории и заменяет поврежденные или отсутствующие файлы, если ни один из этих методов не сработал. Это хорошо работает в большинстве случаев, когда проблема связана с повреждением системы. Этот инструмент также оптимизирует вашу систему, чтобы максимизировать производительность. Его можно скачать по Щелчок Здесь

CCNA, веб-разработчик, ПК для устранения неполадок
Я компьютерный энтузиаст и практикующий ИТ-специалист. У меня за плечами многолетний опыт работы в области компьютерного программирования, устранения неисправностей и ремонта оборудования. Я специализируюсь на веб-разработке и дизайне баз данных. У меня также есть сертификат CCNA для проектирования сетей и устранения неполадок.
Сообщение Просмотров: 108
To totally unlock this section you need to Log-in
Login
Sometimes, during a «Complete Certification Request…» process, you could face the following error message on 64-bit servers when IIS 7.0 is attempting to process a pending certificate request:
Complete Certificate Request
There was an error while performing this operation.
Details:
CertEnroll::CX509Enrollment::p_InstallResponse: ASN1 bad tag value met. 0x8009310b (ASN: 267)
This error seems to mean that the private key (created when the certificate request was made) does not match the public key (the .crt file). The keypair is not successfully joined into a working SSL certificate.
So far this behavior seems most common with .crt files (instead of the .cer files many of us are more used to) issued by one specific Certification Authority, which will remain nameless here.
The error shows up after reaching the point in the process where you «Specify certificate authority response» and guide the wizard to the «File name containing the certification authority’s response…» (the .crt file).
Working Solution
Begin by importing the .crt file into the Personal certificate store for the local computer.
Go to Start > Run: MMC > File Menu > Add/Remove Snap-in > highlight Certificates snap-in and click the ADD button > select Computer Account and click Finish > Click OK > drill into Personal > Certificates > right-click and select All Tasks > select Import > guide to the .crt file.
At this point your certificate is basically a half-certificate. It is still missing its private key.
Second, double-click the .crt certificate file you just imported, select the Details tab, scroll all the way down to Thumbprint and highlight Thumbprint.
In the lower pane, block and copy all the letters of the thumbprint. Paste the thumbprint characters into notepad.
Open the command prompt and run this command: Certutil /?. The command you’ll want to run is:
certutil -repairstore my "{insert all of the thumbprint characters here}"
When you see the response: “CertUtil: -repairstore command completed successfully” you should have a private key associated with the .crt file in the personal store.
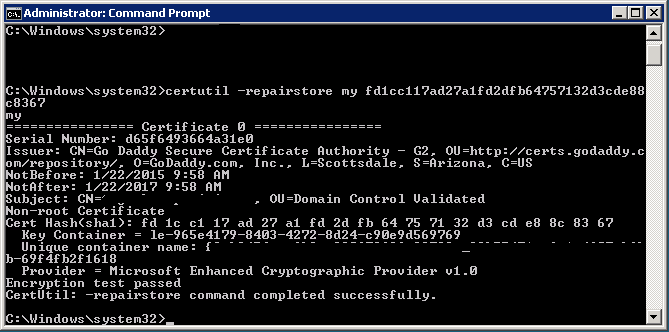
There should no longer be any need to run through the “Complete Certificate Request…” wizard.
The certificate should show up in the IIS Manager’s list of server certificates at this point. It should also be available in the SSL Certificates drop-down list when attempting to edit the https binding for a website.
|
|
|
- Remove From My Forums
-
Question
-
User-1286092494 posted
Hello… Is anyone seen this error when attempting to install a VeriSign chain certificate using IIS 7 server?
CertEnroll:CX509Enrolment:p_InstallResponse: ASN1 bad tag value met. 0x8009310b(ASN: 267)
I have search the internet to no avail… Any help is greatly appreciated.
Answers
-
- Marked as answer by
Anonymous
Tuesday, September 28, 2021 12:00 AM
- Marked as answer by
All replies
-
User113421904 posted
Hi,
I did see one post before that this error is related to permissions of certificate store. Are you running from administrative accounts, make sure you have enough permissions during the installing of certificates.
