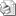|
Страница была создана 28.04.2022
Команда показывает статистику трафика и ошибок на определённом интерфейсе:
Switch#show interfaces имя_интерфейса
Пример вывода команды show interfaces, обратите внимание, на выделенный текст желтым цветом.
Switch#show interfaces gi0/1
GigabitEthernet0/1 is up, line protocol is up (connected)
Hardware is Gigabit Ethernet, address is 001e.1478.b7b1 (bia 001e.1478.b7b1)
Description: SW-2
MTU 1500 bytes, BW 100000 Kbit/sec, DLY 100 usec,
reliability 255/255, txload 1/255, rxload 1/255
Encapsulation ARPA, loopback not set
Keepalive set (10 sec)
Full-duplex, 100Mb/s, media type is 10/100/1000BaseTX
input flow-control is off, output flow-control is unsupported
ARP type: ARPA, ARP Timeout 04:00:00
Last input 00:00:00, output 00:00:00, output hang never
Last clearing of «show interface» counters never
Input queue: 0/75/0/0 (size/max/drops/flushes); Total output drops: 42164
Queueing strategy: fifo
Output queue: 0/40 (size/max)
5 minute input rate 781000 bits/sec, 122 packets/sec
5 minute output rate 183000 bits/sec, 65 packets/sec
75482 packets input, 104620499 bytes, 0 no buffer
Received 6352 broadcasts (3951 multicasts)
0 runts, 0 giants, 0 throttles
105684 input errors, 103301 CRC, 0 frame, 0 overrun, 0 ignored
0 watchdog, 3951 multicast, 0 pause input
0 input packets with dribble condition detected
39937001 packets output, 2917338077 bytes, 0 underruns
0 output errors, 0 collisions, 4 interface resets
10 unknown protocol drops
0 babbles, 0 late collision, 0 deferred
0 lost carrier, 0 no carrier, 0 pause output
0 output buffer failures, 0 output buffers swapped out
После того, как вы устранили вероятную ошибку, нужно сбросить счётчики, чтобы убедиться, что ошибок больше нет.
Switch#clear counters gi0/1
После сброса, повторно проверяем счетчики, как видим счетчики обнулились, в примере я выделил их жёлтым цветом.
Switch#show interfaces gi0/1
GigabitEthernet0/1 is up, line protocol is up (connected)
Hardware is Gigabit Ethernet, address is 001e.1478.b7b1 (bia 001e.1478.b7b1)
Description: SW-2
MTU 1500 bytes, BW 1000000 Kbit/sec, DLY 10 usec,
reliability 255/255, txload 1/255, rxload 1/255
Encapsulation ARPA, loopback not set
Keepalive set (10 sec)
Full-duplex, 1000Mb/s, media type is 10/100/1000BaseTX
input flow-control is off, output flow-control is unsupported
ARP type: ARPA, ARP Timeout 04:00:00
Last input 00:00:00, output 00:00:00, output hang never
Last clearing of «show interface» counters 00:00:08
Input queue: 0/75/0/0 (size/max/drops/flushes); Total output drops: 0
Queueing strategy: fifo
Output queue: 0/40 (size/max)
5 minute input rate 1352000 bits/sec, 306 packets/sec
5 minute output rate 313000 bits/sec, 91 packets/sec
1274 packets input, 455165 bytes, 0 no buffer
Received 199 broadcasts (118 multicasts)
0 runts, 0 giants, 0 throttles
0 input errors, 0 CRC, 0 frame, 0 overrun, 0 ignored
0 watchdog, 118 multicast, 0 pause input
0 input packets with dribble condition detected
663 packets output, 312346 bytes, 0 underruns
0 output errors, 0 collisions, 0 interface resets
0 unknown protocol drops
0 babbles, 0 late collision, 0 deferred
0 lost carrier, 0 no carrier, 0 pause outputv
0 output buffer failures, 0 output buffers swapped out
В таблице показаны некоторые значение и описания к ним.
Table Of Contents
Cisco NX-OS Interfaces Commands
attach fex
auto-recovery
bandwidth (interface)
beacon
bfd
bfd authentication
bfd echo
bfd echo-interface
bfd interval
bfd ipv4
bfd optimize subinterfaces
bfd per-link
bfd slow-timer
carrier-delay
channel-group
clear counters interface
clear l2protocol tunnel counters
clear lacp counters
clear vpc statistics
default interface
delay
delay restore
delay restore interface-vlan
description
description (fex)
dual-active exclude interface-vlan
duplex
encapsulation dot1Q
errdisable detect cause
errdisable recovery cause
errdisable recovery interval
feature bfd
feature interface-vlan
feature lacp
feature-set fex
feature tunnel
feature udld
feature vpc
fex
fex associate
flowcontrol
graceful consistency-check
hsrp bfd
inherit port-profile
install feature-set fex
interface cmp-mgmt module
interface ethernet
interface loopback
interface mgmt
interface port-channel
interface tunnel
interface vlan
ip eigrp bfd
ip ospf bfd
ip pim bfd
ip pim bfd-instance
ip route static bfd
ipv6 eigrp bfd
isis bfd
fabricpath switch-id
l2protocol tunnel
l2protocol tunnel cos
l2protocol tunnel drop-threshold
l2protocol tunnel shutdown-threshold
lacp max-bundle
lacp min-links
lacp port-priority
lacp rate
lacp system-priority
link debounce
load-interval
max-ports
mdix auto
medium
mtu
peer-gateway
peer-keepalive destination
peer-switch
port-channel load-balance
port-profile
rate-mode dedicated
rate-mode shared
reload fex
reload restore
role priority
serial
show bfd neighbors
show environment fex
show fex
show fex detail
show fex transceiver
show fex version
show interface
show interface brief
show interface capabilities
show interface counters
show interface counters errors
show interface counters storm-control
show interface counters trunk
show interface debounce
show interface description
show interface ethernet
show interface flowcontrol
show interface mgmt
show interface port-channel
show interface port-channel counters
show interface transceiver fex-fabric
show interface status
show interface switchport
show interface transceiver
show interface trunk
show interface tunnel
show inventory fex
show ip dhcp snooping statistics
show lacp counters
show lacp interface
show lacp neighbor
show lacp port-channel
show lacp system-identifier
show logging level fex
show module fex
show port-channel capacity
show port-channel compatibility-parameters
show port-channel database
show port-channel load-balance
show port-channel rbh-distribution
show port-channel summary
show port-channel traffic
show port-channel usage
show port-profile
show running-config fex
show running-config interface
show running-config interface mgmt
show running-config vpc
show sprom fex
show startup-config interface
show startup-config vpc
show system reset-reason fex
show tech fex all
show tech-support fex
show udld
show vdc
show version fex
show vpc brief
show vpc consistency-parameters
show vpc orphan-ports
show vpc peer-keepalive
show vpc role
show vpc statistics
shutdown
speed
state enabled
switchport
switchport access vlan
switchport autostate exclude
switchport dot1q ethertype
switchport host
switchport mode
switchport mode dot1q-tunnel
switchport mode fex-fabric
switchport trunk allowed vlan
switchport trunk native vlan
system default switchport
system jumbomtu
system-mac
system-priority
track
tunnel destination
tunnel mode
tunnel path-mtu-discovery
tunnel source
tunnel use-vrf
tunnel ttl
type
udld
udld aggressive
udld message-time
udld reset
vlan dot1q tag native
vpc
vpc domain
vpc orphan-ports suspend
vpc peer-link
Cisco NX-OS Interfaces Commands
This chapter describes the Cisco NX-OS interfaces commands.
attach fex
To access the command-line interface (CLI) of a connected Fabric Extender to run diagnostic commands, use the attach fex command.
attach fex chassis-id
Syntax Description
|
chassis-id |
Fabric Extender chassis ID. The range is from 100 to 199. |
Defaults
None
Command Modes
EXEC mode
Command History
|
Release |
Modification |
|---|---|
|
5.1(1) |
This command was introduced. |
Usage Guidelines
Use the attach fex command to access the CLI on a connected Fabric Extender and perform diagnostic commands. We recommend that you use this command only by following the directions from Cisco technical support personnel.
This command does not require a license.
Examples
This example shows how to access the command-line interface (CLI) of a connected Fabric Extender to run diagnostic commands:
switch(config)# attach fex 101
To exit type 'exit', to abort type '$.'
Bad terminal type: "ansi". Will assume vt100.
Related Commands
|
Command |
Description |
|---|---|
|
show fex |
Displays all configured Fabric Extender chassis connected to the switch. |
auto-recovery
To configure the virtual port channel (vPC) for auto recovery if its peer is presumed nonoperational, use the auto-recovery command. To reset the vPC to the standard behavior, use the no form of this command.
auto-recovery reload-delay time-out-value
no auto-recovery reload-delay time-out-value
Syntax Description
|
reload-delay |
Specifies the duration to wait after reload to recovery vPCs. |
|
time-out-value |
Timeout value for restoring vPC links in seconds. The range is from 240 to 3600. |
Defaults
None
Command Modes
VPC domain configuration mode (config-vpc-domain)
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
5.2(1) |
This command was introduced. |
Usage Guidelines
This command does not require a license.
Examples
This example shows how to display the vPC status in brief:
switch# configure terminal
switch(config)# vpc domain 1
switch(config-vpc-domain)# auto-recovery reload-delay 350
Enables restoring of vPCs in a peer-detached state after reload, will wait for
350 seconds to determine if peer is un-reachable
switch(config-vpc-domain)#
This example shows how to revert the vPC to the standard behavior:
switch# configure terminal
switch(config)# vpc domain 1
switch(config-vpc-domain)# no auto-recovery reload-delay 350
switch(config-vpc-domain)#
Related Commands
|
Command |
Description |
|---|---|
|
vpc |
Moves other port channels into the vPC. |
|
vpc domain |
Creates a vPC domain. |
bandwidth (interface)
To set the inherited and received bandwidth values for an interface, use the bandwidth command in interface configuration mode. To restore the default values, use the no form of this command.
bandwidth {kbps | inherit [kbps]}
no bandwidth {kbps | inherit [kbps]}
Syntax Description
|
kbps |
Intended bandwidth, in kilobits per second. The range if from 1 to 10000000. |
|
inherit |
(Optional) Specifies the inherited bandwidth such as how a subinterface inherits the bandwidth of its main interface. |
Defaults
1000000 kbps
Command Modes
Interface configuration
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
4.0 |
This command was introduced. |
Usage Guidelines
The bandwidth command sets an informational parameter to communicate only the current bandwidth to the higher-level protocols; you cannot adjust the actual bandwidth of an interface using this command.

Note ![]() This is a routing parameter only. It does not affect the physical interface.
This is a routing parameter only. It does not affect the physical interface.
The bandwidth inherit command controls how a subinterface inherits the bandwidth of its main interface.
The no bandwidth inherit command enables all subinterfaces to inherit the default bandwidth of the main interface, regardless of the configured bandwidth. If a bandwidth is not configured on a subinterface, and you use the bandwidth inherit command, all subinterfaces inherit the current bandwidth of the main interface. If you configure a new bandwidth on the main interface, all subinterfaces use this new value.
If you do not configure a bandwidth on the subinterface and you configure the bandwidth inherit command on the main interface, the subinterfaces inherit the specified bandwidth.
In all cases, if an interface has an explicit bandwidth setting configured, that interface uses that setting, regardless of whether the bandwidth inheritance setting is in effect.
This command does not require a license.
Examples
This example shows how to configure all subinterfaces off this main interface to inherit the configured bandwidth:
switch(config-if)# bandwidth inherit 30000
Related Commands
|
Command |
Description |
|---|---|
|
show interface |
Displays the interface configuration information. |
beacon
To enable the beacon mode for an interface, use the beacon command. To disable the beacon mode for an interface, use the no form of this command.
beacon
no beacon
Syntax Description
This command has no arguments or keywords.
Defaults
Disabled
Command Modes
Interface configuration
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
4.0 |
This command was introduced. |
Usage Guidelines
The beacon mode allows you to identify a physical port by flashing its link-state LED with a green light. To identify the physical port for an interface, you activate the beacon parameter for the interface.
This command does not require a license.
Examples
This example shows how to enable the beacon mode for the Ethernet port 3/1:
switch(config)# interface ethernet 3/1
switch(config-if)# beacon
Related Commands
|
Command |
Description |
|---|---|
|
show interface |
Displays the interface status, which includes the beacon mode state. |
bfd
To enable Bidirectional Forwarding Detection (BFD) for a protocol, use the bfd command. To disable BFD for a protocol, use the no form of this command.
bfd
no bfd
Syntax Description
This command has no arguments or keywords.
Defaults
BFD is not enabled on the protocol.
Command Modes
Router configuration
Neighbor configuration
Command History
|
Release |
Modification |
|---|---|
|
5.0(2) |
This command was introduced. |
Usage Guidelines
There are two methods to configure protocols to use BFD for failure detection. To enable BFD for all neighbors or interfaces of a protocol, enter the bfd command in router configuration mode for the Enhanced Interior Gateway Routing Protocol (EIGRP), Open Shortest Path First (OSPFv2), and Intermediate-System-to-Intermediate-System (IS-IS) or in neighbor configuration mode for the Border Gateway Protocol (BGP). If you do not want to enable BFD on all interfaces, see the interface-level BFD enable commands in the Related Commands section.
Examples
This example shows how to enable BFD for all EIGRP neighbors:
switch# configure terminal
switch(config)# router eigrp Test1
switch(config-router)# bfd
This example shows how to enable BFD for all BGP neighbors:
switch# configure terminal
switch(config)# router bgp 1.1
switch(config-router)# neighbor 192.0.2.1 remote-as 1.0
switch(config-router-neighbor)# bfd
Related Commands
|
Command |
Description |
|---|---|
|
hsrp bfd |
Enables BFD on an HSRP interface. |
|
ip eigrp bfd |
Enables BFD on an EIGRP interface. |
|
ip ospf bfd |
Enables BFD on an OSPFv2 interface. |
|
isis bfd |
Enables BFD on an IS-IS interface. |
bfd authentication
To configure SHA-1 authentication for all bidirectional forwarding detection (BFD) sessions on the interface, use the bfd authentication command. To remove the SHA-1 authentication configuration, use the no form of this command.
bfd authentication keyed-SHA1 key-id id hex-key key ascii-key
no bfd authentication keyed-SHA1 key-id id key ascii-key
Syntax Description
|
key-id |
Specifies the key ID to use in BFD frames. |
|
id |
Key ID value. The range is from 1 to 255. |
|
hex-key |
HEX binary SHA1 secret. A hex-key can be any case-sensitive, alphanumeric string up to 40 characters. |
|
key |
Specifies ASCII SHA1 secret. |
|
ascii-key |
SHA1 secret value. An ascii key can be any case-sensitive, alphanumeric string up to 20 characters. |
Defaults
None
Command Modes
Interface configuration (config-if)
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
5.2(1) |
This command was introduced. |
Usage Guidelines
This command does not require a license.
Examples
This example shows how to configure SHA-1 authentication for all BFD sessions on the interface:
switch# configure terminal
switch(config)# interface ethernet 3/1
switch(config-if)# bfd authentication keyed-SHA1 key-id 23 key cisco123
This example shows how to disable SHA-1 authentication on the interface:
switch(config-if)# no bfd authentication keyed-SHA1 key-id 23 key cisco123
Related Commands
|
Command |
Description |
|---|---|
|
show running-config interface |
Displays the running configuration for a specific interface. |
|
show running-config bfd |
Displays the BFD running configuration. |
bfd echo
To enable Bidirectional Forwarding Detection (BFD) echo mode, use the bfd echo command. To disable BFD echo mode, use the no form of this command.
bfd echo
no bfd echo
Syntax Description
This command has no arguments or keywords.
Defaults
BFD echo mode is enabled by default.
Command Modes
Interface configuration
Command History
|
Release |
Modification |
|---|---|
|
5.0(2) |
This command was introduced. |
Usage Guidelines
When echo mode is enabled, the required minimum receive interval value is taken from the BFD slow-timer setting.

Note ![]() Before using BFD echo mode, you must disable the IP packet verification check for identical IP source and destination addresses by entering the no hardware ip verify address identical command in the default virtual device context (VDC).
Before using BFD echo mode, you must disable the IP packet verification check for identical IP source and destination addresses by entering the no hardware ip verify address identical command in the default virtual device context (VDC).

Note ![]() Before using BFD echo mode, you must disable the sending of Internet Control Message Protocol (ICMP) redirect messages by entering the no ip redirects command.
Before using BFD echo mode, you must disable the sending of Internet Control Message Protocol (ICMP) redirect messages by entering the no ip redirects command.
Use the no bfd echo command to stop sending echo packets and signify that the device is unwilling to forward echo packets that are received from BFD neighbors. The RequiredMinEchoRx BFD session parameter is set to zero when echo mode is disabled.
This command does not require a license.
Examples
This example shows how to configure echo mode between BFD neighbors:
switch(config)# interface Ethernet 1/1
switch(config-if)# bfd echo
This example shows that the BFD session neighbor is up and using BFD echo mode. The relevant command output is shown in bold in the output:
switch# show bfd neighbors details
OurAddr NeighAddr LD/RD RH/RS Holdown(mult)State Int
172.16.1.2 172.16.1.1 1/6 Up 0 (3 ) Up Fa0/1
Session state is UP and using echo function with 50 ms interval.
Local Diag: 0, Demand mode: 0, Poll bit: 0
MinTxInt: 1000000, MinRxInt: 1000000, Multiplier: 3
Received MinRxInt: 1000000, Received Multiplier: 3
Holdown (hits): 3000(0), Hello (hits): 1000(337)
Rx Count: 341, Rx Interval (ms) min/max/avg: 1/1008/882 last: 364 ms ago
Tx Count: 339, Tx Interval (ms) min/max/avg: 1/1016/886 last: 632 ms ago
Registered protocols: EIGRP
Last packet: Version: 1 - Diagnostic: 0
State bit: Up - Demand bit: 0
Poll bit: 0 - Final bit: 0
Multiplier: 3 - Length: 24
My Discr.: 6 - Your Discr.: 1
Min tx interval: 1000000 - Min rx interval: 1000000
Related Commands
|
Command |
Description |
|---|---|
|
feature bfd |
Enables the BFD feature. |
|
bfd interval |
Configures the BFD session parameters. |
|
bfd slow-timer |
Configures the BFD RequiredminEchoRx interval. |
|
hardware ip verify address identical |
Enables verifying that IP packets do not have the same address for IP source and IP destination fields. |
|
ip redirects |
Enables the sending of ICMP redirect messages if the Cisco IOS software is forced to resend a packet through the same interface on which it was received. |
bfd echo-interface
To configure the IP address on the loopback interface, use the bfd echo-interface command. To revert the source address of the echo frames to that of the interface, use the no form of this command.
bfd echo-interface loopback interface number
no bfd echo-interface loopback interface number
Syntax Description
|
loopback |
Specifies the loopback interface. |
|
interface number |
Virtual interface number. The range is from 0 to 1023. |
Defaults
The source ip address for echo packets is set to the same as configured on the interface. This command
changes the source address for the echo packets to the one configured on the specified loopback
interface.
Command Modes
Global Configuration mode
Command History
|
Release |
Modification |
|---|---|
|
5.0(2) |
This command was introduced. |
Usage Guidelines
This command does not use the loopback interface directly but uses the ip address configured on the loopback interface.
This command does not require a license.
Examples
This example shows how to configure interface used for BFD echo frames:
switch(config)# bfd echo-interface loopback 1
This example shows how to disable interface used for BFD echo frames:
switch(config)# no bfd echo-interface loopback 1
Related Commands
|
Command |
Description |
|---|---|
|
feature bfd |
Enables the BFD feature. |
|
bfd interval |
Configures the BFD session parameters. |
|
bfd slow-timer |
Configures the BFD RequiredminEchoRx interval. |
|
hardware ip verify address identical |
Enables verifying that IP packets do not have the same address for IP source and IP destination fields. |
|
ip redirects |
Enables the sending of ICMP redirect messages if the Cisco IOS software is forced to resend a packet through the same interface on which it was received. |
bfd interval
To configure the Bidirectional Forwarding Detection (BFD) session parameters, use the bfd interval command. To return to the default setting, use the no form of this command.
bfd interval mintx min_rx msec multiplier value
no bfd interval mintx min_rx msec multiplier value
Syntax Description
|
mintx |
Rate at which BFD control packets are sent to BFD neighbors. The configurable range is from 50 to 999. |
|
min_rx msec |
Specifies the rate at which BFD control packets are expected to be received from BFD neighbors. The range is from 50 to 999. |
|
multiplier value |
Specifies the number of consecutive BFD control packets that must be missed from a BFD neighbor before BFD declares that the neighbor is unavailable and the BFD neighbor is informed of the failure. The range is from 1 to 50. |
Defaults
BFD interval: 50 milliseconds
min_rx: 50 milliseconds
multiplier: 3
Command Modes
Global configuration
Interface configuration
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
5.0(2) |
This command was introduced. |
Usage Guidelines
BFD session parameters configured at the interface level take precedence over the globally configured BFD session parameters.
This command does not require a license.
Examples
This example shows how to set the BFD session parameters for Ethernet interface 3/1:
switch# configure terminal
switch(config)# interface ethernet 3/1
switch(config-if)# bfd interval 50 min_rx 20 multiplier 3
Related Commands
|
Command |
Description |
|---|---|
|
feature bfd |
Enables the BFD feature. |
|
show bfd neighbors |
Displays information about BFD neighbors. |
bfd ipv4
To disable the Bidirectional Forwarding Detection (BFD) IPV4 sessions on the interface, use the bfd ipv4 command. To revert to the default settings, use the no form of this command.
bfd ipv4
no bfd ipv4
Syntax Description
This command has no arguments or keywords.
Defaults
Enabled
Command Modes
Interface configuration
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
5.0(2) |
This command was introduced. |
Usage Guidelines
This command does not require a license.
Examples
This example shows how to disable the IPV4 sessions:
switch# configure terminal
switch(config)# interface ethernet 1/1
switch(config-if)# bfd ipv4
Related Commands
|
Command |
Description |
|---|---|
|
feature bfd |
Enables the BFD feature. |
|
show bfd neighbors |
Displays information about BFD neighbors. |
bfd optimize subinterfaces
To optimize subinterfaces on a physical interface for Bidirectional Forwarding Detection (BFD), use the bfd optimize subinterfaces command. To return to the default setting, use the no form of this command.
bfd optimize subinterfaces
no bfd optimize subinterfaces
Syntax Description
This command has no arguments or keywords.
Defaults
Disabled
Command Modes
Interface configuration
Command History
|
Release |
Modification |
|---|---|
|
5.0(2) |
This command was introduced. |
Usage Guidelines
You can optimize subinterfaces, because BFD creates sessions for all configured subinterfaces. BFD sets the subinterface with the lowest configured VLAN ID as the master subinterface and that subinterface uses the BFD session parameters of the parent interface. The remaining subinterfaces use the slow timer. If the master subinterface session detects an error, BFD marks all subinterfaces on that physical interface as down.
This command does not require a license.
Examples
This example shows how to enable subinterface optimization:
switch(config)# interface Ethernet 1/1
switch(config-if)# bfd optimize subinterfaces
Related Commands
|
Command |
Description |
|---|---|
|
feature bfd |
Enables the BFD feature. |
bfd per-link
To enable Bidirectional Forwarding Detection (BFD) for all links in a port channel, use the bfd per-link command. To disable BFD for a port channel, use the no form of this command.
bfd per-link
no bfd per-link
Syntax Description
This command has no arguments or keywords.
Defaults
BFD is not enabled on the port channel.
Command Modes
Port channel configuration
Command History
|
Release |
Modification |
|---|---|
|
5.0(2) |
This command was introduced. |
Usage Guidelines
Us the bfd per-link command to enable BFD on each link in a port channel. BFD creates a session for each link in the port channel and provides an aggregate result to client protocols. For example, if the BFD session for one link on a port channel is up, BFD informs client protocols such as open shortest path (OSPF) that the port channel is up. The BFD session parameters are negotiated between the BFD peers in a three-way handshake.
This command does not require a license.
Examples
This example shows how to enable BFD for port channel 3:
switch# configure terminal
switch(config)# interface port-channel 3
switch(config-if)# bfd per-link
This example shows how to configure the BFD session parameters for a port channel:
switch# configure terminal
switch(config)# interface port-channel 3
switch(config-if)# bfd interval 50 min_rx 50 multiplier 3
Related Commands
|
Command |
Description |
|---|---|
|
bfd echo |
Enables BFD echo mode. |
|
feature bfd |
Enables the BFD feature. |
|
bfd interval |
Configures the BFD session parameters |
bfd slow-timer
To configure the Bidirectional Forwarding Detection (BFD) slow timer value, use the bfd slow-timer command. To return to the default setting, use the no form of this command.
bfd slow-timer milliseconds
no bfd slow-timer milliseconds
Syntax Description
|
milliseconds |
BFD slow timer value, in milliseconds. The range is from 1000 to 30000. |
Defaults
The default BFD slow timer value is 2000 milliseconds.
Command Modes
Global configuration
Interface configuration
Command History
|
Release |
Modification |
|---|---|
|
5.0(2) |
This command was introduced. |
Usage Guidelines
Use the bfd slow-timer command to configure how fast a BFD session comes up. This value also sets the RequiredMinRx (or min_rx) value when echo mode is enabled.
This command does not require a license.
Examples
This example shows that the BFD slow timer value is configured to 14,000 milliseconds:
switch(config)# bfd slow-timer 14000
This example shows that the BFD slow timer value of 14,000 milliseconds has been implemented. The values for the MinTxInt and MinRxInt correspond to the configured value for the BFD slow timer. The relevant command output is shown in bold.
switch# show bfd neighbors details
OurAddr NeighAddr LD/RD RH/RS Holdown(mult) State Int
172.16.10.1 172.16.10.2 1/1 Up 0 (3 ) Up Et2/0
Session state is UP and using echo function with 50 ms interval.
Local Diag: 0, Demand mode: 0, Poll bit: 0
MinTxInt: 14000, MinRxInt: 14000, Multiplier: 3
Received MinRxInt: 10000, Received Multiplier: 3
Holdown (hits): 3600(0), Hello (hits): 1200(418)
Rx Count: 422, Rx Interval (ms) min/max/avg: 1/1480/1087 last: 112 ms ago
Tx Count: 420, Tx Interval (ms) min/max/avg: 1/2088/1090 last: 872 ms ago
Registered protocols: OSPF
Last packet: Version: 1 - Diagnostic: 0
State bit: Up - Demand bit: 0
Poll bit: 0 - Final bit: 0
Multiplier: 3 - Length: 24
My Discr.: 1 - Your Discr.: 1
Min tx interval: 14000 - Min rx interval: 14000
Related Commands
|
Command |
Description |
|---|---|
|
bfd echo |
Enables BFD echo mode. |
carrier-delay
To set the carrier delay on an interface, use the carrier-delay command. To return to the default carrier delay value, use the no form of this command.
carrier-delay {sec | {msec value}}
no carrier-delay
Syntax Description
|
sec |
Seconds of delay. The range is from 0 to 60. |
|
msec |
Specifies milliseconds of delay. |
|
value |
Milliseconds of delay. The range is from 0 to 1000. |
Defaults
The default is 100 milliseconds.
Command Modes
Interface configuration mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|
4.0(3) |
This command was introduced. |
Usage Guidelines

Note ![]() You must enable the VLAN interface feature, using the feature interface-vlan command, before you can use this command.
You must enable the VLAN interface feature, using the feature interface-vlan command, before you can use this command.
If a link goes down and comes back up before the carrier delay timer expires, the down state is effectively filtered, and the rest of the software on the device is not aware that a link-down event occurred. A large carrier delay timer results in fewer link-up/link-down events being detected. When you set the carrier delay time to 0, the device detects each link-up/link-down event that occurs.

Note ![]() The carrier-delay command is supported only on the VLAN interface mode; no other interface modes support this command.
The carrier-delay command is supported only on the VLAN interface mode; no other interface modes support this command.
In most environments, a lower carrier delay time is better than a higher one. The value that you choose depends on the nature of the link outages and how long you expect these linkages to last in your network. If your data links are subject to short outages (especially if those outages last less time than it takes for your IP routing to converge), you should set a long carrier delay value to prevent these short outages from causing unnecessary churn in your routing tables. However, if you outages tend to be longer, then you may want to set a shorter carrier delay time so that the outages are detected sooner, and the IP route convergence begins and ends sooner.
This command does not require a license.
Examples
This example shows how to set the carrier delay timer to 20 minutes for VLAN 6:
switch(config)# interface vlan 6
switch(config-if)# carrier-delay 20
Related Commands
|
Command |
Description |
|---|---|
|
show interface vlan |
Displays information about VLAN interfaces. |
channel-group
To assign and configure a physical interface to a port-channel group, use the channel-group command. To remove the channel-group configuration from the interface, use the no form of this command.
channel-group number [force] [mode {active | on | passive}]
no channel-group [number]
Syntax Description
|
number |
Number of the channel group. The maximum number of port channels that can be configured is 256 across all virtual device contexts (VDCs), and the range is from 1 to 4096. |
|
force |
(Optional) Forces the interface to join the channel group, although some parameters are not compatible. For information on the compatibility parameters and which ones can be forced, see the Usage Guidelines section. |
|
mode |
Specifies the port-channel mode of the interface. |
|
active |
Specifies that when you enable the Link Aggregation Control Protocol (LACP), this command enables LACP on the specified interface. The interface is in an active negotiating state, in which the port initiates negotiations with other ports by sending LACP packets. |
|
on |
Specifies the default channel mode and all port channels that are not running LACP remain in this mode. If you attempt to change the channel mode to active or passive before enabling LACP, the device returns an error message. The default mode is on. |
|
passive |
Specifies that when you enable LACP, this command enables LACP only if an LACP device is detected.The interface is in a passive negotiation state, in which the port responds to LACP packets that it receives but does not initiate LACP negotiation. |
Defaults
None
Command Modes
Interface configuration mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
4.0 |
This command was introduced. |
Usage Guidelines
Use this command to create a channel group that includes the interface that you are working on and to add or remove specific interfaces from the channel group. Use this command to move a port from one channel group to another. You enter the channel group that you want the port to move to; the device automatically removes the specified port from its present channel group and adds that port to the specified channel group.
After you enable LACP globally by using the feature lacp command, you enable LACP on each channel by configuring the channel mode as either active or passive. A port channel in the on channel mode is a pure port channel and can aggregate a maximum of eight ports. It does not run LACP.
You cannot change the mode for an existing port channel or any of its interfaces if that port channel is not running LACP; the channel mode remains as on. The system returns an error message if you try.
All ports in one port channel must be in the same virtual device context (VDC). With LACP enabled, this requirement applies to the possible eight active ports and the possible eight standby ports. The port channels can originate in one VDC (with all ports in that channel in the same VDC) and partner with a port channel in another VDC (again, all ports in that channel must be in that VDC).
Use the no form of this command to remove the physical interface from the port channel. When you delete the last physical interface from a port channel, the port channel remains. To delete the port channel completely, use the no form of this interface port-channel command.
The compatibility check includes the following operational attributes:
•![]() Network layer
Network layer
•![]() (Link) speed capability
(Link) speed capability
•![]() Speed configuration
Speed configuration
•![]() Duplex capability
Duplex capability
•![]() Duplex configuration
Duplex configuration
•![]() Port mode
Port mode
•![]() Access VLAN
Access VLAN
•![]() Trunk native VLAN
Trunk native VLAN
•![]() Tagged or untagged
Tagged or untagged
•![]() Allowed VLAN list
Allowed VLAN list
•![]() MTU size
MTU size
•![]() SPAN—Cannot be SPAN source or destination port
SPAN—Cannot be SPAN source or destination port
•![]() Layer 3 Ports —Cannot have subinterfaces
Layer 3 Ports —Cannot have subinterfaces
•![]() Storm control
Storm control
•![]() Flow control capability
Flow control capability
•![]() Flow control configuration
Flow control configuration
Use the show port-channel compatibility-parameters command to see the full list of compatibility checks that the Cisco NX-OS uses.
You can only add interfaces configured with the channel mode set to on to static port channels, that is without a configured aggregation protocol and you can only add interfaces configured with the channel mode as active or passive to port channels that are running LACP.
You can configure these attributes on an individual member port. If you configure a member port with an incompatible attribute, Cisco NX-OS suspends that port in the port channel.
Alternatively, you can force ports with incompatible parameters to join the port channel as long the following parameters are the same:
•![]() (Link) speed capability
(Link) speed capability
•![]() Speed configuration
Speed configuration
•![]() Duplex capability
Duplex capability
•![]() Duplex configuration
Duplex configuration
•![]() Flow control capability
Flow control capability
•![]() Flow control configuration
Flow control configuration
When the interface joins a port channel, some of its individual parameters are removed and replaced with the values on the port channel as follows:
•![]() Bandwidth
Bandwidth
•![]() Delay
Delay
•![]() Extended Authentication Protocol over UDP
Extended Authentication Protocol over UDP
•![]() VRF
VRF
•![]() IP address (v4 and v6)
IP address (v4 and v6)
•![]() MAC address
MAC address
•![]() Spanning Tree Protocol
Spanning Tree Protocol
•![]() NAC
NAC
•![]() Service policy
Service policy
•![]() Quality of Service (QoS)
Quality of Service (QoS)
•![]() ACLs
ACLs
Many of the following interface parameters remain unaffected with the interface joins or leaves a port channel:
•![]() Beacon
Beacon
•![]() Description
Description
•![]() CDP
CDP
•![]() LACP port priority
LACP port priority
•![]() Debounce
Debounce
•![]() UDLD
UDLD
•![]() MDIX
MDIX
•![]() Rate mode
Rate mode
•![]() Shutdown
Shutdown
•![]() SNMP trap
SNMP trap
If subinterfaces are configured for the port-channel interface and a member port is removed from the port channel, the configuration of the port-channel subinterface is not propagated to the member ports.
Any configuration changes that you make in any of the compatibility parameters to the port-channel interface are propagated to all interfaces within the same channel group as the port channel (for example, configuration changes are also propagated to the physical interfaces that are not part of the port channel but are part of the channel group).
You do not have to create a port-channel interface before you assign a physical interface to a channel group. A port-channel interface is created automatically when the channel group gets its first physical interface, if it is not already created.
You can create either a Layer 2 or a Layer 3 port channel by entering the interface port-channel command or when the channel group gets its first physical interface assignment. The port channels are not created at run time or dynamically.

Note ![]() The number of ports allowed in a port-channel (for ON mode) is different between M1 modules and F1 modules (D1) only VDCs. The number is 8 for M1 modules or M1-F1 VDCs and 16 for F1 modules.
The number of ports allowed in a port-channel (for ON mode) is different between M1 modules and F1 modules (D1) only VDCs. The number is 8 for M1 modules or M1-F1 VDCs and 16 for F1 modules.
This command does not require a license.
Examples
This example shows how to add an interface to LACP channel group 5 in active mode:
switch(config-if)# channel-group 5 mode active
Related Commands
|
Command |
Description |
|---|---|
|
show interface port-channel |
Displays information about the traffic on the specified port-channel interface. |
|
show port-channel summary |
Displays information on the port channels. |
|
show lacp |
Displays LACP information. |
clear counters interface
To clear the interface counters, use the clear counters interface command.
clear counters interface {all | ethernet slot/port | loopback number | mgmt number | port-channel channel-number | tunnel tunnel-number | vlan vlan-number}
Syntax Description
|
all |
Clears all interface counters |
|
ethernet slot/port |
Clears the Ethernet interface counter for the slot number and port number specified. |
|
loopback number |
Clears the loopback interface counter for the virtual interface number specified. The range is from 0 to 1023. |
|
mgmt number |
Clears the management interface counter for the number specified. The number is 0. |
|
port-channel channel-number |
Clears the port-channel interface for the number specified. The range is from 1 to 4096. |
|
tunnel tunnel-number |
Clears the port-channel interface for the number specified. The range is from 0 to 65535. |
|
vlan vlan-number |
Clears the port-channel interface for the number specified. The range is from 1 to 4096. |
Defaults
None
Command Modes
Any command mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
4.0 |
This command was introduced. |
Usage Guidelines
This command does not require a license.
Examples
This example shows how to clear and reset the counters on Ethernet port 5/5:
switch# clear counters interface ethernet 5/5
Related Commands
|
Command |
Description |
|---|---|
|
show interface counters |
Displays in and out counters for all interfaces in the system. |
clear l2protocol tunnel counters
To clear the Layer 2 protocol tunnel statistics counters, use the clear l2protocol tunnel counters command.
clear l2protocol tunnel counters [interface if-range]
Syntax Description
|
interface |
Specifies the interface statistics to clear. |
|
if-range |
(Optional) Range of interfaces. |
Defaults
None
Command Modes
Any command mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
5.0(2) |
This command was introduced. |
Usage Guidelines
If no interfaces are specified, the Layer 2 protocol tunnel statistics are cleared for all interfaces.
This command does not require a license.
Examples
This example shows how to clear the Layer 2 protocol tunnel statistics counters:
switch# clear l2protocol tunnel counters
Related Commands
|
Command |
Description |
|---|---|
|
show l2protocol tunnel |
Displays Layer 2 protocol tunnel information. |
clear lacp counters
To clear the statistics for all interfaces for Link Aggregation Control Protocol (LACP) groups, use the clear lacp counters command.
clear lacp counters [interface port-channel channel-number]
Syntax Description
|
interface port-channel |
(Optional) Specifies the interface port channel. |
|
channel-number |
(Optional) LACP port-channel number. The range is from 1 to 4096. |
Defaults
None
Command Modes
Any command mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|
4.0 |
This command was introduced. |
Usage Guidelines
If you enter this command for a static port-channel group without enabling the aggregation protocol, the device ignores the command.
If you do not specify a channel number, the LACP counters for all LACP port groups are cleared.
This command does not require a license.
Examples
This example shows how to clear all LACP counters:
switch(config)# clear lacp counters
This example shows how to clear all LACP counters for the LACP port-channel group 20:
switch(config)# clear lacp counters interface port-channel 20
Related Commands
|
Command |
Description |
|---|---|
|
show lacp counters |
Displays information about LACP statistics. |
clear vpc statistics
To clear virtual port-channel (vPC) statistics, use the clear vpc statistics command.
clear vpc statistics {all | peer-keepalive | peer-link | vpc number}
Syntax Description
|
all |
Clears all vPC statistics on the local vPC peer device. |
|
peer-keepalive |
Clears the vPC peer-keepalive statistics on the local vPC peer device. |
|
peer-link |
Clears statistics on the local vPC peer device. |
|
vpc number |
Clears vPC statistics on the specified vPC. The range is from 1 to 4096. |
Defaults
None
Command Modes
Any command mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|
4.1(3) |
This command was introduced. |
Usage Guidelines
Use the clear vpc statistics command to clear the vPC statistics. If the feature is not enabled, this command is unavailable.
The clear vpc statistics peer-link and clear vpc statistics vpc number commands are redirected to the appropriate port channel and the clear statistics port-channel channel-number command.
This command does not require a license.
Examples
This example shows how to clear the statistics for vPC 10:
switch(config)# clear vpc statistics vpc 10
Related Commands
|
Command |
Description |
|---|---|
|
show vpc statistics |
Displays vPC statistical information on vPCs. If the feature is not enabled, the system displays an error when you enter this command. |
default interface
To create a checkpoint of the running configuration for rollback purposes, use the default interface command.
default interface if [checkpoint name]
Syntax Description
|
if |
Interface type and number in module/slot format. |
|
checkpoint |
(Optional) Creates a configuration rollback checkpoint. |
|
name |
(Optional) Checkpoint name. The maximum size is 80 alphanumeric. |
Defaults
None
Command Modes
Interface configuration mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
5.1(1) |
This command was introduced. |
Usage Guidelines
Use this command to return an interface to it’s default state. All the user configuration under the specified interface(s) is deleted upon the successful completion of the command. You can optionally create a checkpoint before deleting the interface configuration, so that you can later choose roll back to the original configuration.

Caution
![]() When using this command, you delete the configuration of the specified interfaces unless you enter the checkpoint keyword. The optional checkpoint keyword allows you to create a checkpoint of the interface configuration to that you can later roll back to the original configuration.
When using this command, you delete the configuration of the specified interfaces unless you enter the checkpoint keyword. The optional checkpoint keyword allows you to create a checkpoint of the interface configuration to that you can later roll back to the original configuration.
This command does not require a license.
Examples
This example shows how to create a checkpoint of the running configuration for rollback purposes:
switch(config)# default interface ethernet 2/1 checkpoint test
Related Commands
|
Command |
Description |
|---|---|
|
show interface switchport |
Displays the administrative and operational status of a switching (nonrouting) port. |
delay
To configure the interface throughput delay for Ethernet interfaces, use the delay command. To remove the configured throughput delay, use the no form of this command.
delay value
no delay
Syntax Description
|
value |
Delay time in tens of microseconds. The range is from 1 to 16777215. |
Defaults
10 microseconds for all interfaces except loopback ports
5000 microseconds for loopback ports
Command Modes
Interface configuration mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
4.0 |
This command was introduced. |
Usage Guidelines
Beginning with Cisco NX-OS Release 4.2(1) for the Cisco Nexus 7000 Series devices, the default delay values are changed. Prior to this release, all the default delay value for all interfaces was 100 microseconds.
After upgrading from an older release, when you enter the show running command on a VLAN interface, the display shows an additional configuration of «delay 100». If you want to revert the delay value to the new default, enter the no delay command for that VLAN interface.
Specifying a value for the throughput delay provides a value for use by Layer 3 protocols; it does not change the actual throughput delay of an interface.
This command does not require a license.
Examples
This example shows how to configure the throughput-delay time to 100,000 microseconds for the slot 3 port 1 Ethernet interface:
switch(config)# interface ethernet 3/1
switch(config-if)# delay 10000
Related Commands
|
Command |
Description |
|---|---|
|
show interface |
Displays information about the interface, which includes the delay parameter. |
delay restore
To delay the virtual port channel (vPC) from coming up on the restored vPC peer device after a reload when the peer adjacency is already established, use the delay restore command. To return to the default value, use the no form of this command.
delay restore seconds
no delay restore seconds
Syntax Description
|
seconds |
Number of seconds to delay bringing up the restored vPC peer device. The range is from 1 to 3600. |
Defaults
30 seconds
Command Modes
vpc-domain command mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
4.2(1) |
This command was introduced. |
Usage Guidelines
Use the delay restore command to avoid upstream traffic from the access device to the core from being dropped when you restore the vPC peer devices. If the restored vPCs come up before the routing tables are converged, you might see packet drops.
This command does not require a license.
Examples
This example shows how to configure the delay reload:
switch# configure terminal
switch(config)# vpc domain 5
switch(config-vpc-domain)# delay restore 40
Related Commands
|
Command |
Description |
|
delay restore interface-vlan |
Allows Layer 3 routing protocols to converge and Forwarding Information Base (FIB) programming to complete for a more graceful restoration of switched virtual interfaces (SVI). |
|
feature vpc |
Enables vPC configuration on the device. |
delay restore interface-vlan
To allow Layer 3 routing protocols to converge and Forwarding Information Base (FIB) programming to complete for a more graceful restoration of switched virtual interfaces (SVI) on the restored virtual port channel (vPC) after the delay of the vPC from coming up on the restored vPC peer device, use the delay restore interface-vlan command. To return to the default value, use the no form of this command.
delay restore interface-vlan seconds
no delay restore interface-vlan seconds
Syntax Description
|
seconds |
Number of seconds to delay bringing up the SVIs on the vPC peer device. The range is from 1 to 3600. |
Defaults
10 seconds
Command Modes
vpc-domain command mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
4.2(1) |
This command was introduced. |
Usage Guidelines
Use the delay restore command to avoid upstream traffic from the access device to the core from being dropped when you restore the vPC peer devices. If the restored vPCs come up before the routing tables are converged, you might see packet drops.
This command does not require a license.
Examples
This example shows how to configure the delay reload:
switch(config)# vpc domain 1
switch(config-vpc-domain)# delay restore 60
switch(config-vpc-domain)# delay restore interface-vlan 30
switch(config-vpc-domain)#
Related Commands
|
Command |
Description |
|
delay restore |
Delays the virtual port channel (vPC) from coming up on the restored vPC peer device after a reload when the peer adjacency is already established. |
|
feature vpc |
Enables vPC configuration on the device. |
description
To provide textual interface descriptions for the Ethernet and management interfaces, use the description command. To remove the description, use the no form of this command.
description text
Syntax Description
|
text |
Description for the interface that you are configuring. The maximum range is 80 alphanumeric, case-sensitive characters. |
Defaults
None
Command Modes
Interface configuration mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
4.0 |
This command was introduced. |
Usage Guidelines
You use the description command to provide textual interface descriptions.
This command does not require a license.
Examples
This example shows how to add the description server1 to the Ethernet interface on slot 5, port 2:
switch(config)# interface ethernet 5/1
switch(config-if)# description server1
Related Commands
|
Command |
Description |
|---|---|
|
show interface |
Displays information about the interface, which includes the description parameter. |
description (fex)
To specify a description for a Fabric Extender, use the description command. To revert to the default description, use the no form of this command.
description description
no description
Syntax Description
|
description |
Description of a Fabric Extender. The default is the string FEXxxxx where xxxx is the chassis ID. For example, if the chassis ID is 123, the default description is FEX0123. The maximum length is 20 alphanumeric characters. |
Defaults
None
Command Modes
Fabric Extender configuration mode
Command History
|
Release |
Modification |
|---|---|
|
5.1(1) |
This command was introduced. |
Usage Guidelines
This command does not require a license.
Examples
This example shows how to specify a description for a Fabric Extender:
switch# configure terminal
switch(config-fex)# description Rack16_FEX101
This example shows how to revert to the default description for a Fabric Extender:
switch# configure terminal
switch(config-fex)# no description
Related Commands
|
Command |
Description |
|---|---|
|
show fex |
Displays all configured Fabric Extender chassis connected to the switch. |
dual-active exclude interface-vlan
To ensure that certain VLAN interfaces are not shut down on the virtual port-channel (vPC) secondary peer device when the vPC peer link fails for those VLANs carried on the vPC peer link but not by the vPC configuration, use the dual-active exclude interface-vlan command. To return to the default value, use the no form of this command.
dual-active exclude interface-vlan {range}
no dual-active exclude interface-vlan {range}
Syntax Description
|
range |
Range of VLAN interfaces that you want to exclude from shutting down. The range is from 1 to 4094. |
Defaults
None
Command Modes
vpc-domain configuration mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
4.2(1) |
This command was introduced. |
Usage Guidelines
Use the dual-active exclude interface-vlan command to ensure that those VLAN interfaces on the vPC secondary peer device that are carried on the vPC peer link but not by the vPC configuration do not go down if the vPC peer link fails. The VLAN interfaces must have already been configured.

Caution
![]() We do not recommend that you configure an interface-VLAN exclude for a VLAN carried on a vPC because this action might cause packet losses on dual-active devices if the interface-VLAN still captures Layer 3 traffic while the vPC primary device and the vPC peer link are down.
We do not recommend that you configure an interface-VLAN exclude for a VLAN carried on a vPC because this action might cause packet losses on dual-active devices if the interface-VLAN still captures Layer 3 traffic while the vPC primary device and the vPC peer link are down.
This command does not require a license.
Examples
This example shows how to configure the device to keep the VLAN interfaces up on the vPC peer devices if the peer link fails:
switch(config)# vpc-domain 5
switch(config-vpc-domain)# dual-active exclude interface-vlan 10
Related Commands
|
Command |
Description |
|
vpc-domain |
Configures a vPC domain and enters the vpc-domain configuration mode. |
duplex
To specify the duplex mode as full, half, or autonegotiate, use the duplex command. To return the system to default mode, use the no form of this command.
duplex {full | half | auto}
no duplex {full | half | auto}
Syntax Description
|
full |
Specifies the duplex mode as full. |
|
half |
Specifies the duplex mode as half. |
|
auto |
Specifies the duplex mode as autonegotiate. |
Defaults
None
Command Modes
Interface configuration mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
4.0 |
This command was introduced. |
Usage Guidelines
The interface speed that you specify can affect the duplex mode used for an interface, so you should set the speed before setting the duplex mode. If you set the speed for autonegotiation, the duplex mode is automatically set to be autonegotiated. If you specify 10- or 100-Mbps speed, the port is automatically configured to use half-duplex mode, but you can specify full-duplex mode instead. Gigabit Ethernet is full duplex only. You cannot change the duplex mode on Gigabit Ethernet ports or on a 10/100/1000-Mbps port that is set for Gigabit Ethernet.
See the Cisco Nexus 7000 Series NX-OS Interfaces Configuration Guide, Release 5.x, for more information on interface speed and duplex settings.
This command does not require a license.
Examples
This example shows how to specify the duplex mode for full duplex:
switch(config-if)# duplex full
Related Commands
|
Command |
Description |
|---|---|
|
show interface |
Displays information about the interface, which includes the duplex parameter. |
encapsulation dot1Q
To enable IEEE 802.1Q encapsulation of traffic on a specified subinterface in a virtual LAN (VLAN), use the encapsulation dot1q command. To disable encapsulation, use the no form of this command.
encapsulation dot1Q vlan-id
no encapsulation dot1Q vlan-id
Syntax Description
|
vlan-id |
VLAN to set when the interface is in access mode. The range is from 1 to 4094 except for the VLANs reserved for internal switch use. |
Defaults
No encapsulation
Command Modes
Subinterface configuration mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
4.0 |
This command was introduced. |
Usage Guidelines
IEEE 802.1Q encapsulation is configurable on Ethernet interfaces. IEEE 802.1Q is a standard protocol for interconnecting multiple switches and routers and for defining VLAN topologies.
Use the encapsulation dot1q command in subinterface range configuration mode to apply a VLAN ID to the subinterface.
This command does not require a license.
Examples
This example shows how to enable dot1Q encapsulation on a subinterface for VLAN 30:
switch(config-subif)# encapsulation dot1q 30
Related Commands
|
Command |
Description |
|---|---|
|
show vlan dot1Q |
Displays dot1Q encapsulation information for a VLAN. |
errdisable detect cause
To enable error-disabled (errdisable) detection for an application, use the errdisable detect cause command. To return to the default setting, use the no form of this command.
errdisable detect cause {acl-exception | all | link-flap | loopback}
no errdisable detect cause {acl-exception | all | link-flap | loopback}
Syntax Description
|
acl- |
Enables error-disabled detection for access-list installation failures. |
|
all |
Enables error-disabled detection on all causes. |
|
link-flap |
Enables error-disabled disable detection on link-state flapping. |
|
loopback |
Enables error-disabled detection on loopback. |
Defaults
Disabled
Command Modes
Global configuration mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
4.0 |
This command was introduced. |
Usage Guidelines
Use the errdisable detect cause command to enable error detection for an application.
A cause is defined as the reason why the error-disabled state occurred. When a cause is detected on an interface, the interface is placed in an error-disabled state. This error-disabled state is an operational state that is similar to the link-down state. You must enter the shutdown command and then the no shutdown command to recover an interface manually from the error-disabled state.
This command does not require a license.
Examples
This example shows how to enable error-disabled detection on all cases:
switch(config)# errdisable detect cause all
Related Commands
|
Command |
Description |
|---|---|
|
shutdown |
Brings the port down administratively. |
|
no shutdown |
Brings the port up administratively. |
|
show interface status err-disabled |
Displays the interface error-disabled state. |
errdisable recovery cause
To enable an automatic recovery from the error-disabled (errdisable) state for an application, use the errdisable recovery cause command. To return to the default setting, use the no form of this command.
errdisable recovery cause {all | bpduguard | link-flap | failed-port-state | psecure-violation | security-violation | storm-control | udld | vpc-peerlink}
no errdisable recovery cause {all | bpduguard | link-flap | psecure-violation | security-violation | storm-control | udld | vpc-peerlink}
Syntax Description
|
all |
Enables an automatic recovery from all causes. |
|
bpduguard |
Enables an automatic recovery from BPDU Guard error-disabled state. |
|
link-flap |
Enables an automatic recovery from link-state flapping. |
|
failed-port |
Enables a timer automatic recovery from the STP set port state failure. |
|
psecure- |
Enables a timer automatic recovery from the psecure violation disable state. |
|
security- |
Enables an automatic recovery from the 802.1X violation disable state. |
|
storm- |
Enables an automatic recovery from the storm control error-disabled state. |
|
udld |
Enables an automatic recovery from the UDLD error-disabled state. |
|
vpc-peerlink |
Enables an automatic recovery from an inconsistent vPC peer-link error-disabled state. |
Defaults
Disabled
Command Modes
Global configuration mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
4.0 |
This command was introduced. |
|
4.1(3) |
Added the vpc-peerlink parameter. |
Usage Guidelines
Use the errdisable recovery cause command to enable an automatic recovery on the interface from the error-disabled state for an application. This command tries to bring the interface out of the error-disabled state and retry operation once all the causes have timed out. The interface automatically tries to come up again after 300 seconds. To change this interval, use the errdisable recovery interval command.
This command does not require a license.
Examples
This example shows how to automatically recover from the error-disabled state for link flapping after you have enabled the recovery timer:
switch(config)# errdisable recovery cause link-flap
Related Commands
|
Command |
Description |
|---|---|
|
errdisable recovery interval |
Enables the recovery timer. |
|
show interface status err-disabled |
Displays interface error-disabled state. |
errdisable recovery interval
To enable the recovery timer, use the errdisable recovery interval command.
errdisable recovery interval interval
Syntax Description
|
interval |
Error detection for access-list installation failures. The range is from 30 to 65535. |
Defaults
300 seconds
Command Modes
Global configuration mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
4.0 |
This command was introduced. |
Usage Guidelines
Use the errdisable recovery interval command to configure the recovery timer.
This command does not require a license.
Examples
This example shows how to configure the recovery timer:
switch(config)# errdisable recovery interval 32
Related Commands
|
Command |
Description |
|---|---|
|
errdisable recovery cause |
Enables the error-disabled recovery for an application. |
|
show interface status err-disabled |
Displays the interface error-disabled state. |
feature bfd
To enable Bidirectional Forwarding Detection (BFD), use the feature bfd command. To return to the default setting, use the no form of this command.
feature bfd
no feature bfd
Syntax Description
This command has no arguments or keywords.
Defaults
Disabled
Command Modes
Global configuration mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
5.0(2) |
This command was introduced. |
Usage Guidelines
You must use the feature bfd command to enable the BFD functionality.

Note ![]() The device does not display any BFD commands until you enable the feature.
The device does not display any BFD commands until you enable the feature.
This command does not require a license.
Examples
This example shows how to enable BFD functionality on the device:
switch(config)# feature bfd
Related Commands
|
Command |
Description |
|---|---|
|
show feature |
Displays information about the features enabled on the device. |
feature interface-vlan
To enable the creation of VLAN interfaces (switched virtual interfaces [SVI]), use the feature interface-vlan command. To disable the VLAN interface feature, use the no form of this command.
feature interface-vlan
no feature interface-vlan
Syntax Description
This command has no arguments or keywords.
Defaults
Disabled
Command Modes
Global configuration mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
4.0 |
This command was introduced. |
Usage Guidelines
You must use the feature interface-vlan command before you can create VLAN interfaces.
This command does not require a license.
Examples
This example shows how to enable the interface VLAN feature:
switch(config)# feature interface-vlan
Related Commands
|
Command |
Description |
|---|---|
|
interface vlan |
Creates a VLAN interface. |
feature lacp
To enable Link Aggregation Control Protocol (LACP) port channeling on the device, use the feature lacp command. To disable LACP on the device, use the no form of this command.
feature lacp
no feature lacp
Syntax Description
This command has no arguments or keywords.
Defaults
Disabled
Command Modes
Global configuration mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
4.0 |
This command was introduced. |
Usage Guidelines
You must remove all the LACP configuration parameters from all port channels on the device before you can disable LACP. You cannot disable LACP while LACP configurations remain on the device.
Even after you enable LACP globally, you do not have to run LACP on all port channels on the device. You enable LACP on each channel mode using the channel-group mode command.
When you enter the no form of this command, the system removes all the LACP configuration from the device.
This command does not require a license.
Examples
This example shows how to enable LACP port channeling on the device:
switch(config)# feature lacp
Related Commands
|
Command |
Description |
|---|---|
|
show lacp port-channel |
Displays information on port channels with LACP enabled. |
feature-set fex
To enable the Fabric Extender (FEX) feature set, use the feature-set fex command.
feature-set fex
Syntax Description
This command has no arguments or keywords.
Defaults
None
Command Modes
Global configuration mode
Command History
|
Release |
Modification |
|---|---|
|
5.1(1) |
This command was introduced. |
Usage Guidelines
This command does not require a license.
Examples
This example shows how to enable a FEX feature set:
switch(config)# feature-set fex
Related Commands
|
Command |
Description |
|---|---|
|
show fex |
Displays all configured Fabric Extender chassis connected to the switch. |
feature tunnel
To enable the creation of tunnel interfaces, use the feature tunnel command. To disable the tunnel interface feature, use the no form of this command.
feature tunnel
no feature tunnel
Syntax Description
This command has no arguments or keywords.
Defaults
Disabled
Command Modes
Global configuration mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
4.0 |
This command was introduced. |
Usage Guidelines
You must use the feature tunnel command before you can create tunnel interfaces.
This command requires the Enterprise license.
Examples
This example shows how to enable the interface tunnel feature:
switch(config)# feature tunnel
Related Commands
|
Command |
Description |
|---|---|
|
interface tunnel |
Creates a tunnel interface. |
feature udld
To enable Unidirectional Link Detection (UDLD) globally on the device, use the feature udld command. To disable UDLD globally on the device, use the no form of this command.
feature udld
no feature udld
Syntax Description
This command has no arguments or keywords.
Defaults
None
Command Modes
Global configuration mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
4.0 |
This command was introduced. |
Usage Guidelines
Use the feature udld command to enable UDLD globally on the device. UDLD must be also enabled on the other linked interface and its device. After enabling the devices, it is possible to enable a UDLD mode for an interface.
Use the no feature udld command to disable UDLD globally for Ethernet interfaces on the device.
This command does not require a license.
Examples
This example shows how to enable the UDLD for a device:
switch(config)# feature udld
This example shows how to disable UDLD for a device:
switch(config)# no feature udld
Related Commands
|
Command |
Description |
|---|---|
|
show udld |
Displays information about the UDLD configuration. |
feature vpc
To enable virtual port channels (vPCs), use the feature vpc command. To return to the default setting, use the no form of this command.
feature vpc
no feature vpc
Syntax Description
This command has no arguments or keywords.
Defaults
Disabled
Command Modes
Global configuration mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|
4.1(3) |
This command was introduced. |
Usage Guidelines
You must use the feature vpc command to enable the vPC functionality. You must enable vPCs before you can configure them.

Note ![]() When you disable vPC, the device clears all the vPC configurations.
When you disable vPC, the device clears all the vPC configurations.
This command does not require a license.
Examples
This example shows how to enable vPC functionality on the device:
switch(config)# feature vpc
Related Commands
|
Command |
Description |
|---|---|
|
show feature |
Displays information about the features enabled on the device. |
|
show vpc brief |
Displays vPC information on vPCs. If the feature is not enabled, the system displays an error when you enter this command. |
fex
To create a Fabric Extender and enter fabric extender configuration mode, use the fex command. To delete the Fabric Extender configuration, use the no form of this command.
fex chassis-id
no fex chassis-id
Syntax Description
|
chassis-id |
Fabric Extender chassis ID. The range is from 100 to 199. |
Defaults
None
Command Modes
Global configuration mode
Command History
|
Release |
Modification |
|---|---|
|
5.1(1) |
This command was introduced. |
Usage Guidelines
You must create and configure the Fabric Extender before you can connect and associate it to an interface on the parent switch. Once you associate the Fabric Extender to the switch, the configuration that you created is transferred over to the Fabric Extender and applied.
This command does not require a license.
Examples
This example shows how to enter Fabric Extender configuration mode:
switch# configure terminal
This example shows how to delete the Fabric Extender configuration:
switch(config-fex)# no fex 101
Related Commands
|
Command |
Description |
|---|---|
|
show fex |
Displays all configured Fabric Extender chassis connected to the switch. |
fex associate
To associate a Fabric Extender to a fabric interface, use the fex associate command. To disassociate the Fabric Extender, use the no form of this command.
fex associate chassis-id
no fex associate chassis-id
Syntax Description
|
chassis-id |
Fabric Extender chassis ID. The range is from 100 to 199. |
Defaults
None
Command Modes
Interface configuration mode
Command History
|
Release |
Modification |
|---|---|
|
5.1(1) |
This command was introduced. |
Usage Guidelines
Before you can associate an interface on the parent switch to the Fabric Extender, you must first make the interface into a fabric interface by entering the switchport mode fex-fabric command.
This command does not require a license.
Examples
This example shows how to associate the Fabric Extender to an Ethernet interface:
switch# configure terminal
switch(config)# interface ethernet 1/40
switch(config-if)# switchport mode fex-fabric
switch(config-if)# fex associate 101
This example shows how to associate the Fabric Extender to an EtherChannel interface:
switch# configure terminal
switch(config)# interface port-channel 4
switch(config-if)# switchport mode fex-fabric
switch(config-if)# fex associate 10
Related Commands
|
Command |
Description |
|---|---|
|
show fex |
Displays all configured Fabric Extender chassis connected to the switch. |
|
switchport mode fex-fabric |
Sets the interface to be an uplink port. |
flowcontrol
To enable or disable the ability of the Ethernet port to send and receive flow-control pause frames, use the flowcontrol command. To return to the default flow-control settings, use the no form of this command.
flowcontrol {send | receive} {desired | on | off}
no flowcontrol {send | receive}
Syntax Description
|
send |
Specifies the flow-control send setting for ports that run at 1000 Mbps or faster. |
|
receive |
Specifies the flow-control receive setting for ports that run at any speed. |
|
desired |
Specifies the remote port setting to desired for both send and receive, if the configuration of the remote port is unknown. |
|
on |
Specifies the remote port setting to on, if you want the local port to send flow-control pause frames. |
|
off |
Specifies the remote port’s send and receive parameter settings to off, if you do not want to use flow control. |
Defaults
1-Gb/s interfaces—Off for receive and send
10-Gb/s interfaces—Off for receive and send
Command Modes
Interface configuration mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
4.0 |
This command was introduced. |
Usage Guidelines
If the traffic between two F1 ports is routed and the sending port have Link flow control enabled, PAUSE frames will not be send if the receiving port is congested by the sending interface. While if the traffic is bridged between two F1 ports and sending port have a link flow control enabled, PAUSE frames will be send if the receiving port is congested by the sending interface.
Make sure that the remote port has the corresponding setting for the flow control that you need. If you want the local port to send flow-control pause frames, the remote port has a receive parameter set to on or desired. If you want the local port to receive flow-control frames, you must make sure that the remote port has a send parameter set to on or desired. If you do not want to use flow control, you can set the remote port’s send and receive parameters to off.
For Ethernet ports that run at 1 Gbps or faster speed, you can enable or disable the port’s ability to send and receive flow-control pause frames. For Ethernet ports that run slower than 1 Gbps, you can enable or disable only the port’s ability to receive pause frames.
When enabling flow control for the local port, you either fully enable the local port to send or receive frames regardless of the flow-control setting of the remote port or you set the local port to use the desired setting used by the remote port. If you enable both the local and remote ports for flow control or set the desired flow control of the other port, or set a combination of those two states, flow control is enabled for those ports.

Note ![]() For ports that run at 10 Gbps, you cannot use the desired state for the send or receive parameter.
For ports that run at 10 Gbps, you cannot use the desired state for the send or receive parameter.
To see how the different port flow-control states affect the link flow-control state, see Table 1.
Table 1 Port Flow-Control Influences on Link Flow Control
|
Port Flow Control States |
Link Flow Control State |
|
|---|---|---|
|
Port Receiving Data (Sends Pause Frames) |
Port Transmitting Data (Receives Pause Frames) |
|
|
Enabled |
Enabled |
Enabled |
|
Enabled |
Desired |
Enabled |
|
Enabled |
Disabled |
Disabled |
|
Desired |
Enabled |
Enabled |
|
Desired |
Desired |
Enabled |
|
Desired |
Disabled |
Disabled |
|
Disabled |
Enabled |
Disabled |
|
Disabled |
Desired |
Disabled |
|
Disabled |
Disabled |
Disabled |
This command does not require a license.
Examples
This example shows how to set Ethernet port 3/1 to send flow-control pause frames:
switch(config)# interface ethernet 3/1
switch(config-if)# flowcontrol send on
Related Commands
|
Command |
Description |
|---|---|
|
show interface flowcontrol |
Displays information about the interface flow control. |
|
show interface |
Displays information about the interface, which includes the flow-control parameter. |
graceful consistency-check
To enable a graceful type-1 consistency check on per VLAN basis, use the graceful consistency-check command. To disable the graceful consistency check, use the no form of this command.
graceful consistency-check
no graceful consistency-check
Syntax Description
This command has no arguments or keywords.
Defaults
Enabled
Command Modes
VPC domain configuration (config-vpc-domain)
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
5.2(1) |
This command was introduced. |
Usage Guidelines
This command does not require a license.
Examples
This example shows how to enable the graceful type-1 consistency check:
switch# configure terminal
switch(config)# vpc domain 1
switch(config-vpc-domain)# graceful consistency-check
switch(config-vpc-domain)#
This example shows how to disable the graceful type-1 consistency check:
switch# configure terminal
switch(config)# vpc domain 1
switch(config-vpc-domain)# no graceful consistency-check
switch(config-vpc-domain)#
Related Commands
|
Command |
Description |
|---|---|
|
vpc |
Moves other port channels into the vPC. |
|
vpc domain |
Creates a vPC domain. |
hsrp bfd
To enable Bidirectional Forwarding Detection (BFD) on a Hot Standby Router Protocol (HSRP) interface, use the hsrp bfd command. To return to the default setting, use the no form of this command.
hsrp bfd
no hsrp bfd
Syntax Description
This command has no keywords or arguments.
Defaults
None
Command Modes
Interface configuration mode
Command History
|
Release |
Modification |
|---|---|
|
5.0(2) |
This command was introduced. |
Usage Guidelines
Use the hsrp bfd command to enable BFD on an HSRP interface.
This command does not require a license.
Examples
This example shows how to enable BFD for an HSRP interface:
switch# configure terminal
switch(config)# interface ethernet 2/1
switch(config-if)# hsrp bfd
Related Commands
|
Command |
Description |
|---|---|
|
feature bfd |
Enables the BFD feature. |
inherit port-profile
To assign a port profile to an interface or range of interfaces and to inherit an additional port profile onto an existing port profile, use the inherit port-profile command. To remove an inherited port profile or to remove a port profile from specified interfaces, use the no form of this command.
inherit port-profile name
no inherit port-profile name
Syntax Description
|
name |
Port profile that you want to assign to interfaces or to inherit onto the existing port profile. |
Defaults
None
Command Modes
Interface configuration mode
Port-profile configuration mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
4.2(1) |
This command was introduced. |
Usage Guidelines
Use the inherit port-profile command to do the following:
•![]() Assign the port profile to a specified interface or range of specified interfaces. You do this action in the interface configuration mode. The maximum number of interfaces that can inherit a single profile is 512.
Assign the port profile to a specified interface or range of specified interfaces. You do this action in the interface configuration mode. The maximum number of interfaces that can inherit a single profile is 512.
•![]() Inherit configuration parameters from another port profile onto an existing port profile. You do this action in the port-profile mode, using the name of the port profile that you want to inherit configurations into. Only port profiles of the same type can be inherited by another port profile. The device supports four levels of inheritance except for the switchport private-vlan mapping and the private-vlan mapping commands, which support only one inheritance level. The same port profile can be inherited by any number of port profiles. In a port-profile inheritance hierarchy, all the profiles must have the same switchport configuration.
Inherit configuration parameters from another port profile onto an existing port profile. You do this action in the port-profile mode, using the name of the port profile that you want to inherit configurations into. Only port profiles of the same type can be inherited by another port profile. The device supports four levels of inheritance except for the switchport private-vlan mapping and the private-vlan mapping commands, which support only one inheritance level. The same port profile can be inherited by any number of port profiles. In a port-profile inheritance hierarchy, all the profiles must have the same switchport configuration.
See the port-profile command and the state-enabled command for information about creating, configuring, and enabling port profiles.
If you attempt to inherit a port profile to the wrong type of interface, the system returns an error.
When you remove a port profile from a range of interfaces, the system undoes the configuration from the interfaces first and then removes the port-profile link. Also, when you remove a port profile, the system checks the interface configuration and either skips port-profile commands that have been overridden by directly entered interface commands or returns the command to the default value.
You can also choose a subset of interfaces from which to remove a port profile from those interfaces to which you originally applied the profile. For example, if you configured a port profile and configured 10 interfaces to inherit that port profile, you can remove the port profile from just some of the specified 10 interfaces. The port profile continues to operate on the remaining interfaces to which it is applied.
You use the port-profile configuration mode to remove an inherited port profile from an original port profile.
This command does not require a license.
Examples
This example shows how to assign a specified port profile to a range of interfaces:
switch(config)# interface ethernet 2/1-10
switch(config-if)# port-profile test
This example shows how to inherit the configuration parameters from the port profile named switch onto the port profile named test:
switch(config-ppm)# inherit port-profile switch
Related Commands
|
Command |
Description |
|---|---|
|
show port-profile |
Displays information about port profiles. |
install feature-set fex
To install a Fabric Extender (FEX) feature set, use the install feature-set fex command.
install feature-set fex
Syntax Description
This command has no arguments or keywords.
Defaults
None
Command Modes
Global configuration mode
Command History
|
Release |
Modification |
|---|---|
|
5.1(1) |
This command was introduced. |
Usage Guidelines
This command does not require a license.
Examples
This example shows how to install a FEX feature set:
switch(config)# install feature-set fex
Related Commands
|
Command |
Description |
|---|---|
|
show fex |
Displays all configured Fabric Extender chassis connected to the switch. |
interface cmp-mgmt module
To create a Connectivity Management Processor (CMP) management interface and enter interface configuration mode, use the interface cmp-mgmt module command.
interface cmp-mgmt module number
Syntax Description
|
number |
Active or standby supervisor module number. Valid values are 9 or 10. |
Defaults
None
Command Modes
Global configuration mode
Interface configuration mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
4.0 |
This command was introduced. |
Usage Guidelines
Use the interface cmp-mgmt module command to create a CMP management interface.
This command does not require a license.
Examples
This example shows how to create a CMP management interface:
switch(config)# interface cmp-mgmt module 9
interface ethernet
To configure an Ethernet interface and enter interface configuration mode, use the interface ethernet command.
interface ethernet slot/port
Syntax Description
|
slot/port |
Slot number and port number for the Ethernet interface. The range is from 1 to 253 for slots and from 1 to 128 for ports.. |
Defaults
None
Command Modes
Global configuration mode
Interface configuration mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
4.0 |
This command was introduced. |
Usage Guidelines
Use the interface ethernet command to enter the interface configuration mode for the specified interface or range of interfaces.
This command does not require a license.
Examples
This example shows how to enter the interface command mode for the Ethernet interface on slot 2, port 1:
switch(config)# interface ethernet 2/1
Related Commands
|
Command |
Description |
|---|---|
|
show interface ethernet |
Displays information about the Ethernet interface. |
interface loopback
To create a loopback interface and enter interface configuration mode, use the interface loopback command. To remove a loopback interface, use the no form of this command.
interface loopback number
no interface loopback number
Syntax Description
|
number |
Interface number. The range is from 0 to 1023. |
Defaults
None
Command Modes
Global configuration mode
Interface configuration mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
4.0 |
This command was introduced. |
Usage Guidelines
Use the interface loopback command to create or modify loopback interfaces.
This command does not require a license.
Examples
This example shows how to create a loopback interface:
switch(config)# interface loopback 50
Related Commands
|
Command |
Description |
|---|---|
|
show interface loopback |
Displays information about the traffic on the specified loopback interface. |
interface mgmt
To configure the management interface and enter interface configuration mode, use the interface mgmt command.
interface mgmt number
Syntax Description
|
number |
Interface number. The range is from 0 to 1023. |
Defaults
None
Command Modes
Global configuration mode
Interface configuration mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
4.0 |
This command was introduced. |
Usage Guidelines
Use the interface mgmt command to configure the management interface and to enter the interface configuration mode.
This command does not require a license.
Examples
This example shows how to enter the interface configuration mode to configure the management interface:
switch(config)# interface mgmt
Related Commands
|
Command |
Description |
|---|---|
|
show interface mgmt0 |
Displays information about the traffic on the management interface. |
interface port-channel
To create a port-channel interface and enter interface configuration mode, use the interface port-channel command. To remove a logical port-channel interface or subinterface, use the no form of this command.
interface port-channel channel-number
no interface port-channel channel-number
Syntax Description
|
channel-number |
Channel number that is assigned to this port-channel logical interface. The range is from 1 to 4096. |
Defaults
None
Command Modes
Global configuration mode
Interface configuration mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
4.0 |
This command was introduced. |
Usage Guidelines
Use the interface port-channel command to create or delete port-channel groups and to enter the interface configuration mode for the port channel.
You can create port channels implicitly using the attach fex command or explicitly using the feature-set fex command.
A port can belong to only one channel group.
You can create subinterfaces on a Layer 3 port-channel interface. However, you cannot add a Layer 3 interface that has existing subinterfaces to a port channel.

Note ![]() The Layer 3 port-channel interface is the routed interface.
The Layer 3 port-channel interface is the routed interface.
The Link Aggregation Control Protocol (LACP) system ID is unique for each virtual device context (VDC), and channel-group numbers and names can be reused in different VDCs.
When you use the interface port-channel command, follow these guidelines:
•![]() If you are using Cisco Discovery Protocol (CDP), you must configure it only on the physical interface and not on the port-channel interface.
If you are using Cisco Discovery Protocol (CDP), you must configure it only on the physical interface and not on the port-channel interface.
•![]() If you do not assign a static MAC address on the port-channel interface, a MAC address is automatically assigned. If you assign a static MAC address and then later remove it, the MAC address is automatically assigned.
If you do not assign a static MAC address on the port-channel interface, a MAC address is automatically assigned. If you assign a static MAC address and then later remove it, the MAC address is automatically assigned.
•![]() The MAC address of the port channel is the address of the first operational port added to the channel group. If this first-added port is removed from the channel, the MAC address comes from the next operational port added, if there is one.
The MAC address of the port channel is the address of the first operational port added to the channel group. If this first-added port is removed from the channel, the MAC address comes from the next operational port added, if there is one.
This command does not require a license.
Examples
This example shows how to create a port-channel group interface with channel-group number 50:
switch(config)# interface port-channel 50
Related Commands
|
Command |
Description |
|---|---|
|
show interface port-channel |
Displays information on traffic on the specified port-channel interface. |
|
show port-channel summary |
Displays information on the port channels. |
|
show lacp |
Displays LACP information. |
interface tunnel
To create a tunnel interface and enter interface configuration mode, use the interface tunnel command. To remove a tunnel interface, use the no form of this command.
interface tunnel number
no interface tunnel number
Syntax Description
|
number |
Identifying interface number. The range is from 0 to 4095. |
Defaults
None
Command Modes
Global configuration mode
Interface configuration mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
4.0 |
This command was introduced. |
|
5.0(1) |
The maximum valid range of values was changed from 65535 to 4095. |
Usage Guidelines
Use the interface tunnel command to create or modify tunnel interfaces.
Cisco NX-OS supports the generic routing encapsulation (GRE) header defined in IETF RFC 2784. Cisco NX-OS does not support tunnel keys and other options from IETF RFC 1701.
You can configure IP tunnels only in the default virtual device context (VDC).
This command requires the Enterprise license.
Examples
This example shows how to create a tunnel interface:
switch(config)# interface tunnel 50
Related Commands
|
Command |
Description |
|---|---|
|
tunnel source |
Sets the source of the IP tunnel. |
|
tunnel destination |
Sets the destination of the IP tunnel. |
|
show interface tunnel |
Displays information about the traffic on the specified tunnel interface. |
interface vlan
To create a VLAN interface and enter interface configuration mode, use the interface vlan command. To remove a VLAN interface, use the no form of this command.
interface vlan vlan-id
no interface vlan vlan-id
Syntax Description
|
vlan-id |
VLAN to set when the interface is in access mode. The range is from 1 to 4094, except for the VLANs reserved for the internal switch use. |
Defaults
None
Command Modes
Global configuration mode
Interface configuration mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
4.0 |
This command was introduced. |
Usage Guidelines
Use the interface vlan command to create or modify VLAN interfaces.
The VLAN interface is created the first time that you enter the interface vlan command for a particular VLAN. The vlan-id argument corresponds to the VLAN tag that is associated with the data frames on an Inter-Switch Link (ISL), the IEEE 802.1Q-encapsulated trunk, or the VLAN ID that is configured for an access port.
This command does not require a license.
Examples
This example shows how to create a VLAN interface for VLAN 50:
switch(config)# interface vlan 50
Related Commands
|
Command |
Description |
|---|---|
|
feature interface-vlan |
Enables the ability to create VLAN interfaces. |
|
show interface vlan |
Displays information about the traffic on the specified VLAN interface. |
ip eigrp bfd
To enable Bidirectional Forwarding Detection (BFD) on an Enhanced Interior Gateway Routing Protocol (EIGRP) interface, use the ip eigrp bfd command. To return to the default setting, use the no form of this command.
ip eigrp instance-tag bfd
no ip eigrp instance-tag bfd
Syntax Description
|
instance-tag |
EIGRP instance tag. The instance tag can be any case-sensitive, alphanumeric string up to 20 characters. |
Defaults
None
Command Modes
Interface configuration mode
Command History
|
Release |
Modification |
|---|---|
|
5.0(2) |
This command was introduced. |
Usage Guidelines
Use the ip eigrp bfd command to enable BFD on an EIGRP interface. This command takes precedence over the bfd command in router configuration mode.
This command does not require a license.
Examples
This example shows how to enable BFD for an EIGRP interface:
switch# configure terminal
switch(config)# interface ethernet 2/1
switch(config-if)# ip eigrp Test1 bfd
Related Commands
|
Command |
Description |
|---|---|
|
bfd |
Enables BFD on all EIGRP interfaces. |
|
feature bfd |
Enables the BFD feature. |
ip ospf bfd
To enable Bidirectional Forwarding Detection (BFD) on an Open Shortest Path First version 2 (OSPFv2) interface, use the ip ospf bfd command. To return to the default setting, use the no form of this command.
ip ospf bfd
no ip ospf bfd
Syntax Description
This command has no keywords or arguments.
Defaults
None
Command Modes
Interface configuration mode
Command History
|
Release |
Modification |
|---|---|
|
5.0(2) |
This command was introduced. |
Usage Guidelines
Use the ip ospf bfd command to enable BFD on an OSPFv2 interface. This command takes precedence over the bfd command in router configuration mode.
This command does not require a license.
Examples
This example shows how to enable BFD for an OSPF interface:
switch# configure terminal
switch(config)# interface ethernet 2/1
switch(config-if)# ip ospf bfd
Related Commands
|
Command |
Description |
|---|---|
|
bfd |
Enables BFD on all OSPFv2 interfaces. |
|
feature bfd |
Enables the BFD feature. |
ip pim bfd
To enable Bidirectional Forwarding Detection (BFD) for Protocol Independent Multicast (PIM), use the ip pim bfd command. To return to the default setting, use the no form of this command.
ip pim bfd
no ip pim bfd
Syntax Description
This command has no keywords or arguments.
Defaults
None
Command Modes
Global configuration mode
Command History
|
Release |
Modification |
|---|---|
|
5.0(2) |
This command was introduced. |
Usage Guidelines
Use the ip pim bfd command to enable BFD for PIM.
This command does not require a license.
Examples
This example shows how to enable BFD for PIM:
switch# configure terminal
switch(config)# ip pim bfd
Related Commands
|
Command |
Description |
|---|---|
|
feature bfd |
Enables the BFD feature. |
ip pim bfd-instance
To enable Bidirectional Forwarding Detection (BFD) for Protocol Independent Multicast (PIM) on an interface, use the ip pim bfd-instance command. To return to the default setting, use the no form of this command.
ip pim bfd-instance [disable]
no ip pim bfd-instance [disable]
Syntax Description
|
disable |
Disables BFD for PIM on this interface. |
Defaults
None
Command Modes
Interface configuration mode
Command History
|
Release |
Modification |
|---|---|
|
5.0(2) |
This command was introduced. |
Usage Guidelines
Use the ip pim bfd-instance command to enable BFD for PIM on an interface. This configuration (with or without the disable keyword) overrides the BFD configuration for PIM at the global or VRF configuration level.
This command does not require a license.
Examples
This example shows how to disable BFD for PIM on interface ethernet 2/1 when BFD is enabled globally for PIM:
switch# configure terminal
switch(config)# ip pim bfd
switch(config)# interface ethernet 2/1
switch(config-if)# ip pim bfd-instance disable
Related Commands
|
Command |
Description |
|---|---|
|
feature bfd |
Enables the BFD feature. |
ip route static bfd
To enable Bidirectional Forwarding Detection (BFD) on a static route, use the ip route static bfd command. To return to the default setting, use the no form of this command.
ip route static bfd interface {nh-address | nh-prefix}
no ip route static bfd interface {nh-address | nh-prefix}
Syntax Description
|
interface |
Interface that this static route resides on. Use the ? keyword to display the supported interfaces. |
|
nh-address |
Next-hop address for this static route, in dotted decimal notation. |
|
nh-prefix |
Next-hop prefix for this static route, in dotted decimal notation. |
Defaults
None
Command Modes
Interface configuration mode
Command History
|
Release |
Modification |
|---|---|
|
5.0(2) |
This command was introduced. |
Usage Guidelines
Use the ip route static bfd command to enable BFD on a static route.
This command does not require a license.
Examples
This example shows how to enable BFD for a static route:
switch# configure terminal
switch(config)# interface ethernet 2/1
switch(config-if)# ip route static bfd ethernet 2/1 192.0.2.4
Related Commands
|
Command |
Description |
|---|---|
|
feature bfd |
Enables the BFD feature. |
ipv6 eigrp bfd
To enable Bidirectional Forwarding Detection (BFD) on an Enhanced Interior Gateway Routing Protocol (EIGRP) interface, use the ipv6 eigrp bfd command. To return to the default setting, use the no form of this command.
ipv6 eigrp instance-tag bfd
no ipv6 eigrp instance-tag bfd
Syntax Description
|
instance-tag |
EIGRP instance tag. The instance tag can be any case-sensitive, alphanumeric string up to 20 characters. |
Defaults
None
Command Modes
Interface configuration mode
Command History
|
Release |
Modification |
|---|---|
|
5.0(2) |
This command was introduced. |
Usage Guidelines
Use the ipv6 eigrp bfd command to enable BFD on an EIGRP interface. This command takes precedence over the bfd command in router configuration mode.
This command does not require a license.
Examples
This example shows how to enable BFD for an EIGRP interface:
switch# configure terminal
switch(config)# interface ethernet 2/1
switch(config-if)# ipv6 eigrp Test1 bfd
Related Commands
|
Command |
Description |
|---|---|
|
bfd |
Enables BFD on all EIGRP interfaces. |
|
feature bfd |
Enables the BFD feature. |
isis bfd
To enable Bidirectional Forwarding Detection (BFD) on an Intermediate System-to-Intermediate System (IS-IS) interface, use the isis bfd command. To return to the default setting, use the no form of this command.
isis bfd
no isis bfd
Syntax Description
This command has no keywords or arguments.
Defaults
None
Command Modes
Interface configuration mode
Command History
|
Release |
Modification |
|---|---|
|
5.0(2) |
This command was introduced. |
Usage Guidelines
Use the isis bfd command to enable BFD on an IS-IS interface. This command takes precedence over the bfd command in router configuration mode.
This command does not require a license.
Examples
This example shows how to enable BFD for an IS-IS interface:
switch# configure terminal
switch(config)# interface ethernet 2/1
switch(config-if)# isis bfd
Related Commands
|
Command |
Description |
|---|---|
|
bfd |
Enables BFD on all IS-IS interfaces. |
|
feature bfd |
Enables the BFD feature. |
fabricpath switch-id
To configure an emulated switch ID, use the fabricpath switch-id command. To return to the default setting, use the no form of this command.
fabricpath switch-id switch-id
no fabricpath switch-id switch-id
Syntax Description
|
switch-id |
Emulated switch ID. The range is from 1 to 4095. |
Defaults
None
Command Modes
Interface configuration mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
5.1(1) |
This command was introduced. |
Usage Guidelines
This command does not require a license.
Examples
This example shows how to configure an emulated switch ID:
switch(config)# vpc domain 1
switch(config-vpc-domain)# fabricpath switch-id 4
Configuring fabricpath switch id will flap vPCs. Continue (yes/no)? [no] yes
--------:: Re-init of peer-link and vPCs started ::--------
switch(config-vpc-domain)#
This example shows how to set the default ID value:
switch(config)# vpc domain 1
switch(config-vpc-domain)# no fabricpath switch-id 4
Deconfiguring fabricpath switch id will flap vPCs. Continue (yes/no)? [no] yes
--------:: Re-init of peer-link and vPCs started ::--------
switch(config-vpc-domain)#
Related Commands
|
Command |
Description |
|---|---|
|
show interface switchport |
Displays the administrative and operational status of a switching (nonrouting) port. |
l2protocol tunnel
To enable Layer 2 protocol tunneling, use the l2protocol tunnel command. To disable protocol tunneling, use the no form of this command.
l2protocol tunnel [cdp | stp | vtp]
no l2protocol tunnel [cdp | stp | vtp]
Syntax Description
|
cdp |
(Optional) Enables Cisco Discovery Protocol (CDP) tunneling. |
|
stp |
(Optional) Enables Spanning Tree Protocol (STP) tunneling. |
|
vtp |
(Optional) Enables VLAN Trunking Protocol (VTP) tunneling. |
Defaults
Layer 2 protocol tunneling is disabled.
Command Modes
Interface configuration mode
Command History
|
Release |
Modification |
|---|---|
|
5.0(2) |
This command was introduced. |
Usage Guidelines
This command does not require a license.
Examples
This example shows how to enable Layer 2 protocol tunneling:
switch(config-if)# l2protocol tunnel cdp
Related Commands
|
Command |
Description |
|---|---|
|
show l2protocol tunnel |
Displays Layer 2 protocol tunnel information. |
l2protocol tunnel cos
To specify a global class of service (CoS) value on all Layer 2 protocol tunneling interfaces, use the l2protocol tunnel cos command. To reset the global CoS value to its default, use the no form of this command.
l2protocol tunnel cos cos-value
no l2protocol tunnel cos
Syntax Description
|
cos-value |
CoS value. The range is from 0 to 7. The default value is 5. |
Defaults
CoS value is 5.
Command Modes
Global configuration mode
Command History
|
Release |
Modification |
|---|---|
|
5.0(2) |
This command was introduced. |
Usage Guidelines
This command does not require a license.
Examples
This example shows how to specify a global CoS value on all Layer 2 protocol tunneling interfaces:
switch(config)# l2protocol tunnel cos 7
Related Commands
|
Command |
Description |
|---|---|
|
show l2protocol tunnel |
Displays Layer 2 protocol tunnel information. |
l2protocol tunnel drop-threshold
To specify the maximum number of packets that can be processed on a Layer 2 protocol tunneling interface before being dropped, use the l2protocol tunnel drop-threshold command. To reset the values to 0 and disable the drop threshold, use the no form of this command.
l2protocol tunnel drop-threshold [cdp | stp | vtp] packets-per-sec
no l2protocol tunnel drop-threshold [cdp | stp | vtp]
Syntax Description
|
cdp |
(Optional) Specifies the number of Cisco Discovery Protocol (CDP) packets that can be processed on an interface. |
|
stp |
(Optional) Specifies the number of Spanning Tree Protocol (STP) packets that can be processed on an interface. |
|
vtp |
(Optional) Specifies the number of VLAN Trunking Protocol (VTP) packets that can be processed on an interface. |
|
packets-per-sec |
Maximum number of packets that can be processed on an interface before being dropped. The range is from 1 to 4096. |
Defaults
The drop threshold is disabled.
Command Modes
Interface configuration mode
Command History
|
Release |
Modification |
|---|---|
|
5.0(2) |
This command was introduced. |
Usage Guidelines
This command does not require a license.
Examples
This example shows how to specify the maximum number of CDP packets that can be processed on an Layer 2 protocol tunneling interface before being dropped:
switch(config-if)# l2protocol tunnel drop-threshold cdp 1024
Related Commands
|
Command |
Description |
|---|---|
|
show l2protocol tunnel |
Displays Layer 2 protocol tunnel information. |
l2protocol tunnel shutdown-threshold
To specify the maximum number of packets that can be processed on a Layer 2 protocol tunneling interface, use the l2protocol tunnel shutdown-threshold command. To reset the values to 0 and disable the shutdown threshold, use the no form of this command
l2protocol tunnel shutdown-threshold [cdp | stp | vtp] packets-per-sec
no l2protocol tunnel shutdown-threshold [cdp | stp | vtp]
Syntax Description
|
cdp |
(Optional) Specifies the number of Cisco Discovery Protocol (CDP) packets that can be processed on an interface. |
|
stp |
(Optional) Specifies the number of Spinning Tree Protocol (STP) packets that can be processed on an interface. |
|
vtp |
(Optional) Specifies the number of VLAN Trunking Protocol (VTP) packets that can be processed on an interface. |
|
packets-per-sec |
Maximum number of packets that can be processed on an interface. When the number of packets is exceeded, the port is put in error-disabled state. The range is from 1 to 4096. |
Defaults
The shutdown threshold is disabled.
Command Modes
Interface configuration mode
Command History
|
Release |
Modification |
|---|---|
|
5.0(2) |
This command was introduced. |
Usage Guidelines
When the number of packets is exceeded, the port is put in error-disabled state.
This command does not require a license.
Examples
This example shows how to specify the maximum number of packets that can be processed on an Layer 2 protocol tunneling interface before the port is put in error-disabled state:
switch(config-if)# l2protocol tunnel shutdown-threshold 2048
Related Commands
|
Command |
Description |
|---|---|
|
show l2protocol tunnel |
Displays Layer 2 protocol tunnel information. |
lacp max-bundle
To configure a port channel maximum bundle, use the lacp max-bundle command. To return to the default setting, use the no form of this command.
lacp max-bundle max-bundle-number
no lacp mac-bundle max-bundle-number
Syntax Description
|
max-bundle- |
Maximum bundle number. The range is from 1 to 16. |
Command Default
The default for the port channel max-bundle is 16.
The allowed range is from 1 to 16.
Command Modes
Interface configuration mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
5.1(1) |
This command was introduced. |
Usage Guidelines
This command does not require a license.

Note ![]() Even if the default value is 16, the number of active members in a port channel is the minimum number of the maximum bundle configured and the maximum active members that are allowed in the portchannel.
Even if the default value is 16, the number of active members in a port channel is the minimum number of the maximum bundle configured and the maximum active members that are allowed in the portchannel.
Examples
This example shows how to configure port channel maximum bundles:
switch(config)# interface port-channel 1
switch(config-if)# lacp max-bundle 2
Related Commands
|
Command |
Description |
|
interface |
Enters the interface configuration mode and configures the types and identities of interfaces. |
lacp min-links
To configure the minimum links for a port channel, use the lacp min-links command. To return to the default setting, use the no form of this command.
lacp min-links number
no lacp min-links number
Syntax Description
|
number |
Minimum link number. The range is from 1 to 16. |
Defaults
The default for the port channel minimum link is 1.
The allowed range is from 1 to 16.
Command Modes
Interface configuration mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
5.1(1) |
This command was introduced. |
Usage Guidelines
This command does not require a license.
Examples
This example shows how to configure the minimum link for a port channel:
switch(config)# interface port-channel 1
switch(config-if)# lacp min-links 3
Related Commands
|
Command |
Description |
|
interface |
Enters the interface configuration mode and configures the types and identities of interfaces. |
lacp port-priority
To set the priority for the physical interfaces for the Link Aggregation Control Protocol (LACP), use the lacp port-priority command. To return the port priority to the default value, use the no form of this command.
lacp port-priority priority
no lacp port-priority
Syntax Description
|
priority |
Priority for the physical interfaces. The range is from 1 to 65535. |
Defaults
32768
Command Modes
Interface configuration mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
4.0 |
This command was introduced. |
Usage Guidelines
Each port configured to use LACP has an LACP port priority. You can accept the default value of 32768 for the LACP port priority, or you can configure a value between 1 and 65535. LACP uses the port priority with the port number to form the port identifier. . The port priority is used to decide which ports should be put into standby mode when there is a hardware limitation that prevents all compatible ports from aggregating or when you have more than eight ports configured for the channel group.
When setting the priority, note that a higher number means a lower priority.
This command does not require a license.
Examples
This example shows how to set the LACP port priority for the interface to 2000:
switch(config-if)# lacp port-priority 2000
Related Commands
|
Command |
Description |
|---|---|
|
show lacp |
Displays LACP information. |
lacp rate
To set the rate at which the Link Aggregation Control Protocol (LACP) sends LACP control packets to an LACP-supported interface, use the lacp rate command. To reset the rate to its default, use the no form of this command.
lacp rate {fast | normal}
no lacp rate {fast | normal}
Syntax Description
|
fast |
Specifies the fast rate of 1 second. |
|
normal |
Specifies the default rate of 30 seconds. |
Defaults
30 seconds
Command Modes
Interface configuration mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
5.1(1) |
This command was introduced. |
Usage Guidelines
You can change the LACP timer rate to modify the duration of the LACP timeout. Use the lacp rate command to set the rate at which LACP control packets are sent to an LACP-supported interface. You can change the timeout rate from the default rate (30 seconds) to the fast rate (1 second).
This command is supported only on LACP-enabled interfaces.
This command does not require a license.
Examples
This example shows how to configure the LACP fast rate on Ethernet interface 1/4:
switch# configure terminal
switch (config)# interface ethernet 1/4
switch(config-if)# lacp rate fast
Related Commands
|
Command |
Description |
|---|---|
|
show lacp |
Displays LACP information. |
lacp system-priority
To set the system priority of the device for the Link Aggregation Control Protocol (LACP), use the lacp system-priority command. To return the system priority to the default value, use the no form of this command.
lacp system-priority priority
no lacp system-priority
Syntax Description
|
priority |
Priority for the physical interfaces. The range is from 1 to 65535. |
Defaults
32768
Command Modes
Global configuration mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
4.0 |
This command was introduced. |
Usage Guidelines
Each device that runs LACP has an LACP system priority value. You can accept the default value of 32768 for this parameter, or you can configure a value between 1 and 65535. LACP uses the system priority with the MAC address to form the system ID and also during negotiation with other systems. The system ID is unique for each virtual device context (VDC).
When setting the priority, note that a higher number means a lower priority.
This command does not require a license.
Examples
This example shows how to set the LACP system priority for the device to 2500:
switch(config)# lacp system-priority 2500
Related Commands
|
Command |
Description |
|---|---|
|
show lacp |
Displays LACP information. |
|
show lacp system identifier |
Displays information on the LACP system identifier. |
link debounce
To enable the debounce timer for Ethernet ports and specify a debounce time, use the link debounce command. To disable the timer, use the no form of this command.
link debounce [time milliseconds]
no link debounce
Syntax Description
|
time milliseconds |
(Optional) Specifies the debounce timer for the time you want to specify. The range is from 0 to 5000. |
Defaults
Enabled
300 milliseconds
Command Modes
Interface configuration mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
4.0 |
This command was introduced. |
Usage Guidelines
Use the link debounce command to enable the debounce timer for Ethernet ports and set it for a specified amount of time in milliseconds. The default debounce time applies when you enter the link debounce command with no arguments.
The range of time is from 1 to 5000 ms. The debounce timer is disabled if you specify the time to 0 ms.
This command does not require a license.
Examples
This example shows how to enable the debounce timer and set the debounce time to 1000 ms for the Ethernet port 3/1:
switch(config)# interface ethernet 3/1
switch(config-if)# link debounce time 1000
This example shows how to disable the debounce timer for the Ethernet port 3/1:
switch(config)# interface ethernet 3/1
switch(config-if)# no link debounce
Related Commands
|
Command |
Description |
|
show interface debounce |
Displays the debounce time information about the interface. |
load-interval
To change the sampling interval for statistics collections on interfaces, use the load-interval command. To return to the default sampling interval, use the no form of this command.
load-interval [counter {1 | 2 | 3}] seconds
no load-interval [counter {1 | 2 | 3}] [seconds]
Syntax Description
|
counter |
Specifies counter for this load interval. |
|
1 | 2 | 3 |
Specifies the number of counters configured on the interface. |
|
seconds |
Specifies the interval between sampling statistics on the interface. The range is from 60 to 300 seconds for VLAN network interfaces, and the range is from 30 to 300 seconds for Ethernet and port-channel interfaces. |
Defaults
1—30 seconds; 60 seconds for VLAN network interface
2—300 seconds
3—not configured
Command Modes
Interface configuration mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
4.2(1) |
This command was introduced. |
Usage Guidelines
Use the load-interval command to obtain bit-rate and packet-rate statistics for three different durations.
You can set the statistics collection intervals on the following types of interfaces:
•![]() Ethernet interfaces
Ethernet interfaces
•![]() Port-channel interfaces
Port-channel interfaces
•![]() VLAN network interfaces
VLAN network interfaces
You cannot use this command on the management interface or subinterfaces.
This command sets the sampling interval for such statistics as packet rate and bit rate on the specified interface.
This command does not require a license.
Examples
This example shows how to set the three sample intervals for the Ethernet port 3/1:
switch(config)# interface ethernet 3/1
switch(config-if)# load-interval counter 1 60
switch(config-if)# load-interval counter 2 135
switch(config-if)# load-interval counter 3 225
Related Commands
|
Command |
Description |
|
show interface |
Displays information about the interface. |
max-ports
To assign a maximum possible number of interfaces that a port profile can inherit, use the max-ports command. To return to the default value, use the no form of this command.
max-ports number
no max-ports number
Syntax Description
|
number |
Maximum number of interfaces that a port profile can inherit. The range is from 1 to 512, and there is no default value. |
Defaults
None
Command Modes
Port-profile configuration mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
4.2(1) |
This command was introduced. |
Usage Guidelines
You must be in the port-profile configuration mode in order to use this command.
You must enable each specific port profile by using the state-enabled command.
This command does not require a license.
Examples
This example shows how to enter the port-profile configuration mode and to configure the maximum possible number of interfaces that a port profile can inherit:
switch(config)# port-profile type ethernet type test
switch(config-ppm)# max-ports 500
Related Commands
|
Command |
Description |
|---|---|
|
state-enabled |
Enables a specified port profile. |
|
show port-profile |
Displays information about port profiles. |
mdix auto
To enable automatic medium-dependent independent crossover (MDIX) detection for the interface, use the mdix auto command. To turn automatic detection off, use the no form of this command.
mdix auto
no mdix
Syntax Description
This command has no arguments or keywords.
Defaults
Enabled
Command Modes
Interface configuration mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
4.0 |
This command was introduced. |
Usage Guidelines
Use the mdix auto command to enable automatic MDIX detection for the port. Use the no mdix command to disable MDIX detection for the port.
This command is only available on copper Ethernet ports. To detect the type of connection (crossover or straight) with another copper Ethernet port, enable the MDIX parameter for the local port. Before you begin, MDIX must be enabled on the remote port.
This command does not require a license.
Examples
This example shows how to enable MDIX for Ethernet port 3/1:
switch(config)# interface ethernet 3/1
switch(config-if)# mdix auto
This example shows how to disable MDIX for Ethernet port 3/1:
switch(config)# interface ethernet 3/1
switch(config-if)# no mdix
Related Commands
|
Command |
Description |
|
show interface |
Displays information about the interface, which includes the MDIX status. |
medium
To set the medium mode for an interface, use the medium command. To remove the entry, use the no form of this command.
medium {broadcast | p2p}
no medium {broadcast | p2p}
Syntax Description
|
broadcast |
Configures the interface as a broadcast medium. |
|
p2p |
Configures the interface as a point-to-point medium. |
Defaults
None
Command Modes
Interface configuration mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
4.0 |
This command was introduced. |
Usage Guidelines
The medium command is used to configure the interface as broadcast or point to point.
This command does not require a license.
Examples
This example shows how to configure the interface for point-to-point medium:
switch(config-if)# medium p2p
mtu
To configure the maximum transmission unit (MTU) size for Layer 2 and Layer 3 Ethernet interfaces, use the mtu command. To return to the default value, use the no form of this command.
mtu size
no mtu
Syntax Description
|
size |
For a Layer 2 interface, specify either the default MTU size (1500) in bytes or the system jumbo MTU size (9216, unless you have changed the default system jumbo size). For a Layer 3 interface, specify any even number between the range of 576 and 9216. |
Defaults
1500 bytes
Command Modes
Interface configuration mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
4.0 |
This command was introduced. |
Usage Guidelines
Use the mtu size command to configure the MTU size for Layer 2 and Layer 3 Ethernet interfaces.
For Layer 3 interfaces, you can configure the MTU to be between 576 and 9216 bytes (even values are required). For Layer 2 interfaces, you can configure the MTU to be either the system default MTU (1500 bytes) or the system jumbo MTU size (which has the default size of 9216 bytes).

Note ![]() You can change the system jumbo MTU size, but if you change that value, you should also update the Layer 2 interfaces that use that value so that they use the new system jumbo MTU value. If you do not update the MTU value for Layer 2 interfaces, those interfaces use the system default MTU (1500 bytes).
You can change the system jumbo MTU size, but if you change that value, you should also update the Layer 2 interfaces that use that value so that they use the new system jumbo MTU value. If you do not update the MTU value for Layer 2 interfaces, those interfaces use the system default MTU (1500 bytes).
This command does not require a license.
Examples
This example shows how to configure the Layer 2 Ethernet port 3/1 with the default MTU size (1500):
switch(config)# interface ethernet 3/1
switch(config-if)# mtu 1500
Related Commands
|
Command |
Description |
|
show interface |
Displays information about the interface, which includes the MTU size. |
peer-gateway
To configure the device to send virtual port-channel (vPC) packets to the device’s MAC address, use the peer-gateway command. To return to the default value, use the no form of this command.
peer-gateway
no peer-gateway
Syntax Description
This command has no arguments or keywords.
Defaults
None
Command Modes
vpc-domain configuration mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
4.2(1) |
This command was introduced. |
Usage Guidelines
Use the peer-gateway command to have a vPC peer device act as the gateway even for packets that are sent to the vPC peer device’s MAC address.
This command does not require a license.
Examples
This example shows how to configure the device to use the switch gateway even for the packets that are sent the vPC:
switch(config)# vpc-domain 5
switch(config-vpc-domain)# peer-gateway
Related Commands
|
Command |
Description |
|
vpc-domain |
Configures a vPC domain and enters the vpc-domain configuration mode. |
peer-keepalive destination
To configure the virtual port-channel (vPC) peer-keepalive link and message between vPC peer devices, use the peer-keepalive destination command.
peer-keepalive destination ipaddress [hold-timeout secs] [interval msecs {timeout secs}[{precedence {prec-value | network | internet | critical | flash-override | flash | immediate | priority | routine}} | {tos {tos-value | max-reliability | max-throughput | min-delay | min-monetary-cost | normal}} | tos-byte tos-byte-value][source ipaddress][udp-port number] [vrf {name | management | vpc-keepalive}]
Syntax Description
|
ipaddress |
IP address of the remote vPC peer device. Note |
|
hold-timeout secs |
(Optional) Specifies when the peer-keepalive link goes down, the secondary vPC peer device waits the hold-timeout interval. The range is from 3 to 10. During the hold-timeout, the vPC secondary device does not take any action based on any keepalive messages received. Because the keepalive might be received just temporarily, such as if a supervisor fails a few seconds after the peer link goes down. |
|
interval msecs |
Specifies the number of milliseconds that you want between sending keepalive messages to the remote vPC peer device. This variable configures the interval between sending peer-keepalive messages to the remote vPC peer device and the maximum period to wait to receive a keepalive message from the remote vPC peer device. The range is from 400 to 10,000. |
|
timeout secs |
(Optional) Specifies that the timeout timer starts at the end of the hold-timeout interval. During the timeout period, the secondary vPC peer device checks for vPC peer-keepalive hello messages from the primary vPC peer device. If the secondary vPC peer device receives a single hello message, that device disables all vPC interfaces on the secondary vPC peer device. The range is from 3 and 20. During the timeout, the vPC secondary device takes action to become the vPC primary device if no keepalive message is received by the end of the configured interval. |
|
precedence prec-value |
(Optional) Specifies the precedence value for the peer-keepalive message. Valid values are as follows: • • • • • • • • • |
|
tos tos-value |
(Optional) Specifies the precedence or ToS value for the peer-keepalive message. Valid values are as follows: • • • • • • Note |
|
tos-byte |
(Optional) Specifies the precedence, or 8-bit ToS value, for the peer-keepalive message. A higher numerical value indicates the higher throughput priority. The range is from 0 to 255. |
|
source |
(Optional) Specifies the IP address of the local vPC peer device. Note |
|
number |
(Optional) Number of the UDP port to send and receive the vPC peer-keepalive messages. The range is from 1024 to 6500. |
|
name |
(Optional) Name of virtual routing and rorwarding (VRF) instance that you want to use for the vPC peer-keepalive link and messages. |
|
vrf vrf-name |
(Optional) Specifies a VRF instance. |
|
management |
(Optional) Specifies management. |
|
vpc-keepalive |
(Optional) Specifies vPC keepalive. |
Defaults
Peer-keepalive is disabled.
Hold-timeout is 3 seconds.
Interval is 1000 milliseconds.
Timeout is 5 seconds.
Precedence is default, with a level of 6 (internet).
UDP port is 3200.
VRF is management VRF.
Command Modes
vpc-domain configuration mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|
4.1(3) |
This command was introduced. |
Usage Guidelines
You must enable the vPC feature before you can configure the peer-keepalive parameters. The vPC keepalive messages notify the system if one of the vPC peer devices goes down.
You must configure the peer-keepalive messages on each of the vPC peer devices to enable the functionality.
Although the keepalive messages can transmit over any Layer 3 topology, we recommend that you create and configure a separate VRF with Layer 3 ports on each vPC peer device as the source and destination for the vPC keepalive messages. The default ports and VRF for the peer-alive link are the management ports and the management VRF. Do not use the peer link itself for the vPC peer-keepalive messages.
Ensure that both the source and destination IP addresses used for the peer-keepalive messages are unique in your network.
The vPC keepalive messages are IP/UDP messages.
This command accepts only IPv4 addresses.
The device assumes that its vPC peer device is down when the device does not receive any messages from the peer during the timeout period. We recommend that you configure the timeout value to be three times the interval value.
You can configure either the precedence, tos, or tos-byte value to ensure throughput for the vPC peer-keepalive message.