-
User-1286092494 posted
Thanks Zhao. I was wondering if you guys have any kind of knowledge base article that talks about this error within IIS 7 during an SSL certificate install? It would be great if there is one.
We would like to put this information in our knowledge base to better assist our customers at VeriSign.
Thank you for your support.
Regards,
Jason R.
-
- Marked as answer by
Anonymous
Tuesday, September 28, 2021 12:00 AM
- Marked as answer by
-
User1810624584 posted
I leave this behind for anyone else searching for an answer to this question. NOTE: I am not using a VeriSign certificate, so this is not directly pertinent to the original question. I leave it behind because the error message is the same and
hits on the search engines.I leave the message with double colons here so that search will pick it up more readily.
CertEnroll::CX509Enrollment::p_InstallResponse: ASN1 bad tag value met. 0x08009310b (ASN: 267)
I requested a certificate from an IIS 7.0 Web Server. I used the request to create a certificate within our internal CA and generate a .cer file. When I went to install the .cer file in the web server, I got hit with this error message.
It didn’t take too much digging to find a hint that perhaps the CA was not trusted by the Web Server. I added the internal CA chain to the Web Server and this got me past the message. Just to be sure, I removed the root certificate from the Trusted
Root Certification Authorities folder and tried again — I got the error again. This is a verified cause. Certainly this may not be the only cause. I sure wish the error message were better. -
User351018772 posted
I’ve had the same issue, below is my information…
- Windows 2008 Web Server 64-bit Edition
- IIS7
- SQL 2005 Express
- Network Solutions Basic SSL certificate
Each time I try to complete the certificate request I get the following error…
CertEnroll::CX509Enrollment::p_InstallResponse: ASN1 bad tag value met. 0x8009310b (ASN: 267)
I should also mention that I have already added the 3 other certificates provided by NetworkSolutions under the Certificates snap-in. When I open up IIS I do not see my certificate request listed however IIS knows that it’s there so I’m not sure if I should
see it listed or not. Under «Certificates -> Certificate Enrollment Requests -> Certificates» I can see the pending request. Up until a few minutes ago I had several listed there and have since cleared/deleted them out and re-requested the certificate
from NetworkSolutions although I don’t have any faith this will work. There were several from past failed attempts. Should I be able to see the certificate request in IIS7 after creating the initial request before it’s completed? My server doesn’t do much
other than host a few websites and run SQL 2005 Express. I know some have said something about SQL but I can’t imagine what that has to do with my situation since I simply want to add an SSL certificate to IIS7 to run a single website with SSL encryption.Is it just me or should this not be ridiculously simple to accomplish and yet it’s been the single most frustrating thing I had to do in a great long while. NetworkSolutions doesn’t have any answers, Microsoft wants to charge me an arm and leg just to say
«Hi», and I’m losing my patience with the whole thing since it should literally take less than 5 minutes to complete a simple certificate request.Does anyone out there have a solution to this problem because I’m Googled out…
Thanks in advance for any support provided,
Matt
-
User882081861 posted
I’d recommend contacting the certification authority and asking them what their preferred way is to abandon the problematic keypair and how to best make a totally new CSR.
-
User56899015 posted
This happened to me because I screwed up.Heres what I did:
I created a certificate request and sent it to the CA. I got the new cert and installed it.
Here’s where I went wrong:
I mis-typed the friendly name during the cert install and stupidly deleted the cert via IIS manager.
How I fixed it:
Take the initial certificate request file (sent to CA) and rename it with a .cer extension.
Open the certificate management snap in.
Right click on «Certificate Enrollment Requests» and import the certificate signing request file.
Go back to IIS Manager and import the certificate that the CA sent back in response to your initial request.Basically, you must have an unfulfilled certificate request corresponding to the certificate provided by your CA before «complete certificate request» is successful.