Note ![]() We recommend that you create a separate VRF and assign a Layer 3 port on each vPC peer device for the peer-keepalive link.
We recommend that you create a separate VRF and assign a Layer 3 port on each vPC peer device for the peer-keepalive link.
This command does not require a license.
Examples
This example shows how to configure the IP address of the remote vPC peer device for the fault-tolerant link:
switch(config-vpc-domain)# peer-keepalive destination 172.28.231.85
Related Commands
|
Command |
Description |
|---|---|
|
show running-config vpc all |
Displays information on the vPC peer-keepalive status. If the feature is not enabled, the system displays an error when you enter this command. |
|
show vpc peer-keepalive |
Displays information on the vPC peer-keepalive status. If the feature is not enabled, the system displays an error when you enter this command. |
peer-switch
To enable the virtual port channel (vPC) switch pair to appear as a single Spanning Tree Protocol (STP) root in the Layer 2 topology, use the peer-switch command. To disable the peer switch vPC topology, use the no form of this command.
peer-switch
no peer-switch
Syntax Description
This command has no arguments or keywords.
Defaults
Peer switch Layer 2 topology is disabled.
Command Modes
vPC domain configuration mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
5.0(2) |
This command was introduced. |
Usage Guidelines
This command does not require a license.
Examples
This example shows how to enable the vPC switch pair to appear as a single STP root in the Layer 2 topology:
switch(config)# vpc domain 5
switch(config-vpc-domain)# peer-switch
2010 Apr 28 14:44:44 switch %STP-2-VPC_PEERSWITCH_CONFIG_ENABLED: vPC peer-switch configuration is enabled. Please make sure to configure spanning tree "bridge" priority as per recommended guidelines to make vPC peer-switch operational.
Related Commands
|
Command |
Description |
|---|---|
|
vpc domain |
Creates a virtual port-channel (vPC) domain. |
port-channel load-balance
To set the load-balancing method among the interfaces in the channel-group bundle, use the port-channel load-balance command. To return the system priority to the default value, use the no form of this command.
port-channel load-balance method [module slot]
no port-channel load-balance [method [module slot]]
Syntax Description
|
method |
Load-balancing method. See the «Usage Guidelines» section for a list of valid values. |
|
module slot |
(Optional) Specifies the module slot number. |
Defaults
Layer 2 packets—src-dst-mac
Layer 3 packets—src-dst-ip
Command Modes
Global configuration mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
4.0 |
This command was introduced. |
|
5.1(3) |
The word ethernet was removed from the command name. |
Usage Guidelines
When you do not specify a module, you are configuring load balancing for the entire device. When you use the module parameter, you are configuring load balancing for the specified modules
Valid method values are as follows:
•![]() dst-ip—Loads distribution on the destination IP address.
dst-ip—Loads distribution on the destination IP address.
•![]() dst-mac—Loads distribution on the destination MAC address.
dst-mac—Loads distribution on the destination MAC address.
•![]() dst-port—Loads distribution on the destination port.
dst-port—Loads distribution on the destination port.
•![]() src-dst-ip—Loads distribution on the source XOR-destination IP address.
src-dst-ip—Loads distribution on the source XOR-destination IP address.
•![]() src-dst-mac—Loads distribution on the source XOR-destination MAC address.
src-dst-mac—Loads distribution on the source XOR-destination MAC address.
•![]() src-dst-port—Loads distribution on the source XOR-destination port.
src-dst-port—Loads distribution on the source XOR-destination port.
•![]() src-ip—Loads distribution on the source IP address.
src-ip—Loads distribution on the source IP address.
•![]() src-mac—Loads distribution on the source MAC address.
src-mac—Loads distribution on the source MAC address.
•![]() src-port—Loads distribution on the source port.
src-port—Loads distribution on the source port.

Note ![]() You cannot configure load balancing using port channels per virtual device context (VDC0. You must be in the default VDC to configure this feature; if you attempt to configure this feature from another VDC, the system returns an error.
You cannot configure load balancing using port channels per virtual device context (VDC0. You must be in the default VDC to configure this feature; if you attempt to configure this feature from another VDC, the system returns an error.
Use the module keyword to configure the module independently for port-channeling and load-balancing mode. The remaining module use the current load-balancing method configured for the entire device or the default method if you have not configured a method for the entire device. When you enter the no with the module keyword, the load-balancing method for the specified module takes the current load-balancing method that is in use for the entire device. If you configured a load-balancing method for the entire device, the specified module uses that configured method rather than the default src-dst-ip/src-dst-mac. The per module configuration takes precedence over the load-balancing method configured for the entire device.
You can configure one load-balancing mode for the entire device, a different mode for specified modules, and another mode for other specified modules. The per-module configuration takes precedence over the load-balancing configuration for the entire device.
Use the option that provides the balance criteria with the greatest variety in your configuration. For example, if the traffic on a port channel is going only to a single MAC address and you use the destination MAC address as the basis of port channel load balancing, the port channel always chooses the same link in that port channel; using source addresses or IP addresses might result in better load balancing.
This command does not require a license.
Examples
This example shows how to set the load-balancing method for the entire device to use the source port:
switch(config)# port-channel load-balance src-port
Related Commands
|
Command |
Description |
|---|---|
|
show port-channel load-balance |
Displays information on port-channel load balancing. |
port-profile
To create a port profile and enter the port-profile configuration mode or to enter into the port-profile configuration mode of a previously created port profile, use the port-profile command. To remove the port profile, use the no form of this command.
port-profile [type {ethernet | interface-vlan | port-channel}] name
no port-profile [type {ethernet | interface-vlan | port-channel}] name
Syntax Description
|
type |
(Optional) Specifies the type of interfaces. |
|
ethernet |
Specifies Layer 2 or Layer 3 interfaces. |
|
interface-vlan |
Specifies VLAN network interfaces. |
|
port-channel |
Specifies port-channel interfaces. |
|
name |
Name of the port profile. |
Defaults
None
Command Modes
Interface configuration mode
Port-profile configuration mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
4.2(1) |
This command was introduced. |
Usage Guidelines
Use the port-profile command to group configuration commands and apply them to several interfaces simultaneously. All interfaces in the range must be the same type. The maximum number of interfaces that can inherit a single port profile is 512.
The port-profile name must be globally unique across types and networks.
Each port profile can be applied only to a specific type of interface; the choices are as follows:
•![]() Ethernet
Ethernet
•![]() VLAN network interface
VLAN network interface
•![]() Port channel
Port channel

Note ![]() When you choose ethernet as the interface type, the port profile is in the default mode which is Layer 3. Enter the switchport command to change the port profile to Layer 2 mode.
When you choose ethernet as the interface type, the port profile is in the default mode which is Layer 3. Enter the switchport command to change the port profile to Layer 2 mode.
A subset of commands are available under the port-profile configuration mode, depending on which interface type you specify. Layer 3 and CTS commands are not supported by port profiles.
You can configure the following port-profile operations:
•![]() Create port profiles
Create port profiles
•![]() Delete port profiles
Delete port profiles
•![]() Add commands to and delete commands from port profiles
Add commands to and delete commands from port profiles
•![]() Inherit port profiles at interfaces
Inherit port profiles at interfaces
•![]() Enable and disable port profiles
Enable and disable port profiles
•![]() Inherit between port profiles
Inherit between port profiles
•![]() Configure maximum number of ports that a profile can inherit
Configure maximum number of ports that a profile can inherit
You inherit the port profile when you attach the port profile to an interface or range of interfaces. The maximum number of interfaces that can inherit a single profile is 512. When you attach, or inherit, a port profile to an interface or range of interfaces, the system applies all the commands in that port profile to the interfaces.
Additionally, you can have one port profile inherit another port profile, which allows the initial port profile to assume all of the commands of the second, inherited port profile that do not conflict with the initial port profile. Four levels of inheritance are supported except for the switchport private-vlan mapping and private-vlan mapping commands, which support only one level of inheritance. See the inherit port-profile command for information about inheriting an additional port profile and assigning port profiles to specified interfaces.
The system applies the commands inherited by the interface or range of interfaces according to the following guidelines:
•![]() Commands that you enter under the interface mode take precedence over the port profile’s commands if there is a conflict. However, the port profile retains that command in the port profile.
Commands that you enter under the interface mode take precedence over the port profile’s commands if there is a conflict. However, the port profile retains that command in the port profile.
•![]() The port profile’s commands take precedence over default commands on the interface, unless it is explicitly overridden by the default command.
The port profile’s commands take precedence over default commands on the interface, unless it is explicitly overridden by the default command.
•![]() When a range of interfaces inherits a second port profile, the commands of the initial port profile override those commands of the second port profile if there is a conflict.
When a range of interfaces inherits a second port profile, the commands of the initial port profile override those commands of the second port profile if there is a conflict.
•![]() After you inherit a port profile onto an interface or range of interfaces, you can override individual configuration values by entering the new value at the interface configuration level. If you then remove the individual configuration values at the interface configuration level, the interface again uses the values in the port profile again.
After you inherit a port profile onto an interface or range of interfaces, you can override individual configuration values by entering the new value at the interface configuration level. If you then remove the individual configuration values at the interface configuration level, the interface again uses the values in the port profile again.
•![]() There are no default configurations associated with a port profile.
There are no default configurations associated with a port profile.

Note ![]() You cannot use port profiles with Session Manager. See the Cisco Nexus 7000 Series NX-OS System Management Configuration Guide, Release 5.x, for information on Session Manager.
You cannot use port profiles with Session Manager. See the Cisco Nexus 7000 Series NX-OS System Management Configuration Guide, Release 5.x, for information on Session Manager.
If you delete a specific configuration for a specified range of interfaces using the interface configuration mode, that configuration is also deleted from the port profile for that range of interfaces only. For example, if you have a channel group inside a port profile and you are in the interface configuration mode and you delete that port channel, the specified port channel is also deleted from the port profile as well.
Just as in the device, you can enter a configuration for an object in port profiles without that object being applied to interfaces. For example, you can configure a VRF instance without it being applied to the system. If you then delete that VRF and its configurations from the port profile, the system is unaffected.
After you inherit a port profile on an interface or range of interfaces and you delete a specific configuration value, that port-profile configuration does not operate on the specified interfaces.
You must enable each specific port profile using the state-enabled command.
This command does not require a license.
Examples
This example shows how to configure, name a port profile, and enter the port-profile configuration mode:
switch(config)# port-profile type ethernet test
Related Commands
|
Command |
Description |
|---|---|
|
state-enable |
Enables a specified port profile. |
|
show port-profile |
Displays information about port profiles. |
rate-mode dedicated
To set the dedicated rate mode for the specified ports, use the rate-mode dedicated command.
rate-mode dedicated
no rate-mode
Syntax Description
This command has no arguments or keywords.
Defaults
Shared rate mode is the default.
Command Modes
Interface configuration mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
4.0 |
This command was introduced. |
Usage Guidelines
Use the rate-mode dedicated command to set the dedicated rate mode for the specified ports.
On a 32-port ,10-Gigabit Ethernet module, each set of four ports can handle 10 gigabits per second (Gb/s) of bandwidth. You can use the rate-mode parameter to dedicate that bandwidth to the first port in the set of four ports or share the bandwidth across all four ports.

Note ![]() When you dedicate the bandwidth to one port, you must first administratively shut down the ports in the group, change the rate mode to dedicated, and then bring the dedicated port administratively up.
When you dedicate the bandwidth to one port, you must first administratively shut down the ports in the group, change the rate mode to dedicated, and then bring the dedicated port administratively up.
Table 2 identifies the ports that are grouped together to share each 10 Gb/s of bandwidth and which port in the group can be dedicated to utilize the entire bandwidth.
Table 2 Dedicated and Shared Ports
|
Ports Groups that Can Share Bandwidth |
Ports that Can be Dedicated to Each 10-Gigabit Ethernet of Bandwidth |
|---|---|
|
1, 3, 5, 7 |
1 |
|
2, 4, 6, 8 |
2 |
|
9, 11, 13, 15 |
9 |
|
10, 12, 14, 16 |
10 |
|
17, 19, 21, 23 |
17 |
|
18, 20, 22, 24 |
18 |
|
25, 27, 29, 31 |
25 |
|
26, 28, 30, 32 |
26 |

Note ![]() All ports in each port group must be part of the same virtual device context (VDC). For more information on VDCs, see the Cisco Nexus 7000 Series NX-OS Virtual Device Context Configuration Guide, Release 5.x.
All ports in each port group must be part of the same virtual device context (VDC). For more information on VDCs, see the Cisco Nexus 7000 Series NX-OS Virtual Device Context Configuration Guide, Release 5.x.
When you enter the rate-mode dedicated command, the full bandwidth of 10 Gbps is dedicated to one port. When you dedicate the bandwidth, all subsequent commands for the port are for dedicated mode.
This command does not require a license.
Examples
This example shows how to configure the dedicated rate mode for Ethernet ports 4/17, 4/19, 4/21, and 4/23:
switch(config)# interface ethernet 4/17, ethernet 4/19, ethernet 4/21, ethernet 4/23
switch(config-if)# shutdown
switch(config-if)# interface ethernet 4/17
switch(config-if)# rate-mode dedicated
switch(config-if)# no shutdown
Related Commands
|
Command |
Description |
|
show interface |
Displays interface information, which includes the current rate mode dedicated. |
rate-mode shared
To set the shared rate mode for the specified ports, use the rate-mode shared command.
rate-mode shared
Syntax Description
This command has no arguments or keywords.
Defaults
Shared rate mode is the default.
Command Modes
Interface configuration mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
4.0 |
This command was introduced. |
Usage Guidelines
Use the rate-mode shared command to set the shared rate mode for the specified ports. This is the default rate mode for the module.
That is, use the rate-mode shared command to specify that each 10 Gbps of bandwidth on a 32-port 10 Gigabit Ethernet module is shared by ports in the same port group.
If the port group is in dedicated rate mode, you must first administratively shut down the ports in the group, change the rate mode to shared, and then bring the ports administratively up.
This command does not require a license.
Examples
This example shows how to configure the shared rate mode for Ethernet ports 4/17, 4/19, 4/21, and 4/23:
switch(config)# interface ethernet 4/17, ethernet 4/19, ethernet 4/21, ethernet 4/23
switch(config-if)# shutdown
switch(config-if)# interface ethernet 4/17
switch(config-if)# rate-mode shared
switch(config-if)# no shutdown
Related Commands
|
Command |
Description |
|
show interface |
Displays interface information, which includes the current rate mode shared. |
reload fex
To reload a Fabric Extender, use the reload fex command.
reload fex chassis-id all
Syntax Description
|
chassis-id |
Fabric Extender chassis ID. The range is from 100 to 199. |
|
all |
Reloads all FEX modules. |
Defaults
None
Command Modes
Global configuration mode
Command History
|
Release |
Modification |
|---|---|
|
5.1(1) |
This command was introduced. |
Usage Guidelines
This command does not require a license.
Examples
This example shows how to reload all FEX modules:
switch(config)# reload fex all
WARNING: This command will reboot all FEX modules
Do you want to continue? (y/n) [n] y
qadc3-ind30(config)# 2010 Sep 6 13:13:24 qadc3-ind30 %CALLHOME-2-EVENT: FEX_OFF
2010 Sep 6 13:13:25 qadc3-ind30 %FEX-2-NOHMS_ENV_FEX_OFFLINE: FEX-101 Off-line
(Serial Number JAF1407AANJ)
This example shows how to reload a specific FEX:
switch(config)# reload fex 101
WARNING: This command will reboot FEX module 101
Do you want to continue? (y/n) [n] y
qadc3-ind30(config)# 2010 Sep 6 13:11:36 qadc3-ind30 %CALLHOME-2-EVENT: FEX_OFF
2010 Sep 6 13:11:37 qadc3-ind30 %VNTAG_MGR-2-VNTAG_SEQ_ERROR: Failed to send me
ssage to FEX slot(33) Chassis (101) - Error Connection timed out. Ignore if FEX
2010 Sep 6 13:11:38 qadc3-ind30 %FEX-2-NOHMS_ENV_FEX_OFFLINE: FEX-101 Off-line
(Serial Number JAF1407AANJ)
Related Commands
|
Command |
Description |
|---|---|
|
show fex |
Displays all configured Fabric Extender chassis connected to the switch. |
reload restore
To configure a virtual port channel (vPC) device to assume that its peer is not functional and to bring up the vPC, use the reload restore command. To reset the vPC to the standard behavior, use the no form of this command.
reload restore [delay time-out]
no reload restore
Syntax Description
|
delay time-out |
(Optional) Sets the time-out for the vPC device. The range is from 240 to 3600. |
Defaults
Delay of 240 seconds
Command Modes
vPC domain configuration mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
5.2(1) |
This command was deprecated. |
|
5.0(2) |
This command was introduced. |
Usage Guidelines
This command does not require a license.
Examples
This example shows how to configure a vPC device to assume that its peer is not functional and to bring up the vPC:
switch(config)# vpc domain 5
switch(config-vpc-domain)# reload restore
Warning: Enables restoring of vPCs in a peer-detached state after reload, will wait for 240 seconds (by default) to determine if peer is un-reachable
Related Commands
|
Command |
Description |
|---|---|
|
vpc domain |
Creates a virtual port-channel (vPC) domain. |
role priority
To override the default selection of virtual port-channel (vPC) primary and secondary devices when you create a vPC domain, use the role priority command. To return to the default vPC system priority, use the no form of this command.
role priority priority
no role priority
Syntax Description
|
priority |
Role priority. The range is from 1 to 65636. |
Defaults
32667
Command Modes
vpc-domain command mode.
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
4.1(3) |
This command was introduced. |
Usage Guidelines
You must enable the vPC feature before you can create a vPC system priority
By default, the system elects a primary and secondary vPC peer device after you configure the vPC domain and both sides of the vPC peer link. However, you may want the system to elect a specific vPC peer device as the primary device for the vPC. Then, you would manually configure the role value for the vPC peer device that you want as primary to be lower than that of the other vPC peer device.
This command does not require a license.
Examples
This example shows how to create a vPC role priority:
switch(config)# vpc domain 5
switch(config-vpc-domain)# role priority 2000
Related Commands
|
Command |
Description |
|---|---|
|
show vpc role |
Displays the role for this device for the vPC domain as primary or secondary. |
serial
To assign a serial number to a Fabric Extender (FEX), use the serial command. To remove the serial number, use the no form of this command.
serial serial-string
no serial
Syntax Description
|
serial-string |
Serial number string for the Fabric Extender. The string is alphanumeric, case sensitive, and has a maximum length of 20 characters. |
Defaults
None
Command Modes
Fabric Extender configuration mode
Command History
|
Release |
Modification |
|---|---|
|
5.1(1) |
This command was introduced. |
Usage Guidelines
The serial number string that you define must match the serial number of the Fabric Extender. If you configure a serial number and then you use the fex associate command to associate the corresponding chassis ID to the switch, the association succeeds only if the Fabric Extender reports a matching serial number string.
Examples
This example shows how to specify a serial number for a Fabric Extender:
switch# configure terminal
switch(config-fex)# serial Rack16_FEX101
This example shows how to remove a serial number from a Fabric Extender:
switch# configure terminal
switch(config-fex)# no serial
Related Commands
|
Command |
Description |
|---|---|
|
fex |
Creates a Fabric Extender and enters fabric extender configuration mode. |
|
show fex |
Displays all configured Fabric Extender chassis connected to the switch. |
show bfd neighbors
To display information about Bidirectional Forwarding Detection (BFD) neighbors, use the show bfd neighbors command.
show bfd neighbors [application name | {dest-ip | src-ip} ipaddr interface int-if] [vrf vrf-name] [details]
Syntax Description
|
application name |
(Optional) Displays BFD information for the named protocol that BFD is enabled on. |
|
dest-ip ipaddr |
(Optional) Displays BFD information for the destination IP address. The IP address is in dotted decimal notation for IPv4 and in A:B::C:D format for IPv6. |
|
src-ip ipaddr |
(Optional) Displays BFD information for the source IP address. The IP address is in dotted decimal notation for IPv4 and in A:B::C:D format for IPv6. |
|
interface int-if |
(Optional) Displays BFD information for the interface. Use the ? keyword to display a list of supported interfaces. |
|
vrf vrf-name |
(Optional) Displays BFD information for the virtual routing and forwarding (VRF) instance. |
|
details |
(Optional) Displays detailed BFD information. |
Defaults
None
Command Modes
Any command mode
Command History
|
Release |
Modification |
|---|---|
|
5.0(2) |
This command was introduced. |
Usage Guidelines
Use the show bfd neighbors command to display information about BFD sessions. If you use the applications keyword, the application name is one of the following:
•![]() bfd_app
bfd_app
•![]() bgp
bgp
•![]() eigrp
eigrp
•![]() hsrp
hsrp
•![]() isis
isis
•![]() ospf
ospf
•![]() pim
pim
•![]() static
static
This command does not require a license.
Examples
This example shows how to display the output from the show bfd neighbors command:
switch# show bfd neighbors
OurAddr NeighAddr LD/RD RH/RS Holdown(mult) State Int
10.0.0.2 10.0.0.1 1124073474/1107296257 Up 582(3) Up Po10
This example shows how to display the output from the show bfd neighbors application details command for BFD:
switch# show bfd neighbors application bfd_app details
OurAddr NeighAddr LD/RD RH/RS Holdown(mult) State Int
1.1.1.2 1.1.1.1 1090519041/1107296257 Up 137(3) Up Eth4/37
Session state is Up and not using echo function
Local Diag: 0, Demand mode: 0, Poll bit: 0
MinTxInt: 50000 us, MinRxInt: 50000 us, Multiplier: 3
Received MinRxInt: 50000 us, Received Multiplier: 3
Holdown (hits): 150 ms (2), Hello (hits): 50 ms (1232223)
Rx Count: 1267540, Rx Interval (ms) min/max/avg: 0/1789/44 last: 12 ms ago
Tx Count: 1232223, Tx Interval (ms) min/max/avg: 41/41/41 last: 13 ms ago
Registered protocols: bfd_app
Uptime: 0day 15hour 5minute 8second 430ms
Last packet: Version: 1 - Diagnostic: 0
State bit: Up - Demand bit: 0
Poll bit: 0 - Final bit: 0
Multiplier: 3 - Length: 24
My Discr.: 1107296257 - Your Discr.: 1090519041
Min tx interval: 50000 - Min rx interval: 50000
Table 3 describes the significant fields shown in the display.
Table 3 show bfd neighbors Field Descriptions
|
Field |
Description |
|---|---|
|
OurAddr |
IP address of the interface for which the show bfd neighbors command was entered. |
|
NeighAddr |
IPv4 or IPv6 address of the BFD adjacency or neighbor. |
|
LD/RD |
Local discriminator and remote discriminator being used for the session. |
|
RH |
Remote Heard—Indicates that the remote BFD neighbor has been heard. |
|
Holdown(mult) |
Detect timer multiplier that is used for this session. |
|
State |
State of the interface—Up or Down. |
|
Int |
Interface type and slot/port. |
|
Session state is UP and not using echo function |
BFD is up and not running in echo mode. |
|
RX Count |
Number of BFD control packets that have been received from the BFD neighbor. |
|
TX Count |
Number of BFD control packets that have been sent by the BFD neighbor. |
|
TX Interval |
Interval, in milliseconds, between sent BFD packets. |
|
Registered protocols |
Routing protocols that have been registered with BFD. |
|
Last packet: Version: |
BFD version detected and run between the BFD neighbors. |
|
Diagnostic |
Diagnostic code specifying the local system’s reason for the last transition of the session from Up to some other state. State values are as follows: • • • • • • • • |
|
Demand bit |
Demand Mode bit. If set, the transmitting system wants to operate in demand mode. BFD has two modes—asynchronous and demand. The Cisco implementation of BFD supports only asynchronous mode. |
|
Poll bit |
Poll bit. If the Poll bit is set, the transmitting system is requesting verification of connectivity or of a parameter change. |
|
Final bit |
Final bit. If the Final bit is set, the transmitting system is responding to a received BFD control packet that had a Poll (P) bit set. |
|
Multiplier |
Detect time multiplier. The negotiated transmit interval, multiplied by the detect time multiplier, determines the detection time for the transmitting system in BFD asynchronous mode. The detect time multiplier is similar to the hello multiplier in Intermediate System-to-Intermediate System (IS-IS), which is used to determine the hold timer: (hello interval) * (hello multiplier) = hold timer. If a hello packet is not received within the hold-timer interval, a failure has occurred. Similarly, for BFD: (transmit interval) * (detect multiplier) = detect timer. If a BFD control packet is not received from the remote system within the detect-timer interval, a failure has occurred. |
|
Length |
Length of the BFD control packet, in bytes. |
|
My Discr. |
My Discriminator. Unique, nonzero discriminator value generated by the transmitting system used to demultiplex multiple BFD sessions between the same pair of systems. |
|
Your Discr. |
Your Discriminator. The discriminator received from the corresponding remote system. This field reflects the received value of My Discriminator or is zero if that value is unknown. |
|
Min tx interval |
Minimum transmission interval, in microseconds, that the local system wants to use when sending BFD control packets. |
|
Min rx interval |
Minimum receipt interval, in microseconds, between received BFD control packets that the system can support. |
|
Min Echo interval |
Minimum interval, in microseconds, between received BFD control packets that the system can support. If the value is zero, the transmitting system does not support the receipt of BFD echo packets. |
Related Commands
|
Command |
Description |
|---|---|
|
bfd echo |
Enables BFD echo mode. |
show environment fex
To display Fabric Extender (FEX) environment information, use the show environment fex command.
show environment fex {all chassis-id} [fan | power | temperature]
Syntax Description
|
all |
Displays information for all Fabric Extender chassis. |
|
chassis-id |
Fabric Extender chassis ID. The range is from 100 to 199. |
|
fan |
(Optional) Displays fan information. |
|
power |
(Optional) Displays power capacity and power distribution information. |
|
temperature |
(Optional) Displays temperature sensor information. |
Defaults
None
Command Modes
EXEC mode
Command History
|
Release |
Modification |
|
5.1(1) |
This command was introduced. |
Usage Guidelines
This command does not require a license.
Examples
This example shows how to display the environmental sensor status for a Fabric Extender:
switch# show environment fex 101
------------------------------------------------------
------------------------------------------------------
Chassis N2K-C2248-FAN -- ok
PS-1 N2200-PAC-400W -- ok
--------------------------------------------------------------------
Module Sensor MajorThresh MinorThres CurTemp Status
(Celsius) (Celsius) (Celsius)
--------------------------------------------------------------------
---------------------------------------------------------------------------
-----------------------------------------------------
PS Model Power Power Status
-----------------------------------------------------
1 N2200-PAC-400W 396.00 33.00 ok
Mod Model Power Power Power Power Status
Requested Requested Allocated Allocated
(Watts) (Amp) (Watts) (Amp)
--- ------------------- ------- ---------- --------- ---------- ----------
1 N2K-C2248TP-1GE 63.60 5.30 63.60 5.30 powered-up
Power Supply redundancy mode: redundant
Total Power Capacity 396.00 W
Power reserved for Supervisor(s) 63.60 W
Power currently used by Modules 0.00 W
Total Power Available 332.40 W
This example shows how to display fan information:
switch# show environment fex 101 fan
------------------------------------------------------
------------------------------------------------------
Chassis N2K-C2248-FAN -- ok
PS-1 N2200-PAC-400W -- ok
This example shows how to display power capacity and power distribution information:
switch# show environment fex 101 power
---------------------------------------------------------------------------
-----------------------------------------------------
PS Model Power Power Status
-----------------------------------------------------
Mod Model Power Power Power Power Status
Requested Requested Allocated Allocated
(Watts) (Amp) (Watts) (Amp)
--- ------------------- ------- ---------- --------- ---------- ----------
1 0.00 0.00 0.00 0.00 powered-up
Power Supply redundancy mode: redundant
Total Power Capacity 0.00 W
Power reserved for Supervisor(s) 0.00 W
Power currently used by Modules 0.00 W
Total Power Available 0.00 W
This example shows how to display temperature sensor information:
switch# show environment fex 101 temperature
--------------------------------------------------------------------
Module Sensor MajorThresh MinorThres CurTemp Status
(Celsius) (Celsius) (Celsius)
--------------------------------------------------------------------
Related Commands
|
Command |
Description |
|---|---|
|
show fex |
Displays all configured Fabric Extender chassis connected to the switch. |
show fex
To display information about a specific or all attached chassis, use the show fex command.
show fex [chassis-id [detail]]
Syntax Description
|
chassis-id |
(Optional) Fabric Extender chassis ID. The range is from 100 to 199. |
|
detail |
(Optional) Displays a detailed listing |
Defaults
None
Command Modes
EXEC mode
Command History
|
Release |
Modification |
|
5.1(1) |
This command was introduced. |
Usage Guidelines
This command does not require a license.
Examples
This example shows how to display information about all attached Fabric Extender chassis:
Number Description State Model Serial
------------------------------------------------------------------------
101 FEX0101 Online N2K-C2248TP-1GE JAF1407AANJ
102 FEX0102 Online N2K-C2248TP-1GE JAF1407AAQN
This example shows how to display information about a specific Fabric Extender chassis:
FEX: 101 Description: FEX0101 state: Online
FEX version: 5.1(1) [Switch version: 5.1(1)]
FEX Interim version: 5.1(0.159.6)
Switch Interim version: 5.1(0.236)
Extender Model: N2K-C2248TP-1GE, Extender Serial: JAF1407AANJ
pinning-mode: static Max-links: 1
Fabric port for control traffic: Po101
Po101 - Interface Up. State: Active
Eth9/1 - Interface Up. State: Active
Eth10/1 - Interface Up. State: Active
This example shows how to display the detailed information about all attached Fabric Extender chassis:
FEX: 101 Description: FEX0101 state: Online
FEX version: 5.1(1) [Switch version: 5.1(1)]
FEX Interim version: 5.1(0.159.6)
Switch Interim version: 5.1(0.236)
Extender Model: N2K-C2248TP-1GE, Extender Serial: JAF1407AANJ
Card Id: 99, Mac Addr: 00:05:9b:70:dd:42, Num Macs: 64
Module Sw Gen: 12594 [Switch Sw Gen: 21]
pinning-mode: static Max-links: 1
Fabric port for control traffic: Po101
Po101 - Interface Up. State: Active
Eth9/1 - Interface Up. State: Active
Eth10/1 - Interface Up. State: Active
Fex Port State Fabric Port Primary Fabric
Eth101/1/1 Down Po101 Po101
Eth101/1/2 Down Po101 Po101
Eth101/1/3 Down Po101 Po101
Eth101/1/4 Down Po101 Po101
Eth101/1/5 Down Po101 Po101
Eth101/1/6 Down Po101 Po101
Eth101/1/7 Down Po101 Po101
Eth101/1/8 Down Po101 Po101
Eth101/1/9 Down Po101 Po101
Eth101/1/10 Down Po101 Po101
Eth101/1/11 Down Po101 Po101
Related Commands
|
Command |
Description |
|---|---|
|
fex |
Creates a Fabric Extender and enters fabric extender configuration mode. |
show fex detail
To display detailed information about a specific Fabric Extender (FEX) or all attached chassis, use the show fex detail command.
show fex detail
Syntax Description
This command has no arguments or keywords.
Defaults
None
Command Modes
EXEC mode
Command History
|
Release |
Modification |
|
5.1(1) |
This command was introduced. |
Usage Guidelines
This command does not require a license.
Examples
This example shows how to display detailed information about a specific Fabric Extender or all attached chassis:
FEX: 101 Description: FEX0101 state: Online
FEX version: 5.1(1) [Switch version: 5.1(1)]
FEX Interim version: 5.1(0.159.6)
Switch Interim version: 5.1(0.236)
Extender Model: N2K-C2248TP-1GE, Extender Serial: JAF1407AANJ
Card Id: 99, Mac Addr: 00:05:9b:70:dd:42, Num Macs: 64
Module Sw Gen: 12594 [Switch Sw Gen: 21]
pinning-mode: static Max-links: 1
Fabric port for control traffic: Po101
Po101 - Interface Up. State: Active
Eth9/1 - Interface Up. State: Active
Eth10/1 - Interface Up. State: Active
Fex Port State Fabric Port Primary Fabric
Eth101/1/1 Down Po101 Po101
Eth101/1/2 Down Po101 Po101
Eth101/1/3 Down Po101 Po101
Eth101/1/4 Down Po101 Po101
Eth101/1/5 Down Po101 Po101
Eth101/1/6 Down Po101 Po101
Eth101/1/7 Down Po101 Po101
Eth101/1/8 Down Po101 Po101
Eth101/1/9 Down Po101 Po101
Eth101/1/10 Down Po101 Po101
Eth101/1/11 Down Po101 Po101
Related Commands
|
Command |
Description |
|---|---|
|
show fex |
Displays all configured Fabric Extender chassis connected to the switch. |
|
fex |
Creates a Fabric Extender and enters fabric extender configuration mode. |
show fex transceiver
To display information about the transceiver that connects a Fabric Extender (FEX) to the Cisco Nexus 7000 Series switch, use the show fex transceiver command.
show fex chassis-id transceiver [calibration | detail]
Syntax Description
|
chassis-id |
Fabric Extender chassis ID. The range is from 100 to 199. |
|
calibration |
(Optional) Displays detailed calibration information about the transceiver. |
|
detail |
(Optional) Displays detailed information about the transceiver. |
Defaults
None
Command Modes
EXEC mode
Command History
|
Release |
Modification |
|
5.1(1) |
This command was introduced. |
Usage Guidelines
This command does not require a license.
Examples
This example shows how to display information about the transceiver that connects a Fabric Extender to the Cisco Nexus 7000 Series switch:
switch# show fex 101 transceiver
sfp information is not available
Fabric Port: Ethernet10/1
part number is FTLX8570D3BCL-C1
serial number is FNS141629V3
nominal bitrate is 10300 MBits/sec
Link length supported for 50/125mm fiber is 0 m(s)
Link length supported for 62.5/125mm fiber is 0 m(s)
cisco extended id number is 4
part number is FTLX8570D3BCL-C1
serial number is FNS141700UE
nominal bitrate is 10300 MBits/sec
Link length supported for 50/125mm fiber is 0 m(s)
Link length supported for 62.5/125mm fiber is 0 m(s)
cisco extended id number is 4
sfp information is not available
Related Commandss
|
Command |
Description |
|---|---|
|
show fex |
Displays all configured Fabric Extender chassis connected to the switch. |
show fex version
To display the software version information about a Fabric Extender (FEX), use the show fex version command.
show fex chassis-id version
Syntax Description
|
chassis-ID |
Fabric Extender chassis ID. The range is from 100 to 199. |
Defaults
None
Command Modes
EXEC mode
Command History
|
Release |
Modification |
|---|---|
|
5.1(1) |
This command was introduced. |
Usage Guidelines
This command does not require a license.
Examples
This example shows how to display the software version of a Fabric Extender:
switch# show fex 101 version
System boot mode: primary
System image version: 5.1(1) [build 5.1(0.159.6)]
Module: Fabric Extender 48x1GE + 4x10G Module
Serial number: JAF1407AANJ
Kernel uptime is 1 day(s), 1 hour(s), 47 minutes(s), 4 second(s)
Last reset at Mon Sep 6 07:43:23 2010
Reason: Reset Requested by CLI command reload
Service: Reload requested by supervisor
Related Commands
|
Command |
Description |
|---|---|
|
show fex |
Displays all configured Fabric Extender chassis connected to the switch. |
show interface
To display the interface status and information, use the show interface command.
show interface
Syntax Description
This command has numerous keywords. For more details, see the Usage Guidelines section for this command.
Defaults
None
Command Modes
Any command mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
5.2(1) |
Changed the show interface output and added the field descriptions in Table 4. |
|
5.1(1) |
Changed the command output to show the port is suspended due to min-links. |
|
4.0 |
This command was introduced. |
Usage Guidelines
To display with keywords, see the following commands in this document:
•![]() show interface brief—Displays brief information of interface.
show interface brief—Displays brief information of interface.
•![]() show interface capabilities—Displays the information about the interfaces capabilities.
show interface capabilities—Displays the information about the interfaces capabilities.
•![]() show interface counters—Displays interface counters.
show interface counters—Displays interface counters.
•![]() show interface counters detailed—Displays only non zero counters.
show interface counters detailed—Displays only non zero counters.
•![]() show interface counters errors—Displays interface error counters.
show interface counters errors—Displays interface error counters.
•![]() show interface counters module—Displays interface counters on a specified module.
show interface counters module—Displays interface counters on a specified module.
•![]() show interface counters snmp—Displays SNMP MIB values.
show interface counters snmp—Displays SNMP MIB values.
•![]() show interface counters storm-control—Displays interface storm-control counters.
show interface counters storm-control—Displays interface storm-control counters.
•![]() show interface counters trunk—Displays interface trunk counters.
show interface counters trunk—Displays interface trunk counters.
•![]() show interface debounce—Displays interface debounce time information.
show interface debounce—Displays interface debounce time information.
•![]() show interface description—Displays a description about the interface.
show interface description—Displays a description about the interface.
•![]() show interface ethernet—Displays Ethernet interface information.
show interface ethernet—Displays Ethernet interface information.
•![]() show interface flowcontrol—Displays interface flow control information.
show interface flowcontrol—Displays interface flow control information.
•![]() show interface mgmt—Displays the management interface.
show interface mgmt—Displays the management interface.
•![]() show interface port-channel—Displays the port-channel interface.
show interface port-channel—Displays the port-channel interface.
•![]() show interface port-channel counters—Displays the interface port-channel counters.
show interface port-channel counters—Displays the interface port-channel counters.
•![]() show interface status—Displays the interface line status.
show interface status—Displays the interface line status.
•![]() show interface switchport—Displays interface switchport information.
show interface switchport—Displays interface switchport information.
•![]() show interface transceiver—Displays interface transceiver information.
show interface transceiver—Displays interface transceiver information.
•![]() show interface trunk—Displays interface trunk information.
show interface trunk—Displays interface trunk information.
This command does not require a license.
Examples
This example shows how to display interface status information. See Table 4 for a description of the command output.
switch# show interface e4/2
Ethernet4/2 is down (Link not connected)
Hardware: 10/100/1000 Ethernet, address: 0018.bad8.80d1 (bia 0024.f71c.739d)
MTU 1500 bytes, BW 1000000 Kbit, DLY 10 usec
reliability 153/255, txload 1/255, rxload 1/255
Auto-Negotiation is turned on
Input flow-control is off, output flow-control is off
Switchport monitor is off
Last link flapped 01:56:44
Last clearing of "show interface" counters 1d04h
30 seconds input rate 0 bits/sec, 0 packets/sec
30 seconds output rate 0 bits/sec, 0 packets/sec
Load-Interval #2: 5 minute (300 seconds)
input rate 0 bps, 0 pps; output rate 0 bps, 0 pps
ucast: 0 pkts, 0 bytes - mcast: 0 pkts, 0 bytes
ucast: 0 pkts, 0 bytes - mcast: 0 pkts, 0 bytes
4 unicast packets 2 multicast packets 0 broadcast packets
6 input packets 730 bytes
0 jumbo packets 0 storm suppression packets
0 runts 0 giants 0 CRC 0 no buffer
4 input error 0 short frame 0 overrun 0 underrun 0 ignored
0 watchdog 0 bad etype drop 0 bad proto drop 0 if down drop
0 input with dribble 0 input discard
0 unicast packets 4 multicast packets 0 broadcast packets
4 output packets 916 bytes
0 output error 0 collision 0 deferred 0 late collision
0 lost carrier 0 no carrier 0 babble 0 output discard
Table 4 describes the output of the show interface command.
Table 4 Field Descriptions for the show interface Command
|
Field |
Description |
|---|---|
|
Ethernet slot/port is {up | down | link-up} |
Indicates that the state of the port is as follows: up — The port is operationally up. down — The port is operationally down. link-up — The link is up, but the port is not yet fully operational for traffic to the data plane, although it is operational for control protocols. |
|
{ Dedicated | Shared | Dedicated(Shared) } Interface |
Indicates interfaces that belong to certain modules like the Cisco Nexus 7000 Series F1 Series modules and the F2 Series modules that can be shared between virtual device contexts (VDCs). The owner VDC is always an Ethernet VDC and the shared VDC is always a storage Fibre Channel over Ethernet (FCoE) VDC. The VDC that actually owns the interface is called the owner VDC and the one with which it is shared is called the shared VDC. Such an interface is listed as Dedicated(Shared) in the owner VDC and it is listed as a Shared interface in the shared VDC. Interfaces that are not shared between VDCs are listed as Dedicated interfaces. |
|
Hardware: speed1 | … | speedn Ethernet, address: mac_address (bia burned_in_mac_address) |
Indicates speed (in Mbps) that the linecard supports. In the preceding example, the linecard supports speeds of 10, 100, and 1000 Mbps. For all interfaces in Layer 3 (routed) mode, the mac_address is the address assigned to the VDC by the virtual device manager. The VDCs are assigned addressed in sequentially increasing order. The mac_address for a Layer 2 interface is the same as its burned_in_mac_address. The burned_in_mac_address is assigned by the manufacturer of the module and is static and different (possibly assigned in serial order) for each of its ports. |
|
MTU x bytes, |
Indicates the maximum transmission unit (MTU). For Layer 2 interfaces, the MTU can be set either to 1500 (the default) or to the system jumbo MTU which is 9216 bytes. For Layer 3 interfaces, the MTU can range from 576 to 9216 bytes, with1500 bytes being the default. MTU can only be set to even values. BW indicates the bandwidth of the interface. The bandwidth is determined by the following logic. The first one that holds true is applied. 1) The user configured bandwidth value. 2) Operational speed of the port (the port is up). 3) User configured speed value. 4) Maximum speed supported by the port (the default case). DLY indicates a value for the throughput-delay parameter and provides a value used by Layer 3 protocols; it does not change the actual throughput delay of an interface. The Layer 3 protocols can use this value to make operating decisions. For example, Enhanced Interior Gateway Routing Protocol (EIGRP) can use the delay setting to set a preference for one Ethernet link over another, if other parameters such as the link speed are equal. The delay value that you set is in the tens of microseconds. |
|
reliability 1-255/255, txload 1-255/255, rxload 1-255/255 |
Indicates that reliability is a function of how many of the incoming and the outgoing packets were erroneous. txload is a function of the outgoing rate of traffic in terms of the configured bandwidth. rxload is a function of the incoming rate of traffic in terms of the configured bandwidth of the port. |
|
Encapsulation ARPA |
Indicates that the encapsulation type is static as ARPA. |
|
{auto | half | full}-duplex, {auto | operational_speed}-speed |
These fields are printed only when the interface is administratively down and neither the speed or duplex parameters are configured on the interface.When the interface is brought administratively up, if there is a valid transceiver inserted in the interface, the speed of the transceiver is shown. Also the supported duplex mode is shown, and is either full or half. For modules that support autonegotiation, the speed and duplex parameters are shown as autonegotiated. These parameters go hand-in-hand, which means that for a certain speed to be configured, there must exist a specific duplex mode. For example: When speed auto is configured, the duplex mode must be auto too. Also for speeds greater than 1 Gbps, the duplex mode cannot be half. |
|
Beacon is turned {on | off } |
Indicates the state of beacon mode that allows you to identify a physical port by a flashing green LED. By default, this mode is disabled. To identify the physical port for an interface, you can activate the beacon parameter for the interface. |
|
Auto-Negotiation is turned {on | off } |
Indicates whether the two connected ports can autonegotiate parameters such as speed and duplex. Autonegotiation is on when multiple speeds are supported by the linecard and the current speed is auto. |
|
Input flow-control is {on | off } output flow-control is {on | off } |
Indicates whether flow control is allowed between two ports. The corresponding receive and send flow control parameters must be set for both ports as enabled or desired. When you set the parameter to enabled, the send or receive flow-control function is activated regardless of the setting of the other port. When you set the parameter to desired, the send or receive flow-control function is activated if you set the corresponding flow-control state of the other port to enabled or desired. If you set one of the flow control states to disabled, flow control is disabled for that transmission direction. |
|
Auto-mdix {on | off } |
Indicates whether automatic medium-dependent interface crossover (auto-mdix) feature is turned on or off. |
|
Switchport monitor is {on | off} |
Indicates whether the port has been configured to act as a SPAN destination port. |
|
EtherType is {0x8100 | 0x88A8 | 0x9100} |
Indicates the type of Ethernet frames that can be carried on this port. The following EtherTypes are possible: • • • |
|
Last link flapped {never | uv:wx:yz} |
Indicates the time elapsed in seconds when the link operationally went down or up. |
|
Last clearing of «show interface» counters {never | uv:wx:yz} |
Indicates the time elapsed since the execution of either the clear counters interface ex/y command or clear counters command. |
|
30 seconds input rate 30 seconds output rate |
Indicates that the average number of bits and packets transmitted per second in the last 30 seconds. The 30 seconds input and output rates should be used only as an approximation of traffic per second during a given 30-second period. These rates are exponentially weighted averages with a time constant of 30 seconds. A period of 4 time constants must pass before the average will be within 2 percent of the instantaneous rate of a uniform stream of traffic over that period. |
|
input packets |
Indicates the number of good and bad input packets. |
|
bytes |
Indicates the number of good and bad input bytes. |
|
storm suppression packets |
Indicates the number of storm suppression packets which is the total of unicast suppression packets, multicast suppression packets, and broadcast suppression packets. |
|
runt |
Indicates packets with a bad cyclic redundancy check (CRC) of fewer than 64 bytes. |
|
giant |
Indicates a packet length that is greater than the configured MTU on the interface. |
|
CRC |
Indicates the count of packets of any length that come in with a CRC error: • • • |
|
no buffer |
Indicates the number of received packets discarded because there was no buffer space in the main system. (Compare with ignored.) Broadcast storms on Ethernet networks and bursts of noise on serial lines are often responsible for no input buffer events. |
|
input error |
Indicates the sum of CRC (as defined previously in this table), short frames, giants, and wrong encapsulation frames. |
|
short frame |
Indicates a good packet length that is less than 64 bytes. |
|
underrun |
Indicates the number of transmit aborts (when the router cannot feed the transmitter fast enough). |
|
ignored |
Indicates the number of received packets that are ignored by the interface because the interface hardware ran low on internal buffers. These buffers are different than the system buffers mentioned previously in the buffer description. Broadcast storms and bursts of noise can cause the ignored count to be increased. |
|
watchdog |
Indicates the number of times the watchdog receive timer expired. The timer expires when it receives a packet with a length greater than 2048. |
|
bad etype drop |
Indicates the number of bad EtherType drops. |
|
bad proto drop |
Indicates the number of bad prototype drops. |
|
if down drop |
Indicates the number of interface down drops. |
|
input with dribble |
Indicates that a frame is slightly too long. This frame error counter is incremented for informational purposes; the frame is accepted. |
|
input discard |
Indicates the number of packets dropped in the input queue due to congestion. This number includes drops due to tail drop and weighted random early detection (WRED). |
|
Rx pause |
Indicates the number of received flow control frames.
Note |
|
unicast packets |
Indicates the number of good output unicast packets. |
|
multicast packets |
Indicates the number of good output multicast packets. |
|
broadcast packets |
Indicates the number of good output broadcast packets. |
|
output packets |
Indicates the total number of good output packets. |
|
jumbo packets |
Indicates the number of good packets that are greater than 1548 bytes. |
|
output error |
Indicates the sum total of excessive length packets, late collision packets, excessive collision packets, excessive deferral packets, crc_tx (output packets with bad CRC) packets, and fifo underrun packets. |
|
collision |
Indicates the number of messages transmitted due to an Ethernet collision. A packet that collides is counted only once in output packets. |
|
deferred |
Indicates that the chip had to defer while it was to transmit a frame because the carrier was asserted. |
|
late collision |
Indicates the number of late collisions. A late collision happens when a collision occurs after transmitting the preamble. The most common cause of late collisions is that Ethernet cable segments are too long for the speed at which they are being transmitting. |
|
lost carrier |
Indicates the number of times the carrier was lost during transmission. |
|
no carrier |
Indicates the number of times the carrier was not present during the transmission. |
|
babble |
Indicates that the transmit jabber timer expired. |
|
output discard |
Indicates the number of packets dropped in the output queue due to congestion. This number includes drops due to tail drop and weighted random early detection (WRED). |
|
Tx pause |
Indicates the number of output flow control frames. |
|
interface reset |
Indicates the number of link flaps. |
Related Commands
|
Command |
Description |
|
interface |
Enters the interface configuration mode and configures the types and identities of interfaces. |
show interface brief
To display brief information about the interface, use the show interface brief command.
show interface [ethernet slot/port | port-channel channel-number]
Syntax Description
|
ethernet |
(Optional) Specifies the slot and port of the Ethernet interface that you want to display. |
|
slot/port |
(Optional) Slot number and port number for the Ethernet interface. The range is from 1 to 253. |
|
port-channel |
(Optional) Specifies the port-channel number of the port-channel interface that you want to display. |
|
channel-number |
(Optional) Channel number. The range is from 1 to 4096. |
Defaults
None
Command Modes
Any command mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
4.0 |
This command was introduced. |
Usage Guidelines
If you do not specify an interface, this command displays information about all Layer 2 interfaces. Use the show interface brief command to display brief information about the interface.
This command does not require a license.
Examples
This example shows how to display brief information about the interface:
switch# show interface brief
--------------------------------------------------------------------------------
Port VRF Status IP Address Speed MTU
--------------------------------------------------------------------------------
mgmt0 -- up 172.28.231.193 1000 1500
--------------------------------------------------------------------------------
Ethernet VLAN Type Mode Status Reason Speed Port
--------------------------------------------------------------------------------
Eth2/1 -- eth routed down Administratively down auto(D) --
Eth2/2 -- eth routed down Administratively down auto(D) --
Eth2/3 -- eth routed down Administratively down auto(D) --
Eth2/4 1 eth pvlan down Administratively down auto(D) --
Eth2/5 -- eth routed down Administratively down auto(D) --
Eth2/6 1 eth access down Link not connected auto(D) --
Eth2/7 1 eth access up none 1000(D) --
Eth2/8 -- eth routed down Administratively down auto(D) --
Eth2/9 1 eth access up none 1000(D) --
Eth2/10 1 eth access down Link not connected auto(D) --
Eth2/11 -- eth routed down Administratively down auto(D) --
Eth2/12 -- eth routed down Administratively down auto(D) --
Eth2/13 -- eth routed down Administratively down auto(D) --
Eth2/14 -- eth routed down Administratively down auto(D) --
Eth2/15 -- eth routed down Administratively down auto(D) --
Eth2/16 -- eth routed down Administratively down auto(D) --
Eth2/17 -- eth routed down Administratively down auto(D) --
Eth2/18 -- eth routed down Administratively down auto(D) --
Eth2/19 -- eth routed down Administratively down auto(D) --
Eth2/20 -- eth routed down Administratively down auto(D) --
Eth2/21 -- eth routed down Administratively down auto(D) --
Eth2/22 -- eth routed down Administratively down auto(D) --
Eth2/23 -- eth routed down Administratively down auto(D) --
Eth2/24 -- eth routed down Administratively down auto(D) --
Eth2/25 -- eth routed down Administratively down auto(D) --
Eth2/26 -- eth routed down Administratively down auto(D) --
Eth2/27 -- eth routed down Administratively down auto(D) --
Eth2/28 -- eth routed down Administratively down auto(D) --
Eth2/29 -- eth routed down Administratively down auto(D) --
Eth2/30 -- eth routed down Administratively down auto(D) --
Eth2/31 -- eth routed down Administratively down auto(D) --
Eth2/32 -- eth routed down Administratively down auto(D) --
Eth2/33 -- eth routed down Administratively down auto(D) --
Eth2/34 -- eth routed down Administratively down auto(D) --
Eth2/35 -- eth routed down Administratively down auto(D) --
Eth2/36 -- eth routed down Administratively down auto(D) --
Eth2/37 -- eth routed down Administratively down auto(D) --
Eth2/38 -- eth routed down Administratively down auto(D) --
Eth2/39 -- eth routed down Administratively down auto(D) --
Eth2/40 -- eth routed down Administratively down auto(D) --
Eth2/41 -- eth routed down Administratively down auto(D) --
Eth2/42 -- eth routed down Administratively down auto(D) --
Eth2/43 -- eth routed down Administratively down auto(D) --
Eth2/44 -- eth routed down Administratively down auto(D) --
Eth2/45 -- eth routed down Administratively down auto(D) --
Eth2/46 -- eth routed down Administratively down auto(D) --
Eth2/47 -- eth routed down Administratively down auto(D) --
Eth2/48 -- eth routed down Administratively down auto(D) --
-------------------------------------------------------------------------------
Interface Secondary VLAN(Type) Status Reason
-------------------------------------------------------------------------------
Related Commands
|
Command |
Description |
|
interface |
Enters the interface configuration mode and configures the types and identities of interfaces. |
show interface capabilities
To display information about the interface capabilities, use the show interface capabilities command.
show interface [ethernet slot/port | port-channel channel-number] capabilities
Syntax Description
|
ethernet |
(Optional) Specifies the slot and port of the Ethernet interface that you want to display. |
|
slot/port |
(Optional) Slot number and port number for the Ethernet interface. The range is from 1 to 253. |
|
port-channel |
(Optional) Specifies the port-channel number of the port-channel interface that you want to display. |
|
channel-number |
(Optional) Channel number. The range is from 1 to 4096. |
Defaults
None
Command Modes
Any command mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
4.0 |
This command was introduced. |
Usage Guidelines
Use the show interface capabilities command to display information about the capabilities of the interface such as the speed, duplex, and rate mode. If you do not specify an interface, this command displays information about all Layer 2 interfaces.
This command does not require a license.
Examples
This example shows how to display the capabilities for a specific interface:
switch# show interface ethernet 2/7 capabilities
Trunk encap. type: 802.1Q
Broadcast suppression: percentage(0-100)
Flowcontrol: rx-(off/on/desired),tx-(off/on/desired)
QOS scheduling: rx-(2q4t),tx-(1p3q4t)
Related Commands
|
Command |
Description |
|---|---|
|
interface |
Enters the interface configuration mode and configures the types and identities of interfaces. |
show interface counters
To display in and out counters for all interfaces in the system, use the show interface counters command.
show interface [ethernet slot/port | port-channel channel-number] counters
Syntax Description
|
ethernet |
(Optional) Specifies the slot and port of the Ethernet interface that you want to display. |
|
slot/port |
(Optional) Slot number and port number for the Ethernet interface. The range is from 1 to 253. |
|
port-channel |
(Optional) Specifies the port-channel number of the port-channel interface that you want to display. |
|
channel-number |
(Optional) Channel number. The range is from 1 to 4096. |
Defaults
None
Command Modes
Any command mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
4.0 |
This command was introduced. |
Usage Guidelines
Use the show interface counters command to display in and out counters for all or a specific interface. If you do not specify an interface, this command displays information about all Layer 2 interfaces.
This command does not require a license.
Examples
This example shows how to display the in and out counters for all interfaces:
switch# show interface counters
--------------------------------------------------------------------------------
Port InOctets InUcastPkts InMcastPkts InBcastPkts
--------------------------------------------------------------------------------
mgmt0 137046816 46882 115497 267729
--------------------------------------------------------------------------------
Port OutOctets OutUcastPkts OutMcastPkts OutBcastPkts
--------------------------------------------------------------------------------
mgmt0 7555343 45951 1352 136
Related Commands
|
Command |
Description |
|---|---|
|
clear counters interface |
Clears the counters for the specified interfaces. |
show interface counters errors
To display interface error counters, use the show interface counters errors.
show interface [ethernet slot/port | port-channel channel-number] counter errors
Syntax Description
|
ethernet |
(Optional) Specifies the slot and port of the Ethernet interface that you want to display. |
|
slot/port |
(Optional) Slot number and port number for the Ethernet interface. The range is from 1 to 253. |
|
port-channel |
(Optional) Specifies the port-channel number of the port-channel interface that you want to display. |
|
channel-number |
(Optional) Channel number. The range is from 1 to 4096. |
Command Default
None
Command Modes
Any command mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
4.0 |
This command was introduced. |
Usage Guidelines
Use the show interface counters errors command to display interface error counters. If you do not specify an interface, this command displays information about all Layer 2 interfaces.
This command does not require a license.
Examples
This example shows how to display the interface error counters:
switch# show interface counters errors
--------------------------------------------------------------------------------
Port Align-Err FCS-Err Xmit-Err Rcv-Err UnderSize OutDiscards
--------------------------------------------------------------------------------
--------------------------------------------------------------------------------
Port Single-Col Multi-Col Late-Col Exces-Col Carri-Sen Runts
--------------------------------------------------------------------------------
--------------------------------------------------------------------------------
Port Giants SQETest-Err Deferred-Tx IntMacTx-Er IntMacRx-Er Symbol-Err
--------------------------------------------------------------------------------
Related Commands
|
Command |
Description |
|---|---|
|
clear counters interface |
Clears the counters for the specified interfaces. |
show interface counters storm-control
To display interface storm control discard counters, use the show interface counters storm-control.
show interface [ethernet slot/port | port-channel channel-number] counters storm-control
Syntax Description
|
ethernet |
(Optional) Specifies the slot and port of the Ethernet interface that you want to display. |
|
slot/port |
(Optional) Slot number and port number for the Ethernet interface. The range is from 1 to 253. |
|
port-channel |
(Optional) Specifies the port-channel number of the port-channel interface that you want to display. |
|
channel-number |
(Optional) Channel number. The range is from 1 to 4096. |
Defaults
None
Command Modes
Any command mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
4.0 |
This command was introduced. |
Usage Guidelines
Use the show interface counters storm-control command to display interface storm control discard counters. If you do not specify an interface, this command displays information about all Layer 2 interfaces.
This command does not require a license.
Examples
This example shows how to display the interface storm control discard counters:
switch# show interface counters storm-control
--------------------------------------------------------------------------------
Port UcastSupp % McastSupp % BcastSupp % TotalSuppDiscards
--------------------------------------------------------------------------------
Eth2/1 100.00 100.00 100.00 0
Eth2/2 100.00 100.00 100.00 0
Eth2/3 100.00 100.00 100.00 0
Eth2/4 100.00 100.00 100.00 0
Eth2/5 100.00 100.00 100.00 0
Eth2/6 100.00 100.00 100.00 0
Eth2/7 100.00 100.00 100.00 0
Eth2/8 100.00 100.00 100.00 0
Eth2/9 100.00 100.00 100.00 0
Eth2/10 100.00 100.00 100.00 0
Eth2/11 100.00 100.00 100.00 0
Eth2/12 100.00 100.00 100.00 0
Eth2/13 100.00 100.00 100.00 0
Eth2/14 100.00 100.00 100.00 0
Eth2/15 100.00 100.00 100.00 0
Eth2/16 100.00 100.00 100.00 0
Eth2/17 100.00 100.00 100.00 0
Eth2/18 100.00 100.00 100.00 0
Eth2/19 100.00 100.00 100.00 0
Eth2/20 100.00 100.00 100.00 0
Eth2/21 100.00 100.00 100.00 0
Eth2/22 100.00 100.00 100.00 0
Eth2/23 100.00 100.00 100.00 0
Eth2/24 100.00 100.00 100.00 0
Eth2/25 100.00 100.00 100.00 0
Eth2/26 100.00 100.00 100.00 0
Eth2/27 100.00 100.00 100.00 0
Eth2/28 100.00 100.00 100.00 0
Eth2/29 100.00 100.00 100.00 0
Eth2/30 100.00 100.00 100.00 0
Eth2/31 100.00 100.00 100.00 0
Eth2/32 100.00 100.00 100.00 0
Eth2/33 100.00 100.00 100.00 0
Eth2/34 100.00 100.00 100.00 0
Eth2/35 100.00 100.00 100.00 0
Eth2/36 100.00 100.00 100.00 0
Eth2/37 100.00 100.00 100.00 0
Eth2/38 100.00 100.00 100.00 0
Eth2/39 100.00 100.00 100.00 0
Eth2/40 100.00 100.00 100.00 0
Eth2/41 100.00 100.00 100.00 0
Eth2/42 100.00 100.00 100.00 0
Eth2/43 100.00 100.00 100.00 0
Eth2/44 100.00 100.00 100.00 0
Eth2/45 100.00 100.00 100.00 0
Eth2/46 100.00 100.00 100.00 0
Eth2/47 100.00 100.00 100.00 0
Eth2/48 100.00 100.00 100.00 0
Related Commands
|
Command |
Description |
|---|---|
|
clear counters interface |
Clears the counters for the specified interfaces. |
show interface counters trunk
To display the counters for Layer 2 switch port trunk interfaces, use the show interface counters trunk command.
show interface {ethernet slot/port} counters trunk
Syntax Description
|
ethernet |
(Optional) Specifies the slot and port of the Ethernet interface that you want to display. |
|
slot/port |
(Optional) Slot number and port number for the Ethernet interface. The range is from 1 to 253. |
Defaults
None
Command Modes
Any command mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
4.0 |
This command was introduced. |
Usage Guidelines
The device supports only IEEE 802.1Q encapsulation. This command also displays the counters for trunk port channels.
This command does not require a license.
Examples
This example shows how to display the counters for a trunk interface. This display shows the frames transmitted and received through the trunk interface, as well as the number of frames with the wrong trunk encapsulation:
switch# show interface ethernet 2/9 counters trunk
---------------------------------------------------------------------
Port TrunkFramesTx TrunkFramesRx WrongEncap
---------------------------------------------------------------------
Related Commands
|
Command |
Description |
|---|---|
|
clear counters interface |
Clears the counters for the specified interfaces. |
show interface debounce
To display the debounce time information about the interface, use the show interface debounce command.
show interface [ethernet slot/port | port-channel channel-number] debounce
Syntax Description
|
ethernet |
(Optional) Specifies the slot and port of the Ethernet interface that you want to display. |
|
slot/port |
(Optional) Slot number and port number for the Ethernet interface. The range is from 1 to 253. |
|
port-channel |
(Optional) Specifies the port-channel number of the port-channel interface that you want to display. |
|
channel-number |
(Optional) Channel number. The range is from 1 to 4096. |
Command Default
None
Command Modes
Any command mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
4.0 |
This command was introduced. |
Usage Guidelines
Use the show interface debounce command to display debounce time information about the interface. If you do not specify an interface, this command displays information about all Layer 2 interfaces.
This command does not require a license.
Examples
This example shows how to display debounce time information about the interface:
switch# show interface debounce
--------------------------------------------------------------------------------
Port Debounce time Value(ms)
--------------------------------------------------------------------------------
Related Commands
|
Command |
Description |
|---|---|
|
link debounce time |
Enables the debounce timer for Ethernet ports. |
show interface description
To display a description about the interface, use the show interface description command.
show interface description
Syntax Description
This command has no arguments or keywords.
Defaults
None
Command Modes
Any command mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
4.0 |
This command was introduced. |
Usage Guidelines
Use the show interface description command to display the interface description.
This command does not require a license.
Examples
This example shows how to display a description of the interface:
switch# show interface description
-------------------------------------------------------------------------------
-------------------------------------------------------------------------------
-------------------------------------------------------------------------------
Port Type Speed Description
-------------------------------------------------------------------------------
Eth2/10 eth 1000 ethernet slot 2 port 10
...<additional lines truncated>
Related Commands
|
Command |
Description |
|---|---|
|
description |
Provides textual interface descriptions for interfaces. |
show interface ethernet
To display information about the Ethernet interface, use the show interface ethernet command.
show interface ethernet slot/port [brief | cable-diagnostics-tdr | capabilities | counters {brief | detailed | errors | snmp | storm-control |trunk}| debounce | description | fcoe | flowcontrol | mac-address | status {err-disabled | err-vlans}| switchport | transceiver | trunk]
Syntax Description
|
slot/port |
Slot number and port number for the Ethernet interface. The range is from 1 to 253. |
|
brief |
(Optional) Displays brief information about the interface. |
|
cable-diagnostics-tdr |
(Optional) Displays information about the time domain reflectometer (TDR) test. |
|
capabilities |
(Optional) Displays interface capabilities. |
|
brief |
Displays information about the counters in brief. |
|
detailed |
Displays only nonzero counters. |
|
errors |
Displays error counters in the interface. |
|
snmp |
Displays SNMP MIB values. |
|
storm-control |
Displays storm-control counters. |
|
trunk |
Displays trunk counters. |
|
debounce |
(Optional) Displays the debounce time of the interface. |
|
description |
(Optional) Displays the interface description. |
|
fcoe |
(Optional) Displays the Fibre Channel over Ethernet (FCoE) information of the interface. |
|
flowcontrol |
(Optional) Displays the flow-control information. |
|
mac-address |
(Optional) Displays the MAC address. |
|
status |
(Optional) Displays the link status of the interface. |
|
err-disabled |
(Optional) Displays the error-disabled state of the interface. |
|
err-vlans |
(Optional) Displays VLAN errors in the interface. |
|
switchport |
(Optional) Displays switch-port information. |
|
transceiver |
(Optional) Displays the transceiver information. |
|
trunk |
(Optional) Displays interface trunk information. |
Defaults
None
Command Modes
Any command mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
5.1(1) |
Added the brief, cable-diagnostics-tdr, capabilities, debounce, description, detailed, errors, err-disabled, err-vlans, fcoe, flowcontrol, mac-address, snmp, storm-control, status, switchport, transceiver, and trunk keywords. |
|
4.0 |
This command was introduced. |
Usage Guidelines
Use the show interface ethernet command to display information about the Ethernet interface.
This command does not require a license.
Examples
This example shows how to display information about the Ethernet interface:
switch# show interface ethernet 2/5
Ethernet2/5 is down (Administratively down)
Hardware: 10/100/1000 Ethernet, address: 0018.bad8.3ffd (bia 0019.076c.4db0)
MTU 1500 bytes, BW 1000000 Kbit, DLY 10 usec,
reliability 255/255, txload 1/255, rxload 1/255
Auto-Negotiation is turned on
Input flow-control is off, output flow-control is off
Switchport monitor is off
Last clearing of "show interface" counters never
1 minute input rate 0 bits/sec, 0 packets/sec
1 minute output rate 0 bits/sec, 0 packets/sec
ucast: 0 pkts, 0 bytes - mcast: 0 pkts, 0 bytes
ucast: 0 pkts, 0 bytes - mcast: 0 pkts, 0 bytes
0 input packets 0 unicast packets 0 multicast packets
0 broadcast packets 0 jumbo packets 0 storm suppression packets
0 output packets 0 multicast packets
0 broadcast packets 0 jumbo packets
0 input error 0 short frame 0 watchdog
0 no buffer 0 runt 0 CRC 0 ecc
0 overrun 0 underrun 0 ignored 0 bad etype drop
0 bad proto drop 0 if down drop 0 input with dribble
0 output error 0 collision 0 deferred
0 late collision 0 lost carrier 0 no carrier
Related Commands
|
Command |
Description |
|---|---|
|
interface |
Enters the interface configuration mode and configures the types and identities of interfaces. |
show interface flowcontrol
To display the flow-control configuration for all or a specified interface, use the show interface flowcontrol command.
show interface flowcontrol [fex | port-channel channel-number] flowcontrol
Syntax Description
|
fex |
(Optional) Displays the Fabric Extender interface that you want to display. the range is from 100 t0 199 |
|
port-channel channel-number |
(Optional) Displays the port-channel number of the port-channel interface that you want to display. The range is from 1 to 4096. |
|
flowcontrol |
(Optional) Displays the interface flowcontrol information. |
Defaults
None
Command Modes
Any command mode
Supported User Roles
network-admin 2
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
4.0 |
This command was introduced. |
|
5.1 |
The fex keyword was added. |
Usage Guidelines
Use the show interface flowcontrol command to display information about the interface flow control. If you do not specify an interface, this command displays information about all Layer 2 interfaces.
This command does not require a license.
Examples
This example shows how to display the interface flow-control information:
switch# show interface flowcontrol
--------------------------------------------------------------------------------
Port Send FlowControl Receive FlowControl RxPause TxPause
--------------------------------------------------------------------------------
Eth2/1 off off off off 0 0
Eth2/2 off off off off 0 0
Eth2/3 off off off off 0 0
Eth2/4 off off off off 0 0
Eth2/5 off off off off 0 0
Eth2/6 off off off off 0 0
Eth2/7 off off off off 0 0
Eth2/8 off off off off 0 0
Eth2/9 off off off off 0 0
Eth2/10 off off off off 0 0
Eth2/11 off off off off 0 0
Eth2/12 off off off off 0 0
Eth2/13 off off off off 0 0
Eth2/14 off off off off 0 0
Eth2/15 off off off off 0 0
Eth2/16 off off off off 0 0
Eth2/17 off off off off 0 0
Eth2/18 off off off off 0 0
Eth2/19 off off off off 0 0
Eth2/20 off off off off 0 0
Eth2/21 off off off off 0 0
Eth2/22 off off off off 0 0
Eth2/23 off off off off 0 0
Eth2/24 off off off off 0 0
Eth2/25 off off off off 0 0
Eth2/26 off off off off 0 0
Eth2/27 off off off off 0 0
Eth2/28 off off off off 0 0
Eth2/29 off off off off 0 0
Eth2/30 off off off off 0 0
Eth2/31 off off off off 0 0
Eth2/32 off off off off 0 0
Eth2/33 off off off off 0 0
Eth2/34 off off off off 0 0
Eth2/35 off off off off 0 0
Eth2/36 off off off off 0 0
Eth2/37 off off off off 0 0
Eth2/38 off off off off 0 0
Eth2/39 off off off off 0 0
Eth2/40 off off off off 0 0
Eth2/41 off off off off 0 0
Eth2/42 off off off off 0 0
Eth2/43 off off off off 0 0
Eth2/44 off off off off 0 0
Eth2/45 off off off off 0 0
Eth2/46 off off off off 0 0
Eth2/47 off off off off 0 0
Eth2/48 off off off off 0 0
Related Commands
|
Command |
Description |
|---|---|
|
flowcontrol |
Enables or disables the ability of the Ethernet port to send and receive flow-control pause frames. |
show interface mgmt
To display the management interface information, use the show interface mgmt command.
show interface mgmt number [brief | counters [detailed | errors [snmp]] | description | status]
Syntax Description
|
number |
Information about the management interface number. The valid value is 0. |
|
brief |
(Optional) Displays brief information about the management interface. |
|
counters |
(Optional) Displays the counters for the management interface. |
|
detailed |
(Optional) Displays detailed information about the counters for the management interface. |
|
errors |
(Optional) Displays the errors for the management interface. |
|
snmp |
(Optional) Displays the SNMP errors for the management interface. |
|
description |
(Optional) Displays the description of the management interface. |
|
status |
(Optional) Displays the status of the management interface. |
Defaults
None
Command Modes
Any command mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
4.0 |
This command was introduced. |
Usage Guidelines
Use the show interface mgmt number command to display information about the management interface.
This command does not require a license.
Examples
This example shows how to display the management interface information:
switch# show interface mgmt0
Hardware: GigabitEthernet, address: 0019.076c.1a78 (bia 0019.076c.1a78)
Internet Address is 172.28.231.193/23
MTU 1500 bytes, BW 1000000 Kbit, DLY 10 usec,
reliability 255/255, txload 1/255, rxload 1/255
Auto-Negotiation is turned on
1 minute input rate 6446522 bits/sec, 78642 packets/sec
1 minute output rate 1965455 bits/sec, 20644 packets/sec
78681 input packets 15607 unicast packets 20178 multicast packets
42896 broadcast packets 24189392 bytes
20647 output packets 20377 unicast packets 246 multicast packets
24 broadcast packets 7370904 bytes
Related Commands
|
Command |
Description |
|---|---|
|
interface |
Enters the interface configuration mode and configures the types and identities of interfaces. |
show interface port-channel
To display descriptive information about port channels, use the show interface port-channel command.
show interface port-channel channel-number [brief | description | flowcontrol | status | switchport | trunk]
Syntax Description
|
channel-number |
Number of the port-channel group. The range is from 1 to 4096. |
|
brief |
(Optional) Specifies the summary information for specified port channels. |
|
description |
(Optional) Specifies the description of specified port channels. |
|
flowcontrol |
(Optional) Specifies information about the flow-control status control for specified port channels and the statistics on received and transmitted flow-control pause packets. |
|
status |
(Optional) Specifies information about the status for specified port channels. |
|
switchport |
(Optional) Specifies information for specified Layer 2 port channels including access and trunk modes. |
|
trunk |
(Optional) Specifies information for specified Layer 2 port channels on the trunk mode. |
Defaults
None
Command Modes
Any command mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
4.0 |
This command was introduced. |
|
4.2(1) |
Display of configured static MAC address for Layer 3 port channels was added. |
Usage Guidelines
To display more statistics for the specified port channels, use the show interface port-channel counters command.
This command does not require a license.
Examples
This example shows how to display information for a specific port channel. This example displays statistical information gathered on the port channel at 1-minute intervals:
switch(config)# show interface port-channel 50
port-channel50 is down (No operational members)
Hardware is Port-Channel, address is 0000.0000.0000 (bia 0000.0000.0000)
MTU 1500 bytes, BW 100000 Kbit, DLY 10 usec,
reliability 255/255, txload 1/255, rxload 1/255
Input flow-control is off, output flow-control is off
Switchport monitor is off
Members in this channel: Eth2/10
Last clearing of "show interface" counters 2d71.2uh
1 minute input rate 0 bytes/sec, 0 packets/sec
1 minute output rate 0 bytes/sec, 0 packets/sec
0 input packets 0 unicast packets 0 multicast packets
0 broadcast packets 0 jumbo packets 0 storm suppression packets
0 output packets 0 multicast packets
0 broadcast packets 0 jumbo packets
0 input error 0 short frame 0 watchdog
0 no buffer 0 runt 0 CRC 0 ecc
0 overrun 0 underrun 0 ignored 0 bad etype drop
0 bad proto drop 0 if down drop 0 input with dribble
0 output error 0 collision 0 deferred
0 late collision 0 lost carrier 0 no carrier
0 Rx pause 0 Tx pause 0 reset
This example shows how to display a brief description for a specific port channel, including the mode for the port channel, the status, speed, and protocol:
switch# show interface port-channel 5 brief
--------------------------------------------------------------------------------
Port-channel VLAN Type Mode Status Reason Speed Protocol
--------------------------------------------------------------------------------
eth access down No operational members auto(D) lacp
This example shows how to display the description for a specific port channel:
switch# show interface port-channel 5 description
-------------------------------------------------------------------------------
-------------------------------------------------------------------------------
This example shows how to display the flow-control information for a specific port channel:
switch# show interface port-channel 50 flowcontrol
------------------------------------------------------------------------------
Port Send FlowControl Receive FlowControl RxPause TxPause
------------------------------------------------------------------------------
The oper display for the show interface port-channel flowcontrol command shows as on if one member of the port channel is set to on for flow control and all the of the members and the entire port channel is set to on for flow control.
This example shows how to display the status of a specific port channel:
switch# show interface port-channel 5 status
--------------------------------------------------------------------------------
Port Name Status Vlan Duplex Speed Type
--------------------------------------------------------------------------------
This example shows how to display information for a specific Layer 2 port channel:
switch# show interface port-channel 50 switchport
Switchport Monitor: Not enabled
Access Mode VLAN: 1 (default)
Trunking Native Mode VLAN: 1 (default)
Trunking VLANs Enabled: 1-3967,4048-4093
Administrative private-vlan primary host-association: none
Administrative private-vlan secondary host-association: none
Administrative private-vlan primary mapping: none
Administrative private-vlan secondary mapping: none
Administrative private-vlan trunk native VLAN: none
Administrative private-vlan trunk encapsulation: dot1q
Administrative private-vlan trunk normal VLANs: none
Administrative private-vlan trunk private VLANs: none
Operational private-vlan: none
This command displays information for Layer 2 port channels in both the access and trunk modes.
When you use this command for a routed port channel, the device returns the following message:
This example shows how to display information for a specific Layer 2 port channel that is in trunk mode:
switch# show interface port-channel 5 trunk
switch# show interface port-channel 50 trunk
port-channel50 is down (No operational members)
Hardware is Ethernet, address is 0000.0000.0000
MTU 1500 bytes, BW 100000 Kbit, DLY 10 usec
Receive flow-control is off, Send flow-control is off
Members in this channel: Eth2/10
Allowed Vlans: 1-3967,4048-4093
This command displays information for only Layer 2 port channels in the trunk modes; you cannot display information about Layer 2 port channels in the access mode with this command.
Related Commands
|
Command |
Description |
|---|---|
|
show interface port-channel counters |
Displays the statistics for channel groups. |
|
show port-channel summary |
Displays summary information for all channel groups. |
show interface port-channel counters
To display information about port-channel statistics, use the show interface port-channel counters command.
show interface port-channel channel-number counters [brief | detailed [all | snmp] | errors [snmp] | trunk]
Syntax Description
|
channel-number |
Number of the port-channel group. The range is from1 to 4096. |
|
brief |
(Optional) Specifies the rate MB/s and total frames for specified port channels. |
|
detailed |
(Optional) Specifies the nonzero counters for specified port channels. |
|
all |
(Optional) Specifies the counters for specified port channels. |
|
snmp |
(Optional) Specifies the SNMP MIB values for specified port channels. |
|
errors |
(Optional) Specifies the interface error counters for specified port channels. |
|
trunk |
(Optional) Specifies the interface trunk counters for specified port channels. |
Defaults
None
Command Modes
Any command mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
4.0 |
This command was introduced. |
Usage Guidelines
This command displays statistics for all port channels including the Link Aggregation Control Protocol (LACP)-enabled port channels and those port channels that are not associated with an aggregation protocol.
This command does not require a license.
Examples
This example shows how to display the counters for a specific port channel. This example display shows the transmitted and received unicast and multicast packets:
switch# show interface port-channel 2 counters
Port InOctets InUcastPkts InMcastPkts InBcastPkts
Port OutOctets OutUcastPkts OutMcastPkts OutBcastPkts
This example shows how to display the brief counters for a specific port channel. This display shows the transmitted and received rate and total frames:
switch# show interface port-channel 20 counters brief
-------------------------------------------------------------------------------
Interface Input (rate is 1 min avg) Output (rate is 1 min avg)
------------------------- -----------------------------
-------------------------------------------------------------------------------
This example shows how to display all the detailed counters for a specific port channel:
switch# show interface port-channel 20 counters detailed all
10. rxTxHCPkts64Octets = 0
11. rxTxHCpkts65to127Octets = 0
12. rxTxHCpkts128to255Octets = 0
13. rxTxHCpkts256to511Octets = 0
14. rxTxHCpkts512to1023Octets = 0
15. rxTxHCpkts1024to1518Octets = 0
16. rxTxHCpkts1519to1548Octets = 0
14. rxHCPkts65to127Octets = 0
15. rxHCPkts128to255Octets = 0
16. rxHCPkts256to511Octets = 0
17. rxHCpkts512to1023Octets = 0
18. rxHCpkts1024to1518Octets = 0
19. rxHCpkts1519to1548Octets = 0
21. txHCPkts65to127Octets = 0
22. txHCPkts128to255Octets = 0
23. txHCPkts256to511Octets = 0
24. txHCpkts512to1023Octets = 0
25. txHCpkts1024to1518Octets = 0
26. txHCpkts1519to1548Octets = 0
74. InLayer3RoutedOctets = 0
76. OutLayer3RoutedOctets = 0
78. OutLayer3UnicastOctets = 0
79. OutLayer3Multicast = 0
80. OutLayer3MulticastOctets = 0
82. InLayer3UnicastOctets = 0
83. InLayer3Multicast = 0
84. InLayer3MulticastOctets = 0
85. InLayer3AverageOctets = 0
86. InLayer3AveragePackets = 0
87. OutLayer3AverageOctets = 0
88. OutLayer3AveragePackets = 0
This example shows how to display the error counters for a specific port channel:
switch# show interface port-channel 5 counters errors
--------------------------------------------------------------------------------
Port Align-Err FCS-Err Xmit-Err Rcv-Err UnderSize OutDiscards
--------------------------------------------------------------------------------
--------------------------------------------------------------------------------
Port Single-Col Multi-Col Late-Col Exces-Col Carri-Sen Runts
--------------------------------------------------------------------------------
--------------------------------------------------------------------------------
Port Giants SQETest-Err Deferred-Tx IntMacTx-Er IntMacRx-Er Symbol-Err
--------------------------------------------------------------------------------
This example shows how to display information about the trunk interfaces for a specific port channel:
switch# show interface port-channel 5 counters trunk
-------------------------------------------------------------------------------
Port TrunkFramesTx TrunkFramesRx WrongEncap
-------------------------------------------------------------------------------
Related Commands
|
Command |
Description |
|---|---|
|
clear counters |
Clears the statistics for all interfaces that belong to a specific channel group. |
show interface transceiver fex-fabric
To display Fabric Extender (FEX) interface transceiver information, use the show interface transceiver fex-fabric command.
show interface transceiver fex-fabric {calibrations | details}
Syntax Description
|
calibrations |
Displays interface transceiver calibration information. |
|
details |
Displays interface transceiver detail information. |
Defaults
None
Command Modes
EXEC mode
Command History
|
Release |
Modification |
|
5.1(1) |
This command was introduced. |
Usage Guidelines
This command does not require a license.
Examples
This example shows how to display interface transceiver calibration information:
switch# show interface transceiver fex-fabric calibrations
part number is FTLX8570D3BCL-C1
serial number is FNS141700UE
nominal bitrate is 10300 MBits/sec
Link length supported for 50/125mm fiber is 0 m(s)
Link length supported for 62.5/125mm fiber is 0 m(s)
cisco extended id number is 4
Calibration info not available
part number is FTLX8570D3BCL-C1
serial number is FNS141700V2
nominal bitrate is 10300 MBits/sec
Link length supported for 50/125mm fiber is 0 m(s)
Link length supported for 62.5/125mm fiber is 0 m(s)
This example shows how to display interface transceiver detail information:
switch# show interface transceiver fex-fabric details
part number is FTLX8570D3BCL-C1
serial number is FNS141700UE
nominal bitrate is 10300 MBits/sec
Link length supported for 50/125mm fiber is 0 m(s)
Link length supported for 62.5/125mm fiber is 0 m(s)
cisco extended id number is 4
Calibration info not available
part number is FTLX8570D3BCL-C1
serial number is FNS141700V2
nominal bitrate is 10300 MBits/sec
Link length supported for 50/125mm fiber is 0 m(s)
Link length supported for 62.5/125mm fiber is 0 m(s)
Related Commands
|
Command |
Description |
|---|---|
|
show fex |
Displays all configured Fabric Extender chassis connected to the switch. |
show interface status
To display the interface line status, use the show interface status command.
show interface status [down | err-disabled | err-vlans | inactive | module number | up]
Syntax Description
|
down |
(Optional) Displays the interface down state. |
|
err-disabled |
(Optional) Displays the interface error-disabled state. |
|
err-vlans |
(Optional) Displays the VLANs with errors. |
|
inactive |
(Optional) Displays the interface inactive state. |
|
module number |
(Optional) Displays the module number. The range is from 1 to 18. |
|
up |
(Optional) Displays the interface up state. |
Defaults
None
Command Modes
Any command mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
4.0 |
This command was introduced. |
|
4.1(2) |
The err-vlans parameter was added. |
Usage Guidelines
Use the show interface status to display the interface line status.
This command does not require a license.
Examples
This example shows how to display the interface status for a specific module:
switch# show interface status module 2
--------------------------------------------------------------------------------
Port Name Status Vlan Duplex Speed Type
--------------------------------------------------------------------------------
Eth2/1 -- down routed auto auto 1000BaseT
Eth2/2 -- down routed auto auto 1000BaseT
Eth2/3 -- down routed auto auto 1000BaseT
Eth2/4 -- down 1 auto auto 1000BaseT
Eth2/5 -- down routed auto auto 1000BaseT
Eth2/6 -- down 1 auto auto 1000BaseT
Eth2/7 server2 up 1 full 1000 1000BaseT
Eth2/8 -- down routed auto auto 1000BaseT
Eth2/9 -- up 1 full 1000 1000BaseT
Eth2/10 ethernet slot 2 po down 1 auto auto 1000BaseT
Eth2/11 -- down routed auto auto 1000BaseT
Eth2/12 -- down routed auto auto 1000BaseT
Eth2/13 -- down routed auto auto 1000BaseT
Eth2/14 -- down routed auto auto 1000BaseT
Eth2/15 -- down routed auto auto 1000BaseT
Eth2/16 -- down routed auto auto 1000BaseT
Eth2/17 -- down routed auto auto 1000BaseT
Eth2/18 -- down routed auto auto 1000BaseT
Eth2/19 -- down routed auto auto 1000BaseT
Eth2/20 -- down routed auto auto 1000BaseT
Eth2/21 -- down routed auto auto 1000BaseT
Eth2/22 -- down routed auto auto 1000BaseT
Eth2/23 -- down routed auto auto 1000BaseT
Eth2/24 -- down routed auto auto 1000BaseT
Eth2/25 -- down routed auto auto 1000BaseT
Eth2/26 -- down routed auto auto 1000BaseT
Eth2/27 -- down routed auto auto 1000BaseT
Eth2/28 -- down routed auto auto 1000BaseT
Eth2/29 -- down routed auto auto 1000BaseT
Eth2/30 -- down routed auto auto 1000BaseT
Eth2/31 -- down routed auto auto 1000BaseT
Eth2/32 -- down routed auto auto 1000BaseT
Eth2/33 -- down routed auto auto 1000BaseT
Eth2/34 -- down routed auto auto 1000BaseT
Eth2/35 -- down routed auto auto 1000BaseT
Eth2/36 -- down routed auto auto 1000BaseT
Eth2/37 -- down routed auto auto 1000BaseT
Eth2/38 -- down routed auto auto 1000BaseT
Eth2/39 -- down routed auto auto 1000BaseT
Eth2/40 -- down routed auto auto 1000BaseT
Eth2/41 -- down routed auto auto 1000BaseT
Eth2/42 -- down routed auto auto 1000BaseT
Eth2/43 -- down routed auto auto 1000BaseT
Eth2/44 -- down routed auto auto 1000BaseT
Eth2/45 -- down routed auto auto 1000BaseT
Eth2/46 -- down routed auto auto 1000BaseT
Eth2/47 -- down routed auto auto 1000BaseT
Eth2/48 -- down routed auto auto 1000BaseT
Related Commands
|
Command |
Description |
|---|---|
|
interface |
Enters the interface configuration mode and configures the types and identities of interfaces. |
show interface switchport
To display information about all the switch-port interfaces, use the show interface switchport command.
show interface [ethernet type/slot | port-channel channel-number] switchport
Syntax Description
|
ethernet type/slot |
(Optional) Type and number of the interface that you want to display. |
|
port-channel channel-number |
(Optional) Specifies the port-channel number of the port-channel interface that you want to display. The range is from 1to 4096. |
Defaults
None
Command Modes
Any command mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
4.0 |
This command was introduced. |
|
4.2(1) |
Information about private VLAN promiscuous trunk ports was added. |
Usage Guidelines
If you do not specify an interface, this command displays information about all Layer 2 interfaces, including access, trunk, port-channel interfaces, and all private VLAN ports.
Use the show interface counters command to display statistics for the specified Layer 2 interface.
This command does not require a license.
Examples
This example shows how to display information for all Layer 2 interfaces:
switch# show interface switchport
Switchport Monitor: Not enabled
Access Mode VLAN: 1 (default)
Trunking Native Mode VLAN: 1 (default)
Trunking VLANs Enabled: 1-3967,4048-4093
Administrative private-vlan primary host-association: none
Administrative private-vlan secondary host-association: none
Administrative private-vlan primary mapping: none
Administrative private-vlan secondary mapping: none
Administrative private-vlan trunk native VLAN: none
Administrative private-vlan trunk encapsulation: dot1q
Administrative private-vlan trunk normal VLANs: none
Administrative private-vlan trunk private VLANs: none
Operational private-vlan: none
Switchport Monitor: Not enabled
Access Mode VLAN: 1 (default)
Trunking Native Mode VLAN: 1 (default)
Trunking VLANs Enabled: 1-3967,4048-4093
Administrative private-vlan primary host-association: none
Administrative private-vlan secondary host-association: none
Administrative private-vlan primary mapping: none
Administrative private-vlan secondary mapping: none
Administrative private-vlan trunk native VLAN: none
Administrative private-vlan trunk encapsulation: dot1q
Administrative private-vlan trunk normal VLANs: none
Administrative private-vlan trunk private VLANs: none
Operational private-vlan: none
Switchport Monitor: Not enabled
Access Mode VLAN: 1 (default)
Trunking Native Mode VLAN: 1 (default)
Trunking VLANs Enabled: 1-3967,4048-4093
Administrative private-vlan primary host-association: none
Administrative private-vlan secondary host-association: none
Administrative private-vlan primary mapping: none
Administrative private-vlan secondary mapping: none
Administrative private-vlan trunk native VLAN: none
Administrative private-vlan trunk encapsulation: dot1q
Administrative private-vlan trunk normal VLANs: none
Administrative private-vlan trunk private VLANs: none
Operational private-vlan: none
Beginning with Cisco NX-OS Release 4.2(1), you can display information on private VLAN promiscuous trunk ports on Cisco Nexus 7000 Series devices. This example shows how to display information for those interfaces:
switch# show interface switchport
Administrative Mode: private-vlan trunk promiscuous
Administrative Trunking Encapsulation: negotiate
Negotiation of Trunking: on
Access Mode VLAN: 1 (default)
Trunking Native Mode VLAN: 1 (default)
Administrative Native VLAN tagging: enabled
Administrative private-vlan host-association: none
Administrative private-vlan mapping: none
Administrative private-vlan secondary mapping: none
Administrative private-vlan trunk Native VLAN tagging: enabled
Administrative private-vlan trunk encapsulation: dot1q
Administrative private-vlan trunk normal VLANs: 1, 4, 3000-4000
Administrative private-vlan trunk private VLAN mappings:
2 (VLAN0002) 3 (VLAN0003) 4 (VLAN0004) 5 (VLAN00005)
10 (VLAN0010) 20 (CLAN0020) 30 (VLAN0030) 40 (Inactive)
Operational private-vlan: none
Related Commands
|
Command |
Description |
|---|---|
|
switchport mode |
Sets the specified interfaces as either Layer 2 access or trunk interfaces. |
show interface transceiver
To display information about all the transceiver interfaces, use the show interface transceiver command.
show interface transceiver [calibrations | details]
Syntax Description
|
calibrations |
(Optional) Displays calibration information for transceivers. |
|
detail |
(Optional) Displays detailed information for transceivers. |
Defaults
None
Command Modes
Any command mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
4.1(2) |
This command was introduced. |
Usage Guidelines
This command does not require a license.
Examples
This example shows how to display calibration information for transceiver interfaces:
switch(config)# show interface transceiver calibrations
part number is SPP5101LR-C1
serial number is ECL121601PB
nominal bitrate is 10300 MBits/sec
Link length supported for 9/125um fiber is 10 km(s)
cisco extended id number is 4
SFP External Calibrations Information
----------------------------------------------------------------------
Slope Offset Rx4/Rx3/Rx2/Rx1/Rx0
----------------------------------------------------------------------
Rx Power 0.0000/0.0000/0.0000/0.0000/0.0000
This example shows how to display detailed information for transceiver interfaces:
switch(config)# show interface transceiver detailed
part number is SPP5101SR-C1
serial number is ECL1120017J
nominal bitrate is 10300 MBits/sec
Link length supported for 50/125um fiber is 82 m(s)
Link length supported for 62.5/125um fiber is 26 m(s)
cisco extended id number is 4
SFP Detail Diagnostics Information (external calibration)
----------------------------------------------------------------------------
----------------------------------------------------------------------------
Temperature 25.54 C 75.00 C -5.00 C 70.00 C 0.00 C
Voltage 3.22 V 3.63 V 2.97 V 3.46 V 3.13 V
Current 4.49 mA 10.00 mA 0.00 mA 9.00 mA 0.00 mA
Tx Power -3.50 dBm 2.99 dBm -11.30 dBm -1.00 dBm -7.30 dBm
Rx Power -2.92 dBm 2.99 dBm -13.97 dBm -1.00 dBm -9.91 dBm
----------------------------------------------------------------------------
Related Commands
|
Command |
Description |
|---|---|
|
show interface |
Displays information about the specified interfaces. |
show interface trunk
To display information about all the trunk interfaces, use the show interface trunk command.
show interface [ethernet slot/port | port-channel channel-number] trunk [module number | vlan vlan-id]
Syntax Description
|
ethernet slot/port |
(Optional) Type and number of the interface that you want to display. |
|
port-channel channel-number |
(Optional) Specifies the port-channel number of the port-channel interface that you want to display. |
|
module number |
(Optional) Specifies the module number. The range is from 1 to 18. |
|
vlan vlan-id |
(Optional) Specifies the VLAN number. The range is from 1 to 2499 to and from 2628 to 4093. |
Defaults
None
Command Modes
Any command mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
4.0 |
This command was introduced. |
Usage Guidelines
If you do not specify an interface, a module number, or a VLAN number, the system displays information for all trunk interfaces.
This command displays information about all Layer 2 trunk interfaces and trunk port-channel interfaces.
Use the show interface counters command to display statistics for the specified Layer 2 interface.
This command does not require a license.
Examples
This example shows how to display information for all Layer 2 trunk interfaces:
switch(config)# show interface trunk
-----------------------------------------------------------------------------
-----------------------------------------------------------------------------
-----------------------------------------------------------------------------
Port Vlans Allowed on Trunk
-----------------------------------------------------------------------------
-----------------------------------------------------------------------------
-----------------------------------------------------------------------------
Related Commands
|
Command |
Description |
|---|---|
|
switchport mode trunk |
Sets the specified interfaces as Layer 2 trunk interfaces. |
show interface tunnel
To display information about the tunnel interfaces, use the show interface tunnel command.
show interface tunnel number
Syntax Description
|
number |
Number of the tunnel interface that you want to display information for. The range is from 0 to 65503. |
Defaults
None
Command Modes
Any command mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
4.1(2) |
This command was introduced. |
|
4.2(1) |
Display of configured static MAC address was added. |
Usage Guidelines
This command does not require a license.
Examples
This example shows how to display information about tunnel interfaces:
switch(config)# show interface tunnel 5
Tunnel5 is down (Administratively down)
MTU 1476 bytes, BW 9 Kbit
Transport protocol is in VRF "default"
Tunnel protocol/transport GRE/IP
Last clearing of "show interface" counters never
0 packets output, 1 minute output rate 0 packets/sec
0 packets input, 1 minute input rate 0 packets/sec
Related Commands
|
Command |
Description |
|---|---|
|
show interface |
Displays information about the specified interfaces. |
show inventory fex
To display the system inventory of a Fabric Extender (FEX), such as the name, description, and volume ID, use the show inventory fex command
show inventory fex chassis-id
Syntax Description
|
chassis-id |
Fabric Extender chassis ID. The range is from 100 to 199. |
Defaults
None
Command Modes
EXEC mode
Command History
|
Release |
Modification |
|
5.1(1) |
This command was introduced. |
Usage Guidelines
This command does not require a license.
Examples
This example shows how to display the system inventory of a specific Fabric Extender chassis:
switch# show inventory fex 101
PID: N2K-C2248TP-1GE , VID: V00 , SN: JAF1407AANJ
NAME: "FEX 101 Module 1", DESCR: "Fabric Extender Module: 32x10G BaseT, 8x10G B
PID: N2K-C2248TP-1GE , VID: V00 , SN: SSI14061500
NAME: "FEX 101 Fan 1", DESCR: "Fabric Extender Fan module"
PID: N2K-C2332-FAN , VID: N/A , SN: N/A
NAME: "FEX 101 Power Supply 1", DESCR: "Fabric Extender AC power supply"
PID: N2200-PAC-400W , VID: V00 , SN: LIT14030HK9
Related Commands
|
Command |
Description |
|---|---|
|
show fex |
Displays all configured Fabric Extender chassis connected to the switch. |
show ip dhcp snooping statistics
To display statistics related to the Dynamic Host Configuration Protocol (DHCP), use the show ip dhcp snooping statistics command.
show ip dhcp snooping statistics
Syntax Description
This command has no arguments or keywords.
Defaults
None
Command Modes
EXEC mode
Command History
|
Release |
Modification |
|
5.1(1) |
Added the command output (added two counters) |
|
4.0 |
This command was introduced. |
Usage Guidelines
To enable this feature, use the feature dhcp command.
Examples
This example shows how to display statistics related to DHCP:
switch# show ip dhcp snooping statistics
Packets received through cfsoe 0
Packets forwarded on cfsoe 0
Packets dropped from untrusted ports 0
Packets dropped due to MAC address check failure 0
Packets dropped due to Option 82 insertion failure 0
Packets dropped due to o/p intf unknown 0
Packets dropped which were unknown 0
Packets dropped due to dhcp relay not enabled 0
Packets dropped due to no binding entry 0
Packets dropped due to interface error/no interface 0
Packets dropped due to max hops exceeded 0
Related Commands
|
Command |
Description |
|---|---|
|
show ip dhcp snooping statistics |
Display statistics related to the Dynamic Host Configuration Protocol. |
show lacp counters
To display information about Link Aggregation Control Protocol (LACP) statistics, use the show lacp counters command.
show lacp counters [interface port-channel channel-number]
Syntax Description
|
interface port-channel |
(Optional) Specifies the interface port channel. |
|
channel-number |
(Optional) Number of the LACP channel group. The range is from 1 to 4096. |
Defaults
None
Command Modes
Any command mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
4.0 |
This command was introduced. |
Usage Guidelines
If you do not specify the channel-number, all channel groups are displayed.
This command does not require a license.
Examples
This example shows how to display the LACP statistics for a specific channel group:
switch# show lacp counters interface port-channel 1
LACPDUs Marker Marker Response LACPDUs
Port Sent Recv Sent Recv Sent Recv Pkts Err
-----------------------------------------------------------------------------
Ethernet1/1 554 536 0 0 0 0 0
Ethernet1/2 527 514 0 0 0 0 0
Ethernet1/3 535 520 0 0 0 0 0
Ethernet1/4 515 502 0 0 0 0 0
Ethernet1/5 518 505 0 0 0 0 0
Ethernet1/6 540 529 0 0 0 0 0
Ethernet1/7 541 530 0 0 0 0 0
Ethernet1/8 547 532 0 0 0 0 0
Ethernet1/9 544 532 0 0 0 0 0
Ethernet1/10 513 501 0 0 0 0 0
Ethernet1/11 497 485 0 0 0 0 0
Ethernet1/12 493 486 0 0 0 0 0
Ethernet1/13 492 485 0 0 0 0 0
Ethernet1/14 482 481 0 0 0 0 0
Ethernet1/15 481 476 0 0 0 0 0
Ethernet1/16 482 477 0 0 0 0 0
Related Commands
|
Command |
Description |
|---|---|
|
clear lacp counters |
Clears the statistics for all LACP interfaces or those interfaces that belong to a specific LACP channel group. |
show lacp interface
To display information about specific Link Aggregation Control Protocol (LACP) interfaces, use the show lacp interface command.
show lacp interface ethernet slot/port
Syntax Description
|
slot/port |
Slot number and port number for the interface you want to display. The range is from 1 to 253. |
Defaults
None
Command Modes
Any command mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
4.0 |
This command was introduced. |
Usage Guidelines
The LACP_Activity field displays whether the link is configured in the active or passive port-channel mode.
The Port Identifier field displays the port priority as part of the information. The part of the information in this field is the port number. The following example shows how to identify the port priority and the port number:
Port Identifier=0x8000,0x101
The port priority value is 0x8000, and the port number value is 0x101 in this example.
This command does not require a license.
Examples
This example shows how to display the LACP statistics for a specific channel group:
switch# show lacp interface ethernet 1/1
switch(config-if-range)# show lacp interface eth1/1
Interface Ethernet1/1 is up
Channel group is 1 port channel is Po1
Lag Id: [ [(8000, 0-11-11-22-22-74, 0, 8000, 101), (8000, 0-11-11-22-22-75, 0, 8
Operational as aggregated link since Wed Jun 11 20:37:59 2008
Local Port: Eth1/1 MAC Address= 0-11-11-22-22-74
System Identifier=0x8000,0-11-11-22-22-74
Port Identifier=0x8000,0x101
LACP_Timeout=Long Timeout (30s)
Partner information refresh timeout=Long Timeout (90s)
MAC Address= 0-11-11-22-22-75
System Identifier=0x8000,0-11-11-22-22-75
Port Identifier=0x8000,0x401
LACP_Timeout=Long Timeout (30s)
Related Commands
|
Command |
Description |
|---|---|
|
show port-channel summary |
Displays information about all port-channel groups. |
show lacp neighbor
To display information about Link Aggregation Control Protocol (LACP) neighbors, use the show lacp neighbor command.
show lacp neighbor [interface port-channel channel-number]
Syntax Description
|
interface port-channel |
(Optional) Specifies the interface port channel. |
|
channel-number |
(Optional) Port-channel number for the LACP neighbor that you want to display. The range is from 1 to 4096. |
Defaults
None
Command Modes
Any command mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
4.0 |
This command was introduced. |
Usage Guidelines
If you do not specify the channel-number, all channel groups are displayed.
This command does not require a license.
Examples
This example shows how to display the information about the LACP neighbors for a specific port channel:
switch# show lacp neighbor interface port-channel 1
Flags: S - Device is sending Slow LACPDUs F - Device is sending Fast LACPDUs
A - Device is in Active mode P - Device is in Passive mode
Port System ID Port Number Age Flags
Eth1/1 32768,0-11-11-22-22-750x401 44817 SA
LACP Partner Partner Partner
Port Priority Oper Key Port State
Port System ID Port Number Age Flags
Eth1/2 32768,0-11-11-22-22-750x402 44817 SA
LACP Partner Partner Partner
Port Priority Oper Key Port State
Related Commands
|
Command |
Description |
|---|---|
|
show port-channel summary |
Displays information about all port-channel groups. |
show lacp port-channel
To display information about Link Aggregation Control Protocol (LACP) port channels, use the show lacp port-channel command.
show lacp port-channel [interface port-channel channel-number]
Syntax Description
|
interface port-channel |
(Optional) Specifies the interface port channel. |
|
channel-number |
(Optional) Port-channel number for the LACP neighbor that you want to display. The range is from 1 to 4096. |
Defaults
None
Command Modes
Any command mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
4.0 |
This command was introduced. |
Usage Guidelines
If you do not specify the channel-number, all channel groups are displayed.
This command does not require a license.
Examples
This example shows how to display the information about LACP port channels:
switch# show lacp port-channel
Local System Identifier=0x8000,0-11-11-22-22-74
Partner System Identifier=0x8000,0-11-11-22-22-75
Aggregate or individual=1
Local System Identifier=0x8000,0-11-11-22-22-74
Partner System Identifier=0x8000,0-11-11-22-22-75
Aggregate or individual=1
Related Commands
|
Command |
Description |
|---|---|
|
show port-channel summary |
Displays information about all port-channel groups. |
show lacp system-identifier
To display the Link Aggregation Control Protocol (LACP) system identifier for the device, use the show lacp system-identifier command.
show lacp system-identifier
Syntax Description
This command has no arguments or keywords.
Defaults
None
Command Modes
Any command mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
4.0 |
This command was introduced. |
Usage Guidelines
The LACP system ID is the combination of the configurable LACP system priority value and the MAC address.
Each system that runs LACP has an LACP system priority value. You can accept the default value of 32768 for this parameter, or you can configure a value between 1 and 65535. LACP uses the system priority with the MAC address to form the system ID and also uses the system priority during negotiation with other devices. A higher system priority value means a lower priority.
The system ID is different for each virtual device context (VDC).
This command does not require a license.
Examples
This example shows how to display the information about the LACP port channel for a specific port channel:
switch> show lacp system-identifier
Related Commands
|
Command |
Description |
|---|---|
|
lacp system-priority |
Sets the system priority for LACP. |
show logging level fex
To display the Fabric Extender (FEX) logging configuration, use the show logging level fex command.
show logging level fex
Syntax Description
This command has no arguments or keywords.
Defaults
None
Command Modes
EXEC mode
Command History
|
Release |
Modification |
|---|---|
|
5.1(1) |
This command was introduced. |
Usage Guidelines
This command does not require a license.
Examples
This example shows how to display the FEX logging configuration:
switch# show logging level fex
Facility Default Severity Current Session Severity
-------- ---------------- ------------------------
0(emergencies) 1(alerts) 2(critical)
3(errors) 4(warnings) 5(notifications)
6(information) 7(debugging)
Related Commands
|
Command |
Description |
|---|---|
|
show fex |
Displays all configured Fabric Extender chassis connected to the switch. |
show module fex
To display the Fabric Extender (FEX) module information, use the show module fex command.
show module fex [all chassis-id]
Syntax Description
|
all |
Displays information about all Fabric Extender modules. |
|
chassis-id |
Fabric Extender chassis ID. The range is from 100 to 199. |
Defaults
None
Command Modes
EXEC mode
Command History
|
Release |
Modification |
|
5.1(1) |
This command was introduced. |
Usage Guidelines
This command does not require a license.
Examples
This example shows how to display the module information for the Fabric Extender:
switch# show module fex all
FEX Mod Ports Card Type Model Status.
--- --- ----- ---------------------------------- ------------------ -----------
101 1 48 Fabric Extender 48x1GE + 4x10G M N2K-C2248TP-1GE ok
FEX Mod Sw Hw World-Wide-Name(s) (WWN)
--- --- -------------- ------ -----------------------------------------------
FEX Mod MAC-Address(es) Serial-Num
--- --- -------------------------------------- ----------
101 1 0005.9b70.dd40 to 0005.9b70.dd6f JAF1407AANJ
FEX Mod Ports Card Type Model Status.
--- --- ----- ---------------------------------- ------------------ -----------
102 1 48 Fabric Extender 48x1GE + 4x10G M N2K-C2248TP-1GE ok
FEX Mod Sw Hw World-Wide-Name(s) (WWN)
--- --- -------------- ------ -----------------------------------------------
FEX Mod MAC-Address(es) Serial-Num
--- --- -------------------------------------- ----------
102 1 68ef.bd61.ce00 to 68ef.bd61.ce2f JAF1407AAQN
This example shows how to display FEX module information:
FEX Mod Ports Card Type Model Status.
--- --- ----- ---------------------------------- ------------------ -----------
101 1 48 Fabric Extender 48x1GE + 4x10G M N2K-C2248TP-1GE ok
FEX Mod Sw Hw World-Wide-Name(s) (WWN)
--- --- -------------- ------ -----------------------------------------------
FEX Mod MAC-Address(es) Serial-Num
--- --- -------------------------------------- ----------
101 1 0005.9b70.dd40 to 0005.9b70.dd6f JAF1407AANJ
FEX Mod Ports Card Type Model Status.
--- --- ----- ---------------------------------- ------------------ -----------
102 1 48 Fabric Extender 48x1GE + 4x10G M N2K-C2248TP-1GE ok
FEX Mod Sw Hw World-Wide-Name(s) (WWN)
--- --- -------------- ------ -----------------------------------------------
FEX Mod MAC-Address(es) Serial-Num
--- --- -------------------------------------- ----------
102 1 68ef.bd61.ce00 to 68ef.bd61.ce2f JAF1407AAQN
This example shows how to display the module information for a specific Fabric Extender:
switch# show module fex 101
FEX Mod Ports Card Type Model Status.
--- --- ----- ---------------------------------- ------------------ -----------
101 1 48 Fabric Extender 48x1GE + 4x10G M N2K-C2248TP-1GE ok
FEX Mod Sw Hw World-Wide-Name(s) (WWN)
--- --- -------------- ------ -----------------------------------------------
FEX Mod MAC-Address(es) Serial-Num
--- --- -------------------------------------- ----------
101 1 0005.9b70.dd40 to 0005.9b70.dd6f JAF1407AANJ
Related Commands
|
Command |
Description |
|---|---|
|
show fex |
Displays all configured Fabric Extender chassis connected to the switch. |
show port-channel capacity
To display the number of port channels currently used and the number of port channels that are still available on the device, use the show port-channel capacity command.
show port-channel capacity
Syntax Description
This command has no arguments or keywords.
Defaults
None
Command Modes
Any command mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
4.1(2) |
This command was introduced. |
Usage Guidelines
There are a total of 768 port channels and virtual port channels (vPCs) available on each device.
This command does not require a license.
Examples
This example shows how to display the number of used and available port channels on the device:
switch (config) # show port-channel capacity
768 total 103 used 665 free 13% used
Related Commands
|
Command |
Description |
|---|---|
|
show port-channel summary |
Displays information about port channels. |
show port-channel compatibility-parameters
To display the parameters that must be the same among the member ports in order to join a port channel, use the show port-channel compatibility parameters command.
show port-channel compatibility-parameters
Syntax Description
This command has no arguments or keywords.
Defaults
None
Command Modes
Any command mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
4.0 |
This command was introduced. |
Usage Guidelines
When you add an interface to a channel group, the software checks certain interface attributes to ensure that the interface is compatible with the channel group. For example, you cannot add a Layer 3 interface to a Layer 2 channel group. The software also checks the operational attributes for an interface before allowing that interface to participate in the port-channel aggregation.
This command displays the list of compatibility checks that the system uses.
Using the channel-group command, you can force ports with incompatible parameters to join the port channel as long as the following parameters are the same:
•![]() (Link) speed capability
(Link) speed capability
•![]() Speed configuration
Speed configuration
•![]() Duplex capability
Duplex capability
•![]() Duplex configuration
Duplex configuration
•![]() Flow-control capability
Flow-control capability
•![]() Flow-control configuration
Flow-control configuration