-
User1063753466 posted
greg88 — I just created this forum account to tell you that you are a genius. Your solution totally worked for me. -
User1180450644 posted
Gregg88 — Saved my butt too — thanks! -
User418653656 posted
I got the same error, through a mistake on my part, but the solution did not work for me.
I was using a GoDaddy cert, which had an intermediate certificate. I followed the instructions to import the GoDaddy intermediate cert into the «Certificates (Local Computer)/Intermediate Certification Authority/Certificates store.
Turns out, I apparently double clicked on the actual web site cert, which happily went in the store.
I think went to IIS which gave me the OP’s error.
Drove me nuts, until I found the web cert in the Intermediate Certification Authority. lol.
So, the fix for me was to export and delete the web site cert, import the proper intermediate cert, and then import the cert like normal into the «Certificates (Local Computer)/Personal/Certificates store.
Now, oddly, IIS still thinks there is a cert request outstanding. I’m assuming I can just ignore this, as I already have the cert loaded.
== John ==
-
User-1938893238 posted
«I mis-typed the friendly name during the cert install»
What does that mean? What defines a mis-typing of the friendly name?…
I need to know to understand if I did the same «mistake».
thanks
-
User1903832623 posted
@greg88: Dude, u are super genious!
Just a note:
Take the initial certificate request file (sent to CA) and rename it with a .cer extension.
i couldn’t import the Certificate Request File renamed as .cer, because the certificate snap-in was
nagging about invalid operation. So i just tried to import in the Certificate Enrollment Requests the certificate itself… and BANG! it worked like a charm!You made my day
Пройдите диагностику и выполните рекомендуемые действия, а затем попробуйте подписать документ или отчёт ещё раз.
Если ошибка повторяется, переустановите КриптоПро CSP с утилитой очистки следов CSPClean.
-
Откройте «Панель управления» → «Программы и компоненты» и удалите КриптоПро CSP.

-
Скачайте утилиту CSPClean и запустите её. Появится окно с предупреждением, что все продукты компании Крипто-Про будут уничтожены. Нажмите «Да».

Если вы самостоятельно сохранили сspclean сайта Крипто-Про, то при запуске может появиться запрос на удаление контейнеров из реестра — отклоните его.
- Перезагрузите компьютер. Затем установите КриптоПро CSP с помощью веб-диска и перезагрузите компьютер ещё раз.
Если ошибка сохранится, обратитесь в поддержку прямо из окна с ошибкой. Если уже закрыли его, вернитесь в Эльбу и нажмите на знак вопроса внизу справа.
We’ve seen a few instances of the following error message on 64 bit servers when IIS 7.0 is attempting to process a pending certificate request:
Complete Certificate Request
There was an error while performing this operation.
Details:
CertEnroll::CX509Enrollment::p_InstallResponse: ASN1 bad tag value met. 0x8009310b (ASN: 267)
This error seems to mean that the private key (created when the certificate request was made) does not match the public key (the .crt file). The keypair is not successfully joined into a working SSL certificate.
So far this behavior seems most common with .crt files (instead of the .cer files many of us are more used to) issued by one specific Certification Authority—which will remain nameless here.
The error shows up after reaching the point in the process where you ‘specify certificate authority response’ and guide the wizard to the ‘File name containing the certification authority’s response…’ (the .crt file).
So far there seem to be two solutions.
Solution 1:
Verisign has a support article that matches this error message: https://knowledge.verisign.com/support/ssl-certificates-support/index?page=content&id=S:SO8467&actp=…. Their recommendation seems to be to replace the certificate with a new one. This method has worked for at least one of my customers in this place with a GoDaddy certificate. All they had to do was make a new certificate request (CSR text file), log into the the Godaddy web interface and re-key (we chose re-key rather than re-issue) their certificate. The new file processed fine.
Solution 2:
Begin by importing the .crt file into the Personal certificate store for the local computer. (Start button > Run: MMC > File Menu > Add/Remove Snap-in > highlight Certificates snap-in and click the ADD button > select Computer Account and click Finish > Click OK > drill into Personal > Certificates > right-click and select All Tasks > select Import > guide to the .crt file.) At this point your certificate is basically a half-certificate. It is still missing its private key.