Note ![]() See the channel-group command for information about forcing ports to join a port channel.
See the channel-group command for information about forcing ports to join a port channel.
This command does not require a license.
Examples
This example shows how to display the list of compatibility checks that the system makes to ensure that an interface is compatible with a channel group:
switch# show port-channel compatibility-parameters
Members must have the same port mode configured, either E or AUTO. If they
are configured in AUTO port mode, they have to negotiate E mode when they
come up. If a member negotiates a different mode, it will be suspended.
Members must have the same speed configured. If they are configured in AUTO
speed, they have to negotiate the same speed when they come up. If a member
negotiates a different speed, it will be suspended.
Members have to have the same MTU configured. This only applies to ethernet
Members have to have the same medium type configured. This only applies to
Members must have the same span mode.
Members must not have sub-interfaces.
Members must have same Duplex Mode configured.
Members must have same Ethernet Layer (switchport/no-switchport) configured.
Members cannot be SPAN ports.
Members must have same storm-control configured.
Members must have same flowctrl configured.
Members must have common capabilities.
Members port does not exist.
Members must be switching port, Layer 2.
Members must have the same port access VLAN.
Members must have the same port native VLAN.
Members must have the same port allowed VLAN list.
Related Commands
|
Command |
Description |
|---|---|
|
channel-group |
Adds or removes interfaces to port-channel groups and assigns the port-channel mode to the interface. |
show port-channel database
To display information about the the port channels, use the show port-channel database command.
show port-channel database [interface port-channel channel-number]
Syntax Description
|
interface port-channel |
(Optional) Specifies the interface port channel. |
|
channel-number |
(Optional) Port-channel number for the Link Aggregation Control Protocol (LACP) neighbor that you want to display. The range is from 1 to 4096. |
Defaults
None
Command Modes
Any command mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
4.0 |
This command was introduced. |
Usage Guidelines
If you do not specify the channel-number, all channel groups are displayed. This command displays Link Aggregation Control Protocol (LACP)-enabled ports channels and port channels without an associated aggregation protocol.
This command does not require a license.
Examples
This example shows how to display information about all port channels:
switch# show port-channel database
Administrative channel mode is active
Operational channel mode is active
Last membership update is successful
1 ports in total, 0 ports up
Age of the port-channel is 1d:16h:18m:50s
Time since last bundle is 1d:16h:18m:56s
Ports: Ethernet2/5 [down]
Administrative channel mode is active
Operational channel mode is active
Last membership update is successful
1 ports in total, 0 ports up
Age of the port-channel is 1d:16h:18m:50s
Time since last bundle is 1d:16h:18m:56s
Ports: Ethernet2/20 [down]
This example shows how to display information about a specific port channel:
switch# show port-channel database interface port-channel 20
Administrative channel mode is active
Operational channel mode is active
Last membership update is successful
1 ports in total, 0 ports up
Age of the port-channel is 1d:16h:23m:14s
Time since last bundle is 1d:16h:23m:20s
Ports: Ethernet2/20 [down]
Related Commands
|
Command |
Description |
|---|---|
|
show port-channel summary |
Displays a summary of information about all port channels. |
show port-channel load-balance
To display information about load balancing using port channels, use the show port-channel load-balance command.
show port-channel load-balance [forwarding-path interface port-channel channel-number]
Syntax Description
|
forwarding-path interface port-channel |
(Optional) Identifies the port in the port channel that forwards the packet. |
|
channel-number |
Port-channel number for the load-balancing forwarding path that you want to display. The is from 1 to 4096. |
Defaults
None
Command Modes
Any command mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
4.0 |
This command was introduced. |
Usage Guidelines
This command does not require a license.
Examples
This example shows how to display information about the current port-channel load balancing for the system:
switch# show port-channel load-balance
Port Channel Load-Balancing Configuration:
System: source-dest-ip-vlan
Port Channel Load-Balancing Addresses Used Per-Protocol:
Related Commands
|
Command |
Description |
|---|---|
|
port-channel load-balance ethernet |
Configures load balancing using port channels. |
show port-channel rbh-distribution
To display information about the Result Bundle Hash (RBH) for port channels, use the show port-channel rbh-distribution command.
show port-channel rbh-distribution [interface port-channel channel-number]
Syntax Description
|
interface port-channel |
(Optional) Specifies the interface port channel. |
|
channel-number |
(Optional) Port-channel number for the LACP neighbor that you want to display. The range is from 1 to 4096. |
Defaults
None
Command Modes
Any command mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
4.0 |
This command was introduced. |
Usage Guidelines
The RBH value ranges from 0 to 7 and is shared among port members in a port channel.
This command does not require a license.
Examples
This example shows how to display RBH distribution for a specific port channel:
switch# show port-channel rbh-distribution interface port-channel 4
ChanId Member port RBH values Num of buckets
-------- ------------- ----------------- ----------------
Related Commands
|
Command |
Description |
|---|---|
|
port-channel summary |
Displays summary information about port channels. |
show port-channel summary
To display summary information about the port channels, use the show port-channel summary command.
show port-channel summary
Syntax Description
This command has no arguments or keywords.
Defaults
None
Command Modes
Any command mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
5.1(1) |
Added a new port channel status `M’ to the command output. |
|
4.0 |
This command was introduced. |
Usage Guidelines
If the Link Aggregation Control Protocol (LACP) is not enabled, the output shows «NONE» in the Protocol column of the display.
A channel-group interface can be in the following operational states:
•![]() Down—The interface is down because it is administratively shut down or some other reason not related to port channels.
Down—The interface is down because it is administratively shut down or some other reason not related to port channels.
•![]() Individual—The interface is part of a port channel but is unable to aggregate into a port channel because of protocol exchange problems:
Individual—The interface is part of a port channel but is unable to aggregate into a port channel because of protocol exchange problems:
–![]() This interface continues to forward traffic as an individual link.
This interface continues to forward traffic as an individual link.
–![]() STP is aware of this interface.
STP is aware of this interface.
•![]() Suspended—The operational parameters of the interface are not compatible with the port channel. This interface is not forwarding traffic, although the physical MAC link state is still up.
Suspended—The operational parameters of the interface are not compatible with the port channel. This interface is not forwarding traffic, although the physical MAC link state is still up.
•![]() Switched—The interface is switched.
Switched—The interface is switched.
•![]() Up (port channel)—The port channel is up.
Up (port channel)—The port channel is up.
•![]() Up in port channel (members)—The port member of the port channel is up.
Up in port channel (members)—The port member of the port channel is up.
•![]() Hot standby (LACP only)—The interface is eligible to join the port group if one of the interfaces currently participating in the LACP channel goes down.
Hot standby (LACP only)—The interface is eligible to join the port group if one of the interfaces currently participating in the LACP channel goes down.
–![]() This interface does not forward data traffic; it forwards only protocol data units (PDUs).
This interface does not forward data traffic; it forwards only protocol data units (PDUs).
–![]() This interface does not run STP.
This interface does not run STP.
•![]() Module-removed—The module has been removed.
Module-removed—The module has been removed.
•![]() Routed—The interface is routed.
Routed—The interface is routed.
This command does not require a license.
Examples
This example shows how to display summary information for the port channels:
switch(config-if)# show port-channel summary
Flags: D - Down P - Up in port-channel (members)
I - Individual H - Hot-standby (LACP only)
s - Suspended r - Module-removed
M - Not in use. Min-links not met
--------------------------------------------------------------------------------
Group Port- Type Protocol Member Ports
--------------------------------------------------------------------------------
2 Po2(SU) Edge LACP Eth4/9(D) Eth4/10(D) Eth4/11(P)
3 Po3(SU) Edge LACP Eth4/27(P) Eth4/28(P) Eth4/29(P)
10 Po10(SU) Edge LACP Eth4/1(P) Eth4/2(P) Eth4/3(P)
Eth4/4(P) Eth4/13(P) Eth4/14(P)
Eth4/15(P) Eth4/16(P) Eth4/17(P)
Eth4/18(P) Eth4/19(P) Eth4/20(P)
Eth4/21(P) Eth4/22(P) Eth4/23(P)
Related Commands
|
Command |
Description |
|---|---|
|
show port-channel usage |
Displays the port-channel numbers used and available. |
|
show port-channel traffic |
Displays transmitted and received unicast, multicast, and broadcast percentages for the port channels. |
show port-channel traffic
To display traffic rx/tx counter statistics for port channels, use the show port-channel traffic command.
show port-channel traffic [interface port-channel channel-number]
Syntax Description
|
interface port-channel |
(Optional) Specifies the interface port channel. |
|
channel-number |
(Optional) Port-channel number for the LACP neighbor that you want to display. The range is from 1 to 4096. |
Defaults
None
Command Modes
Any command mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
4.0 |
This command was introduced. |
Usage Guidelines
This command displays the percentage of transmitted and received unicast, multicast, and broadcast traffic about the port channel.
If you do not specify the channel-number, information for all port channels is displayed.
This command does not require a license.
Examples
This example shows how to display the traffic statistics for all port channels:
switch(config)# show port-channel traffic
ChanId Port Rx-Ucst Tx-Ucst Rx-Mcst Tx-Mcst Rx-Bcst Tx-Bcst
------ --------- ------- ------- ------- ------- ------- -------
5 Eth2/5 0.0% 0.0% 0.0% 0.0% 0.0% 0.0%
------ --------- ------- ------- ------- ------- ------- -------
20 Eth2/20 0.0% 0.0% 0.0% 0.0% 0.0% 0.0%
This example shows how to display the traffic statistics for a specific port channel:
switch(config)# show port-channel traffic interface port-channel 5
ChanId Port Rx-Ucst Tx-Ucst Rx-Mcst Tx-Mcst Rx-Bcst Tx-Bcst
------ --------- ------- ------- ------- ------- ------- -------
5 Eth2/5 0.0% 0.0% 0.0% 0.0% 0.0% 0.0%
Related Commands
|
Command |
Description |
|---|---|
|
port-channel summary |
Displays summary information about port channels. |
show port-channel usage
To display the port-channel numbers used and available, use the show port-channel usage command.
show port-channel usage
Syntax Description
This command has no arguments or keywords.
Defaults
None
Command Modes
Any command mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
4.0 |
This command was introduced. |
Usage Guidelines
This command displays port-channel numbers used and available in the virtual device context (VDC) that you are monitoring.
The number of port-channel numbers available across all VDCs for the entire system is from 1 to 4096.
This command does not require a license.
Examples
This example shows how to display the usage for all port channels:
switch# show port-channel usage
Totally 2 port-channel numbers used
====================================
Unused: 1 - 4 , 6 - 19 , 21 - 4096
Related Commands
|
Command |
Description |
|---|---|
|
port-channel summary |
Displays summary information about port channels. |
show port-profile
To display information about port profiles, use the show port-profile command.
show port-profile [brief | expand-interface [name name] | name name | usage]
Syntax Description
|
brief |
(Optional) Displays brief information about the port profiles. |
|
expand-interface name |
(Optional) Displays the configured attributes at an interface per port profile. An optional name can be specified to show the expanded interface output for that specific port profile. |
|
name name |
(Optional) Displays information for the specified port profile. |
|
usage |
(Optional) Displays a list of interfaces to which each profile is attached. |
Defaults
None
Command Modes
Any command mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
4.2(1) |
This command was introduced. |
Usage Guidelines
Use the show port-profile command to display information about the configured port profiles on the device. It displays all configured port profiles.
Port profiles are not aware of default values, so the default value configuration appears in the port profiles. For example, MTU 1500 is a default value and does not appear in the running-configuration of an interface. However, because port profiles are unaware of default values, MTU 1500 appears in the port-profile display.
This command does not require a license.
Examples
This example shows how to display information about port profiles:
switch(config)# show port-profile
evaluated config attributes:
evaluated config attributes:
This example shows how to display brief port profile information:
switch(config)# show port-profile brief
----------------------------------------------------------
Port Profile Conf Eval Assigned Child
Profile State Items Items Intfs Profs
----------------------------------------------------------
This example shows how to display expanded port profile interface information:
switch(config)# show port-profile expand-interface
This example shows how to display specific port profile information:
switch(config)# show port-profile name try1
evaluated config attributes:
switch(config)# show port-profile usage
This example shows how to display port profiles and values that you have entered in interface configuration mode using the show running-config command:
switch(config)# show running-config interface ethernet 8/5
Related Commands
|
Command |
Description |
|---|---|
|
port-profile |
Configures, names, and allows you to enter port-profile configuration mode. |
|
inherit port-profile |
Assigns port profile to specified interfaces and allows one port profile to inherit configuration parameters from another port profile. |
show running-config fex
To display the Fabric Extender (FEX) running configuration, use the show running-config fex command.
show running-config fex
Syntax Description
This command has no arguments or keywords.
Defaults
None
Command Modes
Global configuration mode
Command History
|
Release |
Modification |
|
5.1(1) |
This command was introduced. |
Usage Guidelines
This command does not require a license.
Examples
This example shows how to display detailed FEX information:
switch# show running-config fex
!Command: show running-config fex
!Time: Tue Sep 7 09:22:40 2010
interface port-channel101
switchport mode fex-fabric
interface port-channel102
switchport mode fex-fabric
switchport mode fex-fabric
switchport mode fex-fabric
switchport mode fex-fabric
switchport mode fex-fabric
Related Commands
|
Command |
Description |
|---|---|
|
show fex |
Displays all configured Fabric Extender chassis connected to the switch. |
show running-config interface
To display the running configuration for a specific interface, use the show running-config interface command.
show running-config interface [all | {ethernet {slot/port} [all]} | expand-port-profile | {loopback {number} [all]} | {mgmt0 [all]} | {port-channel {channel-number} [membership]} | {tunnel {number} [all]} | {vlan {vlan-id} [all]}
Syntax Description
|
all |
(Optional) Displays the configuration with defaults. |
|
ethernet slot/port |
Displays the number of the module and port number. The range is from 1 to 253. |
|
expand-port-profile |
(Optional) Displays port profiles. |
|
loopback number |
Displays the number of the loopback interface. The range is from 1 to 4096. |
|
mgmt0 |
(Optional) Displays the management interface. |
|
port-channel channel-number |
Displays the number of the port-channel group. The range is from 0 to 1023. |
|
membership |
(Optional) Specifies the membership of the specified port channel. |
|
tunnel number |
Displays the number of the tunnel interface. The range is from 0 to 65535. |
|
vlan vlan-id |
Displays the number of the VLAN. The range is from 1 to 4096. |
Defaults
None
Command Modes
Any command mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
4.0 |
This command was introduced. |
|
4.2(1) |
The expand-port-profile parameter was introduced. |
Usage Guidelines
This command does not require a license.
Examples
This example shows how to display information about the running configuration for a specific Ethernet interface:
switch(config)# show running-config interface ethernet 2/7
description Ethernet port 3 on module 1
This example shows how to display information about the running configuration for a specific range of Ethernet interfaces:
switch(config)# show running-config interface ethernet 2/7 - 9
description Ethernet port 3 on module 1
This example shows how to display information about the running configuration for a specific loopback interface:
switch(config)# interface loopback 345
switch(config-if)# show running-config interface loopback 345
This example shows how to display the running configuration for a specific port channel:
switch(config)# show running-config interface port-channel 10
This example shows how to display information about the running configuration for VLAN interface 50:
switch(config)# show running-config interface vlan 50
Related Commands
|
Command |
Description |
|---|---|
|
interface |
Enters the interface configuration mode and configures the types and identities of interfaces. |
|
interface vlan |
Creates a VLAN interface and enters interface configuration mode. |
|
show interface ethernet |
Displays information about the Ethernet interface. |
|
show port-channel summary |
Displays a summary of port-channel information. |
|
show running-config |
Displays the running configuration on the device. |
show running-config interface mgmt
To display the running configuration for a specific management interface, use the show running-config interface mgmt command.
show running-config interface mgmt {number}
Syntax Description
|
number |
Management interface number that you want to display. The value is from 0 to 0. |
Defaults
None
Command Modes
Any command mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
4.0 |
This command was introduced. |
Usage Guidelines
Use the show running-config interface mgmt command to display the running configuration for a management interface.
This command does not require a license.
Examples
This example shows how to display information about the running configuration for management interface 0:
switch# show running-config interface mgmt 0
ip address 172.28.231.193/23
Related Commands
|
Command |
Description |
|---|---|
|
show interface mgmt |
Displays the management interface information. |
show running-config vpc
To display the running configuration information for virtual port channels (vPCs), use the show running-config vpc command.
show running-config vpc [all]
Syntax Description
|
all |
(Optional) Displays the running configuration for all vPCs. |
Defaults
None
Command Modes
Any command mode.
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
4.1(3) |
This command was introduced. |
Usage Guidelines
This command does not require a license.
Examples
This example shows how to display the running configuration for a vPC:
switch (config)# show running-config vpc
peer-keepalive destination 10.10.76.52 source 10.10.76.51 udp-port 3200 vrf ma
engagement interval 1000 timeout 5
interface port-channel101
interface port-channel200
interface port-channel201
Related Commands
|
Command |
Description |
|---|---|
|
show vpc brief |
Displays information about vPCs. If the feature is not enabled, this command returns an error. |
show sprom fex
To display information about the Fabric Extender Serial (FEX) PROM (SPROM), use the show sprom fex command.
show sprom fex {all | chassis-ID {all | backplane | powersupply module-number}}
Syntax Description
|
all |
Displays all SPROM content for a specific Fabric Extender. |
|
chassis-ID |
Fabric Extender chassis ID. The range is from 100 to 199. |
|
backplane |
Displays the backplane SPROM content for a specific Fabric Extender. |
|
powersupply |
Displays the power supply SPROM content for a specific Fabric Extender. |
|
module-number |
Power supply module number for a specific Fabric Extender. The range is from 1 to 2. |
Defaults
None
Command Modes
EXEC mode
Command History
|
Release |
Modification |
|---|---|
|
5.1(1) |
This command was introduced. |
Usage Guidelines
This command does not require a license.
Examples
This example shows how to display all SPROM content for a specific Fabric Extender:
switch# show sprom fex 101 all
DISPLAY FEX 101 SUP sprom contents
OEM String : Cisco Systems, Inc.
Product Number : N2K-C2248TP-1GE
Serial Number : JAF1407AANJ
Part Number : 73-12748-04
snmpOID : 9.12.3.1.9.78.3.0
Supervisor Module specific block:
MAC Addresses : 00-00-00-00-00-00
This command shows how to display the power supply SPROM contents for a specific Fabric Extender:
switch# show sprom fex 104 powersupply 1
DISPLAY FEX 101 power-supply 1 sprom contents:
OEM String : Cisco Systems, Inc.
Product Number : N2200-PAC-400W
Serial Number : LIT14030HK9
Part Number : 341-0375-03
snmpOID : 9.12.3.1.6.273.0.0
This command shows how to display the backplane SPROM content for a specific Fabric Extender:
switch# show sprom fex 101 backplane
DISPLAY FEX 101 SUP sprom contents
OEM String : Cisco Systems, Inc.
Product Number : N2K-C2248TP-1GE
Serial Number : JAF1407AANJ
Part Number : 73-12748-04
snmpOID : 9.12.3.1.9.78.3.0
Supervisor Module specific block:
Related Commands
|
Command |
Description |
|---|---|
|
show fex |
Displays all configured Fabric Extender chassis connected to the switch. |
show startup-config interface
To display interface configuration information in the startup configuration, use the show startup-config interface command.
show startup-config interface [ethernet slot/port | expand-port-profile | loopback number | mgmt | port-channel {channel-number} [membership] | tunnel number | {vlan vlan-id}]
Syntax Description
|
ethernet slot/port |
(Optional) Displays the number of the module and port number. |
|
expand-port-profile |
(Optional) Displays the port profiles. |
|
loopback number |
(Optional) Displays the number of the loopback interface. The range is from 1 to 4096. |
|
mgmt |
(Optional) Displays the management interface. |
|
port-channel channel-number |
(Optional) Displays the number of the port-channel group. The range is from 0 to 1023. |
|
membership |
(Optional) Displays the membership of the specified port channel. |
|
tunnel number |
(Optional) Displays the number of the tunnel interface. The range is from 0 to 65535. |
|
vlan vlan-id |
(Optional) Displays the number of the VLAN. The range is from 1 to 4096. |
Defaults
None
Command Modes
Any command mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
4.1(2) |
This command was introduced. |
|
4.2(1) |
The expand-port-profile parameter was introduced. |
Usage Guidelines
This command does not require a license.
Examples
This example shows how to display the information in the startup configuration for the interface Ethernet 7/1:
switch(config)# show startup-config interface ethernet 7/1
Related Commands
|
Command |
Description |
|---|---|
|
show interface |
Displays information about the specified interface. |
show startup-config vpc
To display virtual port-channel (vPC) configuration information in the startup configuration, use the show startup-config vpc command.
show startup-config vpc [all]
Syntax Description
|
all |
(Optional) Displays the startup-configuration information for all vPCs. |
Defaults
None
Command Modes
Any command mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
4.1(3) |
This command was introduced. |
Usage Guidelines
This command does not require a license.
Examples
This example shows how to display the vPC information in the startup configuration:
switch(config)# show startup-config vpc
Related Commands
|
Command |
Description |
|---|---|
|
show vpc brief |
Displays information about vPCs. |
show system reset-reason fex
To display the reason for the last reset of the Fabric Extender (FEX), use the show system reset-reason fex command.
show system reset-reason fex chassis-ID
Syntax Description
|
chassis-ID |
Fabric Extender chassis ID. The chassis ID range is from 100 to 199. |
Defaults
None
Command Modes
EXEC mode
Command History
|
Release |
Modification |
|---|---|
|
5.1(1) |
This command was introduced. |
Usage Guidelines
This command does not require a license.
Examples
This example shows how to display the last reset reason for a specific Fabric Extender:
switch# show system reset-reason fex 101
----- reset reason for FEX 101 ---
1) At 550180 usecs after Mon Sep 6 07:43:23 2010
Reset Reason: Reset Requested by CLI command reload (9)
Service (Additional Info): Reload requested by supervisor
Image Version: 5.1(0.159.6)
2) At 269728 usecs after Mon Sep 6 07:41:36 2010
Reset Reason: Reset Requested by CLI command reload (9)
Service (Additional Info): Reload requested by supervisor
Image Version: 5.1(0.159.6)
3) At 868270 usecs after Sun Feb 24 22:07:28 2008
Reset Reason: Reset Requested by CLI command reload (9)
Service (Additional Info): Reload requested by supervisor
Image Version: 5.1(0.159.6)
4) At 204499 usecs after Sun Feb 24 20:38:20 2008
Reset Reason: Reset Requested by CLI command reload (9)
Service (Additional Info): Reload requested by supervisor
Image Version: 5.1(0.159.6)
Related Commands
|
Command |
Description |
|---|---|
|
show fex |
Displays all configured Fabric Extender chassis connected to the switch. |
show tech fex all
To gather detailed information for all Fabric Extender (FEX) troubleshooting information, use the show tech fex all command.
show tech fex all
Syntax Description
This command has no arguments or keywords.
Defaults
None
Command Modes
EXEC mode
Command History
|
Release |
Modification |
|---|---|
|
5.1(1) |
This command was introduced. |
Usage Guidelines
This command does not require a license.
Examples
This example shows how to display detailed FEX information:
switch# show tech fex all
02/25/2008 03:38:18.22739: ***************************************************
02/25/2008 03:38:18.23019: Satctrl Built at Thu Aug 5 19:12:00 PDT 2010 on rami
neni-lnx in directory /ws/mhau-sjc/deewhy_june_2/build by mhau
02/25/2008 03:38:18.23040: Version: 2102/25/2008 03:38:18.23055: ***************
************************************
02/25/2008 03:38:18.34242: satellite_init: initializing modules
02/25/2008 03:38:18.34466: satctrl_get_cardid: Platform card ID 99
02/25/2008 03:38:18.34771: Platform info: cardid=99, num_slots=1
02/25/2008 03:38:18.461803: satctrl_get_cardid: Platform card ID 99
02/25/2008 03:38:18.461849: satellite_init: swcardid=99
02/25/2008 03:38:18.461995: get fru: chas ser:SSI14061500 chas model:N2K-C2248TP
-1GE chas part: 68-3601-04
02/25/2008 03:38:18.462022: get fru: mod ser:JAF1407AANJ mod model:N2K-C2248TP-1
02/25/2008 03:38:18.462046: satellite_init: initializing inband
02/25/2008 03:38:18.475965: satellite_init: inband initialized
02/25/2008 03:38:18.476153: satellite_module_cfg_init: initializing modue (0)
02/25/2008 03:38:18.477439: satctrl_module_fsm_init: Fsm initialized for fabric
02/25/2008 03:38:18.477533: satctrl_module_fsm_init: Fsm initialized for fabric
02/25/2008 03:38:18.477855: satellite_init: done initializing satctrl module
02/25/2008 03:38:18.477897: satctrl_set_mts_addr: dummy_addr: 0xff02
02/25/2008 03:38:18.478139: My addr is changed to 0xff
Related Commands
|
Command |
Description |
|---|---|
|
show fex |
Displays all configured Fabric Extender chassis connected to the switch. |
show tech-support fex
To display detailed troubleshooting information for a Fabric Extender (FEX), use the show tech-support fex command.
show tech-support fex all chassis-ID
Syntax Description
|
all |
Specifies detailed information for all FEX. |
|
chassis-ID |
Fabric Extender chassis ID. The range is from 100 to 199. |
Defaults
None
Command Modes
EXEC mode
Command History
|
Release |
Modification |
|
5.1(1) |
This command was introduced. |
Usage Guidelines
This command does not require a license.
Examples
This example shows how to display detailed troubleshooting information for a FEX:
switch# show tech-support fex 101
09/06/2010 07:44:12.26863: Satctrl Built at Thu Aug 5 19:12:00 PDT 2010 on rami
neni-lnx in directory /ws/mhau-sjc/deewhy_june_2/build by mhau
09/06/2010 07:44:12.26883: Version: 2109/06/2010 07:44:12.26898: ***************
************************************
09/06/2010 07:44:12.38241: satellite_init: initializing modules
09/06/2010 07:44:12.38466: satctrl_get_cardid: Platform card ID 99
09/06/2010 07:44:12.38772: Platform info: cardid=99, num_slots=1
09/06/2010 07:44:12.463410: satctrl_get_cardid: Platform card ID 99
09/06/2010 07:44:12.463455: satellite_init: swcardid=99
09/06/2010 07:44:12.463598: get fru: chas ser:SSI14061500 chas model:N2K-C2248TP
-1GE chas part: 68-3601-04
09/06/2010 07:44:12.463625: get fru: mod ser:JAF1407AANJ mod model:N2K-C2248TP-1
09/06/2010 07:44:12.463649: satellite_init: initializing inband
09/06/2010 07:44:12.477534: satellite_init: inband initialized
09/06/2010 07:44:12.477723: satellite_module_cfg_init: initializing modue (0)
09/06/2010 07:44:12.478987: satctrl_module_fsm_init: Fsm initialized for fabric
09/06/2010 07:44:12.479080: satctrl_module_fsm_init: Fsm initialized for fabric
09/06/2010 07:44:12.479423: satellite_init: done initializing satctrl module
09/06/2010 07:44:12.479466: satctrl_set_mts_addr: dummy_addr: 0xff02
09/06/2010 07:44:12.479709: My addr is changed to 0xff
This example shows how to display all troubleshooting information for all FEX:
switch# show tech-support fex all
09/06/2010 07:44:12.26583: ***************************************************
09/06/2010 07:44:12.26863: Satctrl Built at Thu Aug 5 19:12:00 PDT 2010 on rami
neni-lnx in directory /ws/mhau-sjc/deewhy_june_2/build by mhau
09/06/2010 07:44:12.26883: Version: 2109/06/2010 07:44:12.26898: ***************
************************************
09/06/2010 07:44:12.38241: satellite_init: initializing modules
09/06/2010 07:44:12.38466: satctrl_get_cardid: Platform card ID 99
09/06/2010 07:44:12.38772: Platform info: cardid=99, num_slots=1
09/06/2010 07:44:12.463410: satctrl_get_cardid: Platform card ID 99
09/06/2010 07:44:12.463455: satellite_init: swcardid=99
09/06/2010 07:44:12.463598: get fru: chas ser:SSI14061500 chas model:N2K-C2248TP
-1GE chas part: 68-3601-04
09/06/2010 07:44:12.463625: get fru: mod ser:JAF1407AANJ mod model:N2K-C2248TP-1
09/06/2010 07:44:12.463649: satellite_init: initializing inband
09/06/2010 07:44:12.477534: satellite_init: inband initialized
09/06/2010 07:44:12.477723: satellite_module_cfg_init: initializing modue (0)
09/06/2010 07:44:12.478987: satctrl_module_fsm_init: Fsm initialized for fabric
09/06/2010 07:44:12.479080: satctrl_module_fsm_init: Fsm initialized for fabric
09/06/2010 07:44:12.479423: satellite_init: done initializing satctrl module
09/06/2010 07:44:12.479466: satctrl_set_mts_addr: dummy_addr: 0xff02
09/06/2010 07:44:12.479709: My addr is changed to 0xff
Related Commands
|
Command |
Description |
|---|---|
|
show fex |
Displays all configured Fabric Extender chassis connected to the switch. |
show udld
To display information about the Unidirectional Link Detection (UDLD) configuration, use the show udld command.
show udld [ethernet slot/port | global | neighbors]
Syntax Description
|
ethernet slot/port |
(Optional) Displays the Ethernet slot and port number you want to display. The range is from 1 to 253. |
|
global |
(Optional) Displays the UDLD global status and configuration on all interfaces. |
|
neighbors |
(Optional) Displays the UDLD neighbor interfaces. |
Defaults
None
Command Modes
Any command mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
4.0 |
This command was introduced. |
Usage Guidelines
Use the show udld command to display information about the UDLD configuration for an interface. UDLD must be enabled on the device before you can display this command; enter the feature udld command to enable UDLD globally on the device.
This command does not require a license.
Examples
This example shows how to display information about the UDLD configuration for Ethernet port 2/7:
switch# show udld ethernet 2/7
--------------------------------
Port enable administrative configuration setting: disabled
Port enable operational state: disabled
Current bidirectional state: unknown
Current operational state: udld-init - Multiple neighbor not detected
Related Commands
|
Command |
Description |
|---|---|
|
udld |
Configures the ports to use a UDLD mode. |
|
feature udld |
Enables UDLD globally on device. |
show vdc
To display virtual device contexts (VDCs), use the show vdc command.
show vdc
Syntax Description
This command has no arguments or keywords.
Defaults
None
Command Modes
Any command mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
5.1(1) |
This command was introduced. |
Usage Guidelines
This command does not require a license.
Examples
This example shows how to display VDCs:
switch# show vdc
vdc_id vdc_name state mac
lc
—— ——— —— ———-
——
1 switch active 00:22:55:79:a4:c1
M1 F1
2 1 active 00:22:55:79:a4:c2
M1 F1
3 2 active 00:22:55:79:a4:c3
M1 F1
4 fred active 00:22:55:79:a4:c4
M1 F1
switch#
Related Commands
|
Command |
Description |
|
show lacp |
Displays LACP information. |
show version fex
To display the software version information about a Fabric Extender (FEX), use the show version fex command.
show version fex chassis-ID
Syntax Description
|
chassis-ID |
Fabric Extender chassis ID. The range is from 100 to 199. |
Defaults
None
Command Modes
EXEC mode
Command History
|
Release |
Modification |
|---|---|
|
5.1(1) |
This command was introduced. |
Usage Guidelines
This command does not require a license.
Examples
This example shows how to display the software version of a Fabric Extender:
switch# show version fex 100
System boot mode: primary
System image version: 5.1(1) [build 5.1(0.159.6)]
Module: Fabric Extender 48x1GE + 4x10G Module
Serial number: JAF1407AANJ
Kernel uptime is 1 day(s), 1 hour(s), 12 minutes(s), 13 second(s)
Last reset at Mon Sep 6 07:43:23 2010
Reason: Reset Requested by CLI command reload
Service: Reload requested by supervisor
Related Commands
|
Command |
Description |
|---|---|
|
show fex |
Displays all configured Fabric Extender chassis connected to the switch. |
show vpc brief
To display brief information about the virtual port channels (vPCs), use the show vpc brief command.
show vpc brief [vpc number]
Syntax Description
|
vpc number |
(Optional) Displays the brief information for the specified vPC. The range is from 1 to 4096. |
Defaults
None
Command Modes
Any command mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
4.1(3) |
This command was introduced. |
|
4.2(1) |
Added the vpc keyword and number argument. |
Usage Guidelines
The show vpc brief command displays the vPC domain ID, the peer-link status, the keepalive message status, whether the configuration consistency is successful, and whether the peer-link formed or failed to form.
This command is not available if you have not enabled the vPC feature. See the feature vpc command for information on enabling vPCs.
Beginning with Cisco Release 4.2(1), you can display the track object, if you have configured a tracked object for running vPCs on a single module under the vpc-domain configuration mode. See the Cisco Nexus 7000 Series NX-OS Interfaces Configuration Guide, Release 5.x, for information on this feature.
This command does not require a license.
Examples
This example shows how to display brief information about the vPCs:
switch(config)# show vpc brief
(*) - local vpc is down, forwarding via vPC peer-link
Peer status : peer adjacency formed ok
vPC keep-alive status : peer is alive
Configuration consistency status: success
Number of vPC configured : 1
---------------------------------------------------------------------
id Port Status Active vlans
-- ---- ------ --------------------------------------------------
----------------------------------------------------------------------
id Port Status Consistency Reason Active vlans
-- ---- ------ ----------- -------------------------- ------------
20 Po20 up success success 1-100
This example also shows how to display brief information about the vPCs. In this example, the port channel failed the consistency check, and the device displays the reason for the failure:
switch(config)# show vpc brief
(*) - local vpc is down, forwarding via vPC peer-link
Peer status : peer adjacency formed ok
vPC keep-alive status : peer is alive
Configuration consistency status: failed
Configuration consistency reason: vPC type-1 configuration incompatible - STP interface port type inconsistent
Number of vPC configured : 1
---------------------------------------------------------------------
id Port Status Active vlans
-- ---- ------ --------------------------------------------------
----------------------------------------------------------------------
id Port Status Consistency Reason Active vlans
-- ---- ------ ----------- -------------------------- ------------
20 Po20 up failed vPC type-1 configuration -
This example shows how to display information about the tracked objects in the vPCs, which is available beginning in Cisco NX-OS Release 4.2(1):
switch(config)# show vpc brief
(*) - local vpc is down, forwarding via vPC peer-link
Peer status : peer adjacency formed ok
vPC keep-alive status : peer is alive
Configuration consistency status: success
Number of vPC configured : 3
---------------------------------------------------------------------
id Port Status Active vlans
-- ---- ------ --------------------------------------------------
Related Commands
|
Command |
Description |
|---|---|
|
feature vpc |
Enables vPCs on the device. |
|
show port channel summary |
Displays information about port channels. |
show vpc consistency-parameters
To display the consistency of parameters that must be compatible across the virtual port-channel (vPC) interfaces, use the show vpc consistency-parameters command.
show vpc consistency-parameters {global | interface port-channel channel-number | vlan | vpc number}
Syntax Description
|
global |
(Optional) Displays the configuration of all Type 1 global parameters on both sides of the vPC peer link. |
|
interface port-channel |
(Optional) Displays the configuration of all Type 1 interface parameters on both sides of the vPC peer link. |
|
channel- number |
(Optional) Channel number. The range is from 1 to 4096. |
|
vlan |
(Optional) Displays the configuration of all Type 1 interface parameters on both sides of the vPC peer link for the specified VLAN. |
|
vpc number |
(Optional) Displays the configuration of all Type 1 interface parameters on both sides of the vPC peer link for the specified vPC. The range is from 1 to 4096. |
Defaults
None
Command Modes
Any command mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
4.1(3) |
This command was introduced. |
|
4.2(1) |
Added the display of local suspended VLANs. Note |
|
4.2(1) |
Added the vpc argument. |
|
5.2(1) |
Added the vlan keyword. |
Usage Guidelines
The show vpc consistency-parameters command displays the configuration of all the vPC Type 1 parameters on both sides of the vPC peer link.

Note ![]() All the Type 1 configurations must be identical on both sides of the vPC peer link, or the link does not come up.
All the Type 1 configurations must be identical on both sides of the vPC peer link, or the link does not come up.
The vPC Type 1 configuration parameters are as follows:
•![]() Port-channel mode: on, off, or active
Port-channel mode: on, off, or active
•![]() Link speed per channel
Link speed per channel
•![]() Duplex mode per channel
Duplex mode per channel
•![]() Trunk mode per channel
Trunk mode per channel
–![]() Native VLAN
Native VLAN
–![]() VLANs allowed on trunk
VLANs allowed on trunk
–![]() Tagging of native VLAN traffic
Tagging of native VLAN traffic
•![]() Spanning Tree Protocol (STP) mode
Spanning Tree Protocol (STP) mode
•![]() STP region configuration for Multiple Spanning Tree
STP region configuration for Multiple Spanning Tree
•![]() Enable/disable state the same per VLAN
Enable/disable state the same per VLAN
•![]() STP global settings
STP global settings
–![]() Bridge Assurance setting
Bridge Assurance setting
–![]() Port type setting—We recommend that you set all vPC peer link ports as network ports.
Port type setting—We recommend that you set all vPC peer link ports as network ports.
–![]() Loop Guard settings
Loop Guard settings
•![]() STP interface settings:
STP interface settings:
–![]() Port type setting
Port type setting
–![]() Loop Guard
Loop Guard
–![]() Root Guard
Root Guard
•![]() Maximum transmission unit (MTU)
Maximum transmission unit (MTU)
•![]() Allowed VLAN bit set
Allowed VLAN bit set
This command is not available if you have not enabled the vPC feature. See the feature vpc command for information on enabling vPCs.
This command does not require a license.
Examples
This example shows how to display the vPC consistency parameters for the specified port channel:
switch (config)# show vpc consistency-parameters global
Type 1 : vPC will be suspended in case of mismatch
Name Type Local Value Peer Value
------------- ---- ------------------------ --------------------------
STP Mode 1 Rapid-PVST Rapid-PVST
STP Loopguard 1 Disabled Disabled
STP Bridge 1 Enabled Enabled
STP Port Type 1 Normal Normal
Allowed VLAN - 1-100 1-100
This example shows how to display the vPC consistency parameters for the specified port channel:
switch (config)# show vpc consistency-parameters interface port-channel 20
Type 1 : vPC will be suspended in case of mismatch
Name Type Local Value Peer Value
------------- ---- ------------------------ --------------------------
STP Port Type 1 Default Default
Allowed VLAN - 1-100 1-100
Related Commands
|
Command |
Description |
|---|---|
|
show vpc brief |
Displays information about vPCs. If the feature is not enabled, the system displays an error when you enter this command. |
|
show port channel summary |
Displays information about port channels. |
show vpc orphan-ports
To display ports that are not part of the virtual port channel (vPC) but have common VLANs, use the show vpc orphan-ports command.
show vpc orphan-ports
Syntax Description
This command has no arguments or keywords.
Defaults
None
Command Modes
Any command mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
4.2(1) |
This command was introduced. |
Usage Guidelines
The show vpc orphan-ports command displays those ports that are not part of the vPC but that share common VLANs with ports that are part of the vPC.
This command is not available if you have not enabled the vPC feature. See the feature vpc command for information on enabling vPCs.
This command does not require a license.
Examples
This example shows how to display vPC orphan ports:
switch(config)# show vpc orphan ports
--------::Going through port database. Please be patient.::--------
------- -------------------------
Related Commands
|
Command |
Description |
|---|---|
|
feature vpc |
Enables vPCs on the device. |
|
show vpc brief |
Displays brief information about vPCs. |
show vpc peer-keepalive
To display the destination IP for the virtual port-channel (vPC) peer keepalive message and the status of the messages, use the show vpc peer-keepalive command.
show vpc peer-keepalive
Syntax Description
This command has no arguments or keywords.
Defaults
None
Command Modes
Any command mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
4.1(3) |
This command was introduced. |
Usage Guidelines
The show vpc peer-keepalive command displays the destination IP of the peer keepalive message for the vPC. The command also displays the send and receive status as well as the last update from the peer in seconds and milliseconds

Note ![]() We recommend that you create a separate virtual routing and forwarding (VRF) instance on the peer devices to send and receive the vPC peer keepalive messages. Do not use the peer link itself to send the vPC peer-keepalive messages.
We recommend that you create a separate virtual routing and forwarding (VRF) instance on the peer devices to send and receive the vPC peer keepalive messages. Do not use the peer link itself to send the vPC peer-keepalive messages.
This command is not available if you have not enabled the vPC feature. See the feature vpc command for information on enabling vPCs.
This command does not require a license.
Examples
This example shows how to display information about the peer-keepalive message:
n7k-2(config-vpc-domain)# show vpc peer-keepalive
vPC keep-alive status : peer is alive
--Last send at : 2008.05.17 18:23:53 986 ms
--Sent on interface : Eth7/16
--Receive status : Success
--Last receive at : 2008.05.17 18:23:54 99 ms
--Received on interface : Eth7/16
--Last update from peer : (0) seconds, (486) msec
vPC Keep-alive parameters
--Destination : 172.23.145.213
--Keepalive interval : 1000 msec
--Keepalive timeout : 5 seconds
--Keepalive hold timeout : 3 seconds
--Keepalive udp port : 3200
Related Commands
|
Command |
Description |
|---|---|
|
show vpc brief |
Displays information about vPCs. If the feature is not enabled, the system displays an error when you enter this command. |
show vpc role
To display information about the virtual port-channel (vPC) role of the peer device, use the show vpc role command.
show vpc role
Syntax Description
This command has no arguments or keywords.
Defaults
None
Command Modes
Any command mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
4.1(3) |
This command was introduced. |
Usage Guidelines
The show vpc role command displays the following information about the vPC status:
•![]() Status of peer adjacency
Status of peer adjacency
•![]() vPC role of the VDC that you are working on
vPC role of the VDC that you are working on
•![]() vPC MAC address
vPC MAC address
•![]() vPC system priority
vPC system priority
•![]() MAC address of the device that you are working on
MAC address of the device that you are working on
•![]() System priority for the device that you are working on
System priority for the device that you are working on
This command is not available if you have not enabled the vPC feature. See the feature vpc command for information on enabling vPCs.
This command does not require a license.
Examples
This example shows how to display the vPC role information of the device that you are working on:
switch (config)# show vpc role
----------------------------------------------------
Dual Active Detection Status : 0
vPC system-mac : 00:23:04:ee:be:01
vPC system-priority : 32667
vPC local system-mac : 00:22:55:79:ea:c1
vPC local role-priority : 32667
----------------------------------------------------
Dual Active Detection Status : 0
vPC system-mac : 00:23:04:ee:be:01
vPC system-priority : 32667
vPC local system-mac : 00:22:55:79:de:41
vPC local role-priority : 32667
When you reload the primary vPC peer device, the secondary vPC peer device assumes the role of the primary device. The following example shows how the vPC role displays on the new primary device:
switch (config)# show vpc role
----------------------------------------------------
vPC role : secondary, operational primary
Dual Active Detection Status : 0
vPC system-mac : 00:23:04:ee:be:64
vPC system-priority : 32667
vPC local system-mac : 00:22:55:79:de:41
vPC local role-priority : 32667
Related Commands
|
Command |
Description |
|---|---|
|
show vpc brief |
Displays information about vPCs. If the feature is not enabled, the system displays an error when you enter this command. |
|
show port channel summary |
Displays information about port channels. |
show vpc statistics
To display virtual port-channel (vPC) statistics, use the show vpc statistics command.
show vpc statistics {peer-keepalive | peer-link | vpc number}
Syntax Description[
|
peer-keepalive |
Displays statistics about the peer-keepalive message. |
|
peer-link |
Displays statistics about the peer link. |
|
vpc number |
Displays statistics about the specified vPC. The range is from 1 to 4096. |
Defaults
None
Command Modes
Any command mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
4.1(3) |
This command was introduced. |
Usage Guidelines
The peer-link parameter displays the same information as the show interface port-channel channel number command for the vPC peer-link port channel.
The vpc number parameter displays the same information as the show interface port-channel channel number command for the specified vPC port channel.
This command is not available if you have not enabled the vPC feature. See the feature vpc command for information on enabling vPCs.
This command does not require a license.
Examples
This example shows how to display statistics about the peer-keepalive message:
switch# show vpc statistics peer-keepalive
vPC keep-alive status : peer is alive
VPC keep-alive statistics
----------------------------------------------------
peer-keepalive tx count: 1036
peer-keepalive rx count: 1028
average interval for peer rx: 995
Count of peer state changes: 1
Related Commands
|
Command |
Description |
|---|---|
|
show vpc brief |
Displays information about vPCs. If the feature is not enabled, the system displays an error when you enter this command. |
|
show port channel summary |
Displays information about port channels. |
shutdown
To bring the port administratively down, use the shutdown command. To bring the port administratively up, use the no shutdown command.
shutdown [force]
no shutdown [force]
Syntax Description
|
force |
(Optional) Forces the interface state to change. When you shut down a management interface, a warning question is displayed regarding active Telnet sessions. You can bypass the question with the force option. The force option is also useful when you run an automated configuration playback. The force option is only available for Ethernet interfaces or the management port. |
Defaults
None
Command Modes
Interface configuration mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
4.0 |
This command was introduced. |
Usage Guidelines
Use the shutdown command to bring the port administratively down. Use the no shutdown command to bring the port administratively up.
This command does not require a license.
Examples
This example shows how to bring the port administratively down:
switch(config-if)# shutdown
This example shows how to bring the port administratively up:
switch(config-if)# no shutdown
Related Commands
|
Command |
Description |
|---|---|
|
interface ethernet |
Configures the types and identities of Ethernet interfaces. |
speed
To set the speed for Ethernet ports or management interfaces or set the port to autonegotiate its speed with other ports on the link, use the speed command.
speed {10 | 100 | 1000 | 10000 | auto [10 [100 [1000]]]}
Syntax Description
|
10 |
Sets the speed at 10 Mbps. |
|
100 |
Sets the speed at 100 Mbps. |
|
1000 |
Sets the speed at 1 Gbps. |
|
10000 |
Sets the speed at 10 Gbps. |
|
auto |
Sets the interface to autonegotiation. |
Defaults
None
Command Modes
Interface configuration mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
4.0 |
This command was introduced. |
Usage Guidelines
Before you begin, make sure that the remote port has a speed setting that supports your changes for the local port. If you want to set the local port to use a specific speed, you must set the remote port for the same speed or set the local port to autonegotiate the speed.
The interface speed and duplex mode are interrelated, so you should configure both of their parameters at the same time.
The interface speed that you specify can affect the duplex mode used for an interface, so you should set the speed before setting the duplex mode. If you set the speed for autonegotiation, the duplex mode is automatically set to be autonegotiated. If you specify 10- or 100-Mbps speed, the port is automatically configured to use half-duplex mode, but you can specify full-duplex mode instead. If you specify a speed of 1000 Mbps (1 Gbps) or faster, full duplex is automatically used. For more details about configuring this command, see the Cisco NX-OS Interfaces Configuration Guide.
This command does not require a license.
Examples
This example shows how to set the speed of Ethernet port 1 on the 48-port 10/100/1000 module in slot 3 to 1000 Mbps and full-duplex mode:
switch(config)# interface ethernet 3/1
switch(config-if)# speed 1000
switch(config-if)# duplex full
Related Commands
|
Command |
Description |
|---|---|
|
duplex |
Specifies the duplex mode as full, half, or autonegotiate. |
|
show interface |
Displays the interface status, which includes the speed parameters. |
state enabled
To enable the specified port profile, use the state enabled command. To return to the default value, use the no form of this command.
state enabled
no state enabled
Syntax Description
This command has no keywords or arguments.
Defaults
Disabled
Command Modes
Port-profile configuration mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|
4.2(1) |
This command was introduced. |
Usage Guidelines
Use the state enabled command to enable the specified port profile. See the port-profile command for information about the port-profile feature.
To apply the port-profile configurations to the interfaces, you must enable the specific port profile. You can configure and inherit a port profile onto a range of interfaces prior to enabling the port profile; you would then enable that port profile for the configurations to take effect on the specified interfaces. The maximum number of interfaces that can inherit a single profile is 512.
If you inherit one or more port profiles onto an original port profile, only the last inherited port profile must be enabled; the system assumes that the underlying port profiles are enabled.
This command does not require a license.
Examples
This example shows how to enable the port-profile feature:
switch(config)# port-profile type ethernet test
switch(config-ppm)# state enabled
Related Commands
|
Command |
Description |
|---|---|
|
show port-profile |
Displays information about the port profiles. |
switchport
To set the interface as a Layer 2 switching port, use the switchport command. To return the interface to the default Layer 3 routed interface status and cause all Layer 2 configuration to be erased, use the no form of this command.
switchport
no switchport
Syntax Description
This command has no keywords or arguments.
Defaults
Interfaces are Layer 3 by default.
Command Modes
Interface configuration mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|
4.0 |
This command was introduced. |
Usage Guidelines
You must enter the switchport command without any keywords to configure the LAN interface as a Layer 2 interface before you can enter additional switchport commands with keywords. This action is required only if you have not entered the switchport command for the interface.
The default switchport mode is the access mode. Use the switchport mode command to do the following:
•![]() Set the interface to the Layer 2 access mode
Set the interface to the Layer 2 access mode
•![]() Return the interface to the Layer 2 trunk mode
Return the interface to the Layer 2 trunk mode
•![]() Use the interface with private VLANs.
Use the interface with private VLANs.
Enter the no switchport command to shut down the port and then reenable it. This action may generate messages on the device to which the port is connected.
When you use the no switchport command, all the Layer 2 configuration is deleted from that interface, and the interface has the default VLAN configuration.
The port goes down and reinitializes when you change the interface mode.
This command does not require a license.
Examples
This example shows how to cause a port interface to stop operating as a Cisco routed port and convert to a Layer 2 switched interface:
switch(config-if)# switchport
Related Commands
|
Command |
Description |
|---|---|
|
show interface switchport |
Displays the administrative and operational status of a switching (nonrouting) port. |
switchport access vlan
To set the access VLAN when the interface is in access mode, use the switchport access vlan command. To reset the access-mode VLAN to the appropriate default VLAN for the device, use the no form of this command.
switchport access vlan vlan-id
no switchport access vlan
Syntax Description
|
vlan-id |
VLAN to set when the interface is in access mode; valid values are from 1 to 4094, except for the VLANs reserved for internal switch use. |
Defaults
VLAN1
Command Modes
Interface configuration mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|
4.0 |
This command was introduced. |
Usage Guidelines
You must enter the switchport command without any keywords to configure the LAN interface as a Layer 2 interface before you can enter the switchport access vlan command. This action is required only if you have not entered the switchport command for the interface.
Enter the no switchport access vlan command to shut down the port and then reenable it. This action may generate messages on the device to which the port is connected.
Use the no form of the switchport access vlan command to reset the access-mode VLAN to the appropriate default VLAN for the device.
This command does not require a license.
Examples
This example shows how to cause a port interface that has already been configured as a switched interface to operate as an access port in VLAN 2 instead of the platform’s default VLAN in the interface-configuration mode:
switch(config-if)# switchport access vlan 2
Related Commands
|
Command |
Description |
|---|---|
|
show interface switchport |
Displays the administrative and operational status of a switching (nonrouting) port. |
switchport autostate exclude
To exclude an aceess port or trunk from the VLAN interface link-up calculation on the Cisco NX-OS device, use the switchport autostate exclude command. To revert to the default settings, use the no form of this command.
switchport autostate exclude
no switchport autostate exclude
Syntax Description
This command has no keywords or arguments.
Defaults
All ports are included in the VLAN interface link-up calculation.
Command Modes
Interface configuration
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
5.0 |
This command was introduced. |
Usage Guidelines
The switchport autostate exclude command marks the port to be excluded from the interface VLAN up calculation when there are multiple ports in the VLAN.
The show interface interface switchport command displays the autostate mode if the mode has been set. If the mode has not been set, the autostate mode is not displayed.
This command does not require a license.
Examples
This example shows how to exclude a port from the VLAN interface link-up calculation on the Cisco NX-OS device:
switch# configure terminal
switch(config)# interface ethernet 1/1
switch(config-if)# switchport
switch(config-if)# switchport autostate exclude
This example shows how to include all ports in the VLAN interface link-up calculation on the Cisco NX-OS device:
switch(config-if)# no switchport autostate exclude
Related Commands
|
Command |
Description |
|---|---|
|
switchport |
Configures the interface as a Layer 2 switching port. |
|
show interface switchport |
Displays the administrative and operational status of a switching (nonrouting) port. |
switchport dot1q ethertype
To set the EtherType used for Q-in-Q encapsulation on an interface, use the switchport dot1q ethertype command. To reset the EtherType to its default value, Use the no form of this command.
switchport dot1q ethertype ethertype
no switchport dot1q ethertype [ethertype]
Syntax Description
|
ethertype |
Value to set for the EtherType. The range is from 0x600 to 0xffff. • • • |
Defaults
0x8100 is the default EtherType for 802.1q frames
Command Modes
Interface configuration mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|
5.0(2) |
This command was introduced. |
Usage Guidelines
You must enter the switchport command without any keywords to configure the Ethernet interface as a Layer 2 interface before you can enter the switchport mode command. This action is required only if you have not entered the switchport command for the interface.
You must set the EtherType only on the egress trunk interface that carries double tagged frames (the trunk interface that connects the service providers). If you change the EtherType on one side of the trunk, you must set the same value on the other end of the trunk (symmetrical configuration).

Caution
![]() The EtherType value you set affects all the tagged packets going out on the interface (not just Q-in-Q packets).
The EtherType value you set affects all the tagged packets going out on the interface (not just Q-in-Q packets).
This command does not require a license.
Examples
This example shows how to create a 802.1Q tunnel on an interface:
switch(config-if)# switchport dot1q ethertype 0x9100
Related Commands
|
Command |
Description |
|---|---|
|
show interface switchport |
Displays information about all the switch port interfaces. |
switchport host
To configure a port that is not connected to any other devices as a Layer 2 access port with optimized packet forwarding, use the switchport host command. To disable a port that is not connected to any other devices as a Layer 2 access, use the no form of this command.
switchport host
no switchport host
Syntax Description
This command has no keywords or arguments.
Defaults
Interfaces are Layer 3 by default.
Command Modes
Interface configuration mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|
4.0 |
This command was introduced. |
Usage Guidelines
You must enter the switchport command without any keywords to configure the LAN interface as a Layer 2 interface before you can enter the switchport host command. This action is required only if you have not entered the switchport command for the interface.
Entering the switchport host command on an interface:
•![]() Makes the Layer 2 interface an access port.
Makes the Layer 2 interface an access port.
•![]() Makes the Layer 2 interface an STP edge port, which decreases the time that it takes to start up packet forwarding.
Makes the Layer 2 interface an STP edge port, which decreases the time that it takes to start up packet forwarding.
•![]() Disables port channeling on this interface.
Disables port channeling on this interface.
You should enter the switchport host command only on ports that are connected to a single host. When you use this command with an interface connected to other than a single host, the device returns an error message.
To optimize the port configuration, entering the switchport host command sets the switch port mode to access and disables channel grouping. Only an end station can accept this configuration.
This command toggles the port if it is in the UP state.
This command does not require a license.
Examples
This example shows how to optimize an access port configuration for a host connection:
switch(config-if)# switchport host
Related Commands
|
Command |
Description |
|---|---|
|
show interface switchport |
Displays the administrative and operational status of a switching (nonrouting) port. |
switchport mode
To set the Layer 2 interface type, use the switchport mode command. To return the interface to the Layer 2 access mode, use the no form of this command.
switchport mode {access | dot1q-tunnel | fabricpath | fex-fabric | private-vlan {host | promiscuous | trunk [promiscuous | secondary]}| trunk}
no switchport mode
Syntax Description
|
access |
Specifies the interface as a nontrunking, nontagged single-VLAN Layer 2 interface. An access port carries traffic in one VLAN only. |
|
dot1q-tunnel |
Creates a 802.1Q tunnel on the interface. |
|
fabricpath |
Specifies the port mode as FabricPath. |
|
fex-fabric |
Sets the interface type to be an uplink port for a Fabric Extender. |
|
private-vlan |
Sets the port mode as a private-VLAN (PVLAN) host or promiscuous. |
|
host |
Sets the port mode as the PVLAN host. |
|
promiscuous |
(Optional) Sets the port mode as PVLAN promiscuous. |
|
secondary |
Sets the port mode trunk as isolated. |
|
trunk |
Specifies the trunking VLAN interface in Layer 2. A trunk port can carry traffic in one or more VLANs (based on the trunk allowed VLAN list configuration) on the same physical link. |
Defaults
access ports
Command Modes
Interface configuration mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|
5.2(1) |
Added the dot1q-tunnel, fabricpath, fex-fabric, private-vlan, host, promiscuous, and secondary keywords. |
|
4.0 |
This command was introduced. |
Usage Guidelines
You must enter the switchport command without any keywords to configure the LAN interface as a Layer 2 interface before you can enter the switchport mode command. This action is required only if you have not entered the switchport command for the interface.
If you enter access mode, the interface goes into nontrunking mode; if you enter trunk mode, the interface goes into trunking mode.
To correctly deliver the traffic on a trunk port with several VLANs, the switch uses the IEEE 802.1Q encapsulation, or tagging, method. If an access port receives a packet with an 802.1Q tag in the header, that port drops the packet without learning its MAC source address.

Note ![]() A port can function as either an access port, a trunk port, or a private VLAN port; a port cannot function as all three simultaneously.
A port can function as either an access port, a trunk port, or a private VLAN port; a port cannot function as all three simultaneously.
The port goes down and reinitializes when you change the interface mode.
This command does not require a license.
Examples
This example shows how to set the interface to trunking mode:
switch(config-if)# switchport mode trunk
Related Commands
|
Command |
Description |
|---|---|
|
show interface switchport |
Displays the administrative and operational status of a switching (nonrouting) port. |
switchport mode dot1q-tunnel
To creates an 802.1Q tunnel on an interface, use the switchport mode dot1q-tunnel command. To disable the 802.1Q tunnel on the interface, use the no form of this command.
switchport mode dot1q-tunnel
no switchport mode dot1q-tunnel
Syntax Description
This command has no arguments or keywords.
Defaults
No 802.1Q tunnel
Command Modes
Interface configuration mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|
5.0(2) |
This command was introduced. |
Usage Guidelines
You must enter the switchport command without any keywords to configure the Ethernet interface as a Layer 2 interface before you can enter the switchport mode command. This action is required only if you have not entered the switchport command for the interface.
The port goes down and reinitializes (port flap) when the interface mode is changed. BPDU filtering is enabled and the Cisco Discovery Protocol (CDP) is disabled on tunnel interfaces.
This command does not require a license.
Examples
This example shows how to create a 802.1Q tunnel on an interface:
switch(config-if)# switchport mode dot1q-tunnel
Related Commands
|
Command |
Description |
|---|---|
|
switchport mode fex-fabric |
Sets the interface type to be an uplink port for a Fabric Extender. |
switchport mode fex-fabric
To set the interface type to be an uplink port for a Fabric Extender, use the switchport mode fex-fabric command. To return to the default setting, use the no form of this command.
switchport mode fex-fabric
no switchport mode fex-fabric
Syntax Description
This command has no arguments or keywords.
Defaults
None
Command Modes
Interface configuration mode
Command History
|
Release |
Modification |
|
5.1(1) |
This command was introduced. |
Usage Guidelines
This command does not require a license.
Examples
This example shows how to set an Ethernet interface to be an uplink port for a Fabric Extender:
switch# configure terminal
switch(config)# interface ethernet 1/40
switch(config-if)# switchport mode fex-fabric
This example shows how to set an EtherChannel interface to be an uplink port for a Fabric Extender:
switch# configure terminal
switch(config)# interface port-channel 4
switch(config-if)# switchport mode fex-fabric
Related Commands
|
Command |
Description |
|---|---|
|
fex associate |
Associates a Fabric Extender to an Ethernet or EtherChannel interface. |
|
show fex |
Displays all configured Fabric Extender chassis connected to the switch. |
switchport trunk allowed vlan
To set the list of allowed VLANs on the trunking interface, use the switchport trunk allowed vlan command. To allow all VLANs on the trunking interface, use the no form of this command.
switchport trunk allowed vlan {vlan-list | add vlan-list | all | except vlan-list | none | remove vlan-list}
no switchport trunk allowed vlan
Syntax Description
|
vlan-list |
Allowed VLANs that transmit through this interface in tagged format when in trunking mode; the range of valid values is from 1 to 4094. |
|
add |
Adds the defined list of VLANs to those currently set instead of replacing the list. |
|
all |
Allows all appropriate VLANs to transmit through this interface in tagged format when in trunking mode. |
|
except |
Allows all VLANs to transmit through this interface in tagged format when in trunking mode except the specified values. |
|
none |
Blocks all VLANs transmitting through this interface in tagged format when in trunking mode. |
|
remove |
Removes the defined list of VLANs from those currently set instead of replacing the list. |
Defaults
All VLANs
Command Modes
Interface configuration mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|
4.0 |
This command was introduced. |
Usage Guidelines
You must enter the switchport command without any keywords to configure the LAN interface as a Layer 2 interface before you can enter the switchport trunk allowed vlan command. This action is required only if you have not entered the switchport command for the interface.
You can enter the switchport trunk allowed vlan command on interfaces where the Switched Port Analyzer (SPAN) destination port is either a trunk or an access port.
If you remove VLAN 1 from a trunk, the trunk interface continues to send and receive management traffic in VLAN 1.
This command does not require a license.
Examples
This example shows how to add a series of consecutive VLANs to the list of allowed VLANs on a trunking port:
switch(config-if)# switchport trunk allowed vlan add 40-50
Related Commands
|
Command |
Description |
|---|---|
|
show interface switchport |
Displays the administrative and operational status of a switching (nonrouting) port. |
switchport trunk native vlan
To change the native VLAN ID when the interface is in trunking mode, use the switchport trunk native vlan command. To return the native VLAN ID to VLAN 1, use the no form of this command.
switchport trunk native vlan vlan-id
no switchport trunk native vlan
Syntax Description
|
vlan-id |
Native VLAN for the trunk in 802.1Q trunking mode. The range is from 1 to 4094, except the internally reserved VLANs are 3968 to 4047 and 4094. |
Defaults
VLAN1
Command Modes
Interface configuration mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|
4.0 |
This command was introduced. |
Usage Guidelines
You must enter the switchport command without any keywords to configure the LAN interface as a Layer 2 interface before you can enter the switchport trunk native vlan command. This action is required only if you have not entered the switchport command for the interface.

Note ![]() See the vlandot1q tag native command for more information about configuring the native VLAN for 802,1Q trunk ports.
See the vlandot1q tag native command for more information about configuring the native VLAN for 802,1Q trunk ports.
Use the no form of the native vlan command to reset the native mode VLAN to the default VLAN1 for the device.
This command does not require a license.
Examples
This example shows how to configure the native VLAN for an interface in trunk mode:
switch(config-if)# switchport trunk native vlan 5
Related Commands
|
Command |
Description |
|---|---|
|
show interface switchport |
Displays the administrative and operational status of a switching (nonrouting) port. |
system default switchport
To change the default interface mode for the system from Layer 3 routing to Layer 2 switching, use the system default switchport command. To return the system to Layer 3 routing default interface mode, use the no form of this command.
system default switchport [fabricpath | shutdown]
no system default switchport [fabricpath | shutdown]
Syntax Description
|
fabricpath |
(Optional) Configures the default port mode as FabricPath. |
|
shutdown |
(Optional) Configures the administrative state as down. |
Defaults
None
Command Modes
Global configuration mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|
5.2(1) |
Added the fabricpath keyword. |
|
4.0 |
This command was introduced. |
Usage Guidelines
The system default switchport command makes all the interfaces Layer 2 access ports.
This command does not require a license.
Examples
This example shows how to configure the system so that all the interfaces are in Layer 2 access mode:
switch(config-if)# system default switchport
Related Commands
|
Command |
Description |
|---|---|
|
show interface switchport |
Displays the administrative and operational status of a switching (nonrouting) port. |
system jumbomtu
To configure the system jumbo maximum transmission unit (MTU) size for Layer 2 interfaces, use the system jumbomtu command.
system jumbomtu size
Syntax Description
|
size |
Even number between 1500 and 9216. |
Defaults
The system jumbo MTU default size is 9216 bytes and the interface default MTU is 1500 bytes.
Command Modes
Global configuration mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
4.0 |
This command was introduced. |
Usage Guidelines
Use the system jumbomtu command to specify the MTU size for Layer 2 interfaces. The range is from 1500 to 9216.
The physical level uses an unchangeable bandwidth of 1 GB.
This command does not require a license.
Examples
This example shows how to configure the system jumbo MTU as 8000 bytes and how to change the MTU specification for an interface that was configured with the previous jumbo MTU size:
switch(config)# system jumbomtu 8000
switch(config)# show running-config
switch(config)# interface ethernet 2/2
switch(config-if)# switchport
switch(config-if)# mtu 4608
Related Commands
|
Command |
Description |
|---|---|
|
show running-config |
Displays the current operating configuration, which includes the system jumbo MTU size. |
system-mac
To overwrite the MAC address that the device creates for the virtual port-channel (vPC) domain when you create a vPC domain, use the system-mac command. To return to the default vPC system MAC address, use the no form of this command.
system-mac mac-address
no system-mac
Syntax Description[
|
mac-address |
MAC address that you want for the vPC domain using the format xxxx.xxxx.xxxx. |
Defaults
None
Defaults
vpc-domain command mod.
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
4.1(3) |
This command was introduced. |
Usage Guidelines
You must enable the vPC feature before you can create a vPC system MAC address.
Use the system-mac command to overwrite the MAC address created by the system once you create a vPC domain. By default, the system creates a MAC address for the vPC when you create a vPC domain based on the domain ID. Cisco reserved a range of MAC addresses from the IEEE for this purpose and these addresses are used to complete the last 10 bits of the vPC domain MAC address. The range of default MAC addresses is as follows:
•![]() Number of reserved MAC addresses—1024
Number of reserved MAC addresses—1024
•![]() Starting—002304eebe00
Starting—002304eebe00
•![]() Ending—002304eec1ff
Ending—002304eec1ff
This command does not require a license.
Examples
This example shows how to create a vPC system MAC address:
switch(config)# vpc domain 5
switch(config-vpc-domain)# system-mac 22cd.34ab.ca32
Related Commands
|
Command |
Description |
|---|---|
|
show vpc role |
Displays the system MAC address for the vPC domain. |
system-priority
To overwrite the system priority that the device creates for the virtual port-channel (vPC) domain when you create a vPC domain, use the system-priority command. To return to the default vPC system priority, use the no form of this command.
system-priority priority
no system-priority priority
Syntax Description[
|
priority |
System priority. The range is from 1 to 65535. |
Defaults
32667
Command Modes
vpc-domain command mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
4.1(3) |
This command was introduced. |
Usage Guidelines
You must enable the vPC feature before you can create a vPC system priority.

Note ![]() We recommend that you manually configure the vPC system priority when you are running LACP to ensure that the vPC peer devices are the primary devices on LACP.
We recommend that you manually configure the vPC system priority when you are running LACP to ensure that the vPC peer devices are the primary devices on LACP.
This command does not require a license.
Examples
This example shows how to create a vPC system priority:
switch(config)# vpc domain 5
switch(config-vpc-domain)# system-priority 4000
Related Commands
|
Command |
Description |
|---|---|
|
show vpc role |
Displays the system priority for the vPC domain. |
track
To configure the system to monitor the track-list object that contains all the virtual port-channel (vPC) links to the core and to the vPC peer link when you are using only a single module for all links, use the track command. To return to the default, use the no form of this command.
track track-object-id
no track track-object-id
Syntax Description
|
track-object-id |
Track-list object that you already configured. |
Defaults
No tracking
Command Modes
vpc configuration mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
4.2(1) |
This command was introduced. |
Usage Guidelines
Beginning with Release 4.2, if you must configure all the vPC peer links and core-facing interfaces on a single N7K-M132XP-12 module, you should configure a track object and a track list that is associated with the Layer 3 link to the core and on all vPC peer links on both vPC peer devices. You can use this configuration to avoid dropping traffic if that particular module goes down because when all the tracked objects on the track list go down, the system does the following:
•![]() Stops the vPC primary peer device sending peer-keepalive messages, which forces the vPC secondary peer device to take over.
Stops the vPC primary peer device sending peer-keepalive messages, which forces the vPC secondary peer device to take over.
•![]() Brings down all the downstream vPCs on that vPC peer device, which forces all the traffic to be rerouted in the access switch to the other vPC peer device.
Brings down all the downstream vPCs on that vPC peer device, which forces all the traffic to be rerouted in the access switch to the other vPC peer device.
Once you configure this feature and if the module fails, the system automatically suspends all the vPC links on the primary vPC peer device and stops the peer-keepalive messages. This action forces the vPC secondary device to take over the primary role and all the vPC traffic to go to this new vPC primary device until the system stabilizes.
Create a track list that contains all the links to the core and all the vPC peer links as its object. Enable tracking for the specified vPC domain for this track list. Apply this same configuration to the other PC peer device. See the Cisco Nexus 7000 Series NX-OS Unicast Routing Configuration Guide, Release 5.x, for information about configuring object tracking and track lists.
This command does not require a license.
Examples
This example shows how to put the previously configured track-list object into the vPC domain on the vPC peer device:
switch(config)# vpc domain 5
switch(config-vpc-domain)# track object 5
Related Commands
|
Command |
Description |
|---|---|
|
show vpc brief |
Displays information about a vPC tracked object. |
|
feature vpc |
Enables vPCs on the device. |
tunnel destination
To configure the destination endpoint for a tunnel, use the tunnel destination command. To remove the tunnel destination, use the no form of this command.
tunnel destination {ip-address | host-name}
no tunnel destination {ip-address | host-name}
Syntax Description
|
ip-address |
IP address for the tunnel destination. |
|
host-name |
Hostname for the tunnel destination. |
Defaults
None
Command Modes
Interface configuration mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
4.0 |
This command was introduced. |
Usage Guidelines
Use the tunnel destination command to configure the destination address for an IP tunnel.
You should not have two tunnels using the same encapsulation mode with the same source and destination address.
This command requires the Enterprise license.
Examples
This example shows how to configure the tunnel destination:
switch(config-if)# tunnel destination 192.0.2.120
Related Commands
|
Command |
Description |
|---|---|
|
tunnel source |
Sets the source of the IP tunnel. |
|
interface tunnel |
Creates the IP tunnel. |
|
show interface tunnel |
Displays information about the traffic about the specified tunnel interface. |
tunnel mode
To configure the tunnel encapsulation mode for a tunnel, use the tunnel mode command. To restore the default value, use the no form of this command.
tunnel mode gre {ip | ipv6}
no tunnel mode gre {ip | ipv6}
Syntax Description
|
ip |
Configures this tunnel encapsulation mode as IPv4. |
|
ip v6 |
Configures this tunnel encapsulation mode as IPv6. |
Defaults
None
Command Modes
Interface configuration mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
4.0 |
This command was introduced. |
Usage Guidelines
Use the tunnel mode command to configure the tunnel encapsulation mode for a tunnel.
This command requires the Enterprise license.
Examples
This example shows how to configure the tunnel mode:
switch(config-if)# tunnel mode gre ip
Related Commands
|
Command |
Description |
|---|---|
|
tunnel destination |
Sets the destination of the IP tunnel. |
|
interface tunnel |
Creates the IP tunnel. |
|
show interface tunnel |
Displays information about the traffic about the specified tunnel interface. |
tunnel path-mtu-discovery
To enable Path MTU Discovery (PMTUD) on a tunnel interface, use the tunnel path-mtu-discovery command. To disable PMTUD on a tunnel interface, use the no form of this command.
tunnel path-mtu-discovery [age-timer {aging-mins | infinite} | min-mtu mtu-bytes]
no tunnel path-mtu-discovery [age-timer {aging-mins | infinite} | min-mtu mtu-bytes]
Syntax Description
|
age-timer |
(Optional) Sets a timer to run for a specified interval, in minutes, after which the tunnel interface resets the maximum transmission unit (MTU) of the path to the default tunnel MTU minus 24 bytes for GRE tunnels or minus 20 bytes for IP-in-IP tunnels. |
|
aging-mins |
Number of minutes. The range is from 10 to 30. The default is 10. |
|
infinite |
Disables the age timer. |
|
min-mtu mtu-bytes |
(Optional) Specifies the minimum Path MTU across GRE tunnels. The range is from 92 to 65535 bytes. The default is 92. |
Defaults
Disabled
Command Modes
Interface configuration mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
4.0 |
This command was introduced. |
Usage Guidelines
When PMTUD (RFC 1191) is enabled on a tunnel interface, the router performs PMTUD processing for the tunnel IP packets. The router always performs PMTUD processing on the original data IP packets that enter the tunnel. When PMTUD is enabled, no packet fragmentation occurs on the encapsulated packets that travel through the tunnel. Without packet fragmentation, there is a better throughput of TCP connections. PMTUD maximizes the use of available bandwidth in the network between the endpoints of a tunnel interface.
After PMTUD is enabled, the Don’t Fragment (DF) bit of the IP packet header that is forwarded into the tunnel is copied to the IP header of the external IP packets. The external IP packet is the encapsulating IP packet. Adding the DF bit allows the PMTUD mechanism to work on the tunnel path of the tunnel. The tunnel endpoint listens for Internet Control Message Protocol (ICMP) unreachable too-big messages and modifies the IP MTU of the tunnel interface, if required.
When the aging timer is configured, the tunnel code resets the tunnel MTU after the aging timer expires. After the tunnel MTU is reset, a set of full-size packets with the DF bit set is required to trigger the tunnel PMTUD and lower the tunnel MTU. At least two packets are dropped each time that the tunnel MTU changes.
When PMTUD is disabled, the DF bit of an external (encapsulated) IP packet is set to zero even if the encapsulated packet has a DF bit set to one.
The min-mtu keyword sets a low limit through the MTU that can be learned through the PMTUD process. Any ICMP signal received that specifies an MTU less than the minimum MTU configured is ignored. You can use this feature to prevent a denial- of-service attack from any node that can send an ICMP message to the router that specifies a very small MTU.

Note ![]() PMTUD on a tunnel interface requires that the tunnel endpoint is able to receive ICMP messages generated by routers in the path of the tunnel. You should check that ICMP messages can be received before you use PMTUD over firewall connections.
PMTUD on a tunnel interface requires that the tunnel endpoint is able to receive ICMP messages generated by routers in the path of the tunnel. You should check that ICMP messages can be received before you use PMTUD over firewall connections.
This command requires the Enterprise license.
Examples
This example shows how to configure PMTUD:
switch(config-if)# tunnel path-mtu-discovery
Related Commands
|
Command |
Description |
|---|---|
|
tunnel destination |
Sets the destination of the IP tunnel. |
|
interface tunnel |
Creates the IP tunnel. |
|
show interface tunnel |
Displays information about the traffic about the specified tunnel interface. |
tunnel source
To configure the source endpoint for a tunnel, use the tunnel source command. To remove the tunnel source, use the no form of this command.
tunnel source {ip-address | interface-type number}
no tunnel source [ip-address | interface-type number]
Syntax Description
|
ip-address |
IP address for the tunnel source. |
|
interface-type number |
Interface for the tunnel source. |
Defaults
None
Command Modes
Interface configuration mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
4.0 |
This command was introduced. |
Usage Guidelines
Use the tunnel source command to configure the source address for an IP tunnel.
You should not have two tunnels using the same encapsulation mode with the same source and destination address.
This command requires the Enterprise license.
Examples
This example shows how to set the tunnel source:
switch(config-if)# tunnel source 192.0.2.120
Related Commands
|
Command |
Description |
|---|---|
|
tunnel destination |
Sets the destination of the IP tunnel. |
|
interface tunnel |
Creates the IP tunnel. |
|
show interface tunnel |
Displays information about the traffic about the specified tunnel interface. |
tunnel use-vrf
To specify which virtual routing and forwarding (VRF) instance to use to look up a tunnel destination IP address, use the tunnel use-vrf command. To return to the default, use the no form of this command.
tunnel use-vrf vrf-name
no tunnel use-vrf vrf-name
Syntax Description
|
vrf-name |
Name of the VRF in which to look up the tunnel destination IP address. |
Defaults
Default VRF
Command Modes
Interface configuration mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
4.2(1) |
This command was introduced. |
Usage Guidelines
You should have the tunnel interface and tunnel destination IP address in the same VRF. You should have the same value for the vrf-name parameter in both the vrf member and tunnel use-vrf command.
This command requires the Enterprise license.
Examples
This example shows how to specify the VRF in which to look up the tunnel destination IP address:
switch(config-if)# tunnel use-vrf blue
Related Commands
|
Command |
Description |
|---|---|
|
show interface tunnel |
Displays information about the traffic about the specified tunnel interface. |
|
show vrf interface tunnel |
Displays information about the VRF tunnel interface. |
tunnel ttl
To configure the time-to-live value for a tunnel, use the tunnel ttl command. To restore the default value, use the no form of this command.
tunnel ttl value
no tunnel ttl [value]
Syntax Description
|
value |
Time-to-live value for the tunnel. The range is from 1 to 255. |
Defaults
None
Command Modes
Interface configuration mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
4.0 |
This command was introduced. |
Usage Guidelines
Use the tunnel ttl command to configure the time-to-live value for an IP tunnel.
This command requires the Enterprise license.
Examples
This example shows how to configure the time-to-live value for a tunnel interface:
switch(config-if)# tunnel ttl 30
Related Commands
|
Command |
Description |
|---|---|
|
tunnel destination |
Sets the destination of the IP tunnel. |
|
interface tunnel |
Creates the IP tunnel. |
|
show interface tunnel |
Displays information about the traffic about the specified tunnel interface. |
type
To set the Fabric Extender (FEX) card type to a specific card, use the type command. To revert to the default FEX card, use the no form of this command
type fex-card-type
no type
Syntax Description
|
fex-card-type |
Fabric Extender card type. The following Fabric Extender card types are supported: · N2148T Fabric Extender 48x1G 4x10G Module · N2248T Fabric Extender 48x1G 4x10G Module |
Defaults
None
Command Modes
Fabric Extender configuration mode
Command History
|
Release |
Modification |
|---|---|
|
5.1(1) |
This command was introduced. |
Usage Guidelines
This command does not require a license.
Examples
This example shows how to configure the Fabric Extender card:
switch(config-fex)# type N2148T
Related Commands
|
Command |
Description |
|---|---|
|
fex |
Creates a Fabric Extender and enters fabric extender configuration mode. |
|
show fex |
Displays all configured Fabric Extender chassis connected to the switch. |
udld
To configure the interfaces to use a Unidirectional Link Detection (UDLD) mode, use the udld command.
udld {enable | disable}
Syntax Description
|
disable |
Disables the UDLD mode for fiber interfaces. |
|
enable |
Enables the normal UDLD mode for nonfiber interfaces. |
Defaults
By default, UDLD is disabled for the 48-port, 10/100/1000-Ethernet module ports.
By default, UDLD is enabled for the 32-port, 10-Gigabit Ethernet module ports.
Command Modes
Interface configuration mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
4.0 |
This command was introduced. |
Usage Guidelines
Before you can enable a UDLD mode for specified interfaces, you must make sure that UDLD is already enabled globally on the device. Use the feature udld command to enable UDLD globally.
Use the udld command to enable or disable UDLD separately on specified interfaces. This action enables UDLD in normal mode. Enter the udld aggressive command to enable the aggressive mode on UDLD-enabled interfaces.
This command does not require a license.
Examples
This example shows how to enable the normal UDLD mode for Ethernet port 3/1:
switch(config)# feature udld
switch(config)# interface ethernet 3/1
switch(config-if)# udld enable
This example shows how to disable UDLD for Ethernet port 3/1:
switch(config)# interface ethernet 3/1
switch(config-if-range)# udld disable
Related Commands
|
Command |
Description |
|---|---|
|
feature udld |
Enables UDLD globally on the device. |
|
show udld |
Displays information about the UDLD configuration. |
udld aggressive
To configure the interfaces for aggressive Unidirectional Link Detection (UDLD) mode, use the udld aggressive command.
udld aggressive
Syntax Description
This command has no arguments or keywords.
Defaults
None
Command Modes
Interface configuration mode
Global configuration mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
4.0 |
This command was introduced. |
Usage Guidelines
Before you can enable the aggressive UDLD mode for an interface, you must make sure that UDLD is already enabled globally on the device and on the specified interfaces.
Use the udld aggressive command to configure the ports to use a UDLD mode:
•![]() To enable fiber interfaces for the aggressive mode, enter the udld aggressive command in the global command mode and all the fiber interfaces will be in aggressive UDLD mode,
To enable fiber interfaces for the aggressive mode, enter the udld aggressive command in the global command mode and all the fiber interfaces will be in aggressive UDLD mode,
•![]() To enable the copper interfaces for the aggressive, you must enter the udld aggressive command in the interface mode, specifying each interface you want in aggressive UDLD mode.
To enable the copper interfaces for the aggressive, you must enter the udld aggressive command in the interface mode, specifying each interface you want in aggressive UDLD mode.
To use the aggressive UDLD mode, you must configure the interfaces on both ends of the link for the aggressive UDLD mode.
This command does not require a license.
Examples
This example shows how to enable fiber interfaces for the aggressive UDLD mode:
switch(config)# udld aggressive
This example shows how to enable the aggressive UDLD mode for the copper Ethernet interface 3/1:
switch(config)# interface ethernet 3/1
switch(config-if)# udld aggressive
Related Commands
|
Command |
Description |
|---|---|
|
feature udld |
Enables UDLD globally for the device. |
|
show udld |
Displays information about the UDLD configuration. |
udld message-time
To set the Unidirectional Link Detection (UDLD) message interval timer, use the udld message-time command.
udld message-time seconds
Syntax Description
|
seconds |
Number of seconds that you want between sending UDLD messages. The range is from 7 to 90 seconds. |
Defaults
15 seconds
Command Modes
Global configuration mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
4.0 |
This command was introduced. |
Usage Guidelines
Before you can set the UDLD message timer, you must make sure that UDLD is already enabled globally on the device. Use the feature udld command to globally enable UDLD.
This command does not require a license.
Examples
This example shows how to configure UDLD interval to 30 seconds:
switch(config)# udld message-time 30
Related Commands
|
Command |
Description |
|---|---|
|
feature udld |
Enables UDLD globally for the device. |
|
show udld |
Displays information about the UDLD configuration. |
udld reset
To reset the interfaces that Unidirectional Link Detection (UDLD) has shut down and return them to the UP condition, use the udld reset command.
udld reset
Syntax Description
This command has no arguments or keywords.
Defaults
None
Command Modes
Global configuration mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
4.0 |
This command was introduced. |
Usage Guidelines
This command does not require a license.
Examples
This example shows how to reset those interfaces that UDLD has shut down:
switch(config)# udld reset
Related Commands
|
Command |
Description |
|---|---|
|
feature udld |
Enables UDLD globally for the device. |
|
show udld |
Displays information about the UDLD configuration. |
vlan dot1q tag native
To enable dot1q (IEEE 802.1Q) tagging for the native VLAN in a trunk, use the vlan dot1q tag native command. To return to the default where no packets are tagged in the native VLAN in a trunk, use the no form of this command.
vlan dot1q tag native
no vlan dot1q tag native
Syntax Description
This command has no arguments or keywords.
Defaults
Disabled
Command Modes
Global configuration mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
4.0 |
This command was introduced. |
Usage Guidelines
Typically, you configure 802.1Q trunks with a native VLAN ID, which strips tagging from all packets on that VLAN and allows all untagged traffic and control traffic to transit the switch. Packets that enter the switch with 802.1Q tags that match the native VLAN ID value are similarly stripped of tagging. If you choose to maintain the tagging on the native VLAN and drop untagged traffic, enter the vlan dot1q tag native command.
Use the vlan dot1q tag native command to configure the switch to tag the traffic received on the native VLAN and to admit only the 802.1Q-tagged frame, dropping any untagged traffic, including untagged traffic in the native VLAN. Control traffic continues to be accepted untagged on the native VLAN on a trunked port, even when the vlan dot1q tag native command is enabled.
Use this command to enable the tagging behavior on all native VLANs on all trunked ports on the switch.

Note ![]() If you enable 802.1Q tagging on one switch and disable it on another switch, all traffic is dropped; you must identically configure 802.1Q tagging on each switch.
If you enable 802.1Q tagging on one switch and disable it on another switch, all traffic is dropped; you must identically configure 802.1Q tagging on each switch.
This command does not require a license.
Examples
This example shows how to enable dot1q tagging for all VLANs on all trunk ports on the switch:
switch(config)# vlan dot1q tag native
Related Commands
|
Command |
Description |
|---|---|
|
show vlan dot1q tag native |
Displays native VLAN-tagging information. |
vpc
To move other port channels into the virtual port channel (vPC), use the vpc command. To remove a port channel from the vPC, use the no form of this command.
vpc number
no vpc number
Syntax Description
|
number |
Number for the vPC. The range is from 1 to 4096. |
Defaults
None
Command Modes
Interface command mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
4.1(3) |
This command was introduced. |
Usage Guidelines
You must enable the vPC feature before you can create a vPC.
Once you have created the vPC domain ID and the vPC peer link, you create port channels to attach the downstream device to each vPC peer device. That is, you create one port channel from the downstream device to the primary vPC peer device and you create another port channel from the downstream device to the secondary peer device. Finally, working on each vPC peer device, you assign a vPC number to the port channel that connects to the downstream device. You will experience minimal traffic disruption when you are creating vPCs.

Note ![]() The vPC number that you assign to the port channel connecting to the downstream device from the vPC peer device must be identical on both vPC peer devices.
The vPC number that you assign to the port channel connecting to the downstream device from the vPC peer device must be identical on both vPC peer devices.
This command does not require a license.
Examples
This example shows how to move a port channel into the vPC:
switch (config)# interface port-channel 10
switch (config-if)# vpc 100
Related Commands
|
Command |
Description |
|---|---|
|
show vpc brief |
Displays information about vPCs. If the feature is not enabled, the system displays an error when you enter this command. |
vpc domain
To create a virtual port-channel (vPC) domain, use the vpc domain command. To remove a vPC domain, use the no form of this command.
vpc domain domain-id
no vpc domain domain-id
Syntax Description
|
domain-id |
Domain ID for the vPC. The range of numbers is from 1 to 1000. You must use unique vPC IDs for each vPC within a single virtual device context (VDC). |
Defaults
None
Command Modes
Any command mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
4.1(3) |
This command was introduced. |
Usage Guidelines
You must enable the vPC feature before you can create a vPC domain.
You put all vPC interfaces, including the vPC peer link, on both of the vPC peer devices into the identical vPC domain. You must have unique vPC domain numbers within each VDC. In Cisco NX-OS Release 4.1(3), you can have only one vPC per VDC. Once you create a vPC domain, the system automatically creates a vPC system MAC address that is unique to that vPC.
You also use this command to enter the vpc-domain command mode in order to configure vPC parameters.
This command does not require a license.
Examples
This example shows how to create a vPC domain:
switch(config)# vpc domain 5
switch(config-vpc-domain)#
This example shows how to enter the vpc-domain command mode to configure an existing vPC domain:
switch(config)# vpc domain 5
switch(config-vpc-domain)#
Related Commands
|
Command |
Description |
|---|---|
|
show vpc brief |
Displays information about vPCs. If the feature is not enabled, the system displays an error when you enter this command. |
vpc orphan-ports suspend
To shut down the virtual port channel (vPC) port when the peer link is down, use the vpc orphan-ports suspend command. To revert to default settings, use the no form of this command.
vpc orphan-ports suspend
no vpc orphan-ports suspend
Syntax Description
This command has no arguments or keywords.
Defaults
Disabled
Command Modes
Interface configuration (config-if)
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
5.2(1) |
This command was introduced. |
Usage Guidelines
You can use the vpc orphan-ports suspend command only on physical ports.