Second, double-click the crt certificate file you just imported, select the Details tab, scroll all the way down to Thumbprint and highlight Thumbprint. In the lower pane, block and copy all the letters of the thumbprint. Paste the thumbprint characters into notepad. Open the command prompt and run this command: Certutil /?
The command you’ll want to run is:
certutil -repairstore my «{insert all of the thumbprint characters here}»
When you see the response: “CertUtil: -repairstore command completed successfully” you should have a private key associated with the .crt file in the personal store. There should no longer be any need to run through the “Complete Certificate Request…” wizard. The certificate should show up in the IIS Manager’s list of server certificates at this point. It should also be available in the SSL Certificates drop-down list when attempting to edit the https binding for a website.
Incidentally, a common way of attempting to deal with this error is to take the .p7b file from the Certification Authority and import the CA’s certificates into the Trusted and Intermediate stores. As far as I can tell, this approach has no useful effect upon this problem.
Other relevant links:
https://knowledge.verisign.com/support/ssl-certificates-support/index?page=content&id=S:SO8467&actp=…
http://blogs.msdn.com/vijaysk/archive/2008/11/25/certenroll-cx509enrollment-p-installresponse-asn1-b…
Author: Christopher T. Haun
- Remove From My Forums
-
Question
-
Hi All,
I have recieved CSR request from App team but i am getting below error While creating Certificate in root CA.
Certificate Request Denied

Your certificate request was denied.
Your Request Id is 0. The disposition message is
«Error Parsing Request ASN1 bad tag value met. 0x8009310b (ASN: 267)».Contact your administrator for further information.
Answers
-
Thanks Elke . Issue fixed . Application team send one more updated CSR and now i am able to create certificate .
-
Marked as answer by
Tuesday, July 29, 2014 3:01 AM
-
Marked as answer by

- Remove From My Forums
-
Question
-
User-1286092494 posted
Hello… Is anyone seen this error when attempting to install a VeriSign chain certificate using IIS 7 server?
CertEnroll:CX509Enrolment:p_InstallResponse: ASN1 bad tag value met. 0x8009310b(ASN: 267)
I have search the internet to no avail… Any help is greatly appreciated.
Answers
-
-
Marked as answer by
Anonymous
Tuesday, September 28, 2021 12:00 AM
-
Marked as answer by
All replies
-
User113421904 posted
Hi,
I did see one post before that this error is related to permissions of certificate store. Are you running from administrative accounts, make sure you have enough permissions during the installing of certificates.
-
User-1286092494 posted
Thanks Zhao. I was wondering if you guys have any kind of knowledge base article that talks about this error within IIS 7 during an SSL certificate install? It would be great if there is one.
We would like to put this information in our knowledge base to better assist our customers at VeriSign.
Thank you for your support.
Regards,
Jason R.
-
-
Marked as answer by
Anonymous
Tuesday, September 28, 2021 12:00 AM
-
Marked as answer by
-
User1810624584 posted
I leave this behind for anyone else searching for an answer to this question. NOTE: I am not using a VeriSign certificate, so this is not directly pertinent to the original question. I leave it behind because the error message is the same and
hits on the search engines.I leave the message with double colons here so that search will pick it up more readily.
CertEnroll::CX509Enrollment::p_InstallResponse: ASN1 bad tag value met. 0x08009310b (ASN: 267)
I requested a certificate from an IIS 7.0 Web Server. I used the request to create a certificate within our internal CA and generate a .cer file. When I went to install the .cer file in the web server, I got hit with this error message.