Note ![]() You can configure vPC orphan port suspension only on physical ports, not on port channel member ports.
You can configure vPC orphan port suspension only on physical ports, not on port channel member ports.
This command does not require a license.
Examples
This example shows how to shut down the vPC port when the peer link is down:
switch# configure terminal
switch(config)# interface ethernet 5/2
switch(config-if)# vpc orphan-ports suspend
Related Commands
|
Command |
Description |
|---|---|
|
vpc domain |
Creates a vPC domain. |
vpc peer-link
To create a virtual port-channel (vPC) peer link, use the vpc peer-link command. To remove a vPC peer link, use the no form of this command.
vpc peer-link
no vpc peer-link
Syntax Description
This command has no arguments or keywords.
Defaults
None
Command Modes
Interface command mode
Supported User Roles
network-admin
vdc-admin
Command History
|
Release |
Modification |
|---|---|
|
4.1(3) |
This command was introduced. |
Usage Guidelines
You must enable the vPC feature before you can create a vPC peer link.
You configure a port channel using 10-Gigabit Ethernet ports on the N7K-M132XP-12 module. We recommend that you use the 10-Gigabit Ethernet ports for the channel in dedicated mode and configure at least two of these ports on two different modules into the port channel for redundancy.
Use the vpc peer-link command to make that port channel a vPC peer link. The system returns an error message if you attempt to configure a 1-Gigabit Ethernet interface as a vPC peer link.
After you configure the vPC peer device and the vPC peer link is established, the system creates a new MAC address for the vPC and decides which vPC device is the primary device and which is the secondary device.
This command does not require a license.
Examples
This example shows how to create a vPC peer link:
switch(config)# interface port-channel 20
switch(config-if)# vpc peer-link
switch(config-vpc-domain)#
Related Commands
|
Command |
Description |
|---|---|
|
show vpc brief |
Displays information about vPCs. If the feature is not enabled, the system displays an error when you enter this command. |
Introduction
This document describes how to determine why a port or interface experiences problems.
Prerequisites
Requirements
There are no specific requirements for this document.
Components Used
This document applies to Catalyst switches that run on Cisco IOS® System Software.
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, ensure that you understand the potential impact of any command.
Conventions
Refer toCisco Technical Tips Conventionsfor more information on document conventions.
Note: To access tools and websites, you must be a registered Cisco client.
Troubleshoot the Physical Layer
Use the LEDs to Troubleshoot
If you have physical access to the switch, it can save time to look at the port LEDs which give you the link status or can indicate an error condition (if red or orange). The table describes the LED status indicators for Ethernet modules or fixed-configuration switches:
| Platform | URL |
|
Catalyst 6000 Series Switches |
Ethernet Module LEDs |
|
Catalyst 4000 Series Switches |
Ethernet Module LEDs |
|
Catalyst 3750 Series Switches |
Front Panel LEDs |
|
Catalyst 3550 Series Switches |
Front Panel LEDs |
|
Catalyst 2950/2955 Series Switches |
Front Panel LEDs |
|
Catalyst 2900/3500XL Series Switches |
Front Panel LEDs |
|
Catalyst 1900 and 2820 Series Switches |
Front Panel LEDs |
Ensure that both sides have a link. A single broken wire or one shutdown port can cause the problem where one side has a link light, but the other side does not.
A link light does not guarantee that the cable is fully functional. The cable can have encountered physical stress that causes it to be functional at a marginal level. Normally you can identify this situation if the port has many packet errors, or the port constantly flaps (loses and regains link).
Check the Cable and Both Sides of the Connection
If the link light for the port does not come on, you can consider these possibilities:
| Possible Cause | Corrective Action |
|
No cable connected |
Connect cable from switch to a known good device. |
|
Wrong Port |
Make sure that both ends of the cable are plugged into the correct ports. |
|
Device has no power |
Ensure that both devices have power. |
|
Wrong cable type |
Verify the cable selection. Refer to theCatalyst Switch Cable Guide. |
|
Bad cable |
Swap suspect cable with known good cable. Look for broken or lost pins on connectors. |
|
Loose connections |
Check for loose connections. Sometimes a cable appears to be seated in the jack but is not. Unplug the cable and reinsert it. |
|
Patch Panels |
Eliminate faulty patch panel connections. Bypass the patch panel if possible to rule it out. |
|
Media Convertors |
Eliminate faulty media convertors: fiber-to-copper, and so on. Bypass the media convertor if possible to rule it out. |
|
Bad or wrong Gigabit Interface Convertor (GBIC) |
Swap suspect GBIC with known good GBIC. Verify Hw and Sw support for this type of GBIC. |
|
Bad Port or Module Port or Interface or Module not enabled |
Move the cable to a known good port to troubleshoot a suspect port or module. Use the show interface command for Cisco IOS to look for errdisable, disable or shutdown status. The show module command can indicate faulty, which can indicate a hardware problem. See the Common Port and Interface Problems section of this document for more information. |
Ethernet Copper and Fiber Cables
Ensure that you have the correct cable for the type of connection you want to make. Category 3 copper cable can be used for 10 Mbps unshielded twisted pair (UTP) connections but must never be used for 10/100 or 10/100/1000Mbps UTP connections. Always use either Category 5, Category 5e, or Category 6 UTP for 10/100 or 10/100/1000Mbps connections.
Warning: Category 5e and Category 6 cables can store high levels of static electricity because of the dielectric properties of the materials used in their construction. Always ground the cables (especially in new cable runs) to a suitable and safe earth ground before you connect them to the module.
For fiber, make sure you have the correct cable for the distances involved and the type of fiber ports that are used. The two options are single mode fiber (SMF) or multimode fiber (MMF). Make sure the ports on the devices that are connected together are both SMF, or both are MMF ports.
Note: For fiber connections, make sure the transmit lead of one port is connected to the receive lead of the other port. Connections for transmit-to-transmit and receive-to-receive do not work.
Ethernet and Fast Ethernet Maximum Transmission Distances
| Transceiver Speed | Cable Type | Duplex Mode | Maximum Distance between Station |
|
10 Mbps |
Category 3 UTP |
Full and half |
328 ft (100 m) |
|
10 Mbps |
MMF |
Full and half |
1.2 mi (2 km) |
|
100 Mbps |
Category 5 UTP Category 5e UTP |
Full and half |
328 ft (100 m) |
|
100 Mbps |
Category 6 UTP |
Full and half |
328 ft (100 m) |
|
100 Mbps |
MMF |
Half |
1312 ft (400 m) |
|
Full |
1.2 mi (2 km) |
||
|
100 Mbps |
SMF |
Half |
1312 ft (400 m) |
|
Full |
6.2 mi (10 km) |
For more details on the different types of cables/connectors, cable requirements, optical requirements (distance, type, patch cables, and so on.), how to connect the different cables, and which cables are used by most Cisco switches and modules, refer to Catalyst Switch Cable Guide .
Troubleshoot the Gigabit Ethernet
If you have device A connected to device B over a Gigabit link, and the link does not come up, perform this procedure.
Step-by-Step Procedure
-
Verify device A and B use the same GBIC, short wavelength (SX), long wavelength (LX), long haul (LH), extended wavelength (ZX), or copper UTP (TX). Both devices must use the same type of GBIC to establish link. An SX GBIC needs to connect with an SX GBIC. An SX GBIC does not link with an LX GBIC. Refer to Mode-Conditioning Patch Cord Installation Note for more information.
-
Verify distance and cable used per GBIC as defined in this table.
1000BASE-T and 1000BASE-X Port Cabling Specifications
|
GBIC |
Wavelength (nm) |
Copper/Fiber Type |
Core Size1(Microns) |
Modal Bandwidth (MHz / km) |
Cable Distance2 |
|
WS-G54831000Base — T (copper) |
Category 5 UTP Category 5e UTP Category 6 UTP |
328 ft (100 m) |
|||
|
WS-G54841000BASE-SX3 |
850 |
MMF |
62.5 62.5 50.0 50.0 |
160 200 400 500 |
722 ft (220 m) 902 ft (275 m) 1640 ft (500 m) 1804 ft (550 m) |
|
WS-G54861000BASE-LX/LH |
1310 |
MMF4SMF |
62.5 50.0 50.0 8.3/9/10 |
500 400 500 — |
1804 ft (550 m) 1804 ft (550 m) 1804 ft (550 m) 6.2 miles (10 km) |
|
WS-G54871000BASE-ZX5 |
1550 |
MMF SMF6 |
8.3/9/10 8.3/9/10 |
43.5 miles (70 km)762.1 miles (100 km) |
-
The numbers given for multimode fiber-optic cable refer to the core diameter. For single-mode fiber-optic cable, 8.3 microns refers to the core diameter. The 9-micron and 10-micron values refer to the mode-field diameter (MFD), which is the diameter of the portion of the fiber that is light-carrying. This area consists of the fiber core plus a small portion that covers the cladding. The MFD is a function of the core diameter, the wavelength of the laser, and the refractive index difference between the core and the cladding.
-
Distances are based on fiber loss. Multiple splices and substandard fiber-optic cable reduce the cable distances.
-
Use with MMF only.
-
When you use an LX/LH GBIC with 62.5-micron diameter MMF, you must install a mode-conditioning patch cord (CAB-GELX-625 or equivalent) between the GBIC and the MMF cable on both the transmit and receive ends of the link. The mode-conditioning patch cord is required for link distances less than 328 feet (100 m) or greater than 984 feet (300 m). The mode-conditioning patch cord prevents the over use of the receiver for short lengths of MMF and reduces differential mode delay for long lengths of MMF. Refer to Mode-Conditioning Patch Cord Installation Note for more information.
-
Use with SMF only.
-
Dispersion-shifted single-mode fiber-optic cable.
-
The minimum link distance for ZX GBICs is 6.2 miles (10 km) with an 8-dB attenuator installed at each end of the link. Without attenuators, the minimum link distance is 24.9 miles (40 km).
3. If either device has multiple Gigabit ports, connect the ports to each other. This tests each device and verifies that the Gigabit interface functions correctly. For example, you have a switch that has two Gigabit ports. Wire Gigabit port one to Gigabit port two. Does the link come up? If so, the port is good. STP blocks on the port and prevents any loops (port one receive (RX) goes to port two transmit (TX), and port one TX goes to port two RX).
4. If single connection or Step 3 fails with SC connectors, loop the port back to itself (port one RX goes to port one TX). Does the port come up? If not, contact the TAC, as this can be a faulty port.
5. If steps 3 and 4 are successful, but a connection between device A and B cannot be established, loop ports with the cable that adjoins the two devices. Verify that there is not a faulty cable.
6. Verify that each device supports 802.3z specification for Gigabit auto-negotiation. Gigabit Ethernet has an auto-negotiation procedure that is more extensive than the one used for 10/100 Ethernet (Gigabit auto-negotiation spec: IEEE Std 802.3z-1998). When you enable link negotiation, the system auto-negotiates flow control, duplex mode, and remote fault information. You must either enable or disable link negotiation on both ends of the link. Both ends of the link must be set to the same value or the link cannot connect. Problems have been seen when you connect to devices manufactured before the IEEE 802.3z standard was ratified. If either device does not support Gigabit auto-negotiation, disable the Gigabit auto-negotiation, and it forces the link up. It takes 300msec for the card firmware to notify the software that a 10/100/1000BASE-TX link/port is down. The 300msec default debounce timer comes from the firmware polling timer to the linecards, which occurs every 300 msec. If this link is run in 1G (1000BASE-TX) mode, Gigabit sync, which occurs every 10msec, must be able to detect the link down faster. There is a difference in the link failure detection times when you run GigabitEthenet on copper versus GigabitEthernet over fiber. This difference in detection time is based on the IEEE standards.
Warning: Disable auto-negotiation and this hides link drops or physical layer problems. This is only required if end-devices such as older Gigabit NICs are used which cannot support IEEE 802.3z. Do not disable auto-negotiation between switches unless absolutely required to do so, as physical layer problems can go undetected, which results in STP loops. The alternative is to contact the vendor for software/hardware upgrade for IEEE 802.3z Gigabit auto-negotiation support.
For GigabitEthernet system requirements as well as Gigabit Interface Converters (GBICs), Coarse Wavelength Division Multiplexing (CWDM), and Small Form-Factor Pluggable (SFP) system requirements, refer to these:
-
System Requirements to Implement Gigabit Ethernet on Catalyst Switches
-
Catalyst GigaStack Gigabit Interface Converter Switch Compatibility Matrix
-
Cisco Gigabit Ethernet Transceiver Modules Compatibility Matrix
-
Cisco 10-Gigabit Ethernet Transceiver Modules Compatibility Matrix
For general configuration information and additional information on how to troubleshoot, refer to Configuring and Troubleshooting Ethernet 10/100/1000 MB Half/Full Duplex Auto-Negotiation .
Connected vs Notconnected
Most Cisco switches have a port in the notconnect state. This means it is currently not connected to anything, but it can connect if it has a good connection to another operational device. If you connect a good cable to two switch ports in the notconnect state, the link light must become green for both ports, and the port status must indicate connected. This means that the port is up as far as Layer 1 (L1) is concerned.
For Cisco IOS, you can use the show interfaces command to verify whether the interface is up, line protocol is up (connected) . The first up refers to the physical layer status of the interface. The line protocol up message shows the data link layer status of the interface and says that the interface can send and receive keepalives.
Router#show interfaces fastEthernet 6/1 FastEthernet6/1 is down, line protocol is down (notconnect)
!--- The interface is down and line protocol is down. !--- Reasons: In this case, !--- 1) A cable is not properly connected or not connected at all to this port. !--- 2) The connected cable is faulty. !--- 3) Other end of the cable is not connected to an active port or device. !--- Note: For gigabit connections, GBICs need to be matched on each !--- side of the connection. !--- There are different types of GBICs, depends on the cable and !--- distances involved: short wavelength (SX), !--- long-wavelength/long-haul (LX/LH) and extended distance (ZX). !--- An SX GBIC needs to connect with an SX GBIC; !--- an SX GBIC does not link with an LX GBIC. Also, some gigabit !--- connections require conditioning cables, !--- that depend on the lengths involved.
Router#show interfaces fastEthernet 6/1 FastEthernet6/1 is up, line protocol is down (notconnect)
!--- The interface is up (or not in a shutdown state), but line protocol down. !--- Reason: In this case, the device on the other side of the wire is a !--- CatOS switch with its port disabled.
Router#show interfaces fastEthernet 6/1 status Port Name Status Vlan Duplex Speed Type Fa6/1 notconnect 1 auto auto 10/100BaseTX
Ifshow interfacesshows up/ line protocol up (connected) but you see errors increment in the output of either command, refer to the Common Port and Interface Problems section of this document for advice.
Troubleshoot the Most Common Port and Interface Commands for Cisco IOS
This table shows the most common commands used to troubleshoot the port or interface problems on switches that run Cisco IOS System Software on the Supervisor.
Note: The right hand column on the next table gives a brief description of what the command does and lists any exceptions to the use per platform.
If you have the output of the supported commands from your Cisco device, you can use Cisco CLI Analyzer to display potential issues and fixes.
| Cisco IOS Commands | Description |
|
show version |
This command displays output similar to a Cisco router, like software image name and version information and system memory sizes. Helpful with the search for software/hardware incompatibilities (with theRelease NotesorSoftware Advisor) and bugs (with theSoftware Bug Toolkit). |
|
show module |
This command displays what cards are present in the switch, the version of software they are that run, and what state the modules are in: ok, faulty, and so on. This is helpful to diagnose a hardware problem on a module or port. For more information about how to troubleshoot hardware problems with theshow module command, see the Port or Interface Status is disabled or shutdown or the Hardware Problems sections of this document. |
|
show run-config |
This command displays the current configuration file of the switch. Changes are |
|
show interfaces |
The show interface command displays the administrative and operational status of a switch port, input and output packets, buffer failures, errors, and so on. |
|
clear counters |
Use theclear counters command to zero the traffic and error counters so that you can see if the problem is only temporary, or if the counters continue to increment. Note: The Catalyst 6500/6000 series switches do not clear the bit counters of an interface with theclear counterscommand. The only way to clear the bit counters in these switches is to reload. |
|
show interfaces counters |
This is the command to use on the Catalyst 6000, 4000, 3550, 2950, and 3750 series. |
|
show counters interface show controllers ethernet-controller |
Theshow counters interface command was introduced in software version 12.1(13)E for the Catalyst 6000 series only and displays 32-bit and 64-bit error counters. For Cisco IOS on 2900/3500XL, 2950/2955, 3550, 2970 and 3750 series switches, theshow controllers Ethernet-controller command displays discarded frames, deferred frames, alignment errors, collisions, and so on. |
|
show interfaces counters |
This is the command to use on the Catalyst 6000, 4000, 3550, 2950, and and 3750 series. |
|
show diagnostic(s) show post |
The command show diagnostic was introduced in 12.1(11b)E for the Catalyst 6000 series and show diagnostics (with an s ) was introduced in for Catalyst 4000 Series. On the 2900/3500XL, 2950/2955, 3550, 2970 and 3750 series switches the equivalent command is show post which displays the results of the switch POST. For more information on troubleshoot hardware related errors on Catalyst switches, see the Hardware Problems section of this document. |
Understand the Specific Port and Interface Counter Output for Cisco IOS
Most switches have some way to track the packets and errors that occur on a port or interface. The common commands used to find this type of information are described in the Most Common Port and Interface Troubleshooting Commands for Cisco IOS section of this document.
Note: There can be differences in the implementation of the counters across various platforms and releases. Although the values of the counters are largely accurate, they are not very precise by design. In order to pull the exact statistics of the traffic, it is suggested that you use a sniffer to monitor the necessary ingress and egress interfaces.
Excessive errors for certain counters usually indicate a problem. When you operate at half-duplex setup, some data link errors increment in Frame Check Sequence (FCS), alignment, runts, and collision counters are normal. Generally, a one percent ratio of errors to total traffic is acceptable for half-duplex connections. If the ratio of errors to input packets is greater than two or three percent, performance degradation can be noticed.
In half-duplex environments, it is possible for both the switch and the connected device to sense the wire and transmit at exactly the same time and result in a collision. Collisions can cause runts, FCS, and alignment errors due to the frame not completely copied to the wire, which results in fragmented frames.
When you operate at full-duplex, errors in FCS, Cyclic Redundancy Checks (CRC), alignment, and runt counters must be minimal. If the link operates at full-duplex, the collision counter is not active. If the FCS, CRC, alignment, or runt counters increment, check for a duplex mismatch. Duplex mismatch is a situation where the switch operates at full-duplex and the connected device operates at half-duplex, or vice versa. The results of a duplex mismatch are extremely slow performance, intermittent connectivity, and loss of connection. Other possible causes of data link errors at full-duplex are bad cables, faulty switch ports, or NIC software/hardware issues. See the Common Port and Interface Problems section of this document for more information.
Show Interfaces for Cisco IOS
The show interfaces card-type {slot/port}command is the used command for Cisco IOS on the Supervisor to display error counters and statistics. An alternative to this command (for Catalyst 6000, 4000, 3550, 2970 2950/2955, and 3750 series switches) is theshow interfacescard-type <slot/port>counters errors command which only displays the interface error counters. Refer to Table 1 for explanations of the error counter output.
Note: For 2900/3500XL Series switches use theshow interfacescard-type {slot/port}command with theshow controllers Ethernet-controllercommand.
Router#sh interfaces fastEthernet 6/1
FastEthernet6/1 is up, line protocol is up (connected)
Hardware is C6k 100Mb 802.3, address is 0009.11f3.8848 (bia 0009.11f3.8848)
MTU 1500 bytes, BW 100000 Kbit, DLY 100 usec,
reliability 255/255, txload 1/255, rxload 1/255
Encapsulation ARPA, loopback not set
Full-duplex, 100Mb/s
input flow-control is off, output flow-control is off
ARP type: ARPA, ARP Timeout 04:00:00
Last input 00:00:14, output 00:00:36, output hang never
Last clearing of "show interface" counters never
Input queue: 0/2000/0/0 (size/max/drops/flushes); Total output drops: 0
Queueing strategy: fifo
Output queue :0/40 (size/max)
5 minute input rate 0 bits/sec, 0 packets/sec
5 minute output rate 0 bits/sec, 0 packets/sec
Theshow interfacescommand output up to this point is explained here (in order) :
-
up, line protocol is up (connected) — The first up refers to the physical layer status of the interface. The line protocol up message shows the data link layer status of the interface and says that the interface can send and receive keepalives.
-
MTU — The Maximum Transmission Unit (MTU) is 1500 bytes for Ethernet by default (for the max data portion of the frame).
-
Full-duplex, 100Mb/s — Full-duplex and 100Mbps is the current speed and duplex setup of the interface. This does not tell you whether autoneg was used to achieve this. Use theshow interfaces fastEthernet 6/1 statuscommand to display this:
Router#show interfaces fastEthernet 6/1 status Port Name Status Vlan Duplex Speed Type Fa6/1 connected 1 a-full a-100 10/100BaseTX
!--- Autonegotiation was used to achieve full-duplex and 100Mbps.
-
Last input, output — The number of hours, minutes, and seconds since the last packet was successfully received or transmitted by the interface. This is useful to know when a dead interface failed.
-
Last clearing of «show interface» counters — The last time the clear counters command was issued since the last time the switch was rebooted. The clear counters command is used to reset interface statistics.
Note: Variables that can affect routing (for example, load and reliability) are not cleared when the counters are cleared.
-
Input queue — The number of packets in the input queue.Size/max/drops= the current number of frames in the queue / the max number of frames the queue can hold before it must start to drop frames / the actual number of frames dropped because the max queue size was exceeded.Flushesis used to count Selective Packet Discard (SPD) drops on the Catalyst 6000 Series that run Cisco IOS. (The flushes counter can be used but never increments on the Catalyst 4000 Series that run Cisco IOS.) SPD is a mechanism that quickly drops low priority packets when the CPU is overloaded in order to
savesome process capacity for high priority packets. The flushes counter in the show interface command output increments as part of selective packet discard (SPD), which implements a selective packet drop policy on the IP process queue of the router. Therefore, it applies to only process switched traffic.The purpose of SPD is to ensure that important control packets, such as routing updates and keepalives, are not dropped when the IP input queue is full. When the size of the IP input queue is between the minimum and maximum thresholds, normal IP packets are dropped based on a certain drop probability. These random drops are called SPD flushes.
-
Total output drops — The number of packets dropped because the output queue is full. A common cause is traffic from a high bandwidth link that is switched to a lower bandwidth link or traffic from multiple inbound links that are switched to a single outbound link. For example, if a large amount of traffic flow comes in on a gigabit interface and is switched out to a 100Mbps interface, this can cause output drops to increment on the 100Mbps interface. This is because the output queue on that interface is overwhelmed by the excess traffic due to the speed mismatch between the inbound and outbound bandwidths.
-
Output queue — The number of packets in the output queue. Size/max means the current number of frames in the queue/the max number of frames the queue can hold before it is full and must start to drop the frames.
-
5 minute input/output rate — The average input and output rate seen by the interface in the last five minutes. Specify a shorter period of time to get an accurate read (to better detect traffic bursts for example and issue theload-interval <seconds>interface command.
SeeTable 1for explanations of the error counter output.
!--- ...show interfaces command output continues.
1117058 packets input, 78283238 bytes, 0 no buffer
Received 1117035 broadcasts, 0 runts, 0 giants, 0 throttles
0 input errors, 0 CRC, 0 frame, 0 overrun, 0 ignored
0 watchdog, 0 multicast, 0 pause input
0 input packets with dribble condition detected
285811 packets output, 27449284 bytes, 0 underruns
0 output errors, 0 collisions, 2 interface resets
0 babbles, 0 late collision, 0 deferred
0 lost carrier, 0 no carrier
0 output buffer failures, 0 output buffers swapped out
Note: There is a difference between the counter of show interface command output for a physical interface and a VLAN interface.The input packet counters increment in the output ofshow interfacefor a VLAN interface when that packet is Layer 3 (L3) processed by the CPU. Traffic that is Layer 2 (L2) switched never makes it to the CPU and is not counted in theshow interfacecounters for the VLAN interface. It would be counted on theshow interfaceoutput for the appropriate physical interface.
Theshow interfaces <card-type> <slot/port> counters errorscommand is used in Cisco IOS to display the output of the interface errors only. SeeTable 1for explanations of the error counter output.
Router#sh interfaces fastEthernet 6/1 counters errors Port Align-Err FCS-Err Xmit-Err Rcv-Err UnderSize OutDiscards Fa6/1 0 0 0 0 0 0 Port Single-Col Multi-Col Late-Col Excess-Col Carri-Sen Runts Giants Fa6/1 0 0 0 0 0 0 0
Table 1. Cisco IOS error counter output forshow interfacesorshow interfaces<card-type> <x/y> counters errorsfor the Catalyst 6000 and 4000 Series.
| Counters (in alphabetical order) | Issues and Common Causes that Increase Error Counters |
|
Align-Err |
Description:show interfaces counters errors. Alignment errors are a count of the number of frames received that do not end with an even number of octets and have a bad Cyclic Redundancy Check (CRC).Common Causes:These are usually the result of a duplex mismatch or a physical problem (such as cabling, a bad port, or a bad NIC). When the cable is first connected to the port, some of these errors can occur. Also, if there is a hub connected to the port, collisions between other devices on the hub can cause these errors.Platform Exceptions:Alignment errors are not counted on the Catalyst 4000 Series Supervisor I (WS-X4012) or Supervisor II (WS-X4013). |
|
babbles |
Description:show interfaces counter indicates that the transmit jabber timer expired. A jabber is a frame longer than 1518 octets (which exclude frame bits, but include FCS octets), which does not end with an even number of octets (alignment error) or has a bad FCS error. |
|
Carri-Sen |
Description:show interfaces counters errors. The Carri-Sen (carrier sense) counter increments every time an Ethernet controller wants to send data on a half-duplex connection. The controller senses the wire and checks if it is not busy before it transmits.Common Causes:This is normal on an half-duplex Ethernet segment. |
|
collisions |
Descriptions:show interfacescounter. The number of times a collision occurred before the interface transmitted a frame to the media successfully.Common Causes:Collisions are normal for interfaces configured as half-duplex but must not be seen on full duplex interfaces. If collisions increase dramatically, this points to a highly utilized link or possibly a duplex mismatch with the attached device. |
|
CRC |
Description:show interfacescounter. This increments when the CRC generated by the LAN station or far-end device that originates the traffic does not match the checksum calculated from the data received.Common Causes:This usually indicates noise or transmission problems on the LAN interface or the LAN itself. A high number of CRCs is usually the result of collisions but can also indicate a physical issue (such as cabling, bad interface or NIC) or a duplex mismatch. |
|
deferred |
Description:show interfacescounter. The number of frames that have been transmitted successfully after they wait because the media was busy.Common Causes:This is usually seen in half-duplex environments where the carrier is already in use when it tries to transmit a frame. |
|
pause input |
Description:show interfacescounter. An increment in pause input counter means that the connected device requests for a traffic pause when its receive buffer is almost full.Common Causes:This counter is incremented for informational purposes since the switch accepts the frame. The pause packets stop when the connected device is able to receive the traffic. |
|
input packets with dribble condition |
Description:show interfacescounter. A dribble bit error indicates that a frame is slightly too long.Common Causes:This frame error counter is incremented for informational purposes, since the switch accepts the frame. |
|
Excess-Col |
Description: show interfaces counters errors. A count of frames for which transmission on a particular interface fails due to excessive collisions. An excessive collision happens when a packet has a collision 16 times in a row. The packet is then dropped. Common Causes: Excessive collisions are typically an indication that the load on the segment needs to be split across multiple segments but can also point to a duplex mismatch with the attached device. Collisions must not be seen on interfaces configured as full duplex. |
|
FCS-Err |
Description: show interfaces counters errors. The number of valid size frames with Frame Check Sequence (FCS) errors but no frame errors. Common Causes: This is typically a physical issue (such as cabling, a bad port, or a bad Network Interface Card (NIC)) but can also indicate a duplex mismatch. |
|
frame |
Description: show interfaces counter. The number of packets received incorrectly that has a CRC error and a non-integer number of octets (alignment error). Common Causes: This is usually the result of collisions or a physical problem (such as cabling, bad port or NIC) but can also indicate a duplex mismatch. |
|
Giants |
Description: show interfaces and show interfaces counters errors. Frames received that exceed the maximum IEEE 802.3 frame size (1518 bytes for non-jumbo Ethernet) and have a bad Frame Check Sequence (FCS). Common Causes: In many cases, this is the result of a bad NIC. Try to find the offending device and remove it from the network. Platform Exceptions: Catalyst Cat4000 Series that run Cisco IOS Previous to software Version 12.1(19)EW, the giants counter incremented for a frame > 1518bytes. After 12.1(19)EW, a giant in show interfaces increments only when a frame is received >1518bytes with a bad FCS. |
|
ignored |
Description: sh interfaces counter. The number of received packets ignored by the interface because the interface hardware ran low on internal buffers. Common Causes: Broadcast storms and bursts of noise can cause the ignored count to be increased. |
|
Input errors |
Description: show interfaces counter. Common Causes: This includes runts, giants, no buffer, CRC, frame, overrun, and ignored counts. Other input-related errors can also cause the input errors count to be increased, and some datagrams can have more than one error. Therefore, this sum cannot balance with the sum of enumerated input error counts. Also refer to the section Input Errors on a Layer 3 Interface Connected to a Layer 2 Switchport. |
|
Late-Col |
Description: show interfaces and show interfaces counters errors.The number of times a collision is detected on a particular interface late in the transmission process. For a 10 Mbit/s port this is later than 512 bit-times into the transmission of a packet. Five hundred and twelve bit-times corresponds to 51.2 microseconds on a 10 Mbit/s system. Common Causes: This error can indicate a duplex mismatch among other things. For the duplex mismatch scenario, the late collision is seen on the half-duplex side. As the half-duplex side transmits, the full duplex side does not wait its turn and transmits simultaneously which causes a late collision. Late collisions can also indicate an Ethernet cable or segment that is too long. Collisions must not be seen on interfaces configured as full duplex. |
|
lost carrier |
Description: show interfaces counter. The number of times the carrier was lost in transmission. Common Causes: Check for a bad cable. Check the physical connection on both sides. |
|
Multi-Col |
Description: show interfaces counters errors. The number of times multiple collisions occurred before the interface transmitted a frame to the media successfully. Common Causes: Collisions are normal for interfaces configured as half-duplex but must not be seen on full duplex interfaces. If collisions increase dramatically, this points to a highly utilized link or possibly a duplex mismatch with the attached device. |
|
no buffer |
Description:show interfaces counter. The number of received packets discarded because there is no buffer space.Common Causes:Compare with ignored count. Broadcast storms can often be responsible for these events. |
|
no carrier |
Description:show interfacescounter. The number of times the carrier was not present in the transmission.Common Causes:Check for a bad cable. Check the physical connection on both sides. |
|
Out-Discard |
Description:The number of outbound packets chosen to be discarded even though no errors have been detected.Common Causes:One possible reason to discard such a packet can be to free up buffer space. |
|
output buffer failures output buffers swapped out |
Description:show interfacescounter. The number of failed buffers and the number of buffers swapped out.Common Causes:A port buffers the packets to the Tx buffer when the rate of traffic switched to the port is high and it cannot handle the amount of traffic. The port starts to drop the packets when the Tx buffer is full and thus increases the underruns and the output buffer failure counters. The increase in the output buffer failure counters can be a sign that the ports are run at an inferior speed and/or duplex, or there is too much traffic that goes through the port. As an example, consider a scenario where a 1gig multicast stream is forwarded to 24 100 Mbps ports. If an egress interface is over-subscribed, it is normal to see output buffer failures that increment along with Out-Discards. For troubleshoot information, see theDeferred Frames (Out-Lost or Out-Discard)section of this document. |
|
output errors |
Description:show interfacescounter. The sum of all errors that prevented the final transmission of datagrams out of the interface.Common Cause:This issue is due to the low Output Queue size. |
|
overrun |
Description:The number of times the receiver hardware was unable to hand received data to a hardware buffer.Common Cause:The input rate of traffic exceeded the ability of the receiver to handle the data. |
|
packets input/output |
Description:show interfacescounter. The total error free packets received and transmitted on the interface. Monitor these counters for increments as it is useful to determine whether traffic flows properly through the interface. The bytes counter includes both the data and MAC encapsulation in the error free packets received and transmitted by the system. |
|
Rcv-Err |
Description: For the Catalyst 6000 Series only — show interfaces counters error.Common Causes:See Platform Exceptions.Platform Exceptions:Catalyst 5000 Seriesrcv-err = receive buffer failures. For example, a runt, giant, or an FCS-Err does not increment the rcv-err counter. The rcv-err counter on a 5K only increments as a result of excessive traffic. OnCatalyst 4000 Seriesrcv-err = the sum of all receive errors, which means, in contrast to the Catalyst 5000, that the rcv-err counter increments when the interface receives an error like a runt, giant or FCS-Err. |
|
Runts |
Description:show interfacesandshow interfaces counters errors. The frames received that are smaller than the minimum IEEE 802.3 frame size (64 bytes for Ethernet), and with a bad CRC.Common Causes:This can be caused by a duplex mismatch and physical problems, such as a bad cable, port, or NIC on the attached device.Platform Exceptions:Catalyst 4000 Series that run Cisco IOSPrevious to software Version 12.1(19)EW, a runt = undersize. Undersize = frame < 64bytes. The runt counter only incremented when a frame less than 64 bytes was received. After 12.1(19EW, a runt = a fragment. A fragment is a frame < 64 bytes but with a bad CRC. The result is the runt counter now increments inshow interfaces, along with the fragments counter inshow interfaces counters errorswhen a frame <64 bytes with a bad CRC is received.Cisco Catalyst 3750 Series SwitchesIn releases prior to Cisco IOS 12.1(19)EA1, when dot1q is used on the trunk interface on the Catalyst 3750, runts can be seen onshow interfacesoutput because valid dot1q encapsulated packets, which are 61 to 64 bytes and include the q-tag, are counted by the Catalyst 3750 as undersized frames, even though these packets are forwarded correctly. In addition, these packets are not reported in the appropriate category (unicast, multicast, or broadcast) in receive statistics. This issue is resolved in Cisco IOS release 12.1(19)EA1 or 12.2(18)SE or later. |
|
Single-Col |
Description:show interfaces counters errors. The number of times one collision occurred before the interface transmitted a frame to the media successfully.Common Causes:Collisions are normal for interfaces configured as half-duplex but must not be seen on full duplex interfaces. If collisions increase dramatically, this points to a highly utilized link or possibly a duplex mismatch with the attached device. |
|
throttles |
Description:show interfaces. The number of times the receiver on the port is disabled, possibly because of buffer or processor overload. If an asterisk (*) appears after the throttles counter value, it means that the interface is throttled at the time the command is run.Common Causes:Packets which can increase the processor overload include IP packets with options, expired TTL, non-ARPA encapsulation, fragmentation, tunnels, ICMP packets, packets with MTU checksum failure, RPF failure, IP checksum and length errors. |
|
underruns |
Description:The number of times that the transmitter has been that run faster than the switch can handle.Common Causes:This can occur in a high throughput situation where an interface is hit with a high volume of traffic bursts from many other interfaces all at once. Interface resets can occur along with the underruns. |
|
Undersize |
Description:show interfaces counters errors . The frames received that are smaller than the minimum IEEE 802.3 frame size of 64 bytes (which excludes frame bits but includes FCS octets) that are otherwise well formed.Common Causes:Check the device that sends out these frames. |
|
Xmit-Err |
Description:show interfaces counters errors. This is an indication that the internal send (Tx) buffer is full.Common Causes:A common cause of Xmit-Err can be traffic from a high bandwidth link that is switched to a lower bandwidth link, or traffic from multiple inbound links that are switched to a single outbound link. For example, if a large amount of traffic bursts comes in on a gigabit interface and is switched out to a 100Mbps interface, this can cause Xmit-Err to increment on the 100Mbps interface. This is because the output buffer of the interface is overwhelmed by the excess traffic due to the speed mismatch between the inbound and outbound bandwidths. |
Show Interfaces Counters for Cisco IOS
To monitor inbound and outbound traffic on the port as displayed by the next output, for unicast, multicast, and broadcast traffic. Theshow interfacescard-type {slot/port}counterscommand is used when you run Cisco IOS on the Supervisor.
Note: There is, an Out-Discard counter in the Cisco IOSshow interfaces counters errorscommand which is explained inTable 1.
Router#sh interfaces fas 6/1 counters Port InOctets InUcastPkts InMcastPkts InBcastPkts Fa6/1 47856076 23 673028 149 Port OutOctets OutUcastPkts OutMcastPkts OutBcastPkts Fa6/1 22103793 17 255877 3280 Router#
!--- Cisco IOS counters used to monitor inbound and outbound unicast, multicast !--- and broadcast packets on the interface.
Show Counters Interface for Cisco IOS
Theshow counters interfacecard-type {slot/port}command was introduced in Cisco IOS software version 12.1(13)E for the Catalyst 6000 series only, it offers even more detailed statistics for ports and interfaces. This commanda display the 32-bit and 64-bit error counters per port or interface.
Show Controller Ethernet-Controller for Cisco IOS
For Catalyst 3750, 3550, 2970, 2950/2955, 2940, and 2900/3500XL switches use the command show controller ethernet-controller to display traffic counter and error counter output that is similar to theoutput for Catalyst 6000 series switches.
3550-1#show controller ethernet-controller fastEthernet 0/1
!--- Output from a Catalyst 3550.
Transmit FastEthernet0/1 Receive
0 Bytes 0 Bytes
0 Unicast frames 0 Unicast frames
0 Multicast frames 0 Multicast frames
0 Broadcast frames 0 Broadcast frames
0 Discarded frames 0 No dest, unicast
0 Too old frames 0 No dest, multicast
0 Deferred frames 0 No dest, broadcast
0 1 collision frames
0 2 collision frames 0 FCS errors
0 3 collision frames 0 Oversize frames
0 4 collision frames 0 Undersize frames
0 5 collision frames 0 Collision fragments
0 6 collision frames
0 7 collision frames 0 Minimum size frames
0 8 collision frames 0 65 to 127 byte frames
0 9 collision frames 0 128 to 255 byte frames
0 10 collision frames 0 256 to 511 byte frames
0 11 collision frames 0 512 to 1023 byte frames
0 12 collision frames 0 1024 to 1518 byte frames
0 13 collision frames
0 14 collision frames 0 Flooded frames
0 15 collision frames 0 Overrun frames
0 Excessive collisions 0 VLAN filtered frames
0 Late collisions 0 Source routed frames
0 Good (1 coll) frames 0 Valid oversize frames
0 Good(>1 coll) frames 0 Pause frames
0 Pause frames 0 Symbol error frames
0 VLAN discard frames 0 Invalid frames, too large
0 Excess defer frames 0 Valid frames, too large
0 Too large frames 0 Invalid frames, too small
0 64 byte frames 0 Valid frames, too small
0 127 byte frames
0 255 byte frames
0 511 byte frames
0 1023 byte frames
0 1518 byte frames
3550-1#
!--- See the next table for additional counter output for 2900/3500XL Series switches.
| Counter | Description | Possible Causes |
|
Transmitted Frames |
||
|
Discarded frames |
The total number of frames whose transmission attempt is abandoned due to insufficient resources. This total includes frames of all destination types. |
The traffic load on the interface is excessive and causes the frames to be discarded. Reduce the traffic load on the interface if there are increments in the number of packets in this field. |
|
Too old frames |
Number of frames that took longer than two seconds to travel through the switch. For this reason, they were discarded by the switch. This only happens under extreme, high stress conditions. |
The traffic load for this switch is excessive and causes the frames to be discarded. Reduce the switch load if the number of packets in this field increase. You can need to modify your network topology to reduce the traffic load for this switch. |
|
Deferred frames |
The total number of frames whose first transmission attempt was delayed, due to traffic on the network media. This total includes only those frames that are subsequently transmitted without error and not affected by collisions. |
The traffic load destined for this switch is excessive and causes the frames to be discarded. Reduce the switch load if the number of packets in this field increase. You can need to modify your network topology to reduce the traffic load for this switch. |
|
Collision frames |
The collision frames counters are the number of times a packet was attempted to be transmitted but was not successful but was successful on its next attempt. This means that if the 2 collision frames counter incremented, the switch attempted to send the packet twice and failed but was successful on its third attempt. |
The traffic load on the interface is excessive and causes the frames to be discarded. Reduce the traffic load on the interface if you see the number of packets increase in these fields. |
|
Excessive collisions |
The excessive collisions counter increases after 16 consecutive late collisions have occurred in a row. After 16 attempts have been made to send the packet the packet is dropped, and the counter increments. |
If this counter increments, it is an indication of a wiring problem, an excessively loaded network, or a duplex mismatch. An excessively loaded network can be caused by too many devices on a shared Ethernet. |
|
Late collisions |
A late collision occurs when two devices transmit at the same time, and neither side of the connection detects a collision. The reason for this occurrence is because the time to propagate the signal from one end of the network to another is longer than the time to put the entire packet on the network. The two devices that cause the late collision never see that each sends until after it puts the entire packet on the network. Late collisions are not detected by the transmitter until after the first 64 byte slot time. This is because they are only detected in transmissions of packets longer than 64 bytes. |
Late collisions are a result of incorrect cabling or a non-compliant number of hubs in the network. Bad NICs can also cause late collisions. |
|
Good (1 coll) frames |
The total number of frames which experience exactly one collision and are then successfully transmitted. |
Collisions in a half-duplex environment are normal expected behavior. |
|
Good (>1 coll) frames |
The total number of frames which experience between 2 and 15 collisions, inclusive, and are then successfully transmitted. |
Collisions in a half-duplex environment are normal expected behavior. Frames that increment at the upper end of this counter can exceed the 15 collisions and can be counted as Excessive collisions. |
|
VLAN discardframes |
The number of frames dropped on an interface because the CFI bit is set. |
The Canonical Format Indicator (CFI) bit in the TCI of an 802.1q frame is is set to 0 for the ethernet canonical frame format. If the CFI bit is set to 1, this indicates the presence of a RIF (Routing Information Field) or Token Ring noncanonical frame which is discarded. |
|
Received Frames |
||
|
No bandwidth frames |
2900/3500XL only.The number of times that a port received a packet from the network, but the switch did not have the resources to receive it. This only happens under stress conditions but can happen with bursts of traffic on several ports. So, a small number of No bandwidth frames is not a cause for concern. (It still must be far less than one percent of the frames received.) |
The traffic load on the interface is excessive and causes the frames to be discarded. Reduce the traffic load on the interface if you see the number of packets increase in these fields. |
|
No buffers frames |
2900/3500XL only.The number of times that a port received a packet from the network, but the switch did not have the resources to receive it. This only happens under stress conditions but can happen with bursts of traffic on several ports. So, a small number of No buffers frames is not a cause for concern. (It still must be far less than one percent of the frames received.) |
The traffic load on the interface is excessive and causes the frames to be discarded. Reduce the traffic load on the interface if you see the number of packets increase in these fields. |
|
No dest, unicast |
No destination unicast are the number of unicast packets that the port did not forward to any other ports. |
These are brief descriptions of when the No dest, (unicast, multicast, and broadcast) counters can increment:
|
|
No dest, multicast |
No destination multicast are the number of multicast packets that the port did not forward to any other ports. |
|
|
No dest, broadcast |
No destination broadcast are the number of broadcast packets that the port did not forward to any other ports. |
|
|
Alignment errors |
Alignment errors are the number of frames received that do not end with an even number of octets and have a bad CRC. |
Alignment errors are due to the frame that is not completely copied to the wire, which results in fragmented frames. Alignment errors are the result of collisions at half-duplex, a duplex mismatch, bad hardware (NIC, cable, or port), or connected devices that generate frames that do not end with an octet and have a bad FCS. |
|
FCS errors |
FCS error count is the number of frames that were received with a bad checksum (CRC value) in the Ethernet frame. These frames are dropped and not propagated onto other ports. |
FCS errors are the result of collisions at half-duplex, a duplex mismatch, bad hardware (NIC, cable, or port), or connected devices that generate frames that do not end with an octet and have a bad FCS. |
|
Undersize frames |
These are the total number of packets received that were less than 64 octets long (which excludes frame bits but includes FCS) and have a good FCS value. |
This is an indication of a bad frame generated by the connected device. Verify that the connected device operates correctly. |
|
Oversize frames |
Number of packets received by the port from the network, where the packets were more than 1514 bytes. |
This can be an indication of faulty hardware, dot1q or ISL trunking configuration issues. |
|
Collision fragments |
The total number of frames whose length is less than 64 octets (which excludes frame bits, but includes FCS) and have a bad FCS value. |
If this counter increments, this is an indication that the ports are configured at half-duplex. Set the duplex to full-duplex. |
|
Overrun frames |
The number of times the receiver hardware was unable to hand received data to a hardware buffer. |
The input rate of traffic exceeded the ability of the receiver to handle the data. |
|
VLAN filtered frames |
The total number of frames which are filtered because of the type of VLAN information contained in the frame. |
The port can be configured to filter 802.1Q tagged frames. When a frame is received which contains an 802.1Q tag the frame is filtered and this statistic is incremented. |
|
Source routed frames |
The total number of receive frames that are discarded due to situation that the source route bit is set in the source address of the native frame. |
This kind of source routing is only defined for Token Ring and FDDI. The IEEE ethernet specification forbids this bit to be set in any Ethernet frame. Therefore, the switch discards such frames. |
|
Valid oversize frames |
The total number of frames received whose length exceeds the System MTU, yet which have good FCS values. |
This statistic counts frames that exceed the configured System MTU, but which can have been increased from 1518 bytes to allow for Q-in-Q or MPLS encapsulations. |
|
Symbol error frames |
Gigabit Ethernet (1000 Base-X) uses 8B/10B Encoding to translate 8bit data from the MAC sublayer(layer 2) to a 10bit Symbol to send over the wire. When a port receives a Symbol, it extracts the 8 bit data from the Symbol (10 bits). |
A Symbol error means the interface detects an undefined (invalid) Symbol received. Small amounts of symbol errors can be ignored. Large amounts of symbol errors can indicate a bad device, cable, or hardware. |
|
Invalid frames, too large |
Giant frames or frames received that exceed the maximum IEEE 802.3 frame size (1518 bytes for non-jumbo Ethernet) and have a bad Frame Check Sequence (FCS). |
In many cases, this is the result of a bad NIC. Try to find the offending device and remove it from the network. |
|
Invalid frames, too small |
Runt frames or frames received that are less than 64 bytes (which includes the FCS bits and excludes the frame header) and have either an FCS error or an alignment error. |
This can be caused by a duplex mismatch and physical problems, such as a bad cable, port, or NIC on the attached device. |
Common System Error Messages
For the Cisco IOS system messages format, you can refer to theMessages and Recovery Procedures Guidefor the release of software you run. For example, you can look at theMessages and Recovery Proceduresfor Cisco IOS Releases.
%AMDP2_FE-3-UNDERFLO
This error message is caused when a frame is transmitted, and the local buffer of the controller chip local buffer receives insufficient data. The data cannot be transferred to the chip fast enough to keep pace with output rate. Normally, such a condition is temporary, dependent upon transient peak loads within the system. The issue occurs when an excessive amount of traffic is processed by the Fast Ethernet interface. The error message is received when the traffic level reaches about 2.5 Mb. This traffic level constrain is due to hardware limitation. Because of this, a chance exists for the device connected to the catalyst switch to drop packets.
The resolution is that ordinarily the system recovers automatically. No action is required. If the switch overwhelms the Ethernet interface, check the speed and duplex setup. Also, use a sniffer program to analyze packets that come in and out of the router fast Ethernet interface. In order to avoid packet drops on the device connected to the catalyst switch, issue theip cefcommand on the fast Ethernet interface of the device connected to the switch.
%INTR_MGR-DFC1-3-INTR: Queueing Engine (Blackwater) [1]: FIC Fabric-A Received Unexpected Control Code
The reason for this error message is the receipt of a packet from the switch fabric, where the CRC value in the fabric header on that packet did not match the CRC value calculated by the Fabric Interface Controller (FIC) subblock of the Blackwater ASIC. This indicates that a corruption of the packet occurred within transfer, and Blackwater received the corrupted packet.
Command Rejected: [Interface] not a Switching Port
In switches that support both L3 interfaces and L2 switchport, the message «Command rejected: [interface] not a switching port»displays when you try to enter a command related to layer 2 on a port that is configured as a layer 3 interface.
In order to convert the interface from layer 3 mode to layer 2 mode, issue the interface configuration commandswitchport. After you issue this command, configure the port for any layer 2 properties.
Common Port and Interface Problems
Port or Interface Status is Disable or Shutdown
An obvious but sometimes overlooked cause of port connectivity failure is an incorrect configuration on the switch. If a port has a solid orange light, this means the software inside the switch shut down the port, either by way of the user interface or by internal processes.
Note: Some port LEDs of the platform work differently in regard to STP. For example, the Catalyst 1900/2820 turns ports orange when they are in STP block mode. In this case, an orange light can indicate the normal functions of the STP. The Catalyst 6000/4000 does not turn the port light orange when it blocks for STP.
Make sure the port or module has not been disabled or powered down for some reason. If a port or module is manually shut down on one side of the link or the other, the link does not come up until you re-enable the port. Check the port status on both sides. Use theshow run interfacecommand and check to see if the interface is in ashutdownstate:
Switch#show run interface fastEthernet 4/2 ! interface FastEthernet4/2 switchport trunk encapsulation dot1q switchport mode trunk shutdown duplex full speed 100 end
!--- Use the no shut command in config-if mode to re-enable this interface.
If the port goes into shutdown mode immediately after a reboot of the switch, the probable cause is the port security setup. If unicast flooding is enabled on that port, it can cause the port to shut down after a reboot. Cisco recommends that you disable the unicast flooding because it also ensure that no flooding occurs on the port once the MAC address limit is reached.
Port or Interface Status is errDisable
By default, software processes inside the switch can shut down a port or interface if certain errors are detected.
When you look at show interfacecard-type {slot/port}statuscommand for Cisco IOS:
Router#show interface fastethernet 2/4 status Port Name Status Vlan Duplex Speed Type Gi2/4 err-disabled 1 full 1000 1000BaseSX
!--- The show interfaces card-type {slot/port} status command for Cisco IOS !--- displays a status of errdisabled. !--- The show interfaces status errdisabled command shows all the interfaces !--- in this status.
Theshow loggingcommand for Cisco IOS also display the error messages (exact message format varies) that relate to the errdisable state.
Wheb ports or interlaces are shut down as a result of errdisable are referred to as causes in Cisco IOS. The causes for this range from EtherChannel misconfiguration that causes a PAgP flap, duplex mismatch, BPDU port-guard and portfast configured at the same time, UDLD that detects a one-way link, and so on.
You have to manually re-enable the port or interface to take it out the errdisable state unless you configure an errdisable recovery option. InCisco IOS software you have the ability to automatically re-enable a port after a configurable amount of time spent in the errdisable state. The bottom line is that even if you configure the interface to recover from errdisable the problem reoccurs until the root cause is determined.
Note: Use this Recover Errdisable Port State on Cisco IOS Platforms for more information on errdisable status on switches that run Cisco IOS.
This table shows an example of the commands used to configure verify and troubleshoot the errdisable status on switches. Navigate to the link for more information about the commands Recover Errdisable Port State on Cisco IOS Platforms:
| Action | Cisco IOS errdisable Commands |
|---|---|
| Configure | errdisable detect cause |
| Configure | errdisable recovery cause |
| Configure | errdisable recovery interval <timer_interval_in_seconds> |
| Verify & Troubleshoot | show errdisable detect |
| Verify & Troubleshoot | show interfaces status err-disabled |
Port or Interface Status is Inactive
One common cause of inactive ports on switches that run Cisco IOS is when the VLAN they belong to disappears. This can occur when interfaces are configured as layer 2 switchports that use theswitchportcommand.
Every port in a Layer 2 switch belongs to a VLAN. Every port on a Layer 3 switch configured to be a L2 switchport must also belong to a VLAN. If that VLAN is deleted, then the port or interface becomes inactive.
Note: Some switches show a steady orange (amber) light on each port when this happens.
Use theshow interfacescard-type {slot/port}switchportcommand along withshow vlanto verify.
Router#show interfaces fastEthernet 4/47 switchport Name: Fa4/47Switchport: Enabled Administrative Mode: static access Operational Mode: static access Administrative Trunking Encapsulation: negotiate Operational Trunking Encapsulation: native Negotiation of Trunking: Off Access Mode VLAN: 11 ((Inactive))
!--- FastEth 4/47 is inactive. Router#show vlan VLAN Name Status Ports ---- -------------------------------- --------- ------------------------------- 1 default active Gi1/1, Gi2/1, Fa6/6 10 UplinkToGSR's active Gi1/2, Gi2/2
!--- VLANs are displayed in order and VLAN 11 is not available.
30 SDTsw-1ToSDTsw-2Link active Fa6/45
If the switch that deleted the VLAN is a VTP server for the VTP domain, every server and client switch in the domain has the VLAN removed from their VLAN table as well. When you add the VLAN back into the VLAN table from a VTP server switch, the ports of the switches in the domain that belong to that restored VLAN become active again. A port remembers what VLAN it is assigned to, even if the VLAN itself is deleted. Refer toUnderstanding and Configuring VLAN Trunk Protocol (VTP)for more information on VTP.
Note: If the output of theshow interface <interface> switchportcommand displays the port as a trunk port even after you configure the port as an access port with theswitchport access vlan <vlan>command, issue theswitchport mode accesscommand in order to make the port an access port.
Uplink Port or Interface Status is Inactive
On a Catalyst 4510R series switch, in order to enable both the 10-Gigabit Ethernet and the Gigabit Ethernet SFP uplink ports, there is an optional configuration. In order to enable the simultaneous use of 10-Gigabit Ethernet and the Gigabit Ethernet SFP interfaces, issue thehw-module uplink select allcommand. After you issue the command, re-boot the switch or else the output of theshow interface status module <module number>command shows the uplink port as inactive.
Cisco IOS Software Release 12.2(25)SG supports the simultaneous use of 10-Gigabit Ethernet and the Gigabit Ethernet SFP interfaces on Catalyst 4500 switches.
Note: On the Catalyst 4503, 4506, and 4507R series switches, this capability is automatically enabled.
Deferred Counter on the Catalyst Switch Interface Increments
The issue is because the traffic load destined for the switch is excessive and causes the frames to be discarded. Normally the deferred frames are the number of frames that have been transmitted successfully after waiting for the media, because the media was busy. This is usually seen in half-duplex environments where the carrier is already in use when it tries to transmit a frame. But in full duplex environments the issue occurs when the excessive load is destined for the switch.
This is the workaround:
-
Hardcode both ends of the link to full duplex so that the negotiation mismatch can be avoided.
-
Change the cable and patch panel cord to ensure that the cable and patch cords are not defective.
Note: If the Deferred Counter error increments on a GigabitEthernet of a Supervisor 720, turn on speed negotiation on the interface as a workaround.
Intermittent Failure to set timer [value] from vlan [vlan no]
The issue occurs when Encoded Address Recognition Logic (EARL) is unable to set the CAM aging time for the VLAN to the required number of seconds. Here, the VLAN aging time is already set to fast aging.
When the VLAN is already in fast aging, EARL cannot set the VLAN to fast aging, and aging timer set process is blocked. The default CAM aging time is five minutes, which means that the switch flushes the table of learned MAC addresses every five minutes. This ensures that the MAC address table (the CAM table) contains the most recent entries.
Fast aging temporarily sets the CAM aging time to the number of seconds that the user specifies, and is used in conjunction with the Topology Change Notification (TCN) process. The idea is that when a topology change occurs, this value is necessary to flush the CAM table faster, to compensate for the topology change.
Issue theshow cam agingcommand to check the CAM aging time on the switch. TCNs and fast aging are fairly rare. As a result, the message has a severity level of 3. If the VLANs are frequently in fast aging, check the reason for fast aging.
The most common reason for TCNs is client PCs connected directly to a switch. When you power up or down the PC, the switch port changes state, and the switch starts the TCN process. This is because the switch does not know that the connected device is a PC; the switch only knows that the port has changed the state.
In order to resolve this issue, Cisco has developed the PortFast feature for host ports. An advantage of PortFast is that this feature suppresses TCNs for a host port.
Note: PortFast also bypasses spanning-tree calculations on the port, and is therefore only suitable for use on a host port.
Trunking Mode Mismatch
Check the trunking mode on each side of the link. Make sure both sides are in the same mode (both trunking with the same method: ISL or 802.1q, or both not trunking). If you turn the trunking mode to on (as opposed to auto or desirable) for one port and the other port has the trunking mode set to off, they are not able to communicate. Trunking changes the formatting of the packet. The ports need to be in agreement as to what format they use on the link, or they do not understand each other.
For Cisco IOS, use theshow interfacescard-type {mod/port}trunkcommand to verify the trunking configuration and Native VLAN.
Router#sh interfaces fastEthernet 6/1 trunk Port Mode Encapsulation Status Native vlan Fa6/1 desirable 802.1q trunking 1 Port Vlans allowed on trunk Fa6/1 1-4094 !--- Output truncated.
Refer to these documents for more information on the different trunking modes, guidelines, and restrictions:
-
System Requirements to Implement Trunking
-
Trunking Technology Support Page
Jumbos, Giants, and Baby Giants
The Maximum Transmission Unit (MTU) of the data portion of an ethernet frame is 1500 bytes by default. If the transmitted traffic MTU exceeds the supported MTU the switch does not forward the packet. Also, dependent upon the hardware and software, some switch platforms increment port and interface error counters as a result.
-
Jumbo frames are not defined as part of the IEEE Ethernet standard and are vendor-dependent. They can be defined as any frame bigger than the standard ethernet frame of 1518 bytes (which includes the L2 header and Cyclic Redundancy Check (CRC)). Jumbos have larger frame sizes, typically > 9000 bytes.
-
Giant frames are defined as any frame over the maximum size of an ethernet frame (larger than 1518 bytes) that has a bad FCS.
-
Baby Giant frames are just slightly larger than the maximum size of an ethernet frame. Typically this means frames up to 1600 bytes in size.
Support for jumbo and baby giants on Catalyst switches varies by switch platform, sometimes even by modules within the switch. The software version is also a factor.
Refer toConfiguring Jumbo/Giant Frame Support on Catalyst Switchesfor more information on system requirements, configure and troubleshoot for jumbo and baby giant issues.
Cannot Ping End Device
Check the end device with a ping sent from the directly connected switch first, then work your way back port by port, interface by interface, trunk by trunk until you find the source of the connectivity issue. Make sure each switch can see the end device MAC address in its Content-Addressable Memory (CAM) table.
Use theshow mac address-table dynamiccommand or substitute theinterfacekeyword.
Router# show mac-address-table interface fastEthernet 6/3 Codes: * - primary entry vlan mac address type learn qos ports ------+----------------+--------+-----+---+-------------------------- * 2 0040.ca14.0ab1 dynamic No -- Fa6/3
!--- A workstation on VLAN 2 with MAC address 0040.ca14.0ab1 is directly connected !--- to interface fastEthernet 6/3 on a switch running Cisco IOS.
Once you know the switch actually has the MAC address of the device in the CAM table, determine whether this device is on the same or different VLAN from where you try to ping.
If the end device is on a different VLAN from where you try to ping, a L3 switch or router must be configured to allow the devices to communicate. Make sure your L3 addressing on the end device and on the router/ L3 switch is correctly configured. Check the IP address, subnet mask, default gateway, dynamic routing protocol configuration, static routes, and so on.
Use of Switchport Host to Fix Startup Delays
If stations are not able to talk to their primary servers when they connect through the switch, the problem can involve delays on the switch port when it tries to become active after the physical layer link comes up. In some cases, these delays can be up to 50 seconds. Some workstations simply cannot wait this long to find their server and then they give up. These delays are caused by STP, trunking negotiations (DTP), and EtherChannel negotiations (PAgP). All of these protocols can be disabled for access ports where they are not needed, so the switch port or interface starts forwarding packets a few seconds after it establishes a link with its neighbor device.
In Cisco IOS, you can use theswitchport host command to disable channeling and to enable spanning-tree portfast and theswitchport nonegotiatecommand to turn off DTP negotiation packets. Use theinterface-range command to do this on multiple interfaces at once.
Router6k-1(config)#interface range fastEthernet 6/13 - 18 Router6k-1(config-if-range)#switchport Router6k-1(config-if-range)#switchport host switchport mode can be set to access spanning-tree portfast can be enabled channel group can be disabled !--- Etherchannel is disabled and portfast is enabled on interfaces 6/13 - 6/18. Router6k-1(config-if-range)#switchport nonegotiate !--- Trunking negotiation is disabled on interfaces 6/13 - 6/18. Router6k-1(config-if-range)#end Router6k-1#
Cisco IOS has the option to use theglobal spanning-tree portfast defaultcommand to automatically apply portfast to any interface configured as a layer 2 access switchport. Check the Command Reference for your release of software to verify the availability of this command. You can also use thespanning-tree portfastcommand per interface, but this requires that you turn off trunking and etherchannel separately to help fix workstation startup delays.
Note: Refer toUsing Portfast and Other Commands to Fix Workstation Startup Connectivity Delaysfor more information how to fix startup delays.
Speed/Duplex, auto-negotiation, or NIC Issues
If you have a large amount of alignment errors, FCS errors, or late collisions, this can indicate one of these:
-
Duplex Mismatch
-
Bad or Damaged Cable
- NIC Card Issues
Duplex Mismatch
A common issue with speed/duplex is when the duplex setup are mismatched between two switches, between a switch and a router or between the switch and a workstation or server. This can occur when you manually hardcode the speed and duplex or from auto-negotiation issues between the two devices.
If the mismatch occurs between two Cisco devices with the Cisco Discovery Protocol (CDP) enabled, you see the CDP error messages on the console or in the logging buffer of both devices. CDP is useful to detect errors, as well as port and system statistics on nearby Cisco devices. CDP is Cisco proprietary and works when you send packets to a well-known MAC address 01-00-0C-CC-CC-CC.
The example shows the log messages that result from a duplex mismatch between two Catalyst 6000 series switches: one that runs CatOS, and the other that runs Cisco IOS. These messages generally tell you what the mismatch is and where it occurs.
2003 Jun 02 11:16:02 %CDP-4-DUPLEXMISMATCH:Full/half duplex mismatch detected on port 3/2 !--- CatOS switch sees duplex mismatch.
Jun 2 11:16:45 %CDP-4-DUPLEX_MISMATCH: duplex mismatch discovered on FastEthernet6/2 (not half duplex), with TBA04251336 3/2 (half duplex). !--- Cisco IOS switch sees duplex mismatch.
Use theshow cdp neighborscard-type <slot/port>detailcommand to display CDP information for Cisco neighbor devices.
Router#show cdp neighbors fastEthernet 6/1 detail ------------------------- Device ID: TBA04251336 Entry address(es): IP address: 10.1.1.1 Platform: WS-C6006, Capabilities: Trans-Bridge Switch IGMP Interface: FastEthernet6/1, Port ID (outgoing port): 3/1 Holdtime : 152 sec Version : WS-C6006 Software, Version McpSW: 6.3(3) NmpSW: 6.3(3) Copyright (c) 1995-2001 by Cisco Systems !--- Neighbor device to FastEth 6/1 is a Cisco Catalyst 6000 Switch !--- on port 3/1 running CatOS. advertisement version: 2 VTP Management Domain: 'test1' Native VLAN: 1 Duplex: full !--- Duplex is full. Router#
setup auto speed/duplex on one side and 100/Full-duplex on the other side is also a misconfiguration and can result in a duplex mismatch. If the switch port receives a lot of late collisions, this usually indicates a duplex mismatch problem and can place the port in an errdisable status in a result. The half-duplex side only expects packets at certain times, not at any time, and therefore counts packets received at the wrong time as collisions. There are other causes for late collisions besides duplex mismatch, but this is one of the most common reasons. Always set both sides of the connection to auto-negotiate speed/duplex or set the speed/duplex manually on both sides.
Use theshow interfaces <card-type> <slot/port>statuscommand to display speed and duplex setup as well as other information. Use thespeedandduplexcommands from interface configuration mode to hardcode both sides to 10 or 100 and half or full as necessary.
Router#show interfaces fasstEthernet 6/1 status Port Name Status Vlan Duplex Speed Type Fa6/1 connected 1 a-full a-100 10/100BaseTX
If you use theshow interfacescommand without thestatusoption, you see a setup for speed and duplex, but you do not know whether this speed and duplex was achieved through auto-negotiation or not.
Router#sh int fas 6/1
FastEthernet6/1 is up, line protocol is up (connected)
Hardware is C6k 100Mb 802.3, address is 0009.11f3.8848 (bia 0009.11f3.8848)
MTU 1500 bytes, BW 100000 Kbit, DLY 100 usec,
reliability 255/255, txload 1/255, rxload 1/255
Encapsulation ARPA, loopback not set
Full-duplex, 100Mb/s
!--- Full-duplex and 100Mbps does not tell you whether autoneg was used to achieve this.
!--- Use the sh interfaces fas 6/1 status command to display this.
Bad or damaged cable
Always check the cable for marginal damage or failure. A cable can be just good enough to connect at the physical layer, but it corrupts packets as a result of subtle damage to the wiring or connectors. Check or swap the copper or fiber cable. Swap the GBIC (if removable) for fiber connections. Rule out any bad patch panel connections or media convertors between source and destination. Try the cable in another port or interface if one is available and see if the problem continues.
Auto negotiation and NIC Card Issues
Problems sometimes occur between Cisco switches and certain third-party NIC cards. By default, Catalyst switch ports and interfaces are set to autonegotiate. It is common for devices like laptops or other devices to be set to autonegotiate as well, yet sometimes autonegotation issues occur.
In order to troubleshoot auto-negotiation problems it is often recommended to try and hardcode both sides. If neither auto-negotiation or hardcode setup seem to work, there can be a problem with the firmware or software on your NIC card. Upgrade the NIC card driver to the latest version available on the web site of the manufacture to resolve this.
Refer toConfiguring and Troubleshooting Ethernet 10/100/1000 MB Half/Full Duplex Auto-Negotiationfor details on how to resolve speed/duplex and auto-negotiation issues.
Refer toTroubleshooting Cisco Catalyst Switches to NIC Compatibility Issuesfor details on how to resolve third-party NIC issues.
Spanning Tree Loops
Spanning Tree Protocol (STP) loops can cause serious performance issues that masquerade as port or interface problems. In this situation, your bandwidth is used by the same frames over and over again, which leaves little room for legitimate traffic.
The STP loop guard feature provides additional protection against Layer 2 forwarding loops (STP loops). An STP loop is created when an STP block port in a redundant topology erroneously transitions to the forwarding state. This usually happens because one of the ports of a physically redundant topology (not necessarily the STP block port) no longer receives STP BPDUs. In its operation, STP relies on continuous reception or transmission of BPDUs based on the port role. The designated port transmits BPDUs, and the non-designated port receives BPDUs.
When one of the ports in a physically redundant topology no longer receives BPDUs, the STP conceives that the topology is loop free. Eventually, the block port from the alternate or backup port becomes designated and moves to a forwarding state. This situation creates a loop.
The loop guard feature makes additional checks. If BPDUs are not received on a non-designated port, and loop guard is enabled, that port is moved into the STP loop-inconsistent block state, instead of the listening / learning / forwarding state. Without the loop guard feature, the port assumes the designated port role. The port moves to the STP forwarding state and creates a loop. Refer toSpanning-Tree Protocol Enhancements using Loop Guard and BPDU Skew Detection Featuresfor more information on the loop guard feature.
This document covers reasons that STP can fail, what information to look for to identify the source of the problem, and what kind of design minimizes STP risks.
Loops can also be caused by a uni-directional link. For more information, refer to the UDLD: One-Way link problems section of this document.
UDLD: One-Way Link
A unidirectional link is a link where traffic goes out one way, but no traffic is received in the ingress direction. The switch does not know that the link ingress direction is bad (the port thinks that the link is up and works).
A broken fiber cable or other cabling/port issues can cause this one-way only communication. These partially functional links can cause problems such as STP loops when the switches involved do not know that the link is partially broken. UDLD can put a port in errdisable state when it detects a unidirectional link. The command udld aggressive-mode can be configured on switches that run Cisco IOS (check release notes for command availability) for point-to-point connections between switches where unidirectional links cannot be tolerated. The use of this feature can help you identify difficult to find unidirectional link problems
Refer toUnderstand and Configure the Unidirectional Link Detection Protocol (UDLD) Featurefor configuration information on UDLD.
Deferred Frames (Out-Lost or Out-Discard)
If you have a large number of deferred frames, or Out-Discard (also referred to as Out-Lost on some platforms), it means that the switch output buffers have filled up and the switch had to drop these packets. This can be a sign that this segment is run at an inferior speed and/or duplex, or there is too much traffic that goes through this port.
Use theshow interfaces counters errorcommand to look at OutDiscards.
Router#show interfaces counters error Port Align-Err FCS-Err Xmit-Err Rcv-Err UnderSize OutDiscards Fa7/47 0 0 0 0 0 0 Fa7/48 0 0 0 0 0 2871800 Fa8/1 0 0 0 0 0 2874203 Fa8/2 103 0 0 103 0 2878032 Fa8/3 147 0 0 185 0 0 Fa8/4 100 0 0 141 0 2876405 Fa8/5 0 0 0 0 0 2873671 Fa8/6 0 0 0 0 0 2 Fa8/7 0 0 0 0 0 0
!--- The show interfaces counters errors command shows certain interfaces !--- that increment in large amounts OutDiscards while others run clean.
Investigate these common causes of output buffer failures:
Inferior Speed/Duplex for the Amount of Traffic
Your network can send too many packets through this port for the port to handle at its current speed/duplex setup. This can happen where you have multiple high-speed ports flowing to a single (usually slower) port. You can move the device that hangs off this port to faster media. For example, if the port is 10 Mbps, move this device to a 100 Mbps or Gigabit port. You can change the topology to route frames differently.
Congestion Issues: Segment Too Busy
If the segment is shared, other devices on this segment can transmit so much that the switch has no opportunity to transmit. Avoid daisy-chained hubs whenever possible. Congestion can lead to packet loss. Packet loss causes retransmissions at the transport layer which in turn causes users to experience latency at the application level. You can upgrade10Mbps links to 100Mbps or Gigabit Ethernet links when possible. You can remove some devices from crowded segments to other less populated segments. Make congestion avoidance a priority on your network.
Applications
At times the traffic transmission characteristics of the applications used can lead to output buffer problems. NFS file transfers that come from a Gigabit attached server that uses user datagram protocol (UDP) with a 32K window size is one example of an application setup that can bring out this type of problem. If you have checked or tried the other suggestions in this document (checked speed/duplex, no physical errors on the link, all the traffic is normal valid traffic, and so on), then reduce the unit size that is sent by the application which can help to alleviate this problem.
Software Problems
If you see behavior that can only be considered strange, you can isolate the behavior to a specific box, and you have looked at everything suggested so far, this can indicate software or hardware problems. It is usually easier to upgrade the software than it is to upgrade hardware. Change the software first.
Use theshow versioncommand to verify the current software version along with thedir flash: ordir bootflash: (dependent upon the platform) command to verify the available flash memory for the upgrade:
Router#show version Cisco Internetwork Operating System Software IOS (tm) Catalyst 4000 L3 Switch Software (cat4000-IS-M), Version 12.1(13)EW, EA RLY DEPLOYMENT RELEASE SOFTWARE (fc1) TAC Support: http://www.cisco.com/tac Copyright (c) 1986-2002 by cisco Systems, Inc. Compiled Fri 20-Dec-02 13:52 by eaarmas Image text-base: 0x00000000, data-base: 0x00E638AC ROM: 12.1(12r)EW Dagobah Revision 71, Swamp Revision 24 trunk-4500 uptime is 2 weeks, 2 days, 6 hours, 27 minutes System returned to ROM by redundancy reset System image file is "bootflash:cat4000-is-mz.121-13.EW.bin"
!--- Typical Cisco IOS show version output. Router#dir bootflash: Directory of bootflash:/ 1 -rw- 8620144 Mar 22 2002 08:26:21 cat4000-is-mz.121-13.EW.bin 61341696 bytes total (52721424 bytes free)
!--- Verify available flash memory on switch running Cisco IOS.
How to Upgrade Software
For information on how to upgrade software for your Cisco Switches, navigate to link, choose your platform and look at the Software Configuration section.
Hardware Software Incompatibility
There can be a situation where the software is not compatible with the hardware. This happens when new hardware comes out and requires special support from the software. For more information on software compatibility, use the Software Advisor tool.
Software Bugs
The operating system can have a bug. If you load a newer software version, it can often fix this. You can search known software bugs with the Software Bug Toolkit.
Corrupt Images
An image can have become corrupted. For information in regard to the recovery from corrupted images, choose your platform Switch and look at the Troubleshoot section.
Hardware Problems
Check the results ofshow modulefor Catalyst 6000 and 4000 series switches that run Cisco IOS.
Check the results of the POST results from the switch to see if there were any failures indicated for any part of the switch. Failures of any test of a module or port show an ‘F’ in the test results.
For Cisco IOS, on modular switches like the Cat6000, use the commandshow diagnostics. In order to see POST results per module, use theshow diagnostics module<module> command.
ecsj-6506-d2#sh diagnostic module 3
Current Online Diagnostic Level = Minimal
!--- The diagnostic level is set to minimal which is a shorter,
!--- but also less thorough test result.
!--- You may wish to configure diagnostic level complete to get more test results.
Online Diagnostic Result for Module 3 : MINOR ERROR
Online Diagnostic Level when Line Card came up = Minimal
Test Results: (. = Pass, F = Fail, U = Unknown)
1 . TestLoopback :
Port 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24
----------------------------------------------------------------------------
. . . . . . . . . . . . . . . . . . F F F F F F
!--- Notice the MINOR ERROR test result and failed loopback test which means
!--- these ports are currently unusable.
!--- Use the hw-module{mod}reset command or, if necessary, physically reseat the
!--- module to try and fix this problem.
!--- If these steps fail, open a case with Cisco Technical Support.
Note: For Catalyst 3750, 3550, 2970 , 2950/2955, and 2900/3500XL Series switches use theshow postcommand, which indicates a simple pass or fail for the hw status. Use the LEDs on these switches to help you understand the POST results.
For further information on how to troubleshoot hardware problems on Catalyst switches that run Cisco IOS, navigate to the Cisco Switches support pages, choose your platform and look at the Troubleshooting > Hardwaresection. For possible issues related to Field Notices, refer toField Noticesfor LAN and ATM Switches.
Input Errors on a Layer 3 Interface Connected to a Layer 2 Switchport
By default, all layer 2 ports are indynamic desirablemode, so the layer 2 port tries to form a trunk link and sends out DTP packets to the remote device. When a layer 3 interface is connected to a layer 2 switchport, it is not able to interpret these frames, which results in Input errors, WrongEncap errors, and Input queue drops.
In order to resolve this, change the mode of the switch port tostatic accessortrunkas per your requirement.
Switch2(config)#interface fastEthernet1/0/12 Switch2(config-if)#switchport mode access
Or
Switch2(config)#interface fastEthernet1/0/12
Switch2(config-if)#switchport trunk encapsulation dot1q
Switch2(config-if)#switchport mode trunk
Rapidly Increment Rx-No-Pkt-Buff Counter and Input Errors
The Rx-No-Pkt-Buff counter can increase on ports when it has blades, such as WS-X4448-GB-RJ45, WS-X4548-GB-RJ45, and WS-X4548-GB-RJ45V. Also, some packet drop incrementation is normal and is the result of traffic bursts traffic.
These types of errors increase rapidly, especially when the traffic that passes through that link is high or when it has devices such as servers connected to that interface. This high load of traffic oversubscribes the ports, which exhausts the input buffers and causes the Rx-No-Pkt-Buff counter and input errors to increase rapidly.
If a packet cannot be completely received because the switch is out of packet buffers, this counter is incremented once for every dropped packet. This counter indicates the internal state of the Switching ASICs on the Supervisor and does not necessarily indicate an error condition.
Pause Frames
When the receive part (Rx) of the port has its Rx FIFO queue filled and reaches the high water mark, the transmit part (Tx) of the port starts to generate pause frames with an interval value mentioned in it. The remote device is expected to stop / reduce the transmission of packets for the interval time mentioned in the pause frame.
If the Rx is able to clear the Rx queue or reach low water mark within this interval, Tx sends out a special pause frame that mentions the interval as zero (0x0). This enables the remote device to start to transmit packets.
If the Rx still works on the queue, once the interval time expires, the Tx sends a new pause frame again with a new interval value.
If Rx-No-Pkt-Buff is zero or does not increment and the TxPauseFrames counter increments, it indicates that our switch generates pause frames and the remote end obeys, hence Rx FIFO queue depletes.
If Rx-No-Pkt-Buff increments and TxPauseFrames also increments, it means that the remote end disregards the pause frames (does not support flow control) and continues to send traffic despite the pause frames. In order to overcome this situation, manually configure the speed and duplex, as well as disable the flow control, if required.
These types of errors on the interface are related to a traffic problem with the ports oversubscribed. The WS-X4448-GB-RJ45, WS-X4548-GB-RJ45, and WS-X4548-GB-RJ45V switching modules have 48 oversubscribed ports in six groups of eight ports each:
-
Ports 1, 2, 3, 4, 5, 6, 7, 8
-
Ports 9, 10, 11, 12, 13, 14, 15, 16
-
Ports 17, 18, 19, 20, 21, 22, 23, 24
-
Ports 25, 26, 27, 28, 29, 30, 31, 32
-
Ports 33, 34, 35, 36, 37, 38, 39, 40
-
Ports 41, 42, 43, 44, 45, 46, 47, 48
The eight ports within each group use common circuitry that effectively multiplexes the group into a single, non-block, full-duplex Gigabit Ethernet connection to the internal switch fabric. For each group of eight ports, the frames that are received are buffered and sent to the common Gigabit Ethernet link to the internal switch fabric. If the amount of data received for a port begins to exceed buffer capacity, flow control sends pause frames to the remote port to temporarily stop traffic and prevent frame loss.
If the frames received on any group exceeds the bandwidth of 1 Gbps, the device starts to drop the frames. These drops are not obvious as they are dropped at the internal ASIC rather than the actual interfaces. This can lead to slow throughput of packets across the device.
The Rx-No-Pkt-Buff does not depend on the total traffic rate. It depends on the amount of the packets that are stored in the Rx FIFO buffer of the module ASIC. The size of this buffer is only 16 KB. It is counted with short traffic bursts flow when some packets fill this buffer. Thus, Rx-No-Pkt-Buff on each port can be counted when the total traffic rate of this ASIC port group exceeds 1 Gbps, since WS-X4548-GB-RJ45 is 8:1 oversubscribed module.
When you have devices that need to carry a large amount of traffic through that interface, consider the use of one port of each group so that the common circuitry that shares a single group is not affected by this amount of traffic. When the Gigabit Ethernet switching module is not fully utilized, you can balancee the port connections across port groupings to maximize available bandwidth. For example, with the WS-X4448-GB-RJ45 10/100/1000 switching module, you can connect ports from different groups, such as ports 4, 12, 20, or 30 (in any order), before you connect ports from the same group, such as ports 1, 2, 3, 4, 5, 6, 7, and 8. If this does not solve the issue, you need to consider a module without any oversubscription of ports.
Understand Unknown Protocol Drops
Unknown protocol dropsis a counter on the interface. It is caused by protocols that are not understood by the router/switch. This example of theshow run interfacecommand shows the unknown protocol drops on the GigabitEthernet 0/1 interface.
Switch#show run interface GigabitEthernet0/1
GigabitEthernet0/1 is up, line protocol is up
Hardware is BCM1125 Internal MAC, address is 0000.0000.0000 (via 0000.0000)
MTU 1500 bytes, BW 1000000 Kbit/sec, DLY 10 usec,
reliability 255/255, txload 1/255, rxload 1/255
Encapsulation 802.1Q Virtual LAN, Vlan ID 1., loopback not set
Keepalive set (10 sec)
Full-duplex, 1000Mb/s, media type is RJ45
output flow-control is XON, input flow-control is XON
ARP type: ARPA, ARP Timeout 04:00:00
Last input 00:00:05, output 00:00:03, output hang never
Last clearing of "show interface" counters 16:47:42
Input queue: 0/75/0/0 (size/max/drops/flushes); Total output drops: 0
Queueing strategy: fifo
Output queue: 0/40 (size/max)
5 minute input rate 0 bits/sec, 0 packets/sec
5 minute output rate 0 bits/sec, 0 packets/sec
3031 packets input, 488320 bytes, 0 no buffer
Received 3023 broadcasts, 0 runts, 0 giants, 0 throttles
0 input errors, 0 CRC, 0 frame, 0 overrun, 0 ignored
0 watchdog, 63107 multicast, 0 pause input
0 input packets with dribble condition detected
7062 packets output, 756368 bytes, 0 underruns
0 output errors, 0 collisions, 0 interface resets
2015 unknown protocol drops
4762 unknown protocol drops
0 babbles, 0 late collision, 0 deferred
0 lost carrier, 0 no carrier, 0 pause output
0 output buffer failures, 0 output buffers swapped out
Unknown protocol drops are normally dropped because the interface where these packets are received is not configured for this type of protocol, or it can be any protocol that the router does not recognize. For example, if you have two routers connected and you disable CDP on one router interface, this results in unknown protocol drops on that interface. The CDP packets are no longer recognized, and they are dropped.
Trunking between a Switch and a Router
Trunk links between a switch and a router can make the switchport go down. Trunk can come up after you disable and enable the switchport, but eventually the switchport can go down again.
In order to resolve this issue, complete these steps:
-
Make sure Cisco Discovery Protocol (CDP) runs between the switch and router and both can see each other.
-
Disable theKeepaliveson the interface of the router.
-
Reconfigure the trunk encapsulation on both devices.
When the keepalives are disabled, the CDP enables link to operate normally.
Connectivity Issues due to Oversubscription
When you use either the WS-X6548-GE-TX or WS-X6148-GE-TX modules, there is a possibility that individual port utilization can lead to connectivity problems or packet loss on the surrounding interfaces. Refer toInterface/Module Connectivity Problemsfor more information on oversubscription.
Sub Interfaces in SPA Modules
In SPA modules, after you create a sub interface with 802.1Q, the same VLAN is not usable on the switch. Once you have encapsulation dot1q on a subinterface, you can no longer use that VLAN in the system because the 6500 or 7600 internally allocates the VLAN and makes that sub interface its only member. In order to resolve this issue, create trunk ports instead of sub interfaces. That way, the VLAN can be seen in all interfaces.
Troubleshoot Output Drops
Typically, the output drops can occur if QoS is configured and does not provide enough bandwidth to certain class of packets. It also occurs when the hardware hits an oversubscription.
For example, here you see a high amount of output drops on the interface GigabitEthernet 8/9 on a Catalyst 6500 Series Switch:
Switch#show interface GigabitEthernet8/9
GigabitEthernet8/9 is up, line protocol is up (connected)
Hardware is C6k 1000Mb 802.3, address is 0013.8051.5950 (bia 0013.8051.5950)
Description: Connection To Bedok_Core_R1 Ge0/1
MTU 1500 bytes, BW 1000000 Kbit, DLY 10 usec,
reliability 255/255, txload 18/255, rxload 23/255
Encapsulation ARPA, loopback not set
Keepalive set (10 sec)
Full-duplex, 1000Mb/s, media type is SX
input flow-control is off, output flow-control is off
Clock mode is auto
ARP type: ARPA, ARP Timeout 04:00:00
Last input 00:00:28, output 00:00:10, output hang never
Last clearing of "show interface" counters never
Input queue: 0/2000/3/0 (size/max/drops/flushes); Total output drops: 95523364
Queueing strategy: fifo
Output queue: 0/40 (size/max)
5 minute input rate 94024000 bits/sec, 25386 packets/sec
5 minute output rate 71532000 bits/sec, 24672 packets/sec
781388046974 packets input, 406568909591669 bytes, 0 no buffer
Received 274483017 broadcasts (257355557 multicasts)
0 runts, 0 giants, 0 throttles
3 input errors, 2 CRC, 0 frame, 0 overrun, 0 ignored
0 watchdog, 0 multicast, 0 pause input
0 input packets with dribble condition detected
749074165531 packets output, 324748855514195 bytes, 0 underruns
0 output errors, 0 collisions, 3 interface resets
0 babbles, 0 late collision, 0 deferred
0 lost carrier, 0 no carrier, 0 PAUSE output
0 output buffer failures, 0 output buffers swapped out
In order to analyze the problem, collect the output of these commands:
-
show fabric utilization detail
-
show fabric errors
-
show platform hardware capacity
-
show catalyst6000 traffic-meter
-
show platform hardware capacity rewrite-engine drop
Last Input Never from the Output of Show interface Command
This example of the show interface command shows theLast input neveron the TenGigabitEthernet1/15 interface.
Switch#show interface TenGigabitEthernet1/15
TenGigabitEthernet1/15 is up, line protocol is up (connected)
Hardware is C6k 10000Mb 802.3, address is 0025.84f0.ab16 (bia 0025.84f0.ab16)
Description: lsnbuprod1 solaris
MTU 1500 bytes, BW 10000000 Kbit, DLY 10 usec,
reliability 255/255, txload 1/255, rxload 1/255
Encapsulation ARPA, loopback not set
Keepalive set (10 sec)
Full-duplex, 10Gb/s
input flow-control is off, output flow-control is off
ARP type: ARPA, ARP Timeout 04:00:00
Last input never, output 00:00:17, output hang never
Last clearing of "show interface" counters 2d22h
Input queue: 0/2000/0/0 (size/max/drops/flushes); Total output drops: 0
Queueing strategy: fifo
Output queue: 0/40 (size/max)
5 minute input rate 0 bits/sec, 0 packets/sec
5 minute output rate 46000 bits/sec, 32 packets/sec
52499121 packets input, 3402971275 bytes, 0 no buffer
Received 919 broadcasts (0 multicasts)
0 runts, 0 giants, 0 throttles
0 input errors, 0 CRC, 0 frame, 0 overrun, 0 ignored
0 watchdog, 0 multicast, 0 pause input
0 input packets with dribble condition detected
118762062 packets output, 172364893339 bytes, 0 underruns
0 output errors, 0 collisions, 3 interface resets
0 babbles, 0 late collision, 0 deferred
0 lost carrier, 0 no carrier, 0 PAUSE output
0 output buffer failures, 0 output buffers swapped out
This shows the number of hours, minutes, and seconds since the last packet was successfully received by an interface and processed locally on the router. This is useful to know when a dead interface has failed. This counter is updated only when packets are process switched, not when packets are fast switched. Last input nevermeans there was no successful interface packet transfer to other end point or terminal. Usually this means there was no packet transfer relative to that entity.
Related Information
- Troubleshooting Cisco Catalyst Switches to NIC Compatibility Issues
- Using PortFast and Other Commands to Fix Workstation Startup Connectivity Delays
- Configuring and Troubleshooting Ethernet 10/100/1000Mb Half/Full Duplex Auto-Negotiation
- Upgrade Software Images and Working with Configuration Files on Catalyst Switches
- Technical Support & Documentation — Cisco Systems
Introduction
This document describes the errdisabled state, how to recover from it, and provides examples of errdisable recovery. This document uses the terms errdisable and error disable interchangeably. Customers often contact Cisco Technical Support when they notice that one or more of their switch ports have become error disabled, which means that the ports have a status of errdisabled. These customers want to know why the error disablement happened and how they can restore the ports to normal.
Note: The port status of err-disabled displays in the output of the show interfaces interface_number status command.
Prerequisites
Requirements
There are no specific requirements for this document.
Components Used
To create the examples in this document, you need two Cisco Catalyst 4500/6500 Series Switches (or the equivalent) in a lab environment with cleared configurations. The switches must run Cisco IOS® Software and each switch must have two Fast Ethernet ports that are capable of EtherChannel and PortFast.
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, ensure that you understand the potential impact of any command.
Background Information
Platforms That Use Errdisable
The errdisable feature is supported on these Catalyst switches:
-
Catalyst switches that run Cisco IOS Software:
-
2900XL / 3500XL
-
2940 / 2950 / 2960 / 2970
-
3550 / 3560 / 3560-E / 3750 / 3750-E
- 3650 / 3850
-
4500 / 4503 / 4506 / 4507 / 4510 / 4500-X
-
6500 / 6503 / 6504 / 6506 / 6509
- 9200 / 9300 / 9400 / 9500
-
The way in which errdisable is implemented varies between software platforms. This document specifically focuses on errdisable for switches that run Cisco IOS Software.
Errdisable
Function of Errdisable
If the configuration shows a port to be enabled, but software on the switch detects an error situation on the port, the software shuts down that port. In other words, the port is automatically disabled by the switch operating system software because of an error condition that is encountered on the port.
When a port is error disabled, it is effectively shut down and no traffic is sent or received on that port. The port LED is set to the color orange and, when you issue the show interfaces command, the port status shows err-disabled. Here is an example of what an error-disabled port looks like from the command-line interface (CLI) of the switch:
cat6knative#show interfaces gigabitethernet 4/1 status Port Name Status Vlan Duplex Speed Type Gi4/1 err-disabled 100 full 1000 1000BaseSX
Or, if the interface has been disabled because of an error condition, you can see messages that are similar to these in both the console and the syslog:
%SPANTREE-SP-2-BLOCK_BPDUGUARD: Received BPDU on port GigabitEthernet4/1 with BPDU Guard enabled. Disabling port. %PM-SP-4-ERR_DISABLE: bpduguard error detected on Gi4/1, putting Gi4/1 in err-disable state
This example message displays when a host port receives the bridge protocol data unit (BPDU). The actual message depends on the reason for the error condition.
The error disable function serves two purposes:
-
It lets the administrator know when and where there is a port problem.
-
It eliminates the possibility that this port can cause other ports on the module (or the entire module) to fail.
Such a failure can occur when a bad port monopolizes buffers or port error messages monopolize interprocess communications on the card, which can ultimately cause serious network issues. The error disable feature helps prevent these situations.
Causes of Errdisable
This feature was first implemented in order to handle special collision situations in which the switch detected excessive or late collisions on a port. Excessive collisions occur when a frame is dropped because the switch encounters 16 collisions in a row. Late collisions occur because every device on the wire did not recognize that the wire was in use. Possible causes of these types of errors include:
-
A cable that is out of specification (either too long, the wrong type, or defective)
-
A bad network interface card (NIC) card (with physical problems or driver problems)
-
A port duplex misconfiguration
A port duplex misconfiguration is a common cause of the errors because of failures to negotiate the speed and duplex properly between two directly connected devices (for example, a NIC that connects to a switch). Only half-duplex connections can ever have collisions in a LAN. Because of the carrier sense multiple access (CSMA) nature of Ethernet, collisions are normal for half duplex, as long as the collisions do not exceed a small percentage of traffic.
There are various reasons for the interface to go into errdisable. The reason can be:
-
Duplex mismatch
-
Port channel misconfiguration
-
BPDU guard violation
-
UniDirectional Link Detection (UDLD) condition
-
Late-collision detection
-
Link-flap detection
-
Security violation
-
Port Aggregation Protocol (PAgP) flap
-
Layer 2 Tunneling Protocol (L2TP) guard
-
DHCP snooping rate-limit
-
Incorrect GBIC / Small Form-Factor Pluggable (SFP) module or cable
-
Address Resolution Protocol (ARP) inspection
-
Inline power
Note: Error-disable detection is enabled for all of these reasons by default. In order to disable error-disable detection, use the no errdisable detect cause command. The show errdisable detect command displays the error-disable detection status.
Determine If Ports Are in the Errdisabled State
You can determine if your port has been error disabled if you issue the show interfaces command.
Here is an example of an active port:
cat6knative#show interfaces gigabitethernet 4/1 status
!--- Refer to show interfaces status for more information on the command.
Port Name Status Vlan Duplex Speed Type
Gi4/1 Connected 100 full 1000 1000BaseSX
Here is an example of the same port in the error disabled state:
cat6knative#show interfaces gigabitethernet 4/1 status
!--- Refer to show interfaces status for more information on the command.
Port Name Status Vlan Duplex Speed Type
Gi4/1 err-disabled 100 full 1000 1000BaseSX
Note: When a port is error disabled, the LED on the front panel that is associated with the port is set to the color orange.
Determine the Reason for the Errdisabled State (Console Messages, Syslog, and the show errdisable recovery Command)
When the switch puts a port in the error-disabled state, the switch sends a message to the console that describes why it disabled the port. The example in this section provides two sample messages that show the reason for port disablement:
-
One disablement is because of the PortFast BPDU guard feature.
-
The other disablement is because of an EtherChannel configuration problem.
Note: You can also see these messages in the syslog if you issue the show log command.
Here are the sample messages:
%SPANTREE-SP-2-BLOCK_BPDUGUARD: Received BPDU on port GigabitEthernet4/1 with BPDU Guard enabled. Disabling port. %PM-SP-4-ERR_DISABLE: bpduguard error detected on Gi4/1, putting Gi4/1 in err-disable state %SPANTREE-2-CHNMISCFG: STP loop - channel 11/1-2 is disabled in vlan 1
If you have enabled errdisable recovery, you can determine the reason for the errdisable status if you issue the show errdisable recovery command. Here is an example:
cat6knative#show errdisable recovery ErrDisable Reason Timer Status ----------------- -------------- udld Enabled bpduguard Enabled security-violatio Enabled channel-misconfig Enabled pagp-flap Enabled dtp-flap Enabled link-flap Enabled l2ptguard Enabled psecure-violation Enabled gbic-invalid Enabled dhcp-rate-limit Enabled mac-limit Enabled unicast-flood Enabled arp-inspection Enabled Timer interval: 300 seconds Interfaces that will be enabled at the next timeout: Interface Errdisable reason Time left(sec) --------- --------------------- -------------- Fa2/4 bpduguard 273
Recover a Port from Errdisabled State
This section provides examples of how you can encounter an error-disabled port and how to fix it, as well as a brief discussion of a few additional reasons that a port can become error disabled. In order to recover a port from the errdisable state, first identify and correct the root problem, and then reenable the port. If you reenable the port before you fix the root problem, the ports just become error disabled again.
Correct the Root Problem
After you discover why the ports were disabled, fix the root problem. The fix depends on what triggered the problem. There are numerous things that can trigger the shutdown. This section discusses some of the most noticeable and common causes:
-
EtherChannel misconfiguration
In order for EtherChannel to work, the ports that are involved must have consistent configurations. The ports must have the same VLAN, the same trunk mode, the same speed, the same duplex, and so on. Most of the configuration differences within a switch are caught and reported when you create the channel. If one switch is configured for EtherChannel and the other switch is not configured for EtherChannel, the spanning tree process can shut down the channeled ports on the side that is configured for EtherChannel. The on mode of EtherChannel does not send PAgP packets to negotiate with the other side before channeling; it just assumes that the other side is channeling. In addition, this example does not turn on EtherChannel for the other switch, but leaves these ports as individual, unchanneled ports. If you leave the other switch in this state for a minute or so, Spanning Tree Protocol (STP) on the switch where the EtherChannel is turned on thinks that there is a loop. This puts the channeling ports in the errdisabled state.
In this example, a loop was detected and the ports were disabled. The output of the show etherchannel summary command shows that the Number of channel-groups in use is 0. When you look at one of the ports that are involved, you can see that the status is err-disabled:
%SPANTREE-2-CHNL_MISCFG: Detected loop due to etherchannel misconfiguration of Gi4/1 cat6knative#show etherchannel summary !--- Refer to show etherchannel for more information on the command. Flags: D - down P - in port-channel I - stand-alone s - suspended H - Hot-standby (LACP only) R - Layer3 S - Layer2 U - in use f - failed to allocate aggregator u - unsuitable for bundling Number of channel-groups in use: 0 Number of aggregators: 0 Group Port-channel Protocol Ports ------+-------------+-----------+-----------------------------------------------The EtherChannel was torn down because the ports were placed in errdisable on this switch.
cat6knative#show interfaces gigabitethernet 4/1 status Port Name Status Vlan Duplex Speed Type Gi4/1 err-disabled 100 full 1000 1000BaseSX
In order to determine what the problem was, look at the error message. The message indicates that the EtherChannel encountered a spanning tree loop. As this section explains, this problem can occur when one device (the switch, in this case) has EtherChannel turned on manually with use of the on mode (as opposed to desirable) and the other connected device (the other switch, in this case) does not have EtherChannel turned on at all. One way to fix the situation is to set the channel mode to desirable on both sides of the connection, and then reenable the ports. Then, each side forms a channel only if both sides agree to channel. If they do not agree to channel, both sides continue to function as normal ports.
cat6knative(config-terminal)#interface gigabitethernet 4/1 cat6knative(config-if)#channel-group 3 mode desirable non-silent
-
Duplex mismatch
Duplex mismatches are common because of failures to autonegotiate speed and duplex properly. Unlike a half duplex device, which must wait until there are no other devices that transmit on the same LAN segment, a full-duplex device transmits whenever the device has something to send, regardless of other devices. If this transmission occurs while the half-duplex device transmits, the half-duplex device considers this either a collision (during the slot time) or a late collision (after the slot time). Because the full-duplex side never expects collisions, this side never realizes that it must retransmit that dropped packet. A low percentage rate of collisions is normal with half duplex, but is not normal with full duplex. A switch port that receives many late collisions usually indicates a duplex mismatch problem. Be sure that the ports on both sides of the cable are set to the same speed and duplex. The show interfaces interface_number command tells you the speed and duplex for Catalyst switch ports. Later versions of Cisco Discovery Protocol (CDP) can warn you about a duplex mismatch before the port is put in the error-disabled state.
In addition, there are settings on a NIC, such as autopolarity features, that can cause the problem. If you are in doubt, turn these settings off. If you have multiple NICs from a vendor and the NICs all appear to have the same problem, check the manufacturer website for the release notes and be sure that you have the latest drivers.
Other causes of late collisions include:
-
A bad NIC (with physical problems, not just configuration problems)
-
A bad cable
-
A cable segment that is too long
-
-
BPDU port guard
A port that uses PortFast must only connect to an end station (such as a workstation or server) and not to devices that generate spanning tree BPDUs, such as switches, or bridges and routers that bridge. If the switch receives a spanning tree BPDU on a port that has spanning tree PortFast and spanning tree BPDU guard enabled, the switch puts the port in errdisabled mode in order to guard against potential loops. PortFast assumes that a port on a switch cannot generate a physical loop. Therefore, PortFast skips the initial spanning tree checks for that port, which avoids the timeout of end stations at bootup. The network administrator must carefully implement PortFast. On ports that have PortFast enabled, BPDU guard helps ensure that the LAN stays loop-free.
This example shows how to turn on this feature. This example was chosen because creation of an error-disable situation is easy in this case:
cat6knative(config-if)#spanning-tree bpduguard enable !--- Refer to spanning-tree bpduguard for more information on the command.In this example, a Catalyst 6509 switch is connected to another switch (a 6509). The 6500 sends BPDUs every 2 seconds (with use of the default spanning tree settings). When you enable PortFast on the 6509 switch port, the BPDU guard feature watches for BPDUs that come in on this port. When a BPDU comes into the port, which means that a device that is not an end device is detected on that port, the BPDU guard feature error disables the port in order to avoid the possibility of a spanning tree loop.
cat6knative(config-if)#spanning-tree portfast enable !--- Refer to spanning-tree portfast (interface configuration mode) !--- for more information on the command. Warning: Spantree port fast start can only be enabled on ports connected to a single host. Connecting hubs, concentrators, switches, bridges, etc. to a fast start port can cause temporary spanning tree loops. %PM-SP-4-ERR_DISABLE: bpduguard error detected on Gi4/1, putting Gi4/1 in err-disable state.In this message, the switch indicates that it received a BPDU on a PortFast-enabled port, and so the switch shuts down port Gi4/1.
cat6knative#show interfaces gigabitethernet 4/1 status Port Name Status Vlan Duplex Speed Type Gi4/1 err-disabled 100 full 1000 1000BaseSX
You need to turn off the PortFast feature because this port is a port with an improper connection. The connection is improper because PortFast is enabled, and the switch connects to another switch. Remember that PortFast is only for use on ports that connect to end stations.
cat6knative(config-if)#spanning-tree portfast disable
-
UDLD
The UDLD protocol allows devices that are connected through fiber-optic or copper Ethernet cables (for example, Category 5 cabling) to monitor the physical configuration of the cables and detect when a unidirectional link exists. When a unidirectional link is detected, UDLD shuts down the affected port and alerts the user. Unidirectional links can cause a variety of problems, which include spanning-tree topology loops.
Note: UDLD exchanges protocol packets between the neighboring devices. Both devices on the link must support UDLD and have UDLD enabled on the respective ports. If you have UDLD enabled on only one port of a link, it can also leave the end configured with UDLD to go to errdisable state.
Each switch port that is configured for UDLD sends UDLD protocol packets that contain the port device (or port ID) and the neighbor device (or port IDs) that are seen by UDLD on that port. The neighboring ports must see their own device or port ID (echo) in the packets that are received from the other side. If the port does not see its own device or port ID in the incoming UDLD packets for a specific duration of time, the link is considered unidirectional. Therefore, the respective port is disabled and a message that is similar to this is printed on the console:
PM-SP-4-ERR_DISABLE: udld error detected on Gi4/1, putting Gi4/1 in err-disable state.
For more information on UDLD operation, configuration, and commands, refer to the document Configuring UniDirectional Link Detection (UDLD).
-
Link-flap error
Link flap means that the interface continually goes up and down. The interface is put into the errdisabled state if it flaps more than five times in 10 seconds. The common cause of link flap is a Layer 1 issue such as a bad cable, duplex mismatch, or bad Gigabit Interface Converter (GBIC) card. Look at the console messages or the messages that were sent to the syslog server that state the reason for the port shutdown.
%PM-4-ERR_DISABLE: link-flap error detected on Gi4/1, putting Gi4/1 in err-disable state
Issue this command in order to view the flap values:
cat6knative#show errdisable flap-values !--- Refer to show errdisable flap-values for more information on the command. ErrDisable Reason Flaps Time (sec) ----------------- ------ ---------- pagp-flap 3 30 dtp-flap 3 30 link-flap 5 10 -
Loopback error
A loopback error occurs when the keepalive packet is looped back to the port that sent the keepalive. The switch sends keepalives out all the interfaces by default. A device can loop the packets back to the source interface, which usually occurs because there is a logical loop in the network that the spanning tree has not blocked. The source interface receives the keepalive packet that it sent out, and the switch disables the interface (errdisable). This message occurs because the keepalive packet is looped back to the port that sent the keepalive:
%PM-4-ERR_DISABLE: loopback error detected on Gi4/1, putting Gi4/1 in err-disable state
Keepalives are sent on all interfaces by default in Cisco IOS Software Release 12.1EA-based software. In Cisco IOS Software Release 12.2SE-based software and later, keepalives are not sent by default on fiber and uplink interfaces. For more information, refer to Cisco bug ID CSCea46385
 (registered customers only) .
(registered customers only) .The suggested workaround is to disable keepalives and upgrade to Cisco IOS Software Release 12.2SE or later.
-
Port security violation
You can use port security with dynamically learned and static MAC addresses in order to restrict the ingress traffic of a port. In order to restrict the traffic, you can limit the MAC addresses that are allowed to send traffic into the port. In order to configure the switch port to error disable if there is a security violation, issue this command:
cat6knative(config-if)#switchport port-security violation shutdown
A security violation occurs in either of these two situations:
-
When the maximum number of secure MAC addresses is reached on a secure port and the source MAC address of the ingress traffic differs from any of the identified secure MAC addresses
In this case, port security applies the configured violation mode.
-
If traffic with a secure MAC address that is configured or learned on one secure port attempts to access another secure port in the same VLAN
In this case, port security applies the shutdown violation mode.
-
-
L2pt Guard
When the Layer 2 PDUs enter the tunnel or access port on the inbound edge switch, the switch overwrites the customer PDU-destination MAC address with a well-known Cisco proprietary multicast address (01-00-0c-cd-cd-d0). If 802.1Q tunneling is enabled, packets are also double-tagged. The outer tag is the customer metro tag and the inner tag is the customer VLAN tag. The core switches ignore the inner tags and forward the packet to all trunk ports in the same metro VLAN. The edge switches on the outbound side restore the proper Layer 2 protocol and MAC address information and forward the packets to all tunnel or access ports in the same metro VLAN. Therefore, the Layer 2 PDUs are kept intact and delivered across the service-provider infrastructure to the other side of the customer network.
Switch(config)#interface gigabitethernet 0/7 l2protocol-tunnel {cdp | vtp | stp}The interface goes to errdisabled state. If an encapsulated PDU (with the proprietary destination MAC address) is received from a tunnel port or access port with Layer 2 tunneling enabled, the tunnel port is shut down to prevent loops. The port also shuts down when a configured shutdown threshold for the protocol is reached. You can manually reenable the port (issue a shutdown, no shutdown command sequence) or if errdisable recovery is enabled, the operation is retried after a specified time interval.
To recover the interface from errdisable state, reenable the port with the command errdisable recovery cause l2ptguard. This command is used to configure the recovery mechanism from a Layer 2 maximum rate error so that the interface can be brought out of the disabled state and allowed to try again. You can also set the time interval. Errdisable recovery is disabled by default; when enabled, the default time interval is 300 seconds.
-
Incorrect SFP cable
Ports go into errdisable state with the %PHY-4-SFP_NOT_SUPPORTED error message when you connect Catalyst 3560 and Catalyst 3750 Switches and use an SFP Interconnect Cable.
The Cisco Catalyst 3560 SFP Interconnect Cable (CAB-SFP-50CM=) provides for a low-cost, point-to-point, Gigabit Ethernet connection between Catalyst 3560 Series Switches. The 50-centimeter (cm) cable is an alternative to the SFP transceivers to interconnect Catalyst 3560 Series Switches through their SFP ports over a short distance. All Cisco Catalyst 3560 Series Switches support the SFP Interconnect Cable.
When a Catalyst 3560 Switch is connected to a Catalyst 3750 or any other type of Catalyst switch model, you cannot use the CAB-SFP-50CM= cable. You can connect both switches with a copper cable with SFP (GLC-T) on both devices instead of a CAB-SFP-50CM= cable.
-
802.1X Security Violation
DOT1X-SP-5-SECURITY_VIOLATION: Security violation on interface GigabitEthernet4/8, New MAC address 0080.ad00.c2e4 is seen on the interface in Single host mode %PM-SP-4-ERR_DISABLE: security-violation error detected on Gi4/8, putting Gi4/8 in err-disable state
This message indicates that the port on the specified interface is configured in single-host mode. Any new host that is detected on the interface is treated as a security violation. The port has been error disabled.
Ensure that only one host is connected to the port. If you need to connect to an IP phone and a host behind it, configure Multidomain Authentication Mode on that switchport.
The Multidomain authentication (MDA) mode allows an IP phone and a single host behind the IP phone to authenticate independently, with 802.1X, MAC authentication bypass (MAB), or (for the host only) web-based authentication. In this application, Multidomain refers to two domains — data and voice — and only two MAC addresses are allowed per port. The switch can place the host in the data VLAN and the IP phone in the voice VLAN, though they appear to be on the same switch port. The data VLAN assignment can be obtained from the vendor-specific attributes (VSAs) received from the AAA server within authentication.
For more information, refer to the Multidomain Authentication Mode section of Configuring 802.1X Port-Based Authentication.
Reenable the Errdisabled Ports
After you fix the root problem, the ports are still disabled if you have not configured errdisable recovery on the switch. In this case, you must reenable the ports manually. Issue the shutdown command and then the no shutdown interface mode command on the associated interface in order to manually reenable the ports.
The errdisable recovery command allows you to choose the type of errors that automatically reenable the ports after a specified amount of time. The show errdisable recovery command shows the default error-disable recovery state for all the possible conditions.
cat6knative#show errdisable recovery ErrDisable Reason Timer Status ----------------- -------------- udld Disabled bpduguard Disabled security-violatio Disabled channel-misconfig Disabled pagp-flap Disabled dtp-flap Disabled link-flap Disabled l2ptguard Disabled psecure-violation Disabled gbic-invalid Disabled dhcp-rate-limit Disabled mac-limit Disabled unicast-flood Disabled arp-inspection Disabled Timer interval: 300 seconds Interfaces that will be enabled at the next timeout:
Note: The default timeout interval is 300 seconds and, by default, the timeout feature is disabled.
In order to turn on errdisable recovery and choose the errdisable conditions, issue this command:
cat6knative#errdisable recovery cause ?
all Enable timer to recover from all causes
arp-inspection Enable timer to recover from arp inspection error disable
state
bpduguard Enable timer to recover from BPDU Guard error disable
state
channel-misconfig Enable timer to recover from channel misconfig disable
state
dhcp-rate-limit Enable timer to recover from dhcp-rate-limit error
disable state
dtp-flap Enable timer to recover from dtp-flap error disable state
gbic-invalid Enable timer to recover from invalid GBIC error disable
state
l2ptguard Enable timer to recover from l2protocol-tunnel error
disable state
link-flap Enable timer to recover from link-flap error disable
state
mac-limit Enable timer to recover from mac limit disable state
pagp-flap Enable timer to recover from pagp-flap error disable
state
psecure-violation Enable timer to recover from psecure violation disable
state
security-violation Enable timer to recover from 802.1x violation disable
state
udld Enable timer to recover from udld error disable state
unicast-flood Enable timer to recover from unicast flood disable state
This example shows how to enable the BPDU guard errdisable recovery condition:
cat6knative(Config)#errdisable recovery cause bpduguard
A nice feature of this command is that, if you enable errdisable recovery, the command lists general reasons that the ports have been put into the error-disable state. In this example, notice that the BPDU guard feature was the reason for the shutdown of port 2/4:
cat6knative#show errdisable recovery ErrDisable Reason Timer Status ----------------- -------------- udld Disabled bpduguard Enabled security-violatio Disabled channel-misconfig Disabled pagp-flap Disabled dtp-flap Disabled link-flap Disabled l2ptguard Disabled psecure-violation Disabled gbic-invalid Disabled dhcp-rate-limit Disabled mac-limit Disabled unicast-flood Disabled arp-inspection Disabled Timer interval: 300 seconds Interfaces that will be enabled at the next timeout: Interface Errdisable reason Time left(sec) --------- --------------------- -------------- Fa2/4 bpduguard 290
If any one of the errdisable recovery conditions is enabled, the ports with this condition are reenabled after 300 seconds. You can also change this default of 300 seconds if you issue this command:
cat6knative(Config)#errdisable recovery interval timer_interval_in_seconds
This example changes the errdisable recovery interval from 300 to 400 seconds:
cat6knative(Config)#errdisable recovery interval 400
Verify
-
show version—Displays the version of the software that is used on the switch.
-
show interfaces interface interface_number status—Shows the current status of the switch port.
-
show errdisable detect—Displays the current settings of the errdisable timeout feature and, if any of the ports are currently error disabled, the reason that they are error disabled.
Troubleshoot
-
show interfaces status err-disabled—Shows which local ports are involved in the errdisabled state.
-
show etherchannel summary—Shows the current status of the EtherChannel.
-
show errdisable recovery—Shows the time period after which the interfaces are enabled for errdisable conditions.
-
show errdisable detect—Shows the reason for the errdisable status.
For more information on how to troubleshoot switchport issues, refer to Troubleshooting Switch Port and Interface Problems.
Related Information
- Interface Is in errdisable Status Troubleshooting Hardware and Common Issues on Catalyst 6500/6000 Series Switches Running Cisco IOS System Software
- Spanning Tree PortFast BPDU Guard Enhancement
- Understanding EtherChannel Inconsistency Detection
- Troubleshooting Switch Port and Interface Problems
- LAN Product Support
- LAN Switching Technology Support
- Technical Support — Cisco Systems
Страница была создана 28.04.2022
Команда показывает статистику трафика и ошибок на определённом интерфейсе:
Switch#show interfaces имя_интерфейса
Пример вывода команды show interfaces, обратите внимание, на выделенный текст желтым цветом.
Switch#show interfaces gi0/1
GigabitEthernet0/1 is up, line protocol is up (connected)
Hardware is Gigabit Ethernet, address is 001e.1478.b7b1 (bia 001e.1478.b7b1)
Description: SW-2
MTU 1500 bytes, BW 100000 Kbit/sec, DLY 100 usec,
reliability 255/255, txload 1/255, rxload 1/255
Encapsulation ARPA, loopback not set
Keepalive set (10 sec)
Full-duplex, 100Mb/s, media type is 10/100/1000BaseTX
input flow-control is off, output flow-control is unsupported
ARP type: ARPA, ARP Timeout 04:00:00
Last input 00:00:00, output 00:00:00, output hang never
Last clearing of «show interface» counters never
Input queue: 0/75/0/0 (size/max/drops/flushes); Total output drops: 42164
Queueing strategy: fifo
Output queue: 0/40 (size/max)
5 minute input rate 781000 bits/sec, 122 packets/sec
5 minute output rate 183000 bits/sec, 65 packets/sec
75482 packets input, 104620499 bytes, 0 no buffer
Received 6352 broadcasts (3951 multicasts)
0 runts, 0 giants, 0 throttles
105684 input errors, 103301 CRC, 0 frame, 0 overrun, 0 ignored
0 watchdog, 3951 multicast, 0 pause input
0 input packets with dribble condition detected
39937001 packets output, 2917338077 bytes, 0 underruns
0 output errors, 0 collisions, 4 interface resets
10 unknown protocol drops
0 babbles, 0 late collision, 0 deferred
0 lost carrier, 0 no carrier, 0 pause output
0 output buffer failures, 0 output buffers swapped out
После того, как вы устранили вероятную ошибку, нужно сбросить счётчики, чтобы убедиться, что ошибок больше нет.
Switch#clear counters gi0/1
После сброса, повторно проверяем счетчики, как видим счетчики обнулились, в примере я выделил их жёлтым цветом.
Switch#show interfaces gi0/1
GigabitEthernet0/1 is up, line protocol is up (connected)
Hardware is Gigabit Ethernet, address is 001e.1478.b7b1 (bia 001e.1478.b7b1)
Description: SW-2
MTU 1500 bytes, BW 1000000 Kbit/sec, DLY 10 usec,
reliability 255/255, txload 1/255, rxload 1/255
Encapsulation ARPA, loopback not set
Keepalive set (10 sec)
Full-duplex, 1000Mb/s, media type is 10/100/1000BaseTX
input flow-control is off, output flow-control is unsupported
ARP type: ARPA, ARP Timeout 04:00:00
Last input 00:00:00, output 00:00:00, output hang never
Last clearing of «show interface» counters 00:00:08
Input queue: 0/75/0/0 (size/max/drops/flushes); Total output drops: 0
Queueing strategy: fifo
Output queue: 0/40 (size/max)
5 minute input rate 1352000 bits/sec, 306 packets/sec
5 minute output rate 313000 bits/sec, 91 packets/sec
1274 packets input, 455165 bytes, 0 no buffer
Received 199 broadcasts (118 multicasts)
0 runts, 0 giants, 0 throttles
0 input errors, 0 CRC, 0 frame, 0 overrun, 0 ignored
0 watchdog, 118 multicast, 0 pause input
0 input packets with dribble condition detected
663 packets output, 312346 bytes, 0 underruns
0 output errors, 0 collisions, 0 interface resets
0 unknown protocol drops
0 babbles, 0 late collision, 0 deferred
0 lost carrier, 0 no carrier, 0 pause outputv
0 output buffer failures, 0 output buffers swapped out
В таблице показаны некоторые значение и описания к ним.
![]()
|
![]()
![]()
![]()
You can view the counters for a port on a Cisco switch using the
show interfaces command. E.g., if I want to check on whether
cyclic redundancy check (CRC) errors have been occurring on port fa0/16,
I can issue the command shown below:
Huron>show interfaces fa0/16
FastEthernet0/16 is up, line protocol is up (connected)
Hardware is Fast Ethernet, address is 0009.e897.d290 (bia 0009.e897.d290)
MTU 1500 bytes, BW 10000 Kbit, DLY 1000 usec,
reliability 255/255, txload 19/255, rxload 1/255
Encapsulation ARPA, loopback not set
Keepalive set (10 sec)
Full-duplex, 10Mb/s, media type is 100BaseTX
input flow-control is unsupported output flow-control is unsupported
ARP type: ARPA, ARP Timeout 04:00:00
Last input never, output 00:00:00, output hang never
Last clearing of "show interface" counters 2d17h
Input queue: 0/75/0/0 (size/max/drops/flushes); Total output drops: 0
Queueing strategy: fifo
Output queue: 0/40 (size/max)
5 minute input rate 24000 bits/sec, 40 packets/sec
5 minute output rate 756000 bits/sec, 64 packets/sec
46168 packets input, 4608074 bytes, 0 no buffer
Received 1250 broadcasts (1161 multicast)
0 runts, 0 giants, 0 throttles
121 input errors, 16 CRC, 105 frame, 0 overrun, 0 ignored
0 watchdog, 1161 multicast, 0 pause input
0 input packets with dribble condition detected
255151 packets output, 119141892 bytes, 0 underruns
0 output errors, 0 collisions, 0 interface resets
0 babbles, 0 late collision, 0 deferred
0 lost carrier, 0 no carrier, 0 PAUSE output
0 output buffer failures, 0 output buffers swapped out
Huron>
I can see that 16 CRC errors have occurred since the counters for this
port were last reset 2 days and 17 hours ago. I can tell the counters for
the port were reset that long ago from the line below that appears in
the output of the «show interface» command.
Last clearing of "show interface" counters 2d17h
I can reset the counters by entering
privileged EXEC mode by isssuing the enable command. I can
then clear the counters for just the one particular port by the command
clear counters port_designator. When you enter the
command you will be prompted to confirm that you wish the counters
on the interface to be reset. You can enter y to confirm that
you wish that action taken. E.g.:
Huron>enable
Password:
Huron#clear counters fa0/16
Clear "show interface" counters on this interface [confirm]y
Huron#show interface fa0/16
FastEthernet0/16 is up, line protocol is up (connected)
Hardware is Fast Ethernet, address is 0009.e897.d290 (bia 0009.e897.d290)
MTU 1500 bytes, BW 10000 Kbit, DLY 1000 usec,
reliability 255/255, txload 1/255, rxload 1/255
Encapsulation ARPA, loopback not set
Keepalive set (10 sec)
Full-duplex, 10Mb/s, media type is 100BaseTX
input flow-control is unsupported output flow-control is unsupported
ARP type: ARPA, ARP Timeout 04:00:00
Last input never, output 00:00:01, output hang never
Last clearing of "show interface" counters 00:01:27
Input queue: 0/75/0/0 (size/max/drops/flushes); Total output drops: 0
Queueing strategy: fifo
Output queue: 0/40 (size/max)
5 minute input rate 0 bits/sec, 0 packets/sec
5 minute output rate 0 bits/sec, 0 packets/sec
0 packets input, 0 bytes, 0 no buffer
Received 0 broadcasts (0 multicast)
0 runts, 0 giants, 0 throttles
0 input errors, 0 CRC, 0 frame, 0 overrun, 0 ignored
0 watchdog, 0 multicast, 0 pause input
0 input packets with dribble condition detected
80 packets output, 7161 bytes, 0 underruns
0 output errors, 0 collisions, 0 interface resets
0 babbles, 0 late collision, 0 deferred
0 lost carrier, 0 no carrier, 0 PAUSE output
0 output buffer failures, 0 output buffers swapped out
Huron#
In addition to resetting the error counters, the clear counters
command also resets the input and output counters.
Huron>show interfaces fa0/16 counters Port InOctets InUcastPkts InMcastPkts InBcastPkts Fa0/16 386867 1624 294 21 Port OutOctets OutUcastPkts OutMcastPkts OutBcastPkts Fa0/16 2527937 2352 671 39 Huron>enable Password: Huron#clear counters fa0/16 Clear "show interface" counters on this interface [confirm]y Huron#show interfaces fa0/16 counters Port InOctets InUcastPkts InMcastPkts InBcastPkts Fa0/16 0 0 0 0 Port OutOctets OutUcastPkts OutMcastPkts OutBcastPkts Fa0/16 192 0 3 0 Huron#
 Errdisable is a feature that automatically disables a port on a Cisco Catalyst switch. When a port is error disabled, it is effectively shut down and no traffic is sent or received on that port.
Errdisable is a feature that automatically disables a port on a Cisco Catalyst switch. When a port is error disabled, it is effectively shut down and no traffic is sent or received on that port.
The error disabled feature is supported on most Catalyst switches running the Cisco IOS software. Including all the following models:
- Catalyst 2940 / 2950 / 2960 / 2960S
- Catalyst 3550 / 3560 / 3560-E / 3750 / 3750-E
- Catalyst 4000 / 4500 / 4507R
- Catalyst 6000 / 6500
The Errdisable error disable feature was designed to inform the administrator when there is a port problem or error. The reasons a catalyst switch can go into Errdisable mode and shutdown a port are many and include:
-
Duplex Mismatch
-
Loopback Error
- Link Flapping (up/down)
- Port Security Violation
- Unicast Flodding
- UDLD Failure
- Broadcast Storms
- BPDU Guard
When a port is in error-disabled state, it is effectively shut down and no traffic is sent or received on that port. The port LED is set to the orange color and, when you issue the show interfaces command, the port status shows as Errdisabled.
Following is an example of what an error-disabled port looks like:
2960G# show interface gigabit0/7
GigabitEthernet0/7 is down, line protocol is down (err-disabled)
Hardware is Gigabit Ethernet, address is 001b.54aa.c107 (bia 001b.54aa.c107)
MTU 1500 bytes, BW 100000 Kbit, DLY 100 usec,
reliability 234/255, txload 1/255, rxload 1/255
Encapsulation ARPA, loopback not set
Keepalive set (10 sec)
Auto-duplex, Auto-speed, media type is 10/100/1000BaseTX
input flow-control is off, output flow-control is unsupported
ARP type: ARPA, ARP Timeout 04:00:00
Last input 18w5d, output 18w5d, output hang never
Last clearing of «show interface» counters never
Input queue: 0/75/0/0 (size/max/drops/flushes); Total output drops: 0
Queueing strategy: fifo
Output queue: 0/40 (size/max)
5 minute input rate 0 bits/sec, 0 packets/sec
5 minute output rate 0 bits/sec, 0 packets/sec
1011 packets input, 862666 bytes, 0 no buffer
Received 157 broadcasts (0 multicast)
0 runts, 0 giants, 0 throttles
3021 input errors, 2 CRC, 0 frame, 0 overrun, 0 ignored
0 watchdog, 144 multicast, 0 pause input
0 input packets with dribble condition detected
402154 packets output, 86290866 bytes, 0 underruns
0 output errors, 0 collisions, 1 interface resets
0 babbles, 0 late collision, 0 deferred
0 lost carrier, 0 no carrier, 0 PAUSE output
0 output buffer failures, 0 output buffers swapped out
To recover a port that is in an Errdisable state, manual intervention is required, and the administrator must access the switch and configure the specific port with ‘shutdown‘ followed by the ‘no shutdown‘ command. This command sequence will enable the port again, however, if the problem persists expect to find the port in Errdisable state again soon.
Understanding and Configuring Errdisable AutoRecovery
As outlined above, there are a number of reasons a port can enter the Errdisable state. One common reason is the Port Security error, also used in our example below.
Of all the errors, Port Security is more a feature rather than an error. Port Security allows the restriction of MAC Addresses on an interface configured as a layer 2 port. This effectively prevents others connecting unwanted hubs or switches on the network. Port Security allows us to specify a single MAC Address to be connected to a specific port, thus restricting access to a specific computer.
In the case of a violation, Port Security will automatically disable the port. This is the behaviour of the default port security policy when enabling Port Security. Following is a configuration example of port security:
2960G(config)# interface GigabitEthernet0/48
2960G(config-if)# switchport access vlan 2
2960G(config-if)# switchport mode access
2960G(config-if)# switchport port-security
2960G(config-if)# spanning-tree portfast
Once a host is connected to the port, we can get more information on its port-security status and actions that will be taken when a violation occurs:
2960G# show port-security interface GigabitEthernet 0/48
Port Security : Enabled
Port Status : Secure-up
Violation Mode : Shutdown
Aging Time : 0 mins
Aging Type : Absolute
SecureStatic Address Aging : Disabled
Maximum MAC Addresses : 1
Total MAC Addresses : 1
Configured MAC Addresses : 0
Sticky MAC Addresses : 0
Last Source Address:Vlan : 001b.54aa.c107
Security Violation Count : 0
Note that the Violation Mode is set to Shutdown. This means that when a violation is detected, the switch will place gigabitethernet 0/48 in the err-disable shutdown state as shown below:
%PORT_SECURITY-2-PSECURE_VIOLATION: Security violation occurred, caused by MAC address 0031.f6ac.03f5 on port GigabitEthernet0/48
While it’s almost always necessary to know when a port security violation occurs there are some circumstances where autorecovery is a desirable feature, especially durng accidental violations.
The following commands enable the autorecovery feature 30 seconds after a port security violation:
2960G(config)# errdisable recovery cause psecure-violation
2960G(config)# errdisable recovery interval 30
Determine the Reason for the Errdisabled State
To view the Errdisabled reasons, and see for which reason the autorecovery feature has been enabled, use the show Errdisable recovery command:
2960G# show errdisable recovery
ErrDisable Reason Timer Status
—————— —————
udld Disabled
bpduguard Disabled
security-violatio Disabled
channel-misconfig Disabled
vmps Disabled
pagp-flap Disabled
dtp-flap Disabled
link-flap Disabled
secure-violation Enabled
sfp-config-mismat Disabled
gbic-invalid Disabled
dhcp-rate-limit Disabled
unicast-flood Disabled
storm-control Disabled
loopback Disabled
Timer interval: 30 seconds
Interfaces that will be enabled at the next timeout.
We have now confirmed that autorecovery is enabled for port-security violations. If it is required to enable the Errdisable autorecovery feature for all supported reasons, use the following command:
2960G(config)# errdisable recovery cause all
To test our configuration we forced a port security violation, causing the switch to place the offending port in the shutdown state. Notice we’ve enabled autorecovery for all Errdisable reasons and the time left to enable the interfaces placed in shutdown state by the port security violation:
2960G# show errdisable recovery
ErrDisable Reason Timer Status
—————— —————
udld Enabled
bpduguard Enabled
security-violatio Enabled
channel-misconfig Enabled
vmps Enabled
pagp-flap Enabled
dtp-flap Enabled
link-flap Enabled
psecure-violation Enabled
sfp-config-mismat Enabled
gbic-invalid Enabled
dhcp-rate-limit Enabled
unicast-flood Enabled
storm-control Enabled
loopback Enabled
Timer interval: 30 seconds
Interfaces that will be enabled at the next timeout:
Interface Errdisable reason Time left(sec)
——— —————— —————
Gi0/48 security-violation 17
Seventeen seconds later, the switch automatically recovered from the port security violation and re-enabled the interface:
%PM-4-ERR_RECOVER: Attempting to recover from secure-violation err-disable state on gigabitethernet0/48
18w4d: %LINK-3-UPDOWN: Interface GigabitEthernet0/48, changed state to up
18w4d: %LINEPROTO-5-UPDOWN: Line protocol on Interface GigabitEthernet0/48, changed state to up
Disabling The Errdisable Feature
There are cases where it might be necessary to disable the Errdisable mechanism for specific supported features in order to overcome constant interface shutdowns and auto recoveries. While the Catalyst IOS does not allow disabling all features we can still fine-tune the mechanism and selectively disable a few.
To view the Errdisable reasons monitored by the switch, use the show Errdisable detect command:
2960G# show errdisable detect
ErrDisable Reason Detection Mode
----------------- --------- ----
bpduguard Enabled port
channel-misconfig Enabled port
community-limit Enabled port
dhcp-rate-limit Enabled port
dtp-flap Enabled port
gbic-invalid Enabled portinline-power Enabled port
invalid-policy Enabled port
link-flap Enabled port
loopback Enabled port
lsgroup Enabled port
mac-limit Enabled port
pagp-flap Enabled portport-mode-failure Enabled port
secure-violation Enabled port/vlan
security-violation Enabled portsfp-config-mismatch Enabled port
small-frame Enabled port
storm-control Enabled port
udld Enabled port
vmps Enabled port
As shown, the command lists all supported Errdisable reasons. For our example, let’s assume we want to disable the inline-power Errdisable feature.
To achieve this, we simply use the following command:
2960G(config)# errdisable recovery cause all
And verify that Errdisable has been disabled for the feature:
2960G# show errdisable detectErrDisable Reason Detection Mode
----------------- --------- ----
bpduguard Enabled port
channel-misconfig Enabled port
community-limit Enabled port
dhcp-rate-limit Enabled port
dtp-flap Enabled port
gbic-invalid Enabled portinline-power Disabled port
invalid-policy Enabled port
link-flap Enabled port
loopback Enabled port
lsgroup Enabled port
mac-limit Enabled port
pagp-flap Enabled portport-mode-failure Enabled port
psecure-violation Enabled port/vlan
security-violation Enabled portsfp-config-mismatch Enabled port
small-frame Enabled port
storm-control Enabled port
udld Enabled port
vmps Enabled port
Overall, the Errdisable feature is an extremely useful tool if configured and monitored correctly. Take the necessary time to play around with the supported options of your Cisco Catalyst switch and fine-tune it to suit your network needs.
Back to Cisco Switches Section