It didn’t take too much digging to find a hint that perhaps the CA was not trusted by the Web Server. I added the internal CA chain to the Web Server and this got me past the message. Just to be sure, I removed the root certificate from the Trusted
Root Certification Authorities folder and tried again — I got the error again. This is a verified cause. Certainly this may not be the only cause. I sure wish the error message were better. -
User351018772 posted
I’ve had the same issue, below is my information…
- Windows 2008 Web Server 64-bit Edition
- IIS7
- SQL 2005 Express
- Network Solutions Basic SSL certificate
Each time I try to complete the certificate request I get the following error…
CertEnroll::CX509Enrollment::p_InstallResponse: ASN1 bad tag value met. 0x8009310b (ASN: 267)
I should also mention that I have already added the 3 other certificates provided by NetworkSolutions under the Certificates snap-in. When I open up IIS I do not see my certificate request listed however IIS knows that it’s there so I’m not sure if I should
see it listed or not. Under «Certificates -> Certificate Enrollment Requests -> Certificates» I can see the pending request. Up until a few minutes ago I had several listed there and have since cleared/deleted them out and re-requested the certificate
from NetworkSolutions although I don’t have any faith this will work. There were several from past failed attempts. Should I be able to see the certificate request in IIS7 after creating the initial request before it’s completed? My server doesn’t do much
other than host a few websites and run SQL 2005 Express. I know some have said something about SQL but I can’t imagine what that has to do with my situation since I simply want to add an SSL certificate to IIS7 to run a single website with SSL encryption.Is it just me or should this not be ridiculously simple to accomplish and yet it’s been the single most frustrating thing I had to do in a great long while. NetworkSolutions doesn’t have any answers, Microsoft wants to charge me an arm and leg just to say
«Hi», and I’m losing my patience with the whole thing since it should literally take less than 5 minutes to complete a simple certificate request.Does anyone out there have a solution to this problem because I’m Googled out…
Thanks in advance for any support provided,
Matt
-
User882081861 posted
I’d recommend contacting the certification authority and asking them what their preferred way is to abandon the problematic keypair and how to best make a totally new CSR.
-
User56899015 posted
This happened to me because I screwed up.Heres what I did:
I created a certificate request and sent it to the CA. I got the new cert and installed it.
Here’s where I went wrong:
I mis-typed the friendly name during the cert install and stupidly deleted the cert via IIS manager.
How I fixed it:
Take the initial certificate request file (sent to CA) and rename it with a .cer extension.
Open the certificate management snap in.
Right click on «Certificate Enrollment Requests» and import the certificate signing request file.
Go back to IIS Manager and import the certificate that the CA sent back in response to your initial request.Basically, you must have an unfulfilled certificate request corresponding to the certificate provided by your CA before «complete certificate request» is successful.
-
User1063753466 posted
greg88 — I just created this forum account to tell you that you are a genius. Your solution totally worked for me. -
User1180450644 posted
Gregg88 — Saved my butt too — thanks! -
User418653656 posted
I got the same error, through a mistake on my part, but the solution did not work for me.
I was using a GoDaddy cert, which had an intermediate certificate. I followed the instructions to import the GoDaddy intermediate cert into the «Certificates (Local Computer)/Intermediate Certification Authority/Certificates store.
Turns out, I apparently double clicked on the actual web site cert, which happily went in the store.
I think went to IIS which gave me the OP’s error.
Drove me nuts, until I found the web cert in the Intermediate Certification Authority. lol.
So, the fix for me was to export and delete the web site cert, import the proper intermediate cert, and then import the cert like normal into the «Certificates (Local Computer)/Personal/Certificates store.
Now, oddly, IIS still thinks there is a cert request outstanding. I’m assuming I can just ignore this, as I already have the cert loaded.
== John ==
-
User-1938893238 posted
«I mis-typed the friendly name during the cert install»
What does that mean? What defines a mis-typing of the friendly name?…
I need to know to understand if I did the same «mistake».
thanks
-
User1903832623 posted
@greg88: Dude, u are super genious!
Just a note:
Take the initial certificate request file (sent to CA) and rename it with a .cer extension.
i couldn’t import the Certificate Request File renamed as .cer, because the certificate snap-in was
nagging about invalid operation. So i just tried to import in the Certificate Enrollment Requests the certificate itself… and BANG! it worked like a charm!You made my day